Table of contents
Kubernetes, also known as K8s, is an open source container orchestration platform for the management of containerized applications. Hosted by the Cloud Native Computing Foundation (CNCF), Kubernetes has become a popular choice for container orchestration due to its scalability, flexibility, and ease of use.
Despite the speed and agility Kubernetes offers, it comes with important security concerns and challenges. In a Kubernetes environment, security threats can arise from misconfigured clusters, unauthorized access, insecure container images, and more. These security concerns appear to be widespread for organizations leveraging Kubernetes. According to Orca’s 2024 State of Cloud Security Report, 82% of organizations have a publicly-accessible Kubernetes API server. This critical exposure can allow attackers to modify resource states and potentially breach underlying infrastructure, containers, and more. Kubernetes Security Posture Management (KSPM) aims to solve security risks such as these by implementing and sustaining the proper security measures.
In this post, we dive deep into the topic of KSPM, defining what it entails, why organizations need it, common risks and security threats, best practices, and more.
What is Kubernetes Security Posture Management (KSPM)?
Kubernetes Security Posture Management (KSPM) is a comprehensive approach to managing and maintaining the security of Kubernetes deployments. It involves implementing various security measures, such as securing cluster configurations, ensuring access control, protecting container images, and more.
KSPM solutions are designed with a deep understanding of the intricacies of the Kubernetes core platform and its various extensions across the ecosystem. Whether organizations use different distributions, hosted services, or local deployments of Kubernetes, a KSPM solution can establish a consistent baseline to enhance Kubernetes security effectively. This includes enforcing internal policies such as naming conventions and adhering to industry-standard best practices outlined in the CIS Kubernetes Benchmarks.
By adopting KSPM, organizations can proactively identify and remediate security risks, prevent unauthorized access, and maintain a robust security posture. Kubernetes Security Posture Management helps ensure the confidentiality, integrity, and availability of resources within the Kubernetes environment, protecting sensitive data, and preserving the overall integrity of the system.
Kubernetes uses a cluster architecture to run. A cluster consists of a master node with one or more worker nodes running containerized applications. Each worker node can have one or more pods, and each pod can have one or more containers. The master node manages the worker nodes and the pods. The master node sits inside a host, while one or more hosts run the worker nodes. The worker nodes contain the pods that have containers.
KSPM protects the host running the master node, the host(s) running worker nodes, and all the containers running inside of the worker nodes. At a minimum, it involves:
- Properly configuring and hardening all Kubernetes components according to CIS Kubernetes benchmarks.
- Detecting and remediating the vulnerabilities in all Kubernetes components.
- Using encryption.
- Mitigating IAM risk across the Kubernetes cluster.
Common Kubernetes risks and challenges
Kubernetes plays a crucial role in many cloud-based applications, providing a flexible and scalable platform for running and managing applications in the cloud. While it provides substantial benefits, the orchestration platform also presents a variety of security risks.
Among those security risks are those included in the OWASP Kubernetes Top 10 list, which details the most important security risks for organizations using Kubernetes. OWASP (Open Web Application Security Project) is a non-profit organization focused on enhancing software security, providing numerous resources on how to detect and address vulnerabilities.
Below, we examine the types of risks associated with Kubernetes.
Kubernetes misconfigurations
Kubernetes provides several controls that can help organizations effectively secure clusters and applications. While useful, it doesn’t provide secure configurations out-of-the-box or adequate default configuration rules. Kubernetes prioritizes speed and agility at the expense of security.
Many of Kubernetes configurations provide open access and permissions by default. For example, it doesn’t segment pods, allowing any pod to communicate with another one in the Kubernetes environment. This gives attackers the freedom to laterally move and launch multi-phased attacks after an initial compromise. It also illustrates the importance of defining network policies for all cluster resources prior to deployment.
Improper secrets management is another common risk with Kubernetes. Secrets define how keys, credentials, and other sensitive information is accessed and stored. To avoid creating a security risk, organizations shouldn’t hard-code secrets within container images or use them as environment variables. Instead, they should guard them with strict access controls and manage them externally.
Insecure transport controls
When it comes to self-managed Kubernetes clusters, it’s not enough to secure clusters. Organizations need to also set proper security measures for data in transport, which often gets overlooked and can expose data to malicious actors.
To help prevent potential attackers from intercepting or manipulating network traffic, organizations should allow encrypted connections over TLS when configuring communication in the cluster between services. This helps prevent successful man-in-the-middle (MiTM) attacks and similar exploits.
Etcd is another important consideration. Etcd is an open-source, distributed key-value store for the critical information that distributed systems need to keep running. Most notably, etcd manages Kubernetes configuration data, state data, and metadata. These sensitive objects should be encrypted in transit.
Lack of visibility into Kubernetes
When it comes to security, you can only protect what you can see. That explains a significant security concern with Kubernetes. Achieving visibility is challenging in distributed, complex, and containerized environments.
For one, cloud service providers offer their own inventory and monitoring tools, making multi-cloud visibility challenging. Additionally, the rate and scale of container development makes monitoring it difficult, with many containers being scheduled, deployed, and terminated. Meanwhile, the distributed and dynamic nature of containerized workloads makes it challenging to collect data.
The more containers that get deployed, the more challenging it becomes to gain or maintain visibility into cloud-native infrastructure. More concerning, however, is that containers often become unmaintained and neglected assets, leaving them susceptible to anomalous activity, out-of-date applications, or a lack of security components.
Supply chain vulnerabilities
Speaking of containers, they depend on a multitude of third-party dependencies and components that present significant security risks for Kubernetes. These dependencies can introduce known software vulnerabilities, taint image integrity, or container images that increase your attack surface and increase the chances attackers can escalate privileges after a compromise or exploit known vulnerabilities.
Unified policy enforcement
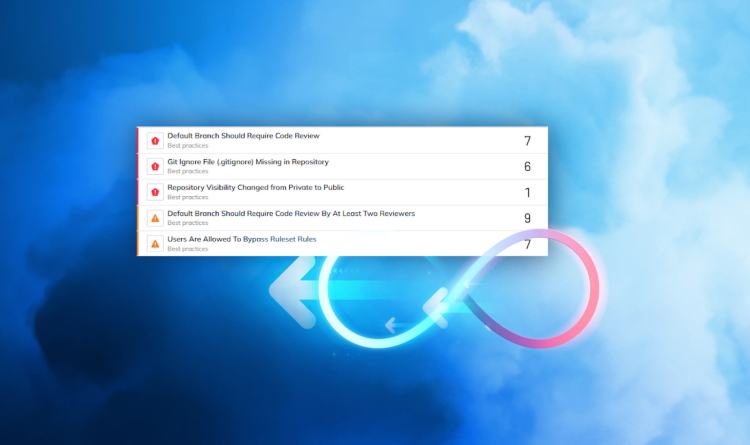
Security teams often lack the ability to set, manage, and enforce security policies across their sprawling cloud estates and Kubernetes environments. This occurs when teams lack a centralized, unified dashboard for detecting, prioritizing, and remediating misconfigurations. As a result, security teams often can’t effectively secure clusters, leaving them open to exploitation.
Secrets management
When it comes to Kubernetes, a “secret” is a sensitive piece of information such as a password or token. Secrets in Kubernetes play a valuable role, allowing you to keep your confidential data separate from your application code. Unfortunately, Kubernetes misconfigurations and default settings put secrets at risk. For example, Kubernetes creates secrets like any other object and does not encrypt them by default. If checked into a source code management platform like GitHub or GitLab, this creates the risk of secrets leaking to unwanted locations.
Vulnerabilities
Like any other cloud system, Kubernetes contain vulnerabilities that attackers can exploit. Yet due to the complexity of this digital ecosystem, and its significant dependency on third-party components, security teams find it difficult to effectively support patch management and vulnerability management functions in Kubernetes.
Cloud Native Application Protection Platform (CNAPP)
In addition to providing KSPM and container security capabilities, Cloud-Native Application Protection Platforms (CNAPP) also provide additional protections needed to fully secure your Kubernetes deployments. This includes the ability to detect vulnerabilities, IAM risk, malware, sensitive data, and other risks across containers, worker nodes, and master nodes. Equally important, advanced CNAPP solutions can extend these capabilities to components in development and production environments.
KSPM best practices
To make the most of Kubernetes Security Posture Management and ensure robust security for your Kubernetes deployments, consider implementing the following best practices:
1. Leverage proper configuration and continuous monitoring
Focus on configuring your Kubernetes clusters securely, following best practices such as enabling encryption, using strong passwords, and applying the principle of least privilege (PoLP). Continuously monitor your clusters to detect any security vulnerabilities or configuration drifts. Additionally, utilize Kubernetes to gain visibility into container performance and security metrics. And leverage Kubernetes audit logging to track activities generated by users, applications using the Kubernetes API, and the Kubernetes cloud plane. This enables you to track container activity and detect any suspicious or unauthorized behavior.
2. Adopt a CNAPP
CNAPPs provide additional protections needed to fully secure your Kubernetes deployments. CNAPPs augment and extend the capabilities of KSPM to cover important security gaps. This includes the ability to detect vulnerabilities, IAM risk, malware, sensitive data, and other risks across containers, worker nodes, and master nodes. Equally important, advanced CNAPP solutions can extend these capabilities to components in development and production environments.
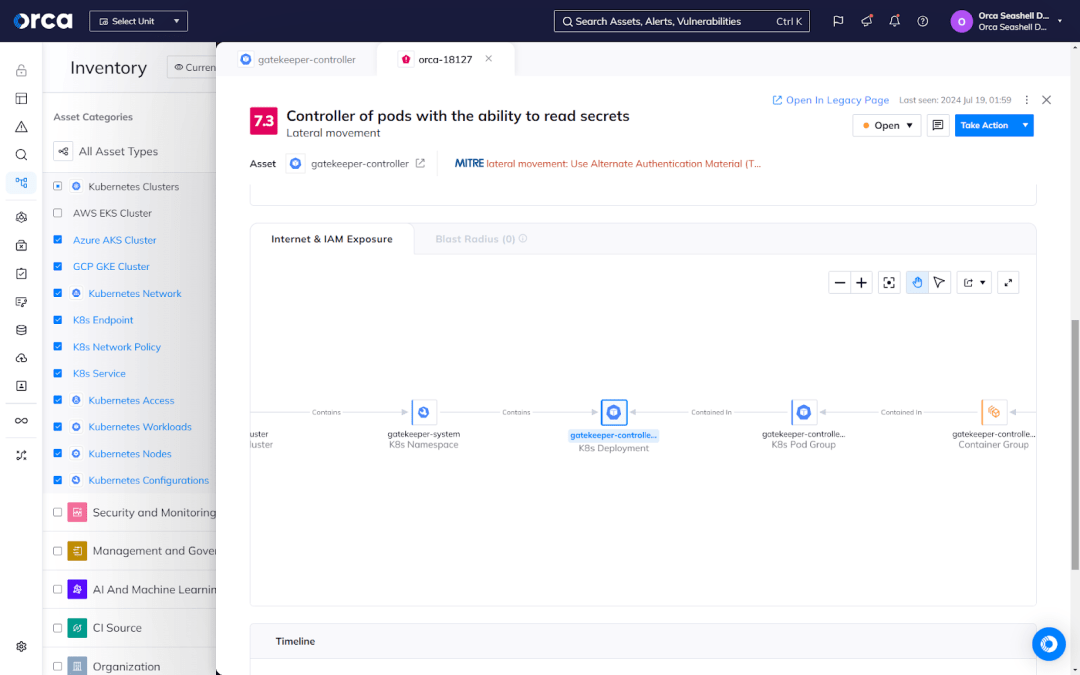
For example, the Orca Cloud Security Platform provides complete coverage of your entire cloud estate, including your Kubernetes deployments. Together with comprehensive risk detection, the Orca Platform effectively prioritizes risks and detects hidden attack paths between assets and risks that attackers may exploit to endanger high-value assets. This enables your team to stay on top of every critical risk, reduce alert fatigue, and boost productivity.
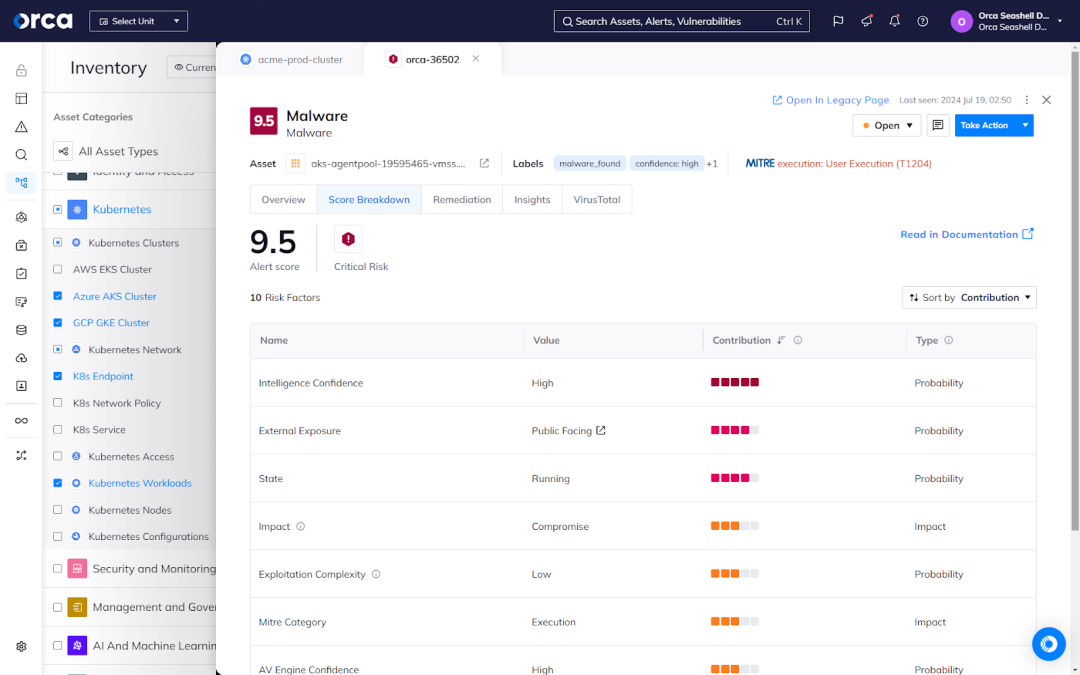
3. Conduct regular vulnerability assessments and penetration testing
Run regular vulnerability assessments and penetration testing to detect security flaws in your Kubernetes environment. This enables you to identify and remediate issues before threat actors can exploit them.
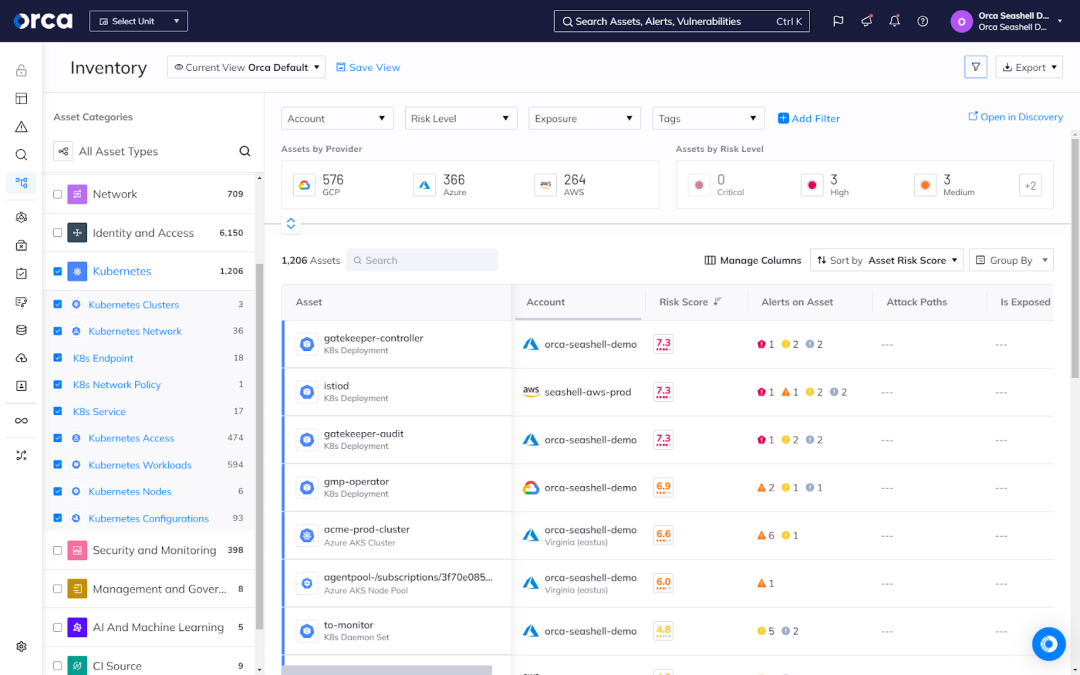
Orca allows you to continuously monitor and remediate your critical and high-risk vulnerabilities across your cloud estate, including your Kubernetes environments. From Orca’s Vulnerability Management dashboard, you can quickly review vulnerabilities by severity, asset type, SLA widgets, and more. You can also view a prioritized list of vulnerabilities and at-risk assets.
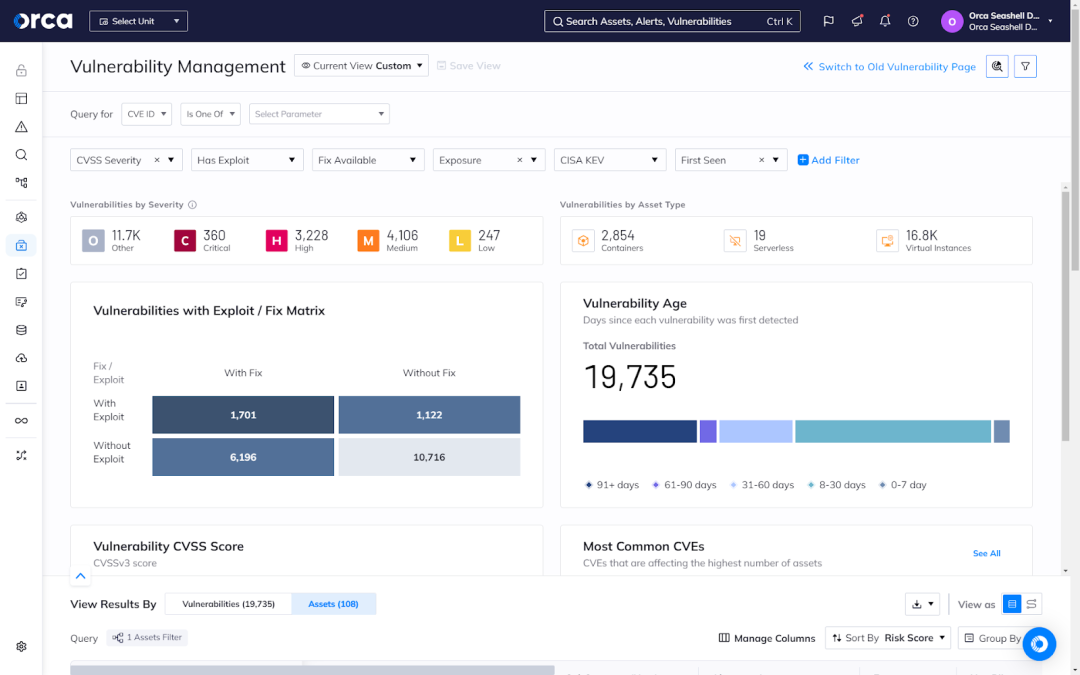
4. Maintain timely updates and patch management
Implement a robust patch management process to protect against emerging threats. As part of this process, regularly apply patches and security updates to your Kubernetes components, including the control plane and worker nodes. Also, routinely update container images and promptly address any known vulnerabilities.
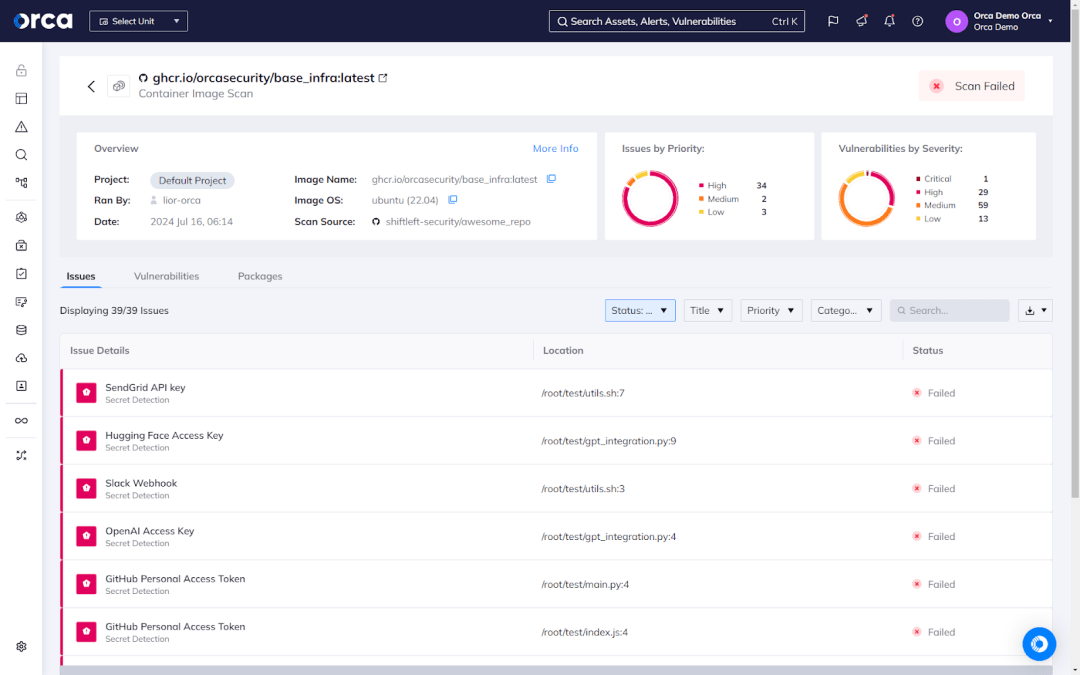
As part of its Shift Left Security solution, the Orca Platform continually scans your container images for vulnerabilities and prioritizes detected risks by severity. Orca also enables you to isolate and view vulnerabilities by image layer for targeted remediation.
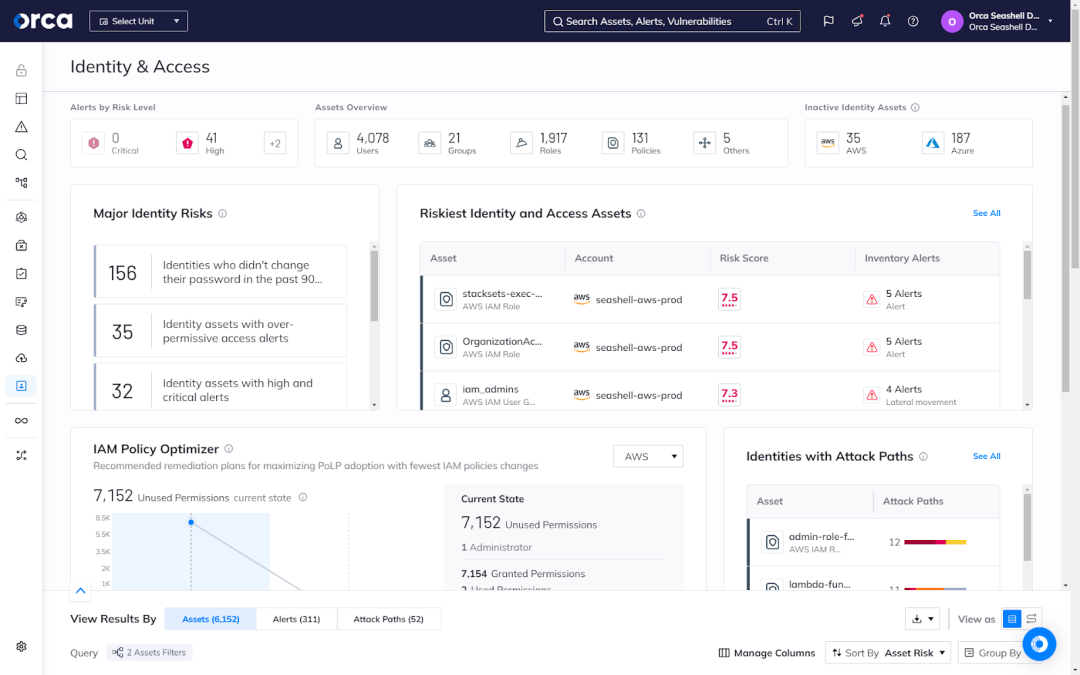
5. Implement Role-Based Access Control (RBAC) and robust authentication
Leverage role-based access control mechanisms to manage access and permissions within your Kubernetes environment. Enforce strong authentication mechanisms such as multi-factor authentication (MFA) or certificate-based authentication to fortify the security of user identities.
Orca’s Cloud Infrastructure Entitlement Management (CIEM) solution provides deep and contextualized visibility into all identities, configurations, access policies, entitlements, permissions, and activities in your cloud estate. This includes your multi-cloud environments and Kubernetes deployments. Orca automatically detects and prioritizes your most time-sensitive IAM risks, allowing you to expedite remediation and limit the potential for exploitation.
6. Follow other Kubernetes best practices
Kubernetes offers numerous security features that provide significant benefits, such as protections for sensitive data, workload isolation during runtime, granular access controls, and more. To ensure you take advantage of Kubernetes built-in controls, consult Center for Internet Security (CIS) Kubernetes benchmarks.
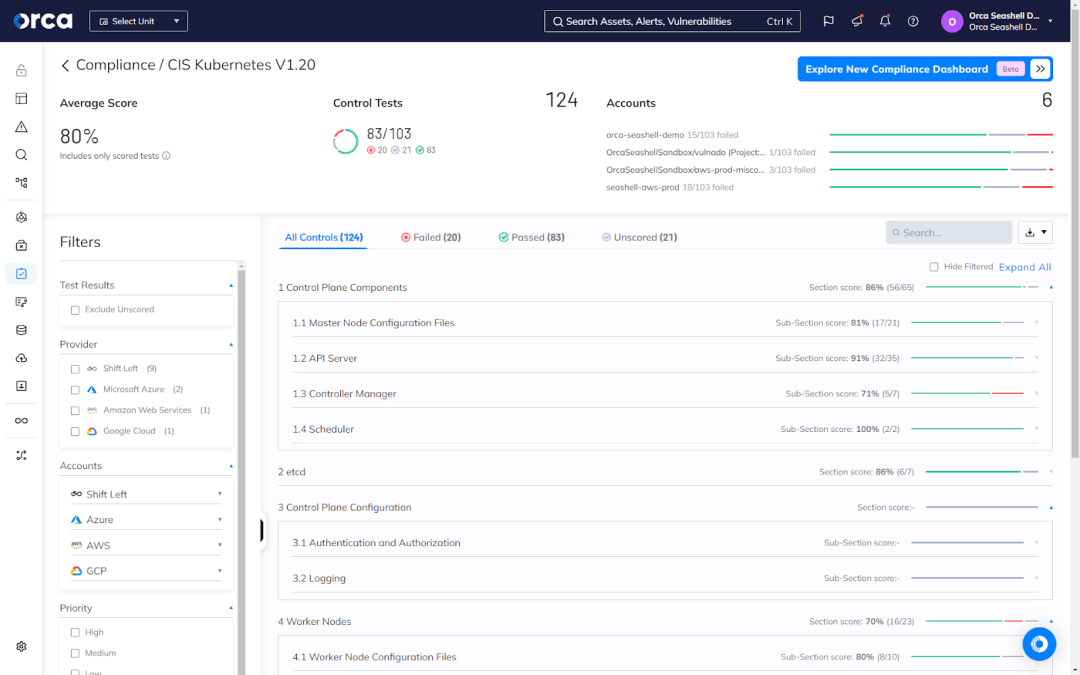
Advanced CNAPPs provide the ability to automatically track and monitor compliance against important frameworks for Kubernetes best practices, including CIS Kubernetes benchmarks. When available, this product feature offers significant value, enabling your team to continuously track adherence to best practices and address out-of-compliance issues in a timely manner.
As part of Orca’s Multi-Cloud Compliance solution, the Orca Platform offers a built-in compliance framework for meeting CIS Kubernetes benchmarks. This framework automatically detects, prioritizes, and alerts on issues out of compliance with CIS standards, enabling your team to efficiently address issues on a continuous basis. This helps prevent compliance drift or limits your security risks.
7. Leverage automation
In addition to automated and continual monitoring capabilities, some CNAPPs also offer valuable features to accelerate critical tasks across your workflows. Best practice is to leverage any automated features including the ability to auto-remediate security risks and compliance issues, leverage integrations to easily delegate tasks in common developer tools, schedule and send recurring reports on the status of your Kubernetes Security Posture Management, and more.
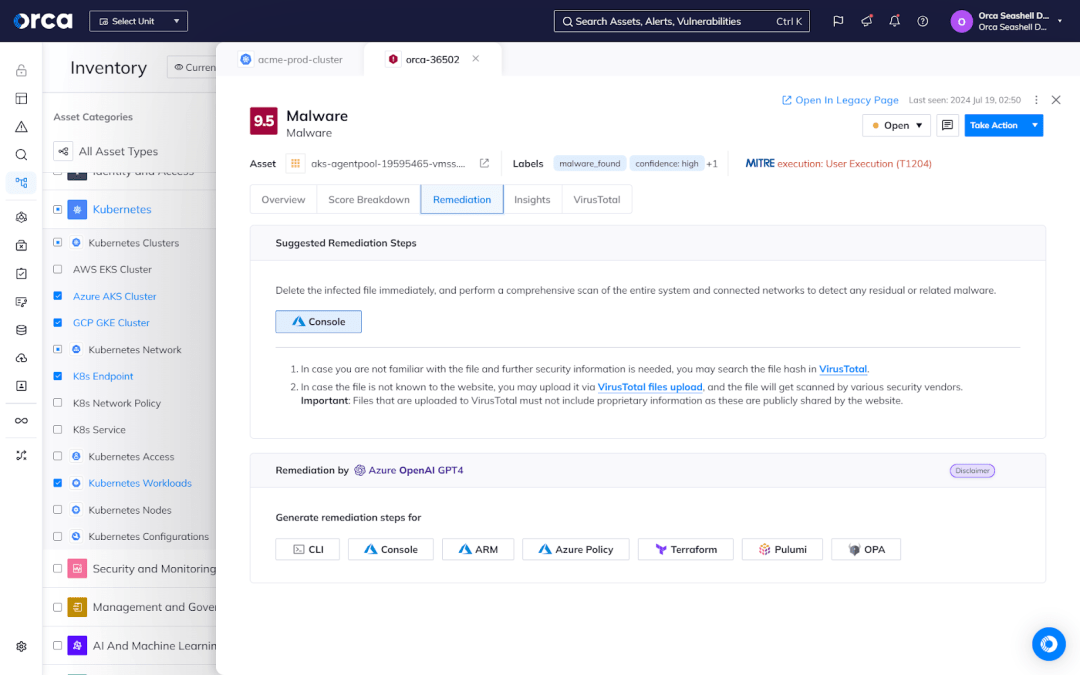
For example, the Orca Platform provides several features for automation and greater efficiency. For remediation, Orca generates recommended remediation instructions, the ability to auto-remediate certain risks, and AI-powered remediation, which automatically generates remediation instructions and code according to your specific remediation process.
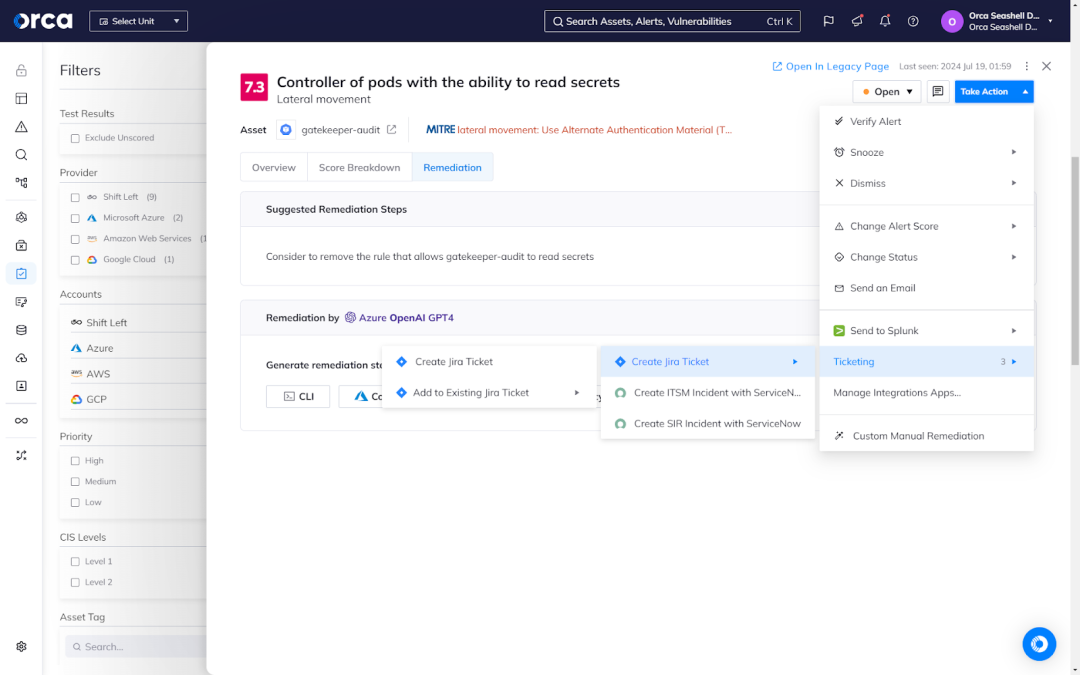
Additionally, Orca maintains more than 50+ technical integrations which support or facilitate automation. This includes Orca’s two-way integrations with Jira and ServiceNow, which enable security teams to create, monitor, and verify tickets from the Orca Platform. This enables them to assign remediation tasks to the appropriate developer without forcing them to learn or use another tool. The Orca Platform also automatically verifies issue resolution every time a ticket is closed, and reopens the ticket in the event the issue still persists.
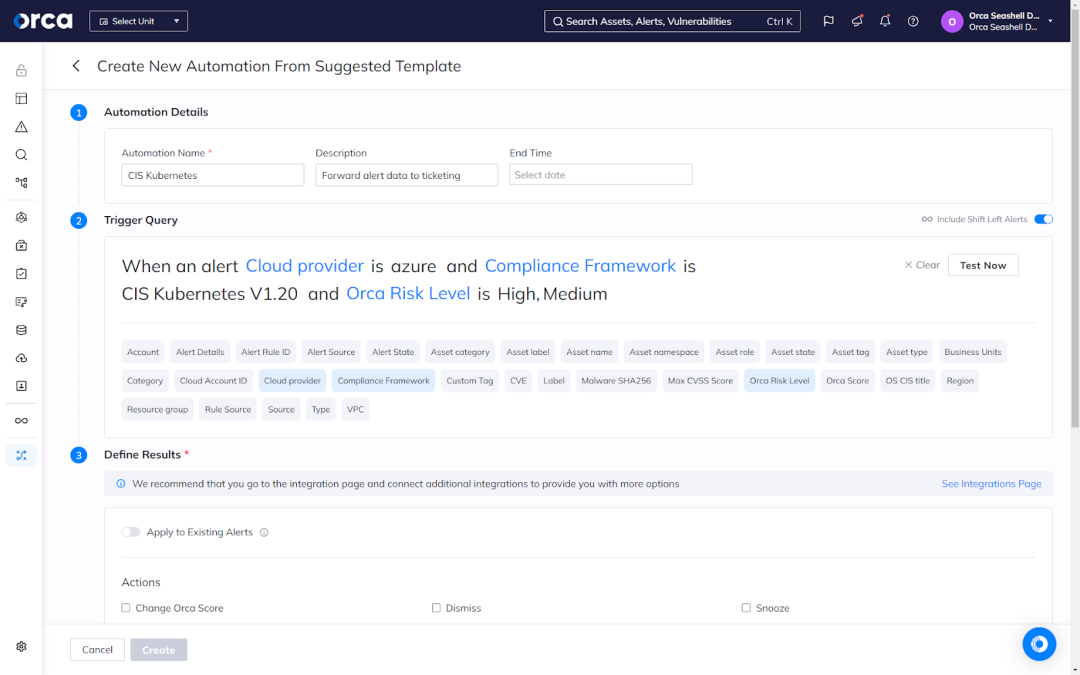
Additionally, Orca provides the ability to build automated workflows that complete tasks on behalf of your team. This includes sending notifications across applications, assigning alerts to the appropriate teams, and more. Orca’s automations streamline compliance efforts and augment the time, capacity, and skill requirements of your team.
8. Administer education and training
Regularly educate and train your personnel on KSPM best practices. Validate that they understand security policies and procedures and the importance of adhering to them. Also, ensure they can recognize potential security threats and follow secure coding practices. By fostering a culture of security vigilance, you can significantly reduce the risk of security breaches.
Implementing these practices help you leverage the full potential of KSPM to protect your deployments. Once implemented, continue to review and update these practices to ensure they protect against the evolving threat landscape.
KSPM vs. CSPM
You may question the difference between KSPM and another foundational cloud security technology: Cloud Security Posture Management (CSPM). Both cloud security solutions secure the infrastructure of the environments they protect. This involves detecting and mitigating misconfigurations, enforcing native security policies, ensuring full coverage and visibility of the infrastructure, and facilitating compliance with relevant regulatory standards and frameworks. Yet CSPM secures cloud-native environments (e.g., AWS, Azure, Google Cloud), while KSPM covers Kubernetes deployments. For this reason, KSPM and CSPM are complementary solutions without redundancies.
About the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first CNAPP that identifies, prioritizes, and remediates security and compliance risks across multi-cloud environments supported by AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
From one unified solution, the Orca Platform natively integrates and provides Kubernetes Security Posture Management (KSPM), Shift Left Security, CSPM, CWPP, CIEM, DSPM, API Security, AI Security Posture Management (AI-SPM), Multi-Cloud Compliance, Vulnerability Management, and more. Orca leverages our patented SideScanning™ technology to maintain complete coverage across your entire cloud estate and comprehensive risk detection.
Orca’s deep and complete visibility into your cloud estate enables it to contextualize risks and uncover hidden, interrelated issues that present dangerous attack paths. As a result, the Orca Platform effectively prioritizes risks and ensures your teams can move past alert fatigue to focus on their most critical tasks.
See how the Orca Cloud Security Platform enhances your cloud security by scheduling a personalized demo with one of our experts.
Conclusion
Kubernetes Security Posture Management is essential for organizations using Kubernetes, the open-source orchestration platform. This security solution enables organizations to protect their Kubernetes environments and ensure the confidentiality, integrity, and availability of all resources residing with them. Yet complete and comprehensive KSPM requires you to look beyond traditional solutions and adopt more comprehensive platforms, such as an advanced CNAPP.
FAQs
What is Kubernetes?
Kubernetes is an open source platform that helps organizations manage and deploy containerized applications at scale, including their workloads and services. Kubernetes, also referred to as K8s, was first developed by Google and is hosted by the Cloud Native Computing Foundation (CNCF). Kubernetes is used by many organizations for container orchestration due to the scalability, flexibility, and ease of use of the technology.
What is a KSPM tool?
KSPM solutions are designed with a thorough understanding of Kubernetes and the complexity of its ecosystem. KSPM solutions provide a uniform standard to bolster Kubernetes security. This involves enforcing internal policies like naming conventions and following industry best practices as defined in the CIS Kubernetes Benchmarks.
By adopting KSPM, organizations can proactively detect and remediate security risks, while also fortifying their security posture. KSPM enables organizations to protect the confidentiality, integrity, and availability of resources within the Kubernetes environment.
What roles generally use KSPM?
Security teams leverage KSPM solutions to rely on CSPM tools to identify and remediate misconfigurations that put their Kubernetes deployments and environments at risk. While KSPM impacts developers, security professionals are the primary users of KSPM technology.
Who needs KSPM?
Every organization that uses Kubernetes needs a KSPM solution. This ensures that they can properly secure their Kubernetes infrastructure and configurations. Cloud Native Application Protection Platforms (CNAPP) provide KSPM capabilities. CNAPPs that provide Kubernetes security natively offer the most enhanced protection for KSPM.