‘[Redacted product name] analyzes cloud activity across multiple heuristics, develops a behavioral model for each user, and flags an anomaly when a user shows a departure from this model. [Redacted product name] analyzes user activity across multiple cloud services using machine learning techniques to identify anomalous use. It then goes a step further by correlating multiple data points to determine which anomalies most likely represent real threats versus false positives. This way, the solution ensures that IT and security teams receive timely alerts on high-likelihood threats so they can avoid their impact on the company without being overwhelmed with a constant chorus of alerts…’
This certainly sounds impressive. Digging deeper into the article, they explain how geolocation data can detect location anomalies by looking at what is called a “superhuman anomaly” (someone who simultaneously logs in from two or more locations) and similar measures.
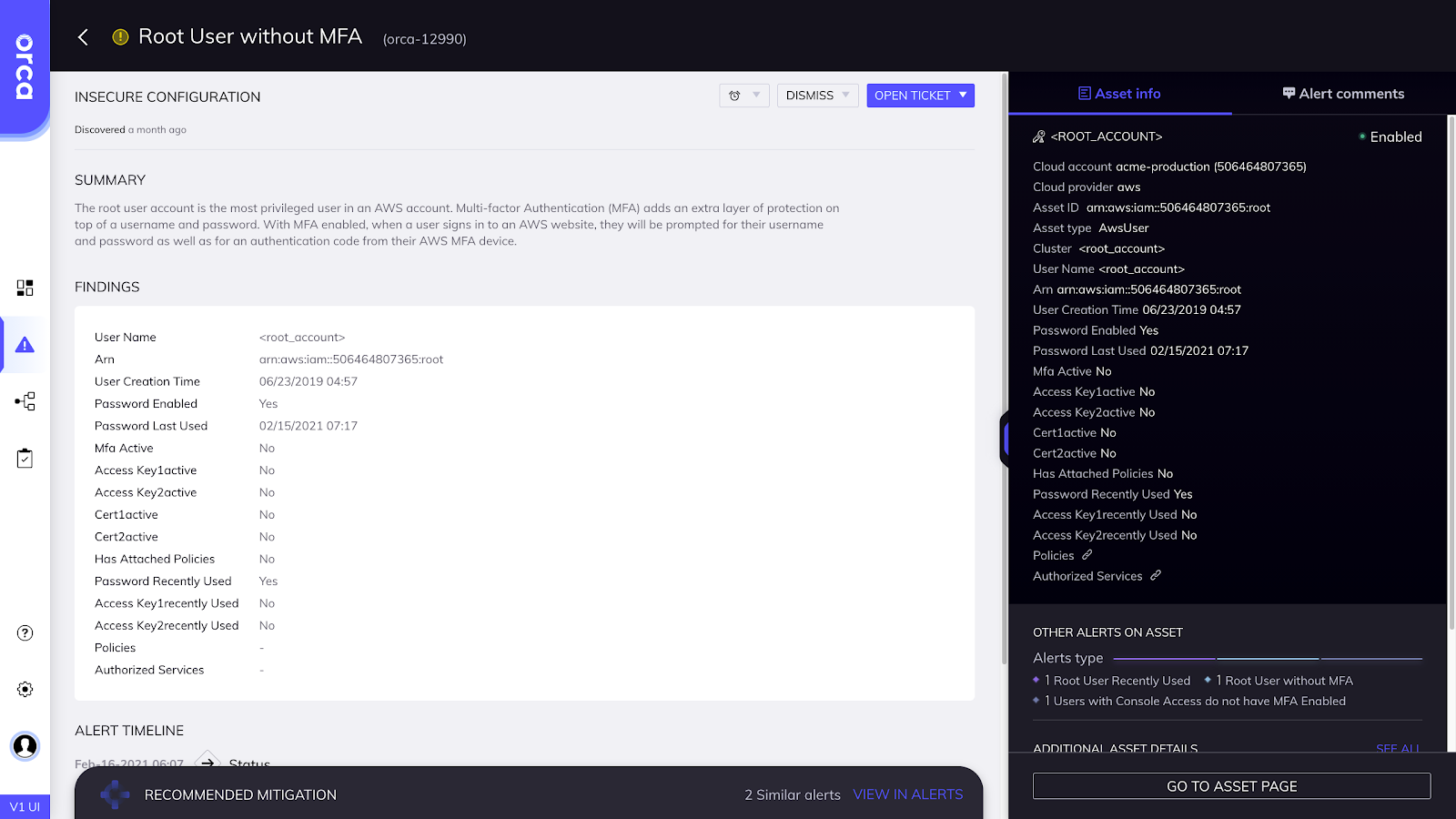
Machine learning isn’t a crystal ball. If your users use passwords without Multi-Factor Authentication (MFA), depending on such advertised security heuristics can put you on shaky ground. Do you really expect an attacker not to look at your user location (readily available using Facebook and other methods) and then use a VPN to access your network from what appears to be the same place?
Yes, there are other indicators, but none of them are solid and can lead to a litany of false positives:
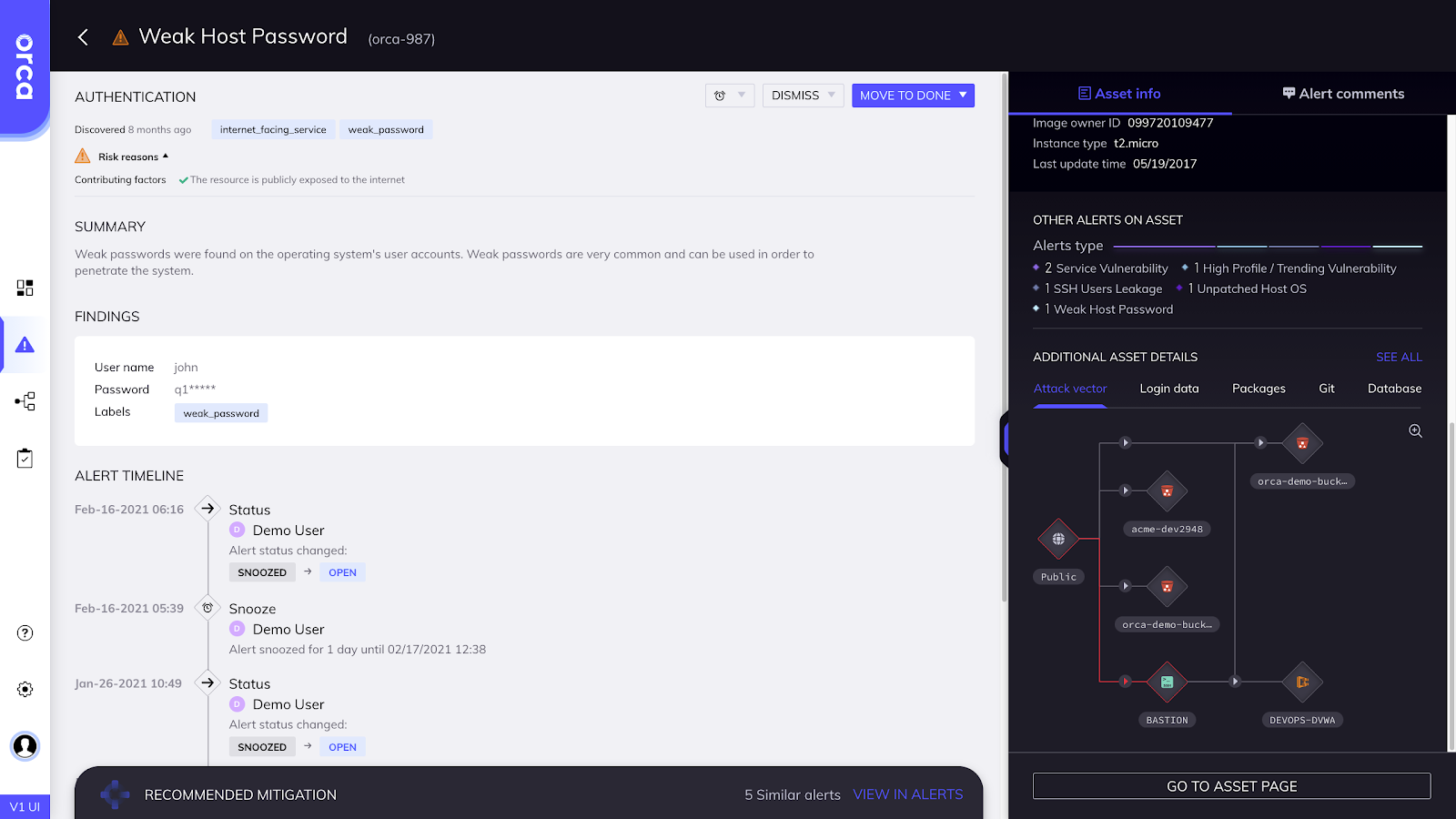
- Use of a new device (which happens frequently). Do you want an alert each time one of your users purchases and logs on with a new smartphone?
- Different usage patterns. Guess what? Different patterns occur due to business needs.
Instead of Artificial Intelligence (AI), an excellent and cost effective access solution is to deploy MFA and verify there is 100% coverage. Indeed, organizational friction will be more challenging than having dinner with a sales rep attempting to sell you his newest AI-driven, anomaly-killing tool. But it’ll protect your organization.
Conclusion
By now you know I’m a proponent of practicing comprehensive IT hygiene rather than using shiny-object security products. Years of experience reminds me of this truism every day. My guidance over these past four blog posts has been simply that.
Practice IT hygiene; patch your software often, harden your systems, manage risk of lateral movement within your IT infrastructure, and use inexpensive, highly-available, MFA instead of some fancy AI solution. These solutions won’t mitigate all attacks, but they’ll provide an excellent baseline (and more) for your defense.
Orca specializes in AWS Cloud Security, Google Cloud Platform Security, and Microsoft Azure Cloud Security.





