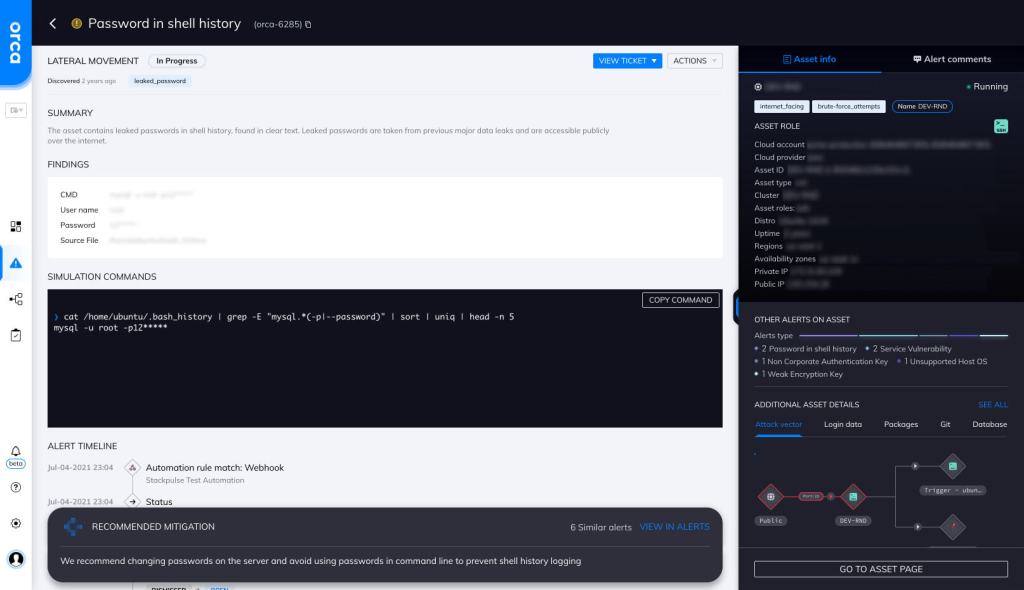
Password in Shell History
Hazardous (3)
Orca Best Practices
About Shell History
The GNU history utility keeps a record of the commands a user enters during a shell/terminal session. By default, 1,000 historical commands are stored, but the number can be changed using the $HISTSIZE and $HISTFILESIZE variables. The history is logged in a hidden file named “.bash_history” in the user’s home directory.
Simply running the history command on a shell will print out all the commands that have been executed during a session. You can replay any of the historically run commands using the “!” sign. For example, “!5” will run the command present on the fifth line of your bash history.
You can also search your history for any previously run commands. grep history | git will filter out all the git commands from your history. You can also press ctrl + R to start a recursive search of your history. During a recursive search, matching results will start appearing as you type a keyword.
The bash history file can also contain sensitive information like API keys, secrets, and passwords.
Cloud Risk Description
Bash users often enter their passwords and other sensitive information on the command line, which ends up getting stored in the bash history file. For example, a user may run the following command to log in to a SQL Server database:
SQLCMD -S mydatabase -U admin -P p@@sw0rd
This command will end up in the bash history, along with the plaintext password.
On a compromised system, malicious actors can search this file for credentials and other exploitable information.
How can Orca Help?
Orca can detect passwords in the shell history. Orca uses pattern matching techniques on each line of the bash history file to look for different password execution types. Some password examples that Orca can detect and alert on are as follows:
- mongo admin -u uname -p ‘hello’
- ftp backup:[email protected]:2121
- mysqladmin processlist -u root -p12345
Recommended Mitigation Strategies
-
Turn history saving off
Use the command set +o history to temporarily turn history saving on or off.
-
Don't store "password" in bash history
Set HISTIGNORE=”*[Pp][Aa][Ss][Ss][Ww][Oo][Rr][Dd]*” to ensure that any command with the word password isn’t stored in bash history. Note: The $HISTIGNORE environment variable controls which commands are entered into the history and which are ignored.
-
Don't enter passwords via command line
Educate people to not enter passwords via the command line. A relatively safer alternative is to provide passwords via the standard input (stdin) stream.
-
Clear history as needed
Use the command history –d to clear a specific line from a history file. You can also clear the entire history using history -c.
Useful Links
- Using bash history https://www.howtogeek.com/44997/how-to-use-bash-history-to-improve-your-command-line-productivity/
- Bash history tips https://opensource.com/article/20/6/bash-history-control
- Managing Linux command history https://www.redhat.com/sysadmin/history-command
- GNU history documentation https://tiswww.case.edu/php/chet/readline/history.html
- Bash history shortcuts https://opensource.com/article/19/10/bash-history-shortcuts
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
