As more organizations adopt containerized infrastructure, the need for effective security practices becomes increasingly important. Recently released by the OWASP community, the Kubernetes Top 10 list provides a set of guidelines and best practices specifically designed to help practitioners identify and mitigate common security risks in their Kubernetes deployments.
In this blog post, we will take a closer look at the OWASP Top 10 for Kubernetes and explore some of the key concepts that practitioners can use to improve the security of their containerized infrastructure. Whether you’re new to Kubernetes or an experienced practitioner, this guide will provide you with valuable insights for securing your deployments with Orca Security.
What is Kubernetes?
Kubernetes (K8s) is an open-source container orchestration system that automates the deployment, scaling, and management of containerized applications. It is designed to be used in conjunction with cloud platforms, such as GCP, AWS and Azure, to enable the deployment and management of applications at scale.
By using Kubernetes, developers can focus on building their applications without having to worry about the underlying infrastructure, allowing them to more quickly and easily deploy and update their applications. As a result, Kubernetes plays a crucial role in many cloud-based applications, providing a flexible and scalable platform for running and managing applications in the cloud.
What is OWASP?
OWASP (Open Web Application Security Project) is a non-profit organization that aims to improve the security of software. It provides a range of resources to help organizations identify and address vulnerabilities, including the OWASP Top 10 list of the most significant web application security risks. In addition to the Top 10 list, OWASP offers a testing guide, a guide to secure coding practices, and a list of automated testing tools which can be found here: https://owasp.org/www-project-web-security-testing-guide/latest/6-Appendix/A-Testing_Tools_Resource. By utilizing these resources, organizations can strengthen the security of their applications and protect against cyber threats.
OWASP Kubernetes Top 10
The OWASP Kubernetes Top 10 is a list of the most important security risks for organizations using Kubernetes.
The Top 10 Risks:
- K01:2022 Insecure Workload Configurations
- K02:2022 Supply Chain Vulnerabilities
- K03:2022 Overly Permissive RBAC Configurations
- K04:2022 Lack of Centralized Policy Enforcement
- K05:2022 Inadequate Logging and Monitoring
- K06:2022 Broken Authentication Mechanisms
- K07:2022 Missing Network Segmentation Controls
- K08:2022 Secrets Management Failures
- K09:2022 Misconfigured Cluster Components
- K10:2022 Outdated and Vulnerable Kubernetes Components
This list helps security professionals, system administrators, and developers understand and prioritize these risks. The list is based on data from various types of organizations. Its purpose is to help organizations identify and address critical security risks in their Kubernetes environments. More can be found in the link below:
https://owasp.org/www-project-kubernetes-top-ten/
Kubernetes Security Risks
Like any system that is connected to the Internet, Kubernetes holds cyber risks which must be addressed and mitigated. Two of the major risks are:
1. Insecure Configuration: Kubernetes misconfigurations can result in different types of attacks such as unauthorized access, privilege escalation, denial of service and more. These attacks can be made possible when components like the kubelet or etcd are misconfigured and allowing unauthorized access, for example, the TeamTNT attack group has targeted kubelets which were exposed through the network.
Detecting the risk with Orca:

Misconfigurations on etcd database can result in access to sensitive information or performing unauthorized operations.
Orca example detection:
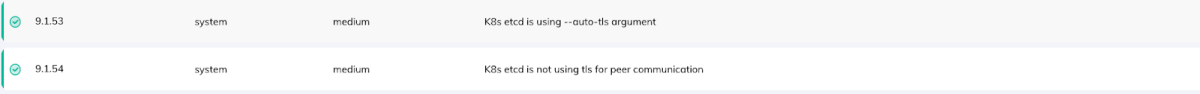
2. Network Misconfigurations: The outcome of Kubernetes network misconfigurations can be critical in cases of unencrypted communications between different K8s components which may result in data breaches.
Detecting the risk with Orca:
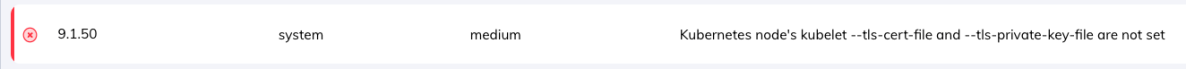
Missing network policies can lead to unauthorized access and actions on the K8s cluster as well.
Orca example detection:

How Orca Security Can Help Secure Your Cloud Environment
Using agentless technology, Orca Security has developed advanced detections for Kubernetes vulnerabilities and misconfigurations in organizations cloud environments while giving them the ability to prioritize the risks from the most critical to the noncritical ones. Using Orca’s game changing capabilities, organizations have the power to get complete visibility into their K8s environments in the cloud and easily secure them according to the organization policy.
Orca’s OWASP Kubernetes Top 10 Compliance Framework
Orca Security now has a new compliance framework for assisting organizations in securing their Kubernetes (K8s) environments. The framework is based on the OWASP Kubernetes Top 10 list of security risks and includes a set of Orca’s advanced detection tests for identifying vulnerabilities and misconfigurations in K8s environments. By using this new framework, Orca helps its customers secure their K8s clusters while monitoring their progress in the remediation process.
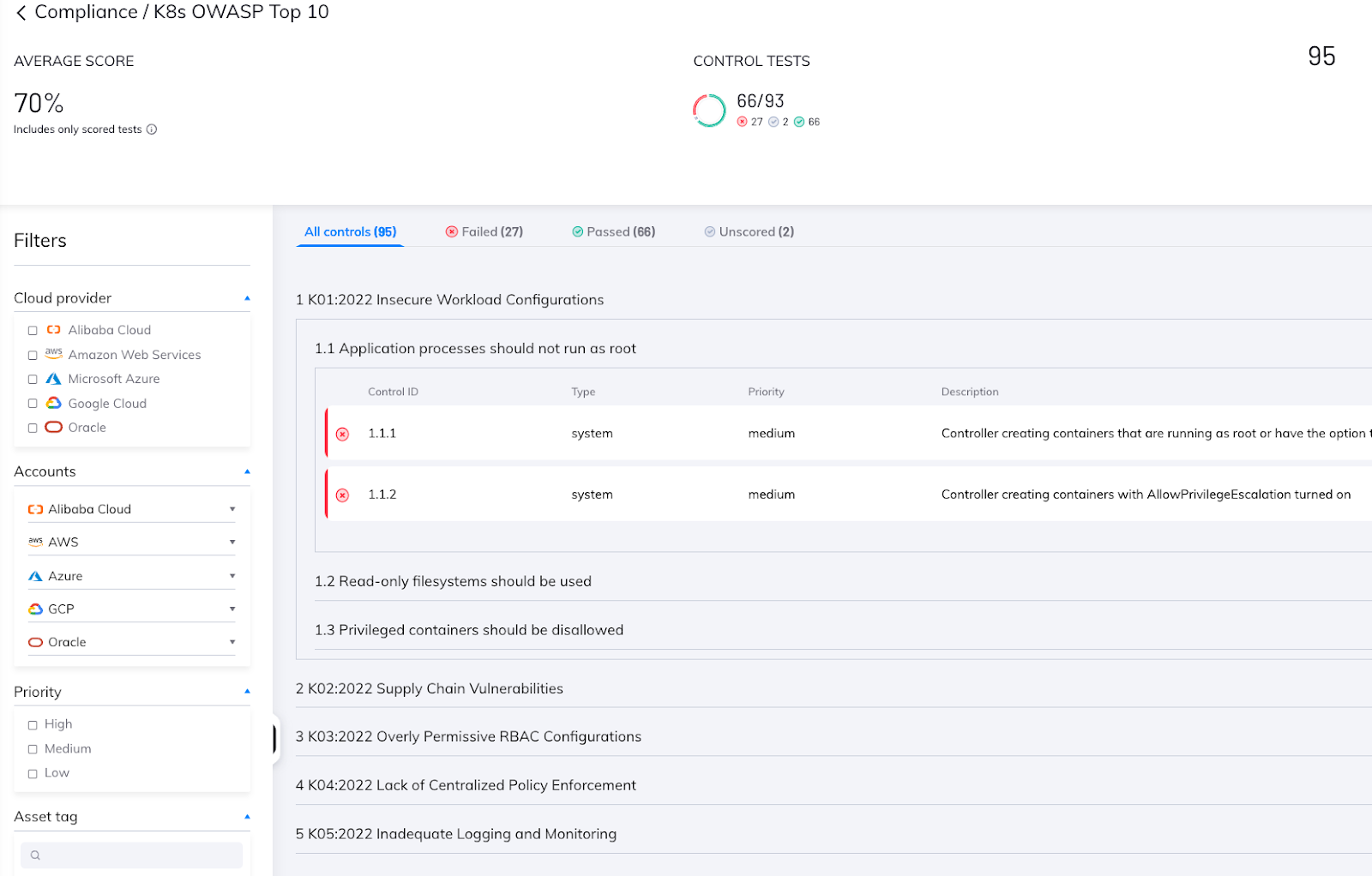
Conclusion
The OWASP Kubernetes Top 10 is an essential guide for organizations looking to address and mitigate potential security threats in their containerized infrastructure. As organizations look to adopt more complex cloud environments, it’s important to take proactive measures to safeguard your deployments. If you’re interested in further enhancing your Kubernetes security, sign up for a free cloud security risk assessment or request a demo of the Orca cloud security platform.





