‘A state-sponsored attacker uses a zero-day exploit to breach an asset-rich environment. This foothold lets them run previously unknown, file-less attacks originating from an exploited process. Fortunately, the evil plan is foiled by our next-generation, AI-powered security tool that detected the threat in microseconds and prevented it in nanoseconds!’
—Numerous cybersecurity marketing videos inspired by Hollywood movies
Silver bullets shine brightly, but, unfortunately, they tend to mostly work against werewolves.
I spent a decade in Unit 8200 of the Israel Defense Forces, considered one of the most elite cybersecurity offensive units globally. I spent another decade at Check Point Software Technologies, one of the largest pure-play security vendors. At Check Point I served as chief technologist, responsible for that company’s “advanced threat prevention” product suite.
What’s the most important lesson I learned in the IDF and at Check Point? For cyber defense, security basics are always more important than shiny new security toys. Why? It doesn’t matter how dazzling your “next-gen, real-time enforcement cyber death ray” is—attackers will use the simplest means possible to breach your defenses.
Of course, “cyber lightsabers” have value, but they must be regarded as a secondary layer of protection—never the primary one.
IT Hygiene Should Be Your Priority
I’m not the only one to think so. Security basics and good IT hygiene are always listed as fundamentals in anyone’s cybersecurity pyramid, as illustrated below.
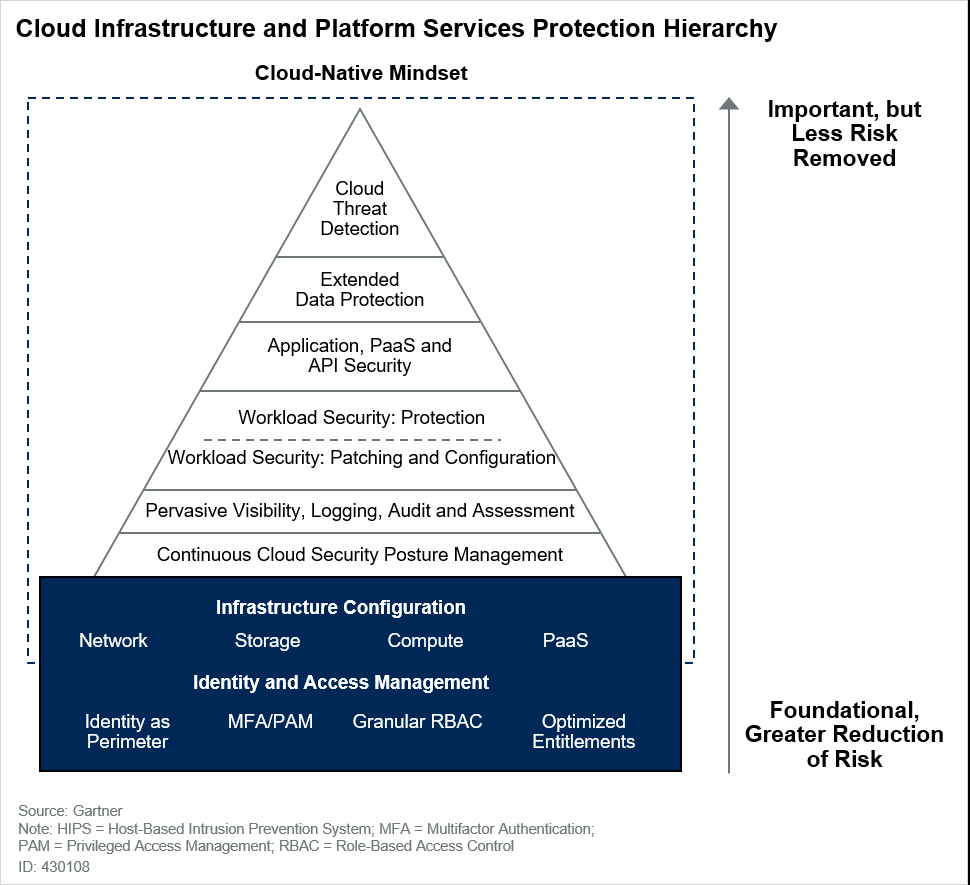
Experienced practitioners won’t be surprised by this fundamentals-first strategy. Correct infrastructure configuration, effective posture management, full visibility to the environment, and patching/configuring it are at the base of the pyramid, closer to the (so-labeled) Foundational, Greater Reduction of Risk. Advanced threat detection tools are at the top of the pyramid, where they’re Important, but Less [is] Risk Removed. Why is this? Simply put, good IT hygiene dramatically reduces risk more than quasi-advanced silver-bullet solutions.
Orca specializes in AWS Cloud Security, Google Cloud Platform Security, and Microsoft Azure Cloud Security.





