The power of integrating security scanning and policy enforcement earlier in the application development lifecycle is tremendous. Orca’s GitHub App has enabled security organizations to begin scanning source code repositories seamlessly and with very little friction. Today, we’re pleased to announce that we’ve extended this approach to the GitLab platform.
While the security benefits of shifting security left are clear, implementation has traditionally been more problematic. Command line tools have to be manually inserted into pipelines, requiring unnecessary coordination between security and DevOps teams as well as making it difficult to ensure complete coverage. This creates separation of duties concerns – security teams should have control over where policy is enforced and DevOps teams may prefer not to invest in operationalizing security.
The GitLab App in the Orca Cloud Security Platform, like the GitHub App, delivers a simpler approach with less friction. With a single authorization, security teams can centrally integrate scanning into code repositories in their GitLab organization without needing to manually embed CLI tools or change pipeline configurations. Teams can manage and apply policies for detecting vulnerabilities, misconfigurations, and secrets in application source code and Infrastructure-as-Code (IaC) artifacts.
GitLab Integration, Simplified
With the GitLab App, administrators of Orca can connect to GitLab tenants, enumerating all GitLab projects (code repositories) and integrating Orca’s scanning into them. They can also tailor policies to the projects, centrally managing what needs to be scanned for and what security issues will result in an enforcement action.
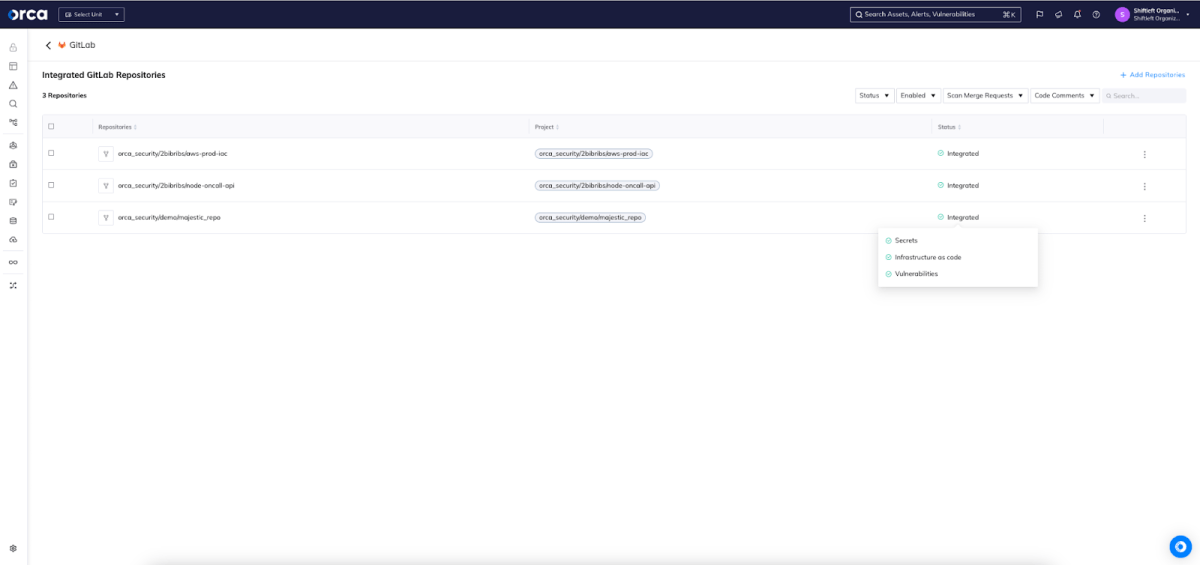
Onboarding and managing GitLab repositories
Once the tenant is onboarded, administrators can easily configure scanning projects, individually or all at once. New projects are easily discovered and onboarded as needed. Finally, projects are onboarded with separation of duties maintained.
Central Policy and Visibility for Security Teams
Once the repository is onboard, security teams can easily create policies to find the problems they’re concerned about and, if desired, when to enforce the policy to block a problematic merge request. You can apply policies per repo, across groups of repos, or all of the repos in the organization easily. In this example, we’ve applied a policy that fails a merge request based on the presence of plaintext secrets and, in the scan of the merge request, Orca Security found a GitLab Personal Access Token. Security teams have complete control over the security policy applied in Shift Left integration.
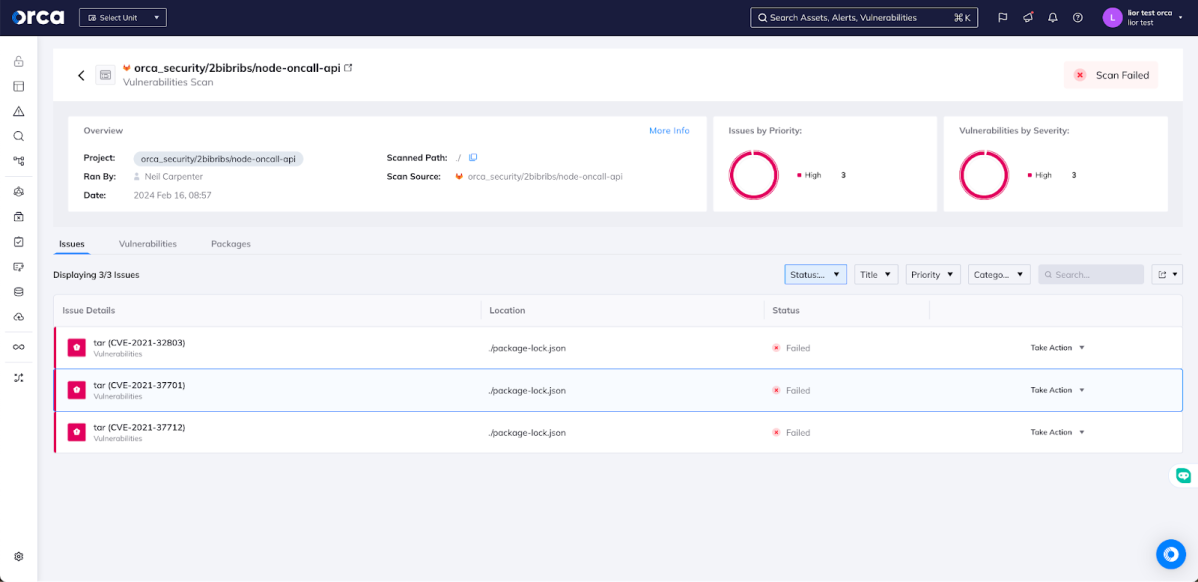
Security teams can see details of each change to the repo and the security issues introduced.
Additionally, analysts have a single pane to show them the status of every scanned repository, showing top issues and trends across the entire organization. The security team can quickly zero in on new or pervasive problems while demonstrating the effectiveness of application security programs over time.
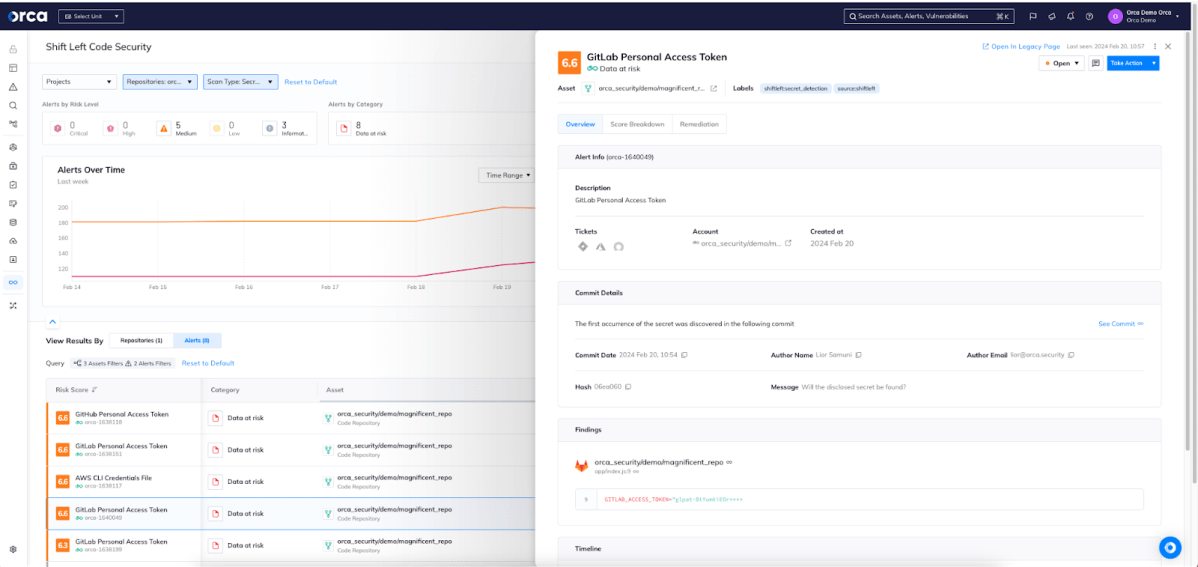
Orca’s Shift Left Code Security dashboard puts code quality results and trends at your fingertips.
Developer Experience
Having a great solution for security teams is only part of it, though; we also have to deliver the right intelligence to the developers who are building and shipping cloud applications. Thankfully, the Orca Security GitLab App delivers – while a scan of the primary branch will show all the problems that are present, scans on merge requests filter out existing issues and only show new problems introduced in the developer’s changes. This allows developers to focus on the impact of their work and to only be blocked if they’ve introduced a new policy violation. For example, if we accidentally introduce a new vulnerability older than 15 days with an exploit available while fixing an issue, our merge request will be caught by Orca’s vulnerability scan and blocked until we resolve the issue.
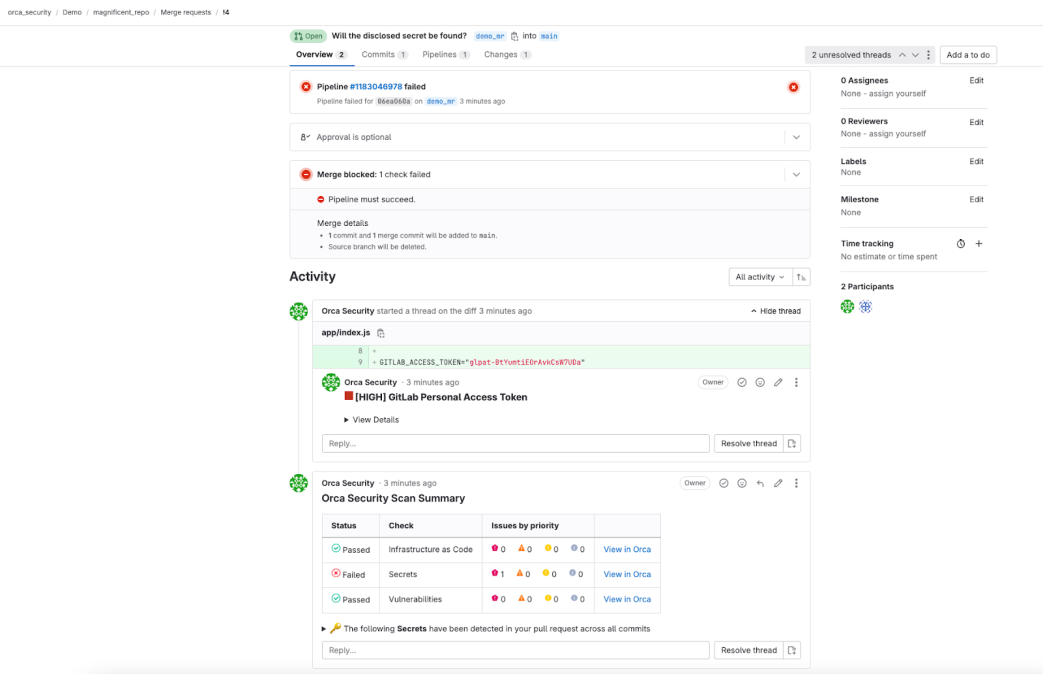
A merge request has been blocked because a secret was introduced into the codebase.
This is familiar territory for modern developers – just as failures in other automated unit, integration, and performance tests may result in errors that have to be remediated before shipping, now security tests show up in the same way.
Conclusion: Centralize Deploying and Managing IShift-Left Scanning
By centralizing the integration and configuration of scanning repositories for adherence to security policy, Orca helps our customers realize the promise of Shift Left Security. Security teams can easily apply controls early in the application lifecycle while DevOps teams gain security insight without having to manage the integration themselves.This is only the beginning, though – we have big plans to keep extending what security and DevOps teams can accomplish with Orca Security.





