Multiple vulnerabilities (one severe) have been discovered in CUPS (Common Unix Printing System) and related components. These vulnerabilities (CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177) allow unauthenticated remote code execution (RCE), impacting all major GNU/Linux distributions, including Debian and Red Hat.
If exploited, it could result in remote code execution (RCE)—potentially leading to full system compromise, loss of data, and further attacks. Immediate attention and mitigation are recommended.
In this post, we explain what steps are required to protect against the vulnerabilities and how the Orca Cloud Security Platform can help.
What are the CUPS vulnerabilities?
The CUPS vulnerabilities allow unauthenticated remote code execution (RCE) through a combination of insecure handling of IPP (Internet Printing Protocol) attributes and poor sanitization practices. The vulnerabilities are present across various GNU/Linux distributions, BSD systems, and potentially ChromeOS and Oracle Solaris.
CUPS (Common Unix Printing System) is widely used in Unix-like operating systems (Linux, macOS, and others) to manage printing tasks over a network. It handles communication between the system and printers, often using IPP (Internet Printing Protocol) to transfer data and control print jobs.
Below are the identified vulnerabilities affecting CUPS components:
- CVE-2024-47176: cups-browsed (<= 2.0.1): The cups-browsed service manages printer discovery and configuration. It listens on UDP port 631, trusting any packet from any source. This can allow an attacker to send a malicious packet that triggers a Get-Printer-Attributes request, redirecting it to a URL under the attacker’s control.
- CVE-2024-47076 libcupsfilters (<= 2.1b1): libcupsfilters is part of the filtering system that processes print jobs. The vulnerable function, cfGetPrinterAttributes5, does not properly validate IPP attributes returned from a print server. This allows attackers to inject malicious data into the CUPS system.
- CVE-2024-47175: libppd (<= 2.1b1): PPD (PostScript Printer Description) files define printer capabilities and options. The libppd library handles these files, but it does not properly sanitize IPP attributes before writing them to temporary files. This opens the door for attackers to inject harmful data into the printing configuration.
- CVE-2024-47177: foomatic-rip utility in cups-filters (<= 2.0.1): foomatic-rip is a part of CUPS that processes print jobs by interpreting PPD parameters. One of these parameters, FoomaticRIPCommandLine, can be manipulated by an attacker to execute arbitrary commands on the system.
Potential impact of the CUPS vulnerabilities
An unauthenticated, remote attacker can exploit these vulnerabilities to:
- Silently replace or install new printers with malicious URLs.
- Trigger arbitrary command execution when a print job is started, allowing full compromise of the system running CUPS.
Steps to mitigate the CUPS vulnerabilities
So far, it appears that these vulnerabilities are not significantly impacting cloud assets, primarily due to the less frequent use of CUPS and IPP in cloud environments, as well as the following factors:
- Having cups-browsed installed is a non-default configuration on server installs for cloud computing workloads.
- This is only exploitable if you have udp/631 open from the outside world to an asset that has cups-browsed installed on it, or the attacker already has access to the local network segment, and cups-browsed and DNS-SD or zeroconf are enabled. This would mean that a compromise has already occurred.
- Exploitation requires creating a print job on the asset targeting the malicious print queue created by exploiting the cups-browsed vulnerability.
However, we recommend that organizations prioritize remediating assets that are exposed on udp/631, running vulnerable libraries, and used to create print jobs. For these assets, we recommend the following remediation steps:
- Disable the service: Disable and remove the cups-browsed service if it’s not needed.
- Apply the latest patch when released: Update CUPS to the latest patched versions as soon as the updates become available.
- Block traffic if needed: If your system can’t be updated for any reason, block UDP traffic to port 631, and consider blocking DNS-SD/zeroconf traffic, especially if your system relies on these protocols.
How the Orca Platform can help
The Orca Cloud Security Platform provides complete visibility across your cloud assets and risks. Using the Orca Platform, you can easily identify any specific assets that may be impacted by CUPS vulnerabilities.
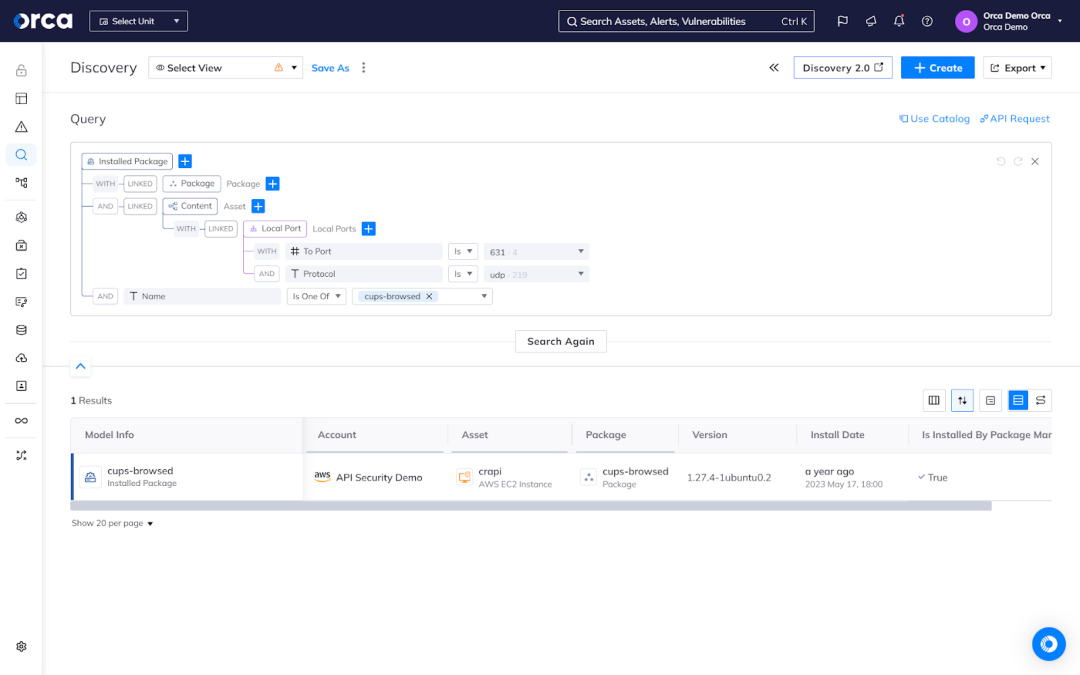
The Orca Platform is not only able to report on the presence of each CUPS CVE, but it also determines which vulnerabilities in your environment should be remediated first.
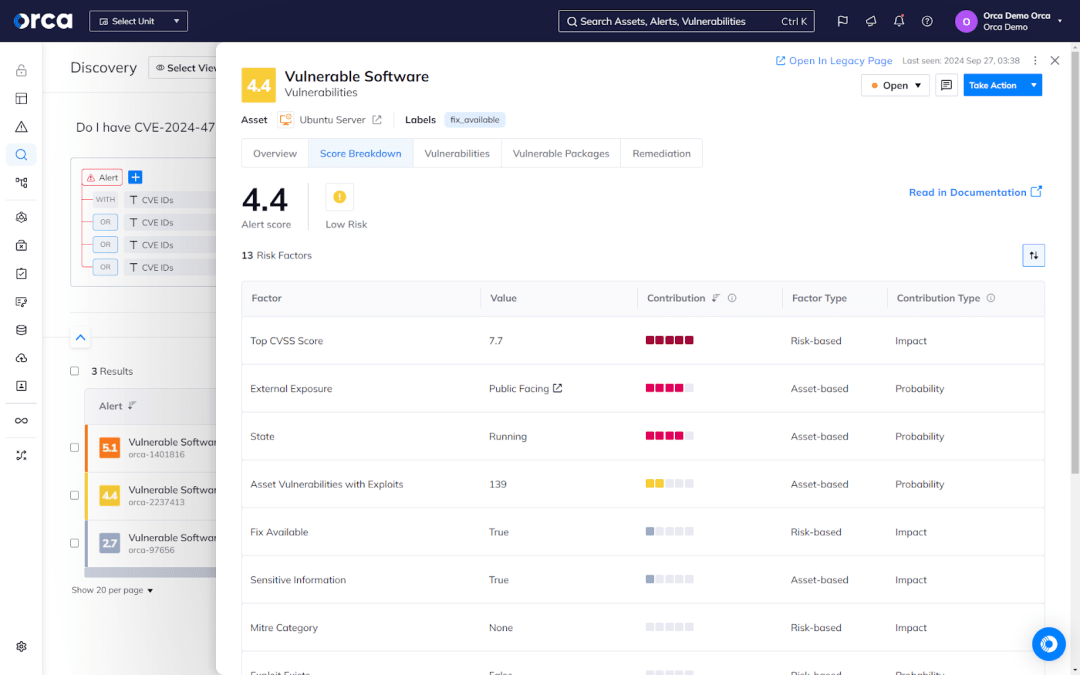
Combining full contextual awareness and deep insights, Orca automatically assesses the criticality of each vulnerability using several factors, including its severity, likelihood of exploitation, exposure, access to sensitive data, and potential business impact if compromised. Orca also detects the interconnected risks between cloud risks and assets, prioritizing hidden attack paths that endanger your high-value assets.
Orca performs this analysis continually and updates each alert score as conditions in your environment change.
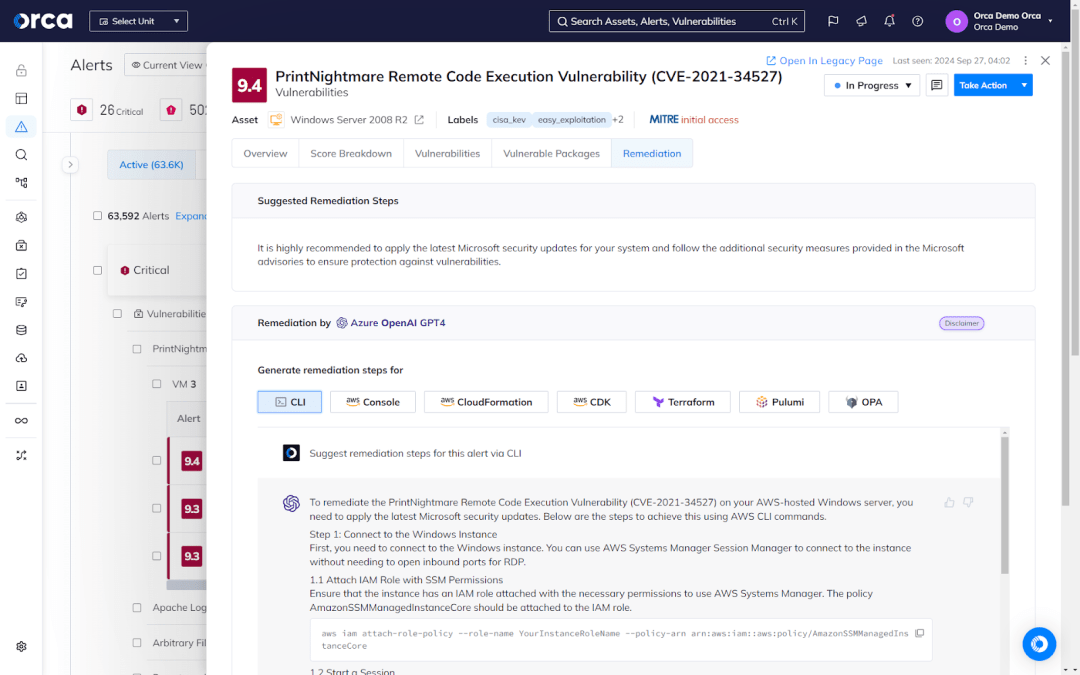
Additionally, Orca provides multiple remediation options for every alert. This includes suggested remediation instructions from Orca Security experts, as well as AI-Driven Remediation. The latter enables you to generate remediation code and steps for the console, CLI, and IaC tools such as Terraform and Pulumi, helping accelerate your mean time to resolution (MTTR).
Orca also offers two-way integrations with Jira and ServiceNow, allowing you to assign tickets for remediation and include the remediation instructions.
About Orca Security
We’re on a mission to provide the industry’s most comprehensive cloud security platform while adhering to what we believe in: frictionless security and contextual insights, so you can prioritize your most critical risks and operate in the cloud with confidence.
Unlike other solutions, Orca is agentless-first and fully deploys in minutes with 100% coverage, providing wide and deep visibility into risks across every layer of your cloud estate. This includes cloud configurations, workloads, and identities. Orca combines all this information in a Unified Data Model to effectively prioritize risks and recognize when seemingly unrelated issues can be combined to create dangerous attack paths. To learn more, see the Orca Platform in action.






