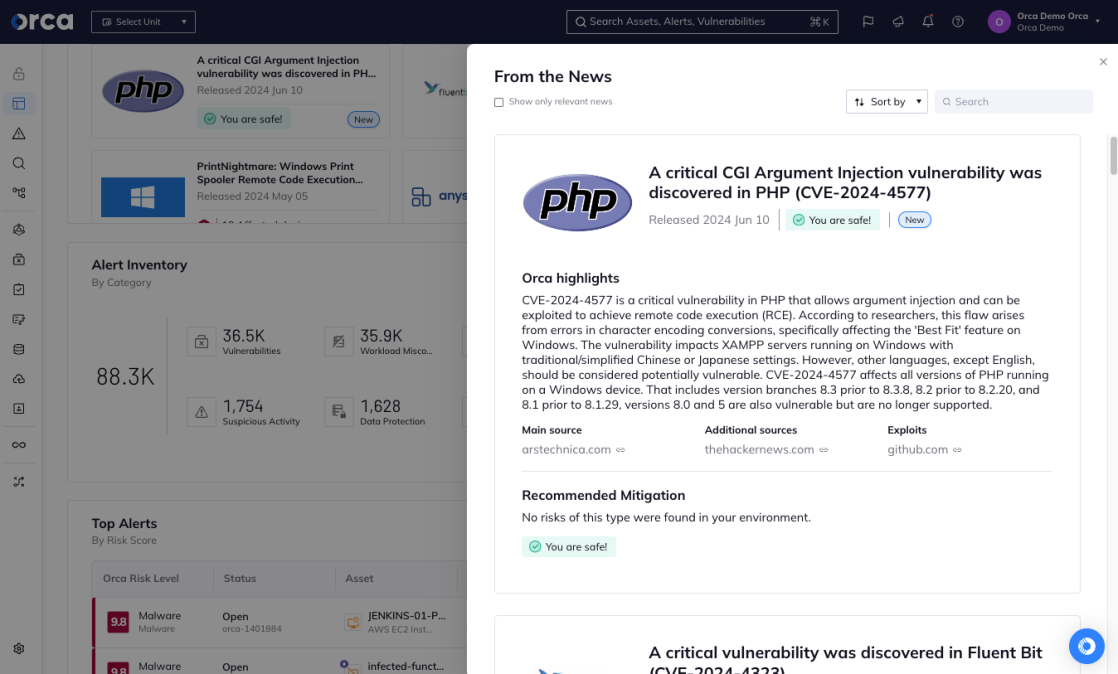
On June 6th, researchers from Shadowserver, a nonprofit security organization, discovered a heavily exploited vulnerability in PHP servers running on Windows devices.
About CVE-2024-4577 PHP-CGI Vulnerability
The CVE–2024-4577 vulnerability allows an attacker to remotely execute malicious commands on Windows servers hosting a PHP system. The vulnerability is exploited through the PHP-CGI script engine, even if PHP is not configured in CGI mode. The PHP-CGI module is embedded in IIS web servers and XAMPP servers, which is a popular platform for hosting web applications.
This exploit is especially dangerous since PHP and XAMPP are widely used and the vulnerability is easy to exploit, involves remote code execution (RCE), and a malicious payload proof-of-concept (PoC) is already available.
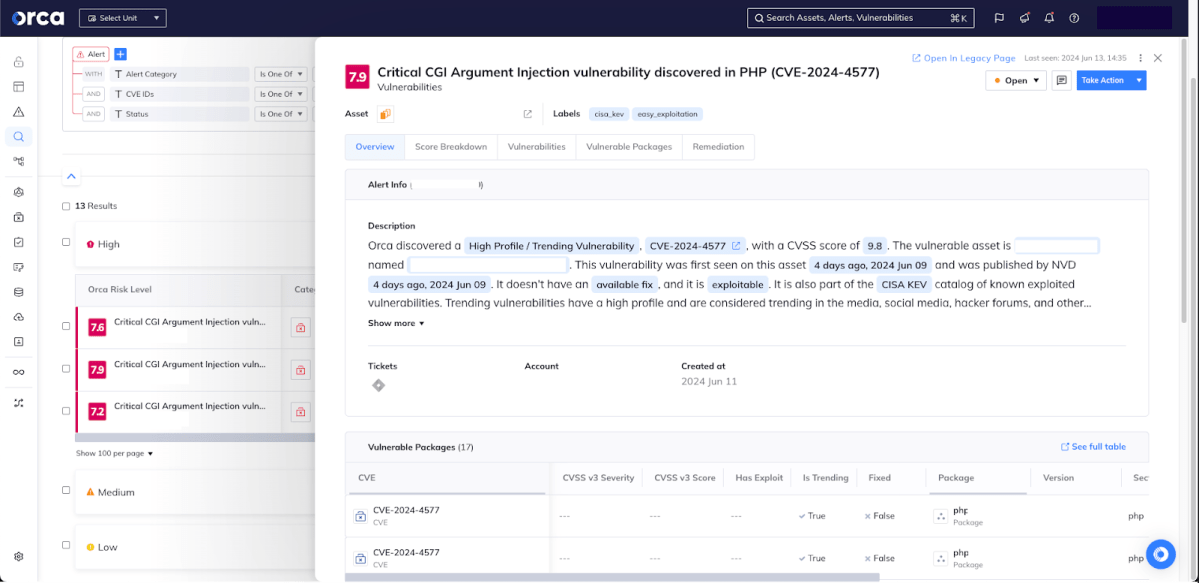
This vulnerability has been assigned the identifier CVE-2024-4577 with a CVSS score of 9.8 (Critical). Known exploit code exists and it is listed in the CISA KEV (Known Exploited Vulnerabilities) catalog. As of June 13th, it has an EPSS Probability Score of 93.20%, indicating that it is very likely to be exploited in the near future wherever the vulnerability exists.
For this reason, it is extremely important to follow the mitigation instructions described below, to ensure that your environment is not vulnerable. But before you can start mitigating, you first need to understand if and where you are vulnerable.
What is XAMPP?
XAMPP is a cross-platform web server solution based on Apache HTTP Server, MariaDB database server, and script interpreters PHP and Perl. Because of the ease of deployment and the support for common applications such as WordPress and Joomla!, XAMPP is a popular platform for hosting web applications and might be the most common deployment of PHP.
XAMPP is a recursive algorithm meaning “XAMPP Apache + MariaDB + PHP + Perl”.
The Exploit
The original exploit, which allows RCE on PHP servers, was discovered back in 2012 and patched as CVE-2012-1823. Recently, however, a new exploit has been detected that reopens this vulnerability. The attack targets XAMPP PHP servers running on Windows operating systems, specifically when PHP is configured to run in CGI mode (Common Gateway Interface).
By default, XAMPP servers are vulnerable when Windows is set to use traditional Chinese or Japanese settings combined with “Best Fit” encoding. This setup allows for argument injection by malicious actors. Although researchers have only tested these specific languages, other languages except English could potentially be at risk. The exploit can also be executed without CGI if the directories containing php.exe and php-cgi.exe are accessible by the web server, which is the default configuration in XAMPP for Windows.
Vulnerable Versions and Platforms
The known exploit code affects XAMPP running on Windows with traditional/simplified Chinese or Japanese settings. However, workloads using other languages besides English should be considered potentially exploitable.
PHP running on Windows outside of XAMPP is also potentially exploitable in the same configurations.
Affected Versions:
- 8.3 < 8.3.8
- 8.2 < 8.2.20
- 8.1 < 8.1.29
- 8.0
- 7 and 5 (which are no longer supported)
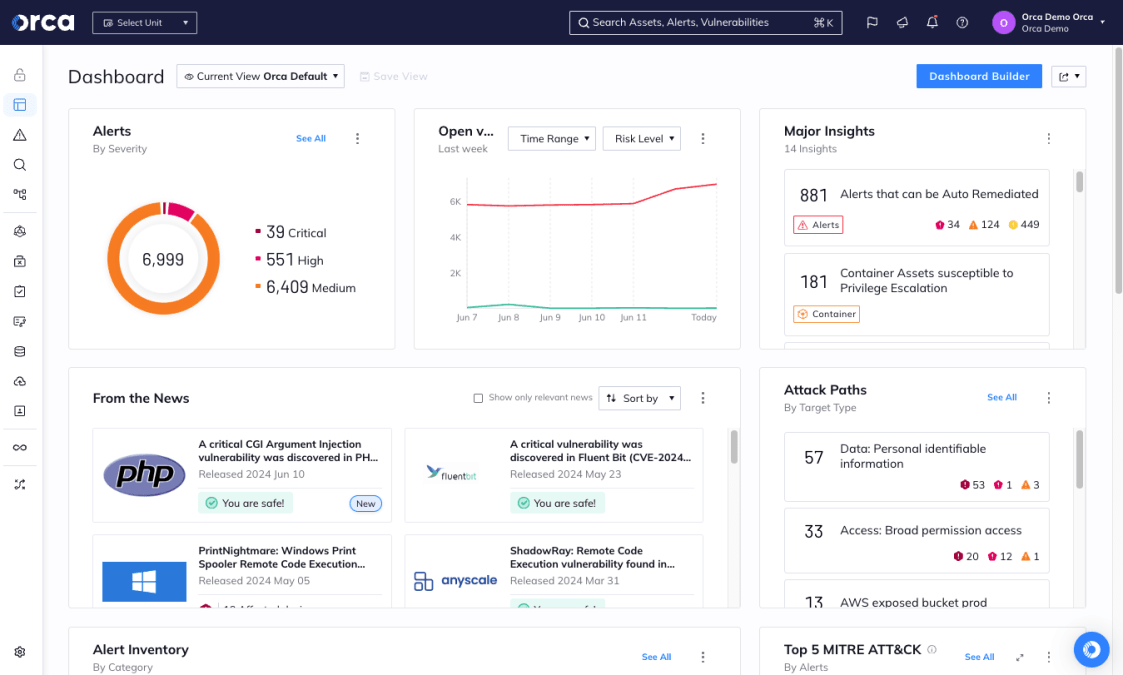
How does Orca help discover and mitigate PHP CGI Vulnerabilities?
To protect against this vulnerability, organizations should upgrade to the latest PHP versions: 8.3.8, 8.2.20, and 8.1.29. If you are unable to upgrade at this time, you should take additional action to mitigate the issue.
For administrators who do not need CGI, it is recommended to disable it:
- Open C:/xampp/apache/conf/extra/httpd-xampp.conf
- Locate the corresponding lines and comment them out:
# ScriptAlias /php-cgi/ "C:/xampp/php/"
For 8.0, 7 and 5 versions, another option is to apply what are known as rewrite rules such as:
RewriteEngine On
RewriteCond %{QUERY_STRING} ^%ad [NC]
RewriteRule .? - [F,L]How does Orca help?
The Orca Cloud Security Platform performs comprehensive vulnerability management and automatically detects CVE-2024-4577 in vulnerable workloads on AWS, Azure, Google Cloud, Kubernetes, and more. Once detected, Orca helps you remove any risk by providing easy-to-follow mitigation instructions. Orca can also create custom mitigation code for your tool of choice (e.g. CLI, console, IaC tools) using built-in Generative AI remediation.
Since Orca has full visibility into your cloud environments, it ensures that no vulnerable assets are overlooked or missed through blind spots.
Learn More
Orca Security is trusted by hundreds of organizations and provides comprehensive, AI-driven cloud security that is easy to use and provides 100% coverage. After a simple 30-minute deployment, Orca will start scanning and within hours show you all the risks in your cloud workloads, configurations, and identities and which ones are the most critical – all from a single platform.
If you would like to learn more about the Orca Platform, schedule a 1:1 personalized demo with one of our experts.





