When it comes to a cyber attack, expediting your investigation and response can mean the difference between a crisis averted and a worst case scenario. This uncomfortable reality illustrates the significance of cloud detection and response (CDR). CDR helps organizations catch early-stage attacks and orchestrate rapid responses that neutralize threats. Despite the importance of CDR, many organizations face challenges in this area of cloud security. Legacy CDR tools and inadequate solutions delay their investigations and remediations, leaving security teams constantly overwhelmed and organizations at elevated risk of exploitation.
That’s why Orca is pleased to announce new enhancements to Orca Cloud Detection and Response, a deeply integrated set of capabilities within the Orca Cloud Security Platform. The new updates introduce a number of exciting capabilities and improvements to expedite threat investigation and response. From an improved user experience, to enriched insights, to new functionality, the latest release empowers security teams to level up the speed and performance of their work.
Why is Orca updating its CDR capabilities?
Unauthorized access and data breaches are the top two cloud security risks reported by executives, according to Orca’s 2023 & 2024 Cloud Security Strategies Report. Meanwhile, respondents say increasing efficiency, scaling the security team, and securing supply chains are among their top objectives in the year ahead. These findings point to the importance of CDR, an invaluable yet challenging area of cloud security.
Orca has enhanced its CDR capabilities to ensure our customers can meet the evolving demands of the modern threat landscape.
What are Orca’s new CDR improvements?
Orca is introducing several exciting updates that advance its current CDR capabilities. The following four updates headline this release.
#1: Cloud-agnostic classification
Challenge: Cloud service providers each use unique naming conventions to define the parameters of a specific event, including the actor, action, target, source, and service. Security teams must possess specialized knowledge of these naming conventions to conduct forensic investigations. This can prove especially challenging for busy teams needing to work across multi-cloud environments, onboard new team members, or compensate for skill shortages.
Orca Solution: Orca’s CDR classifies events based on well-established, cloud-agnostic terminology. Orca’s event parameters index events using the following categories:
- Actor: Human or non-human identities that performed an action.
- Action: Action grouped by type.
- Target: Target resource(s) impacted by action.
- Source: Action grouped by source IP, account, region, location.
- Services: Services impacted by events.
With Orca’s cloud-agnostic classification, security teams can leverage a common language across their CDR workflows, boosting their efficiency and productivity.
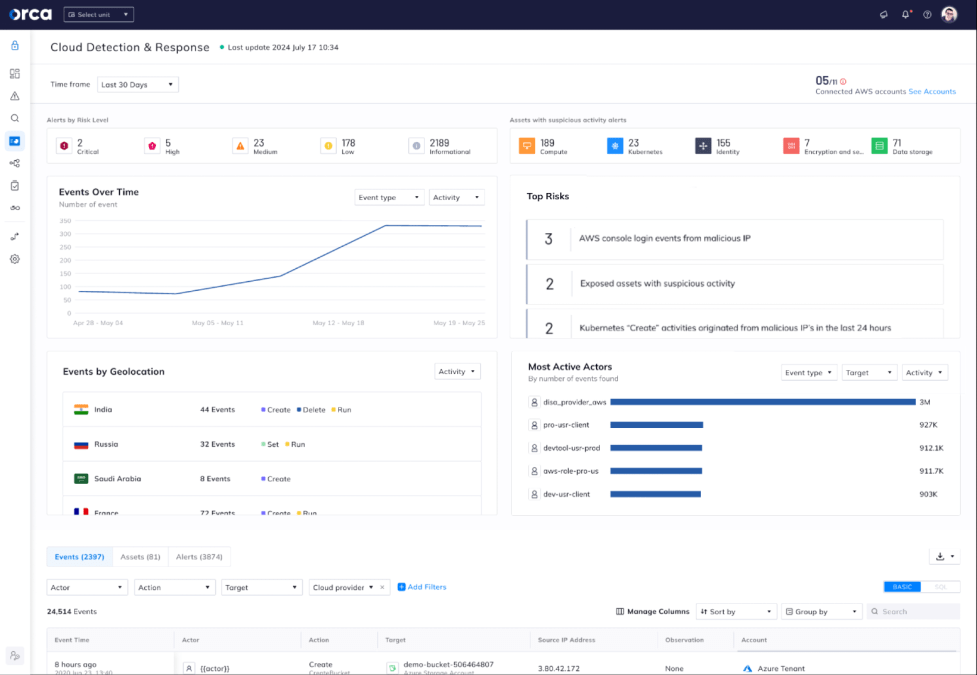
#2: Event-driven security dashboard
Challenge: Security teams need the ability to quickly diagnose anomalous activity, correlate seemingly unrelated events and findings, and launch investigations to discover answers—and fast. Personnel often encounter delays from needing to rely on over-simplified dashboards that offer minimal insight or actionable guidance.
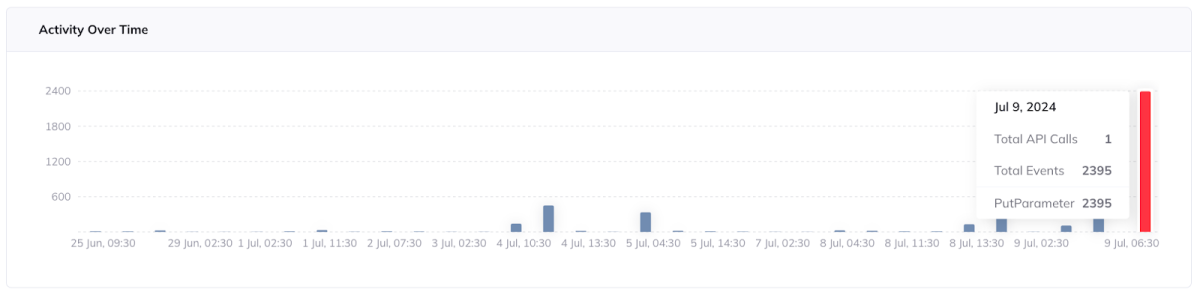
Orca Solution: Orca’s CDR dashboard provides security teams with important, actionable, and at-a-glance insights to expedite investigations and response. Teams can see Orca Alerts by risk level, assets with detected suspicious activity, events over time, events by geolocation, top event-driven security risks, most active actors, and more.
For example, using Orca’s “Events over time” widget, security personnel can easily spot anomalous activity based on their unique understanding of the cloud estate.
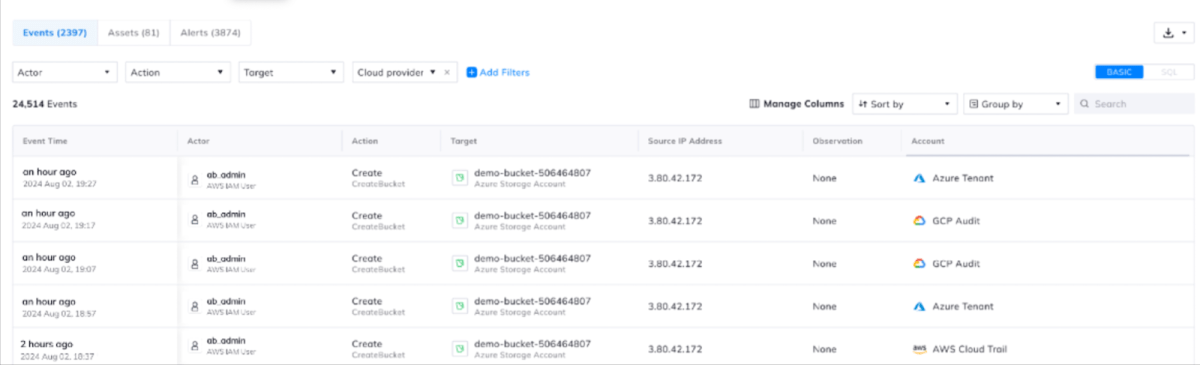
#3: Unified event data stream
Challenge: Security teams face a never-ending supply of cloud logs that only create noise and add complexity to their work. Each cloud service provider uses unique schemas and services that require specialized knowledge to interpret the logs. Additionally, unifying them in a central location calls for logging into each CSP platform, delaying time-sensitive investigations.
Orca Solution: Orca’s unified event-driven data stream empowers teams to expedite their investigation and response capabilities. Orca aggregates logs across all CSPs to provide a comprehensive feed with no gaps in coverage or visibility. Security teams can quickly search and filter the results by using any of Orca’s cloud-agnostic parameters, including specific actors, target, account, and more.
Additionally, security teams can search all cloud logs using SQL queries. This saves time and expense, eliminating the need to use a third-party database or export logs as a CSV from each CSP.
Orca’s unified event data stream also provides teams with a catalog to start investigations or ask specific questions.
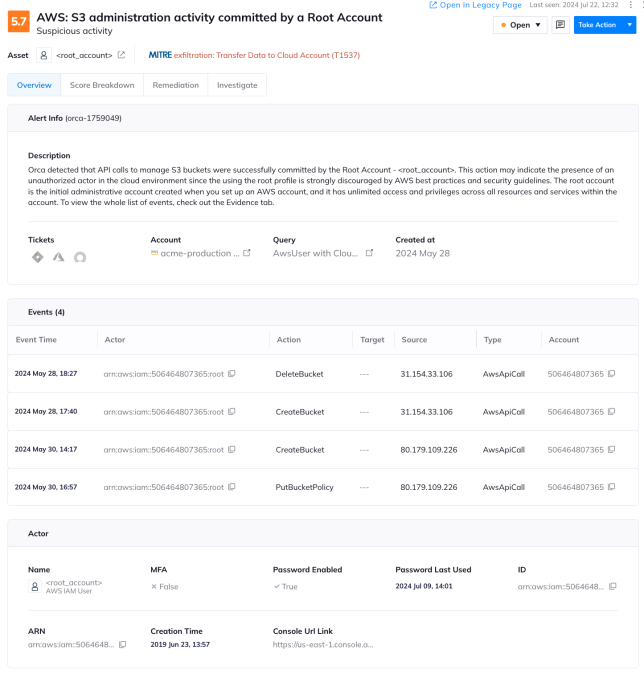
#4: Event-driven alerts
Challenge: Many security teams struggle to focus on the most impactful and time-sensitive risks in their cloud estate. This struggle often comes from alert fatigue and a lack of context for detected risks.
Orca Solution: Orca provides comprehensive risk detection and prioritization that empowers security teams to remediate critical risks without delay. Organized based on severity, every Orca Alert presents rich and meaningful data that fully contextualizes the risk. This enables security teams to further expedite their response and remediate the most time-pressing risks without delay.
Consider three common CDR use cases that showcase the range and benefits of Orca Alerts:
- Pattern-based risks: Orca generates alerts based on predefined event patterns that pose a high risk. This type of Orca Alert provides detailed information about the actor and the history of each event, including the event time, action, source, type, account, and more. Users can click any event to see the event details.
- Anomaly-based risks: Orca generates an alert when detecting anomalous activity that deviates from normal conditions. This Orca Alert displays Anomaly Details, relevant findings, as well as a time-based graph that charts anomalous activity for fast diagnosis. By hovering over the graph, users can see additional relevant details. In the example of a permissive IAM role, this may include the total number of regions an actor used on a particular date or date range.
- Alerts from AWS GuardDuty, Azure Defender for Cloud, and GCP Security Command Center: Orca ingests alerts from AWS GuardDuty, Azure Defender for Cloud, and GCP Security Command Center, prioritizes them, and integrates them with all other Orca Alerts. This gives security teams a single pane of glass for threat investigation and response activities.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform and its CDR capabilities? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can expedite and enhance your investigations and response.