S3 Bucket Allows Public READ Access
Hazardous (3)
AWS Well-Architected Framework, GDPR, NIST 800-53 (Rev. 4), PCI DSS
About S3 Buckets
Amazon Simple Storage Service (S3) provides the ability to store, retrieve, access, and backup any amount of data.
S3 storage can be used for a variety of use-cases and applications; from data lakes and big data analytics, to web apps, enterprise applications, and data archiving. S3 is object-based storage, which means that everything is stored as objects within buckets.
Each object has three main components: the object’s content, the object’s unique identifier, and the object’s metadata (including its name, size, and URL). An object cannot be independent; it must exist within a bucket. There can be hundreds of buckets within an Amazon account and hundreds of objects within a bucket.
S3 buckets are designed to store mission-critical sensitive data. However, AWS S3 bucket misconfigurations can put you at risk of a data breach, so applying the recommended security configuration policies is critical.
It’s easy to create S3 buckets, but it’s even easier to make mistakes that can potentially expose your infrastructure to security threats. One such mistake is allowing public READ access to an S3 bucket.
Cloud Risk Description
Even though by default an S3 bucket is always created as “private,” misconfigurations and human error can sometimes expose them to the public internet. On AWS, you can use Identity and Access Management (IAM) policies, bucket policies, and access control lists (ACLs) to define access policies for your buckets. Misconfigurations in any of these three policies can lead to an S3 bucket being exposed to the public. Moreover, sometimes, inexperienced engineers/administrators may allow public READ access while integrating with a trusted third party.
An S3 bucket that allows public READ (LIST) access can be exploited by a malicious actor to list the objects within the bucket. They can use this information to identify objects with ACL misconfigurations and then access those objects.
Unauthorized access to said objects can lead to data and/or service loss.
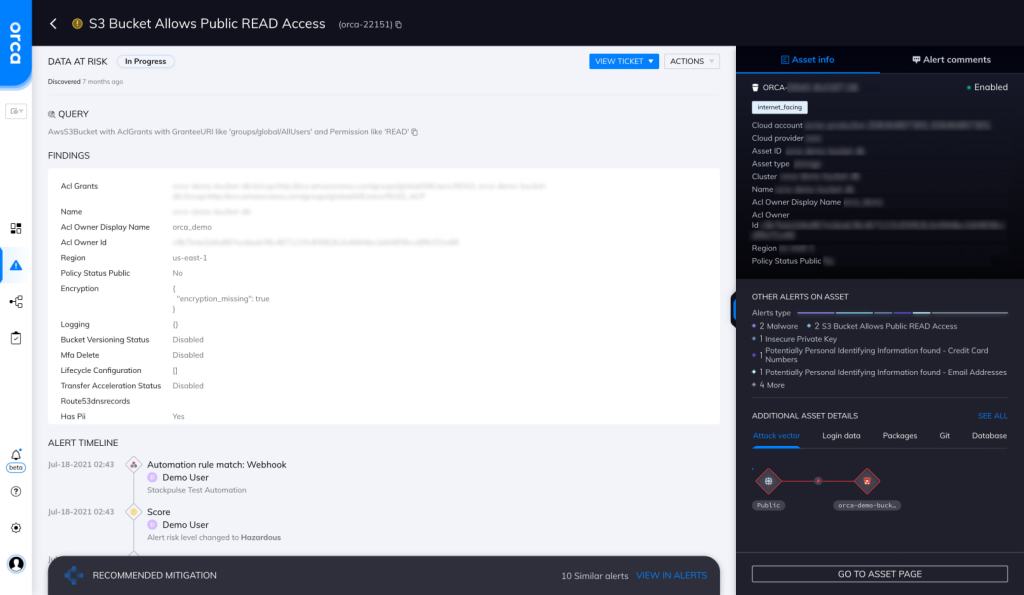
How Does Orca Help?
Orca detects and prioritizes common and obscure IAM misconfigurations that put your storage buckets at risk. Orca looks for “S3 Buckets that Allow Public READ Access” and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Use the principle of least privilege
Give people the bare minimum level of access privileges that they need to do their job.
-
Use encryption
Ensure that your S3 buckets are encrypted by default.
-
Enable the “Block public access” option
From your AWS console, enable the “block public access” option for all the buckets and accounts that you don’t want to publicly expose.
-
Monitor continuously
Have a dedicated team monitor and audit your S3 resources for any discrepancies or potential misconfigurations.
-
Enable MFA delete
MFA (multi-factor authentication) delete requires the user to provide a secondary authentication factor, before deleting an S3 bucket object.
Useful Links
- Leaky Buckets: 10 of the worst S3 breaches: https://businessinsights.bitdefender.com/worst-amazon-breaches
- Best security practices for S3: https://docs.aws.amazon.com/AmazonS3/latest/userguide/security-best-practices.html
- S3 FAQs: https://aws.amazon.com/s3/faqs/
- Data protection in S3: https://docs.aws.amazon.com/AmazonS3/latest/userguide/DataDurability.html
- Protecting data using encryption: https://docs.aws.amazon.com/AmazonS3/latest/userguide/UsingEncryption.html
- Monitoring Amazon S3: https://docs.aws.amazon.com/AmazonS3/latest/userguide/monitoring-overview.html
- Creating and configuring S3 buckets: https://docs.aws.amazon.com/AmazonS3/latest/userguide/creating-buckets-s3.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
