According to the 2025 State of Cloud Security Report, 78% of organizations have at least one IAM role that has yet to be used in the last 90 days. Neglected cloud identities such as these, especially overpermissioned ones, expand an organization’s attack surface and increase the likelihood of severe security incidents, including data breaches. The prevalence of IAM risks points to the growing need for a faster, more manageable, and more secure way of provisioning access to both non-human and human identities.
Orca is pleased to announce a new feature that does just that. With Just-in-Time (JIT) Access, security teams can grant temporary, least-privilege access to specific cloud assets—quickly and easily. This gives organizations a powerful way to reduce standing permissions, enforce least privilege, and better control identity sprawl across their environments.
What is Just-in-Time (JIT) Access?
JIT Access is a cloud security methodology and capability designed to enforce the principle of least privilege and significantly reduce unnecessary access to environments. It grants both human and non-human identities limited access to specific applications or systems for a set period of time.
The Orca Cloud Security Platform’s JIT capability enables organizations to adopt and apply this methodology efficiently and effectively, allowing admins to grant temporary, time-bound access to specific cloud resources with a specific set of permissions. Access is only given when requested and only for the duration required—enforcing least privilege by default and eliminating unnecessary standing permissions.
Why is Orca releasing JIT Access?
Conventional identity access models rely on static, always-on permissions. While intended to streamline access, these standing permissions often outlive their usefulness—especially when tied to inactive or forgotten roles. Left unchecked, they create opportunities for privilege misuse, lateral movement, and data exposure.
Orca’s JIT Access provides a superior, more flexible alternative. Rather than defaulting to persistent access, it allows teams to grant short-term, purpose-specific permissions on demand. This modern approach enforces least privilege by default and reduces identity-related risk across dynamic cloud environments.JIT Access further enhances the advanced and comprehensive Cloud Infrastructure Entitlement Management (CIEM) capabilities of the Orca Cloud Security Platform. It gives security teams the visibility, context, and control needed to provision secure access—without slowing down users or overloading administrators
Key capabilities of JIT Access
Orca’s JIT Access offering offers four key features to users, including:
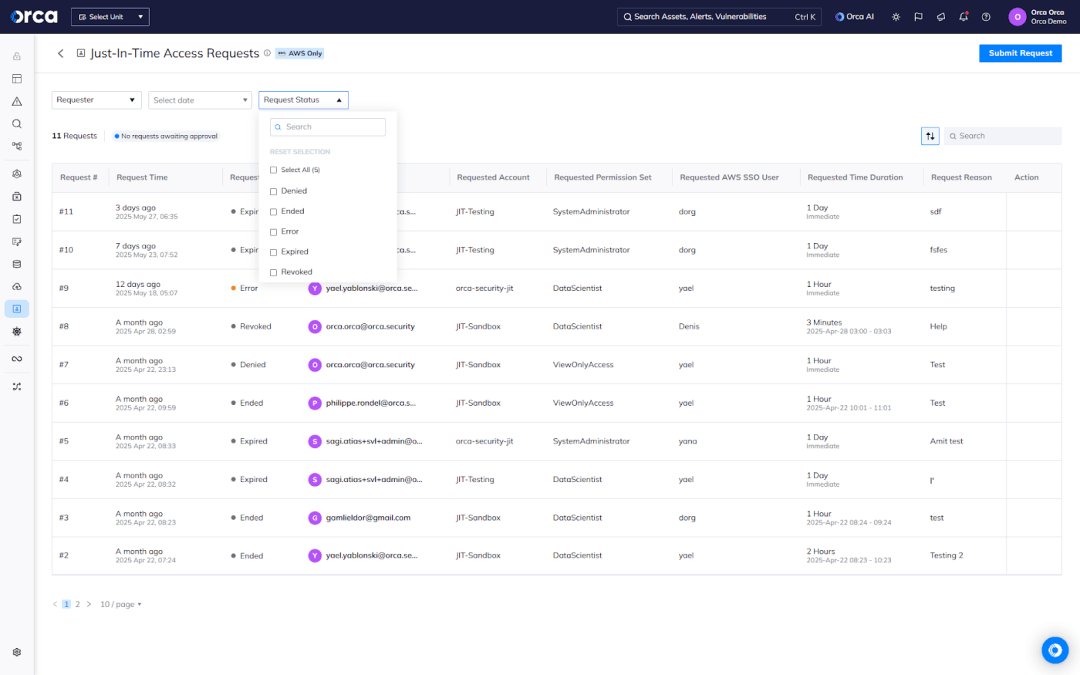
#1. Centralized management of JIT requests
Managing JIT access can be time-consuming, especially when using disjointed tools or manual processes.
Orca provides a centralized interface for viewing and managing JIT requests. Admins can see each request’s date, time, status, requested permissions, duration, requester, and more. They can take action directly in the interface and use filters to quickly find relevant requests, making it fast, efficient, and scalable to manage JIT access.
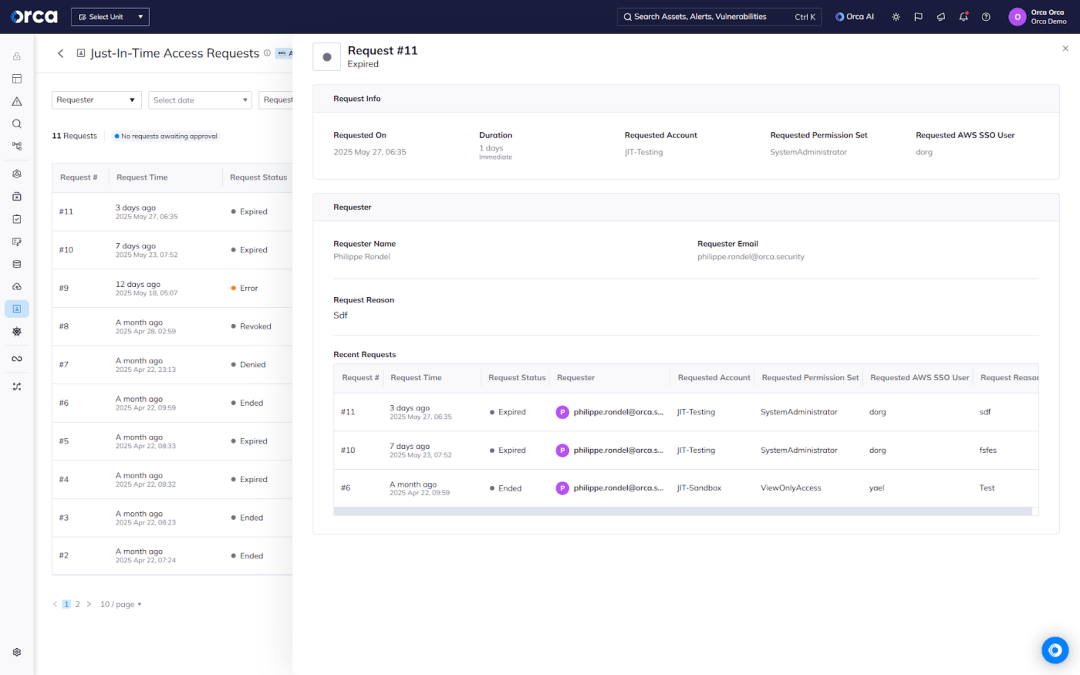
#2. Full context for each request
When access requests lack context, admins may hesitate—or worse, approve excessive access without knowing the full picture.
Using Orca, admins can view the full context of any JIT access request to streamline and enhance decision-making. By clicking any JIT request, admins can view the request number, permissions, duration, requester (name, email, role, reason for request), and the requester’s history. The latter shows the user’s five most recent requests and their associated details. This ensures admins can make informed, on-the-fly decisions that also account for historical context.
#3. Detailed audit logs for compliance and oversight
While JIT access reduces risk, it still requires oversight to ensure it’s being used appropriately. Many teams lack the audit capabilities to validate and document access decisions.
Orca’s JIT Access feature maintains detailed audit logs of all JIT access and activity, including all instances of JIT access that ended due to session expiration, manual revoking, and other conditions. Orca also makes it seamless to query this information. Orca’s extensive tracking and detailed audit capabilities enable organizations to continually validate the efficacy of their JIT access program with internal and external stakeholders.
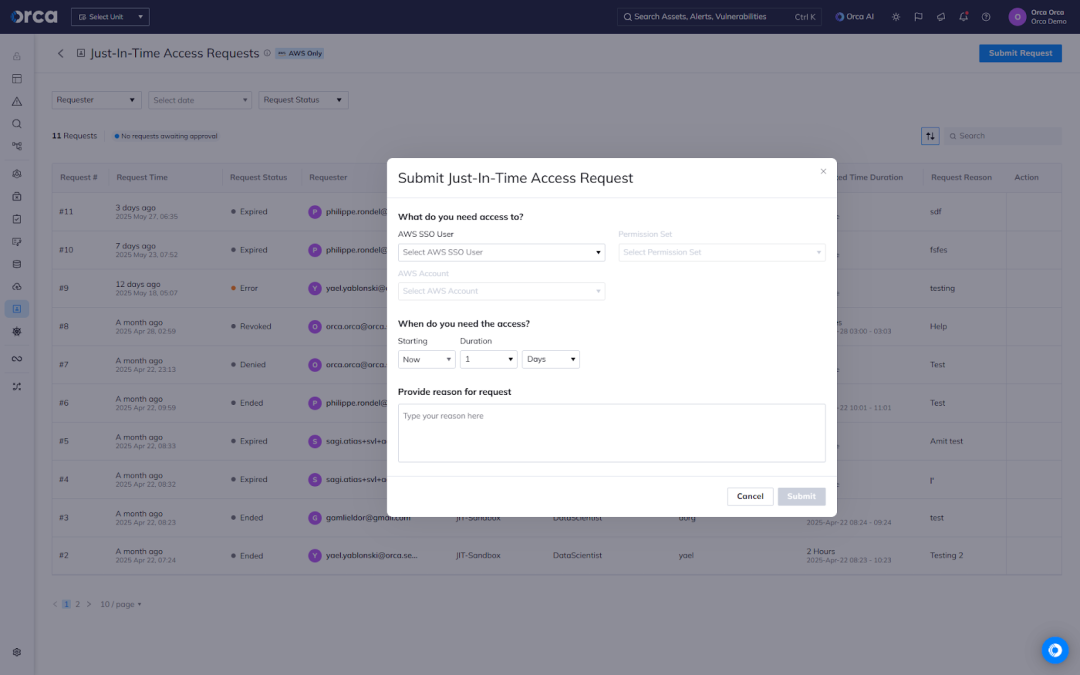
#4. Flexible request workflows, including Slack integration
Not all users—especially third-party contractors or auditors—have direct access to the cloud security platform. Without flexible request options, admins are forced to use manual workarounds.
JIT requests can be submitted directly from the Orca Platform or through Slack using Orca’s bidirectional integration. This supports a wide range of users and use cases, including developers and third parties who may not have direct access to the platform. Requesters can track their request status in Slack, while admins receive real-time notifications.
Aligning with our integration-first approach, Orca remains committed to accommodating the workflows and tools your teams currently use, empowering them with advanced security intelligence and capabilities for improved efficiency and effectiveness.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ Technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform, including its capabilities for JIT Access? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can expedite and enhance your CIEM.






