On Friday, July 19th, 2024, CrowdStrike customers experienced a major outage impacting Windows systems running the Falcon Sensor. This outage was caused by a bugcheck, otherwise known as a Blue Screen of Death (BSOD), resulting in affected systems continually rebooting. The impact is ongoing, but is clearly significant and has caused numerous issues across industries as highlighted in breaking news articles.
Finding assets affected by Crowdstrike update
Because Orca’s patented agentless approach provides organizations with comprehensive visibility into deployed assets even when the assets are crashing or stopped, the Orca Cloud Security Platform enables security and operations teams to quickly find virtual machines that this issue might impact, a critical first step in assessing and responding. Teams can start with the “From the News” widget in your dashboard to understand the CrowdStrike issue with a single click:
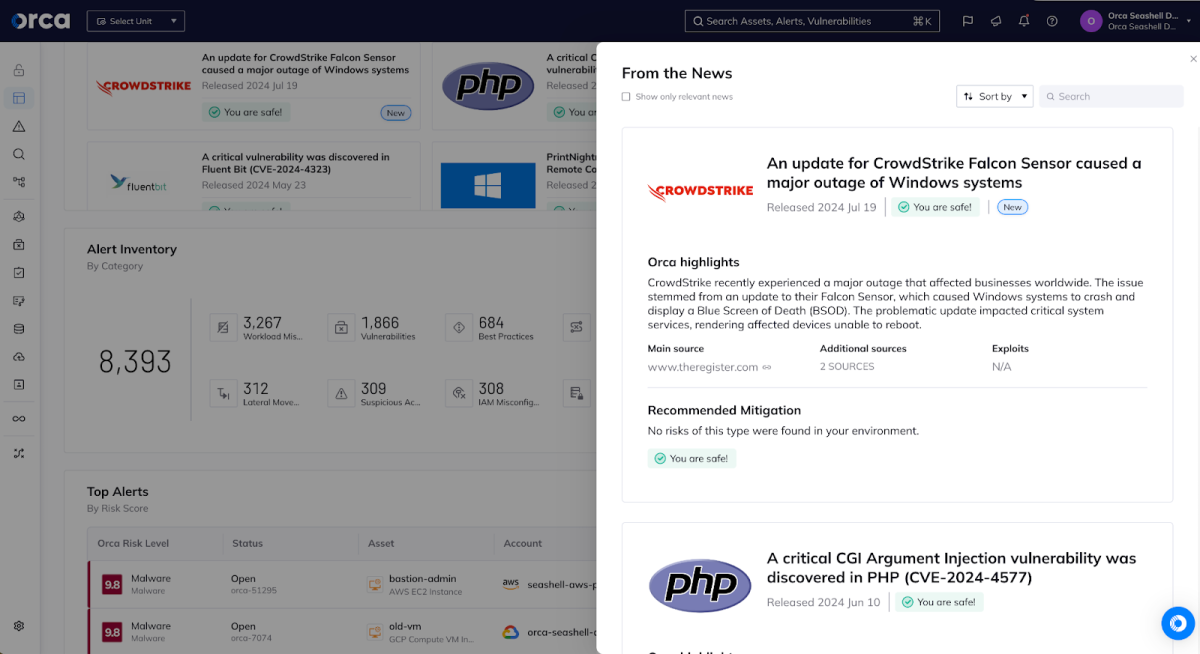
From the News shows trending news stories and automatically queries your environment for impact
From here, organizations may want to use Discovery to identify specific assets that may be impacted (US Global / South America / Europe / Australia / India / Gov Cloud). This is easily accomplished as Orca models the presence of the Falcon Sensor on workloads, so a query like this would identify all Windows workloads with Falcon deployed:
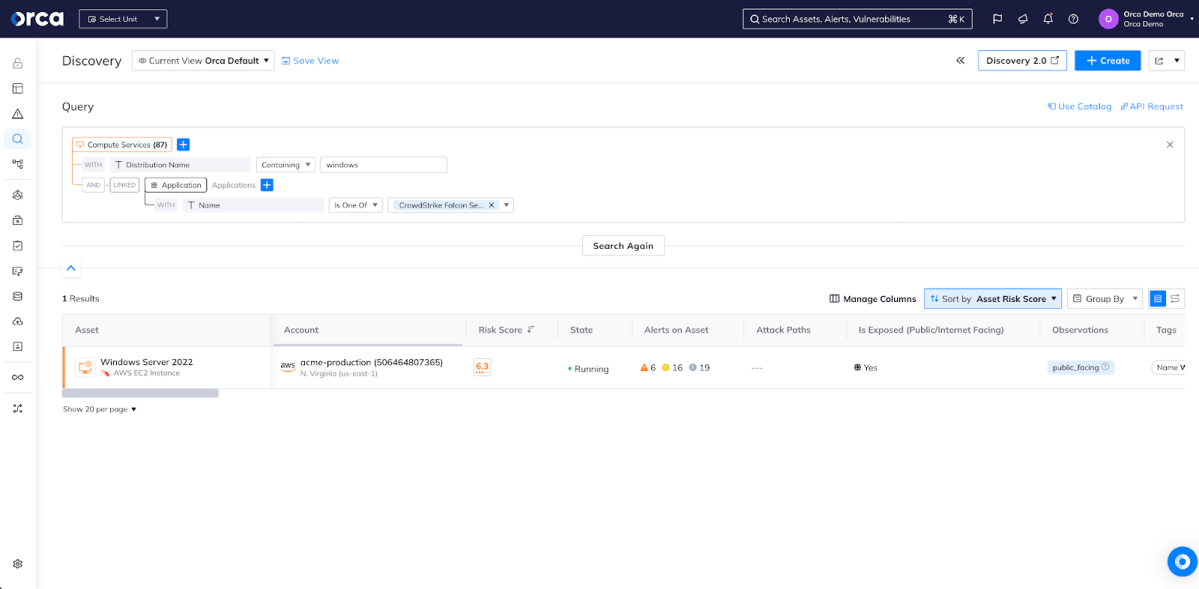
This query is available in Orca Security’s Discovery Query Catalog as “VMs with CrowdStrike Falcon Sensor agent application running on Windows” in the General Discovery category.
Discovery AI makes this even easier. Asking Orca “What assets do I have that are running Windows and CrowdStrike?” will answer the question without further work.
Remediation for VMs in the cloud
The initial remediation guidance instructs users to boot into Windows Safe Mode in order to remove a file; however, unfortunately, this guidance isn’t helpful for cloud-deployed virtual machines. There are at least two possible approaches to addressing this for VMs in the cloud.
First, if possible, restore from a backup taken prior to the last CrowdStrike update.
If restoring from a backup isn’t possible, you can:
- Attach the VM’s OS disk to another virtual machine. (The exact instructions for this will differ from cloud to cloud.)
- Delete
Windows/System32/Drivers/CrowdStrike/C00000291*.sys - Detach the disk and re-attach it to the affected VM.
Connect with our team
Orca Security is here to help. If you would like to learn more about the Orca Platform and see how it could help you investigate and remediate issues like this one, please contact us.





