Today, Aqua Security and Orca Security are proud to announce the availability of an integration between the Aqua Platform and the Orca Cloud Security Platform, enabling organizations to efficiently monitor workloads for and protect against runtime compromise using the Aqua’s advanced runtime capabilities while using Orca’s rich cloud data to agentlessly provide context and support investigations. Mutual customers can use Orca Security to ensure that Aqua’s agent is deployed on workloads and to enrich alerts so that security operations and incident response teams have the intelligence they need at their fingertips.
Deployment Assurance
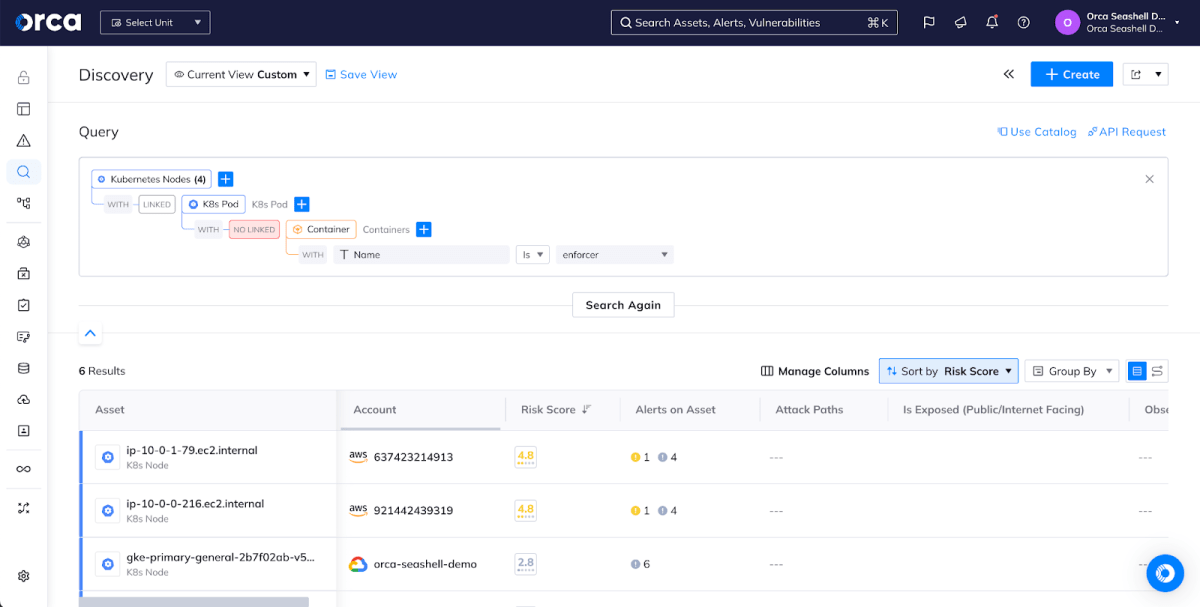
While agents provide runtime visibility that provides a layer of assurance that you can catch abnormal, possibly malicious behavior in a workload and investigate it, you first have to make sure the agent is deployed on all the workloads of interest. This can be a particularly difficult problem in cloud-native environments where new VMs and clusters are created and destroyed all the time; however, by combining the complete coverage of agentless Orca Security with the workload protection of Aqua’s Enforcer, organizations can quickly identify gaps in coverage. For example, here we can see a query for all Kubernetes nodes that don’t have Enforcer deployed on them, representing a gap in our real-time coverage. We could also create an alert from this to proactively notify responsible parties when a new workload doesn’t have the Aqua Enforcer appropriately deployed.
Runtime Alerts With Context
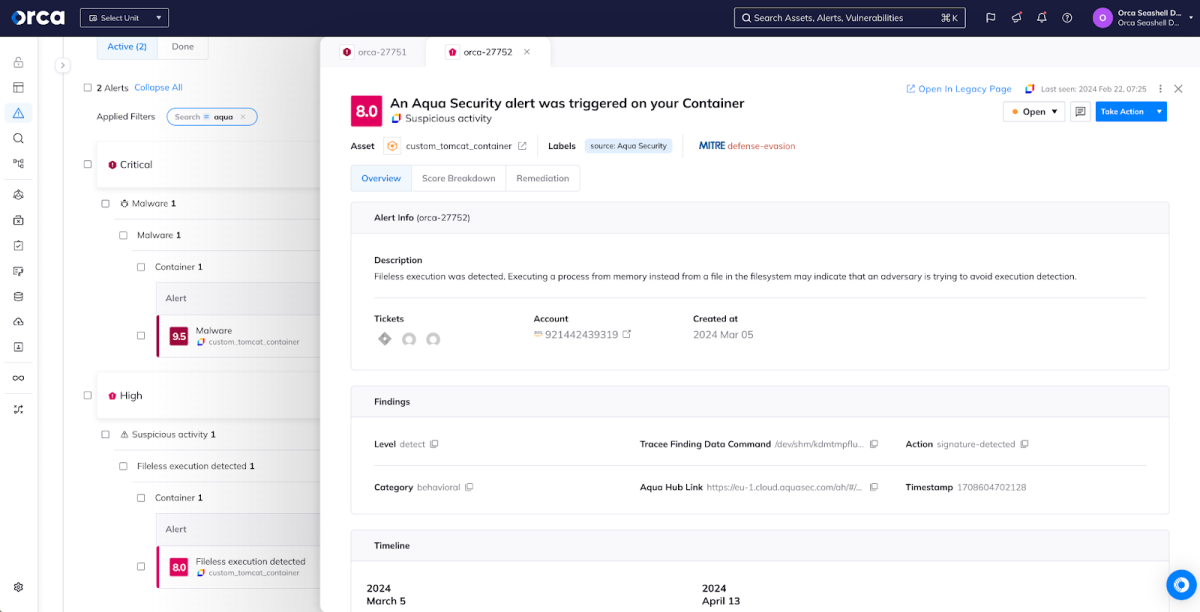
Once Aqua has been integrated with Orca Security, new runtime alerts will automatically surface in the Orca interface, allowing analysts and responders to triage the anomaly and get the full story. In this example, Aqua Enforcer detected fileless execution happening inside of a running container on a cluster in one of our cloud accounts. Fileless execution is an approach that some threat actors take where malware that might be easily detected, if written to disk, is executed directly from memory, making it much harder to detect.
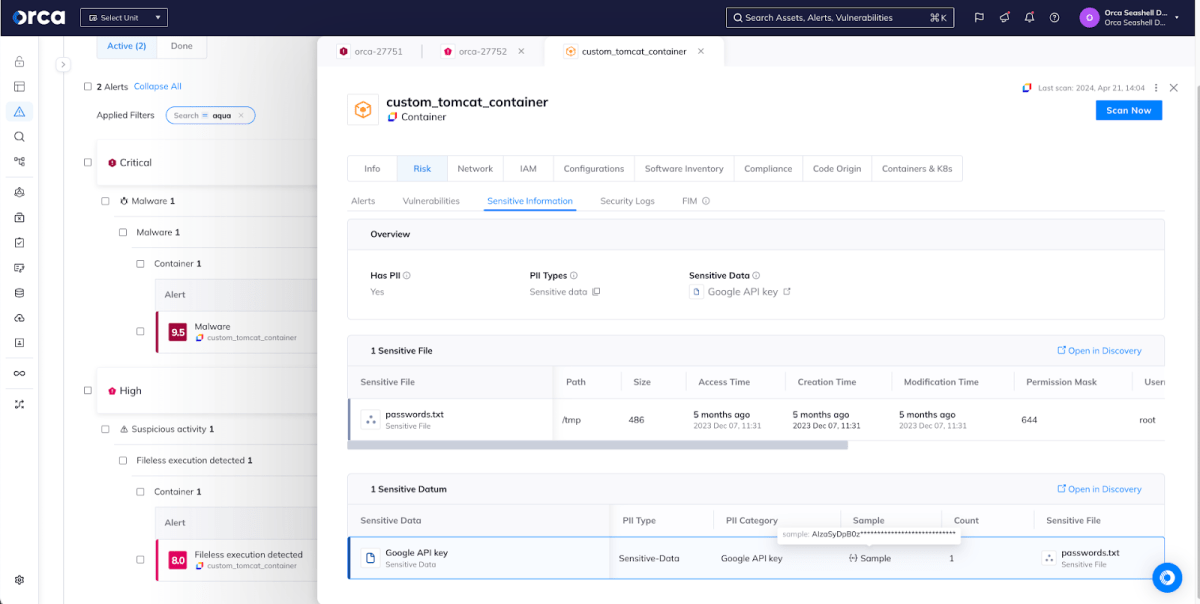
From here, responders have a wealth of intelligence at their fingertips. For example, if responders determine that the fileless execution was malicious, they will want to understand the potential impact of the incident by examining the blast radius of the underlying asset and any sensitive information it has access to. We can see that this particular container has a Google API key embedded in it, something that a savvy threat actor could use to move laterally in our environment. The next steps in our investigation will include inspecting assets that this key would allow access to.
Conclusion
Orca Security is committed to supporting an open ecosystem of integrations to ensure users increase their overall visibility and cloud security goals. By integrating with Aqua Security, users benefit from the deep telemetry between cloud native solutions.
If you are interested in seeing the demo or learning more about the integration, please sign up for a demo.





