We founded Orca because we believe that security solutions should support organizational growth, provide security across the entire technology stack, and secure all of the assets seamlessly. That starts with security visibility.
I worked in cybersecurity for over 25 years, serving as the chief technologist at Check Point, the world’s largest cybersecurity vendor before co-founding Orca Security. I saw how the industry evolved over the years both for whitehats and blackhats and I would frequently notice security teams erroneously emphasizing strong security for the obvious front doors, while neglecting the equally important rear ones. This is why I often share the following cartoon about how attacks usually evolve.
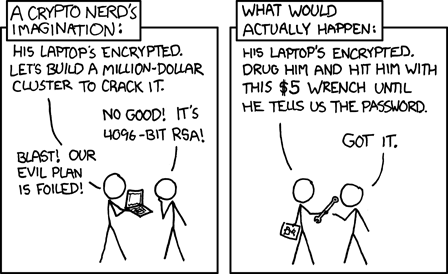
(Credits: XKCD)
After all, it’s far more exciting to build ever-more-complicated front gates than methodologically securing each and every one of the rear ones. We, as security industry professionals, share the blame. I can personally testify to the fact that there are great ‘front gate’ controls.
Unfortunately, we lack strong security visibility solutions for these rusty back doors. Remember, the assets that you don’t see are far more likely to be responsible for your next breach.
This is even more crucial today because growing cloud environments contain more than just one clearly defined front door. In fact, there are dozens of entry points to protect, as you’re never more than one click away from another entry point.
The need for solutions that can provide full-stack visibility for an entire cloud environment is more pressing than it has ever been. Today’s CISOs need to be able to see all assets through all layers starting at the cloud control plane, continuing through the operating system and basic infrastructures, and extending through to the applicative and data layers.
The current state of security visibility – and why it needs to change
Today, all security visibility solutions require you to either invest substantial efforts into per-asset integration or use external probing, which can only provide limited visibility.
We didn’t think the current solutions were simple enough. We knew there had to be a better way to provide security visibility.
Analyzing the situation, we were shocked to discover that the technology in use for security assessment hasn’t changed in the last 20 years. It was designed to work for individual machines. CISOs either relied on agents and network scanning tools to gain insight into the assets themselves or settled for limited visibility. We saw organizations devote months solely to integration, and even after addressing intra-organizational obstacles, they would only achieve partial security.
This is why we started Orca Security
Modern IT environments that leverage cloud computing look dramatically different today than they did 20 years ago. Why should security visibility solutions be bound by restrictions from two decades ago?
That’s why we designed a visibility platform for the modern, virtualized data center in both public and private cloud environments. Along with our patent-pending SideScanning™ engine, we’re able to provide full stack visibility that
- Covers the cloud config layer, operating system, applications, and business data
- Detects application vulnerabilities, critical security misconfigurations, compromised assets and use of leaked credentials
- Includes all virtual assets
- Requires a one-time, 5-minute, infrastructure-level integration, regardless of whether you have 100 or 100k assets
- Doesn’t necessitate per-asset integration
- Boasts zero risk – using read-only access
Security teams today are swamped with tasks. They should have tools that operate automatically. They need solutions that will allow them to devote their time to fighting attackers rather than solving intra-organization obstacles. We will empower security teams to regain control of their cloud environment so that they can better support organizational growth, and will provide organizations transforming to the cloud a level of security that was simply impossible in the physical world.
Ultimately, this is what Orca Security is all about.





