Kubernetes, aka K8s, is an open source container orchestration platform for the management of containerized applications. K8s is an open source project hosted by the Cloud Native Computing Foundation (CNCF).
Kubernetes is complex, and security is a huge concern. In fact, according to the 2021 Red Hat State of Kubernetes Security Report, 94% of respondents experienced at least one security incident in their Kubernetes environment in the last 12 months.
The is a silver lining in that CIS benchmarks for Kubernetes can significantly simplify and improve the security of your Kubernetes systems.
Here at Orca we wanted to highlight a few simple ways CIS can be used to significantly decrease your Kubernetes attack surfaces.
A Simple Model for Tackling Kubernetes Security
When you use Kubernetes you are running what is called a cluster. A cluster consists of a master node and one or more worker nodes that run containerized applications.
The master node manages the worker nodes and the pods. A node can have one or more pods, and a pod can have one or more containers.
To simplify this, as seen in the diagram below, you will be running a Kubernetes master node inside a host with one or more hosts running worker nodes. The worker nodes contain pods that have containers.
So a simple way of thinking of Kubernetes security is protecting: 1) the host running the master node, 2) the host(s) running worker nodes, and 3) all of the containers running inside of the worker nodes.
So now that we have the components we need to secure (i.e. master node, worker nodes, and all containers). What does securing them mean? At a minimum, it means the following:
- Make sure all components are configured and hardened to security best practices using CIS Kubernetes benchmarks
- Make sure you detect and patch/mitigate the vulnerabilities in all of your Kubernetes components
- Makes sure you are using encryption(CIS can help with this)
- Reduce IAM risk across the entire Kubernetes cluster.
Security Controls Hardening and Best Practices
The best way to apply Kubernetes security best practices is to use Center for Internet Security (CIS) benchmarks to do the heavy lifting of hardening your cloud controls.
CIS benchmarks are a set of best-practice cybersecurity standards for a range of IT systems that includes Kubernetes and containers.
To use CIS to protect your Kubernetes system, you will need three different CIS Benchmarks: one for Kubernetes, one for the containers you are using in your Kubernetes system, and one for the host operating systems that you are running your master and worker nodes on.
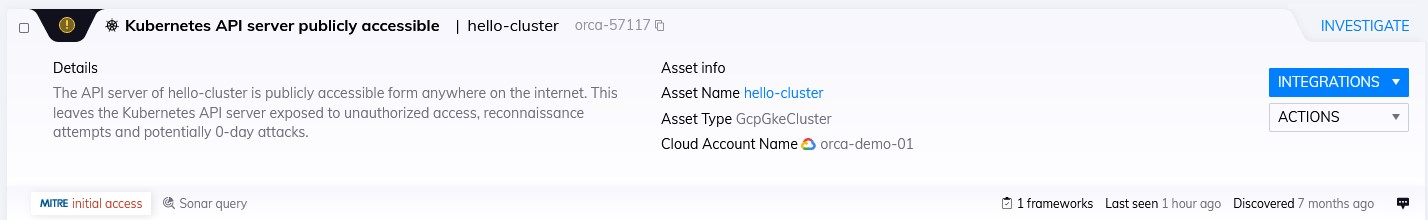
An Orca alert showing a publicly accessible Kubernetes API server
Let’s assume you are using Google Cloud as your cloud service provider and run your master and worker nodes on CentOS instances, you will then need to use the following three CIS policies:
- CIS Kubernetes Benchmark
- CIS Docker Benchmark
- CIS CentOS Benchmark (for the version of CentOS you are using)
Using CIS benchmarks can be an automated affair if your security solution provides support for the needed CIS policies and is capable of scanning the master node, worker nodes, and all of the containers in the cluster.
The key is leveraging CIS benchmarks with a solution that supports all of the CIS policies needed.
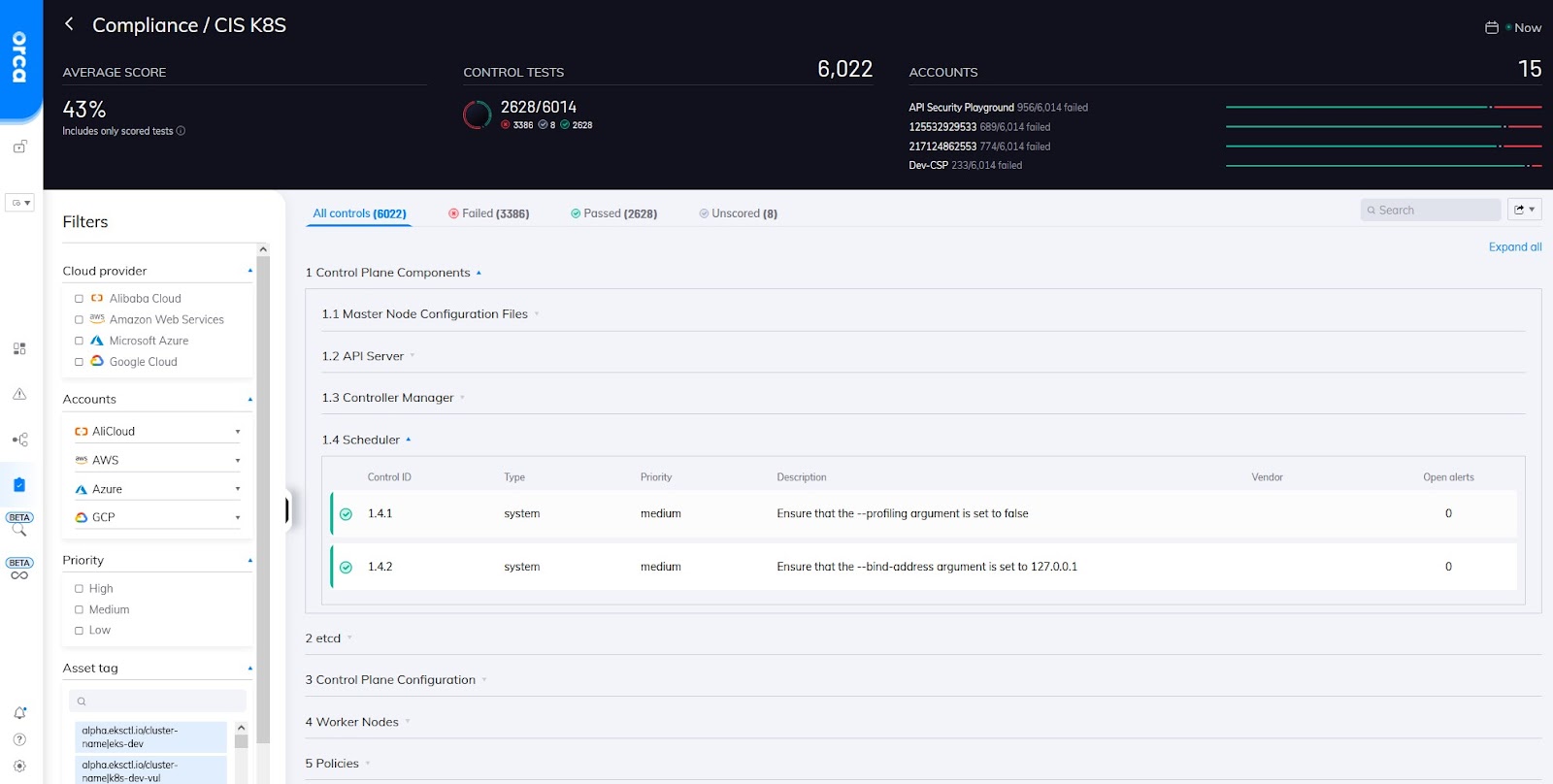
Orca’s implementation of the CIS K8s benchmark showing the 1.4 policy sub-section.
Vulnerability Management
The hosts that run the master and worker nodes and all containers need to be scanned for vulnerabilities. In this case, the cloud security solution needs to be able to scan both the host images and the containers that are being used.
For this example, the security solution needs to be able to support the scanning of CentOs VM instances and Docker containers and be able to find Kubernetes vulnerabilities.
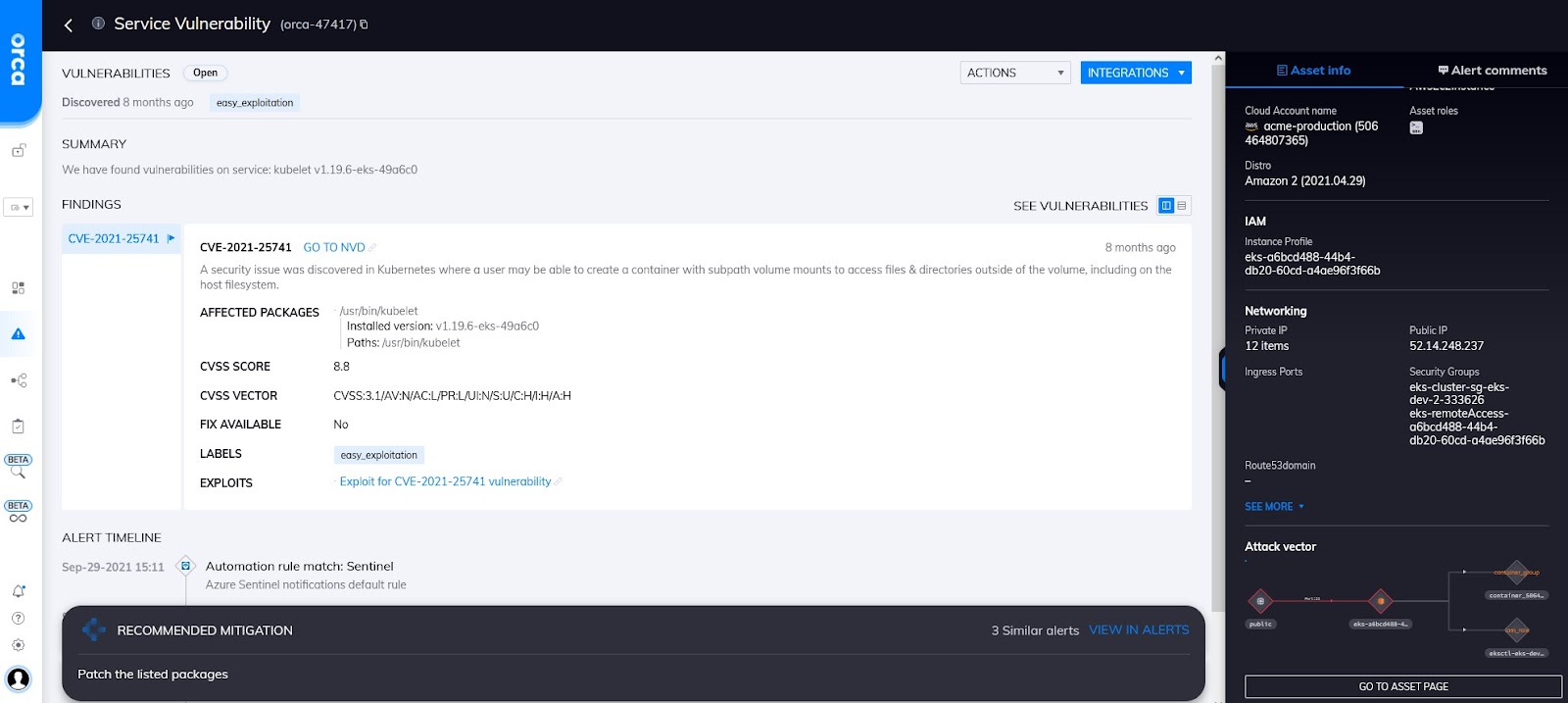
A Kubernetes service vulnerability detected by Orca (CVE-2021-25741)
IAM Risk
Many of the IAM risks are covered by the CIS Benchmarks. Almost every CIS benchmark has an entire section devoted to IAM best practices and configurations. For example from the CIS K8S policy, section
However, you can’t rely only on CIS policies alone and should have a solution that is able to do things like perform PoLP (Principle of Least Privilege) analysis and look at other types of IAM risk, like lateral movement risk.
The most common issue is ensuring that only permissions explicitly required for their operation should be used. Whilst each cluster will be different, some general rules that can be applied are:
- Minimize distribution of privileged tokens
- Ideally, pods shouldn’t be assigned service accounts granted powerful permissions (listed here)
CIS Benchmarks and Encryption
Encryption best practices are covered in all of the different Kubernetes CIS benchmarks. CIS helps substantially by checking to make sure most of the configuration settings around encryption are set properly. For example in the CIS K8S policy 4.2.13 “Ensure that the Kubelet only makes use of Strong Cryptographic Ciphers” checks the Kubelet config file and checks to see if the TLSCipherSuites parameter is set to a strong cypher.
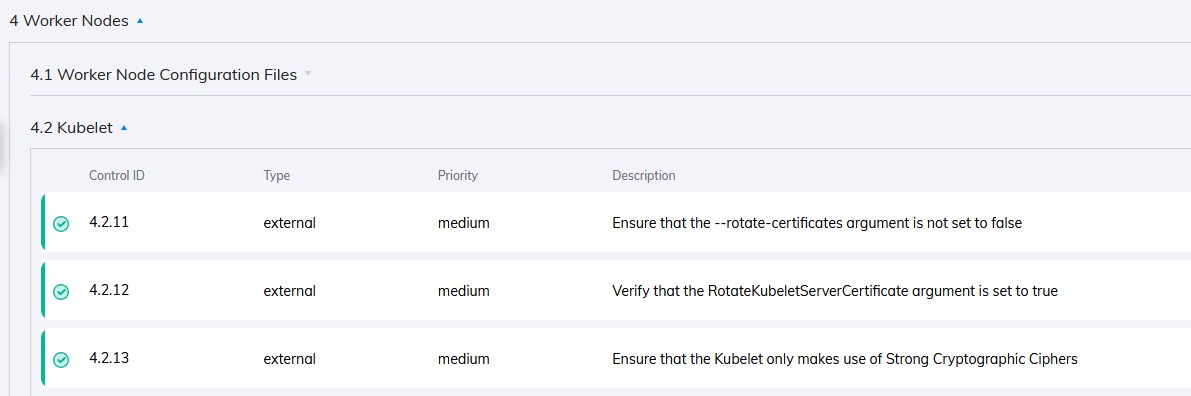
Several of the encryption related CIS controls in the Orca UI
How Orca Helps
Orca helps because it supports all of the CIS policies needed to protect Kubernetes and is also capable of scanning your all Kubernetes nodes and containers for vulnerabilities.
Beyond full support for all the relevant CIS Benchmarks and the ability to scan containers and all hosts for vulnerabilities.
Orca also has the ability to do PoLP (Principle of Least Privilege) analysis on all Kubernetes permissions as well as look at IAM risk in Kubernetes in a variety of different ways to include looking for lateral movement risk.
In addition Orca can also look in all your Kubernetes hosts and containers for sensitive data and malware and has the ability to look at host and container images both in development and in production environments.
Kubernetes security doesn’t have to be hard. The key is a security solution that can scan all of your hosts and containers and then check them against all the needed CIS policies as well as be able to detect vulnerabilites, IAM risk, malware, and sensitive data in all of your containers, worker nodes, and master nodes.






