According to the Orca 2025 State of Cloud Security Report, 70% of organizations now use Kubernetes (K8s) in their cloud environments. Yet despite its widespread adoption, Kubernetes continues to pose significant security challenges. The report found that 50% of organizations using K8s run at least one unsupported cluster version, and 93% have overprivileged service accounts, which attackers can exploit to escalate privileges, access sensitive data, or disrupt the cluster.
To help organizations address these risks more effectively, Orca is enhancing its Platform with Cloud-to-Dev tracing for Kubernetes assets deployed via Helm Charts. This new enhancement enables security teams to connect running K8s resources—such as clusters, pods, secrets, config maps, and more—directly to their code origins. With this context, teams can quickly trace security risks back to the source, accelerate remediation, and improve collaboration with development.
Understanding Kubernetes and Helm
Kubernetes is an open-source platform designed to automate the deployment, scaling, and management of containerized applications, allowing workloads to run consistently across clouds and environments—critical for cloud-native architectures and multi-cloud strategies.
Most organizations manage Kubernetes applications using Helm, the widely adopted package manager for Kubernetes. Helm Charts act as reusable, version-controlled deployment blueprints composed of YAML templates and configuration files, enabling teams to deploy complex applications efficiently through Infrastructure as Code (IaC). This makes Helm integral to modern DevOps workflows.
However, the efficiency and convenience of Helm can amplify the impact of security risks. For instance, a single misconfiguration in a Helm Chart template could propagate rapidly across many deployments. Helm Charts obtained from untrusted or inadequately vetted third-party repositories might introduce critical vulnerabilities and misconfigurations, increasing the potential attack surface. While Helm greatly simplifies Kubernetes management, teams must remain vigilant to maintain secure configurations.
How Orca secures Kubernetes
The Orca Cloud Security Platform delivers comprehensive Kubernetes protection through its Kubernetes Security Posture Management (KSPM) and Container Security capabilities. With agentless-first visibility into every layer of a K8s environment—including clusters, worker nodes, control plane components, containers, and pods—Orca enables teams to detect, prioritize, and remediate risks with minimal operational overhead.
Now, with Cloud-to-Dev tracing for Helm-deployed resources, Orca takes Kubernetes Security a step further. By linking runtime insights with the development artifacts that created them, Orca gives security teams the context they need to work faster and more effectively across the entire application lifecycle.
What does this feature include?
This latest enhancement to the Orca Platform provides security teams with new capabilities.
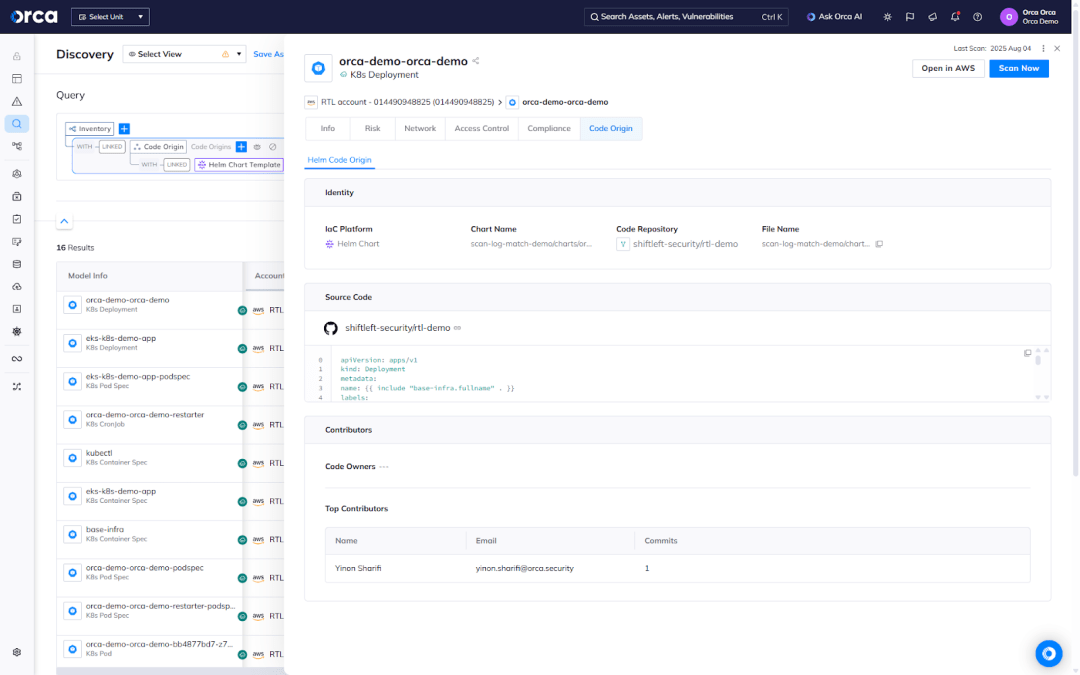
Trace running Kubernetes assets to their origins in Helm
Challenge: When a risk is detected in production—such as a misconfigured pod or exposed secret—it can be time-consuming to determine its origin and identify the developer responsible for remediation.
Solution: Orca’s Cloud-to-Dev capability automatically maps K8s assets that originated from Helm Charts to their precise definition in code. This includes:
- The originating Helm Chart and Helm resource.
- The file name and code lines where the asset is defined.
- The appropriate source code repository and code owner(s).
This level of traceability enables security teams to quickly collaborate with developers, reduce mean time to remediation (MTTR), and ensure accountability.
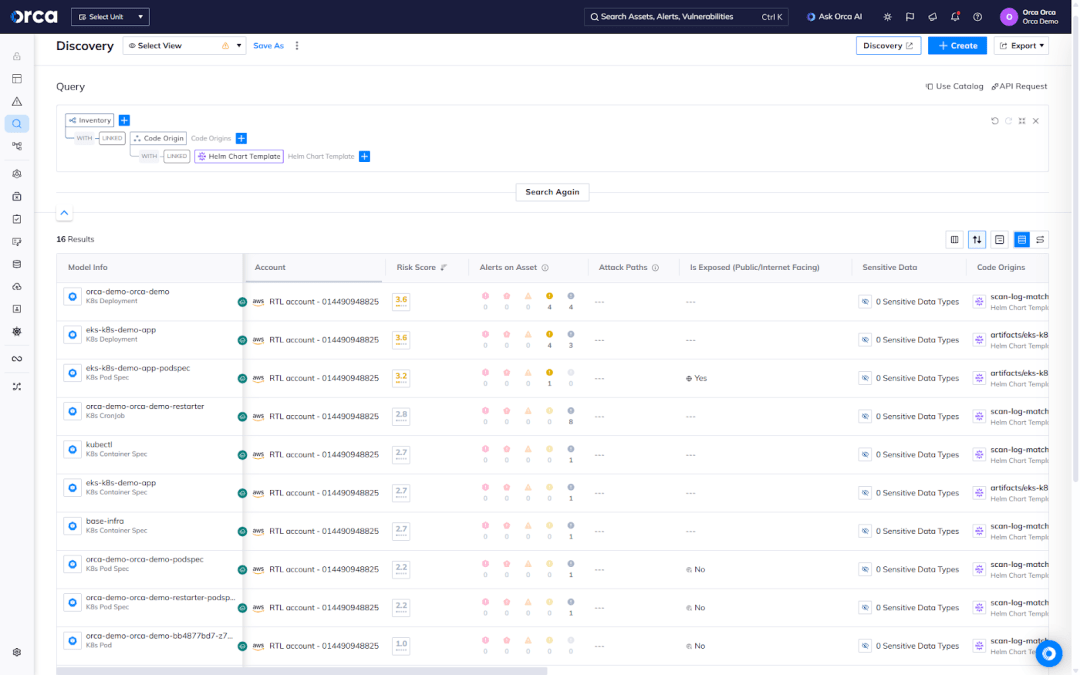
Inventory all K8s resources per Helm Chart or Helm Chart template
Challenge: When a security risk is discovered in a Kubernetes resource, it’s rarely an isolated issue. In many environments, a single Helm Chart or template is reused across multiple deployments, meaning a single risk can easily multiply in a runtime context. Without a way to see all running K8s resources deployed from a specific Helm Chart or template, security teams struggle to understand the full scope of a misconfiguration, vulnerability, or other risk.
Solution: Using Orca’s Discovery view, users can immediately inventory all running K8s resources deployed from a specific Helm Chart. This helps security teams assess the full impact of a risk linked to a particular Chart. With this complete Cloud-to-Dev context in one place, teams can quickly assess their risk exposure and streamline remediation.
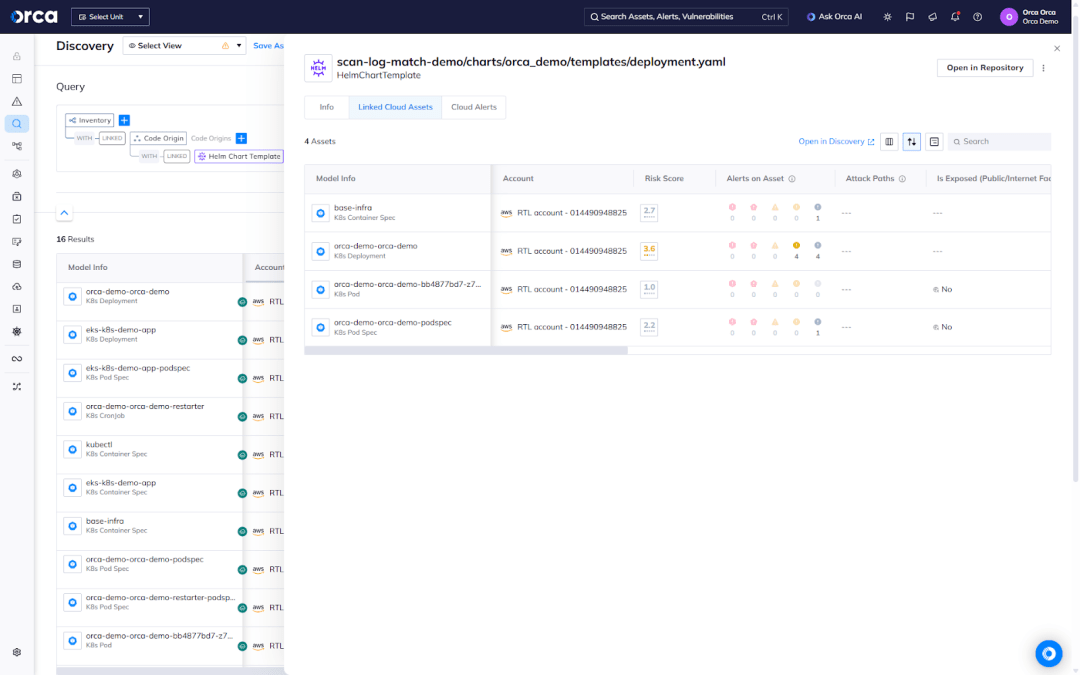
Additionally, Orca enables users to view all running K8s resources generated from a Helm Chart template, providing critical insight into how a single templated definition is used across the environment. Since these templates are often reused within and across Helm Charts, identifying all assets tied to a specific template enables teams to pinpoint systemic misconfigurations, assess their runtime footprint, and prioritize remediation at the source before issues can proliferate.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform and its Cloud-to-Dev capabilities for Kubernetes? Schedule a personalized 1:1 demo.






