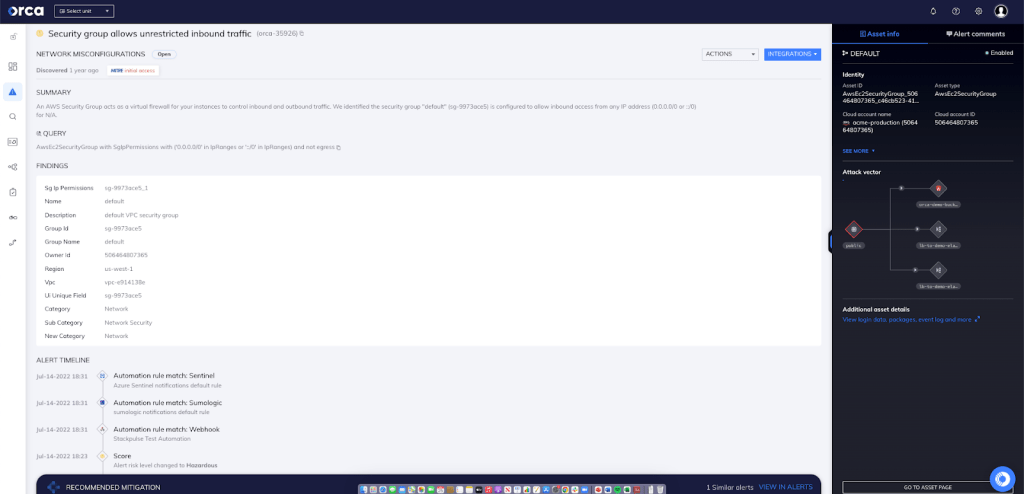
Security group allows unrestricted inbound traffic
Hazardous (3)
CCM-CSA, CSA CCM, HITRUST, Orca Best Practices
About Security Groups in AWS
AWS security groups act as virtual firewalls to protect your instances from unauthorized access. Security groups allow you to define a set of rules to regulate the flow of incoming and outgoing traffic of an instance. .
Security group rules can only be permissive. You cannot create rules that deny access. If you don’t add any rules to a security group, then all inbound traffic is blocked by default. The opposite is true for outgoing traffic: by default, security groups allow all outgoing traffic.
A rule is made up of the following information:
Protocols: Which protocols are allowed? ( for example, TCP, UDP, ICMP)
Port range: Which system ports should be open for traffic?
IPs: Which source and destination IPs or IP groups are whitelisted?
You can create security groups directly from the Amazon EC2 console. You can also add or remove rules to a security group at any time. The changes are propagated to all the instances that are linked to the security group.
Security group rules should be created and applied with care. A misconfigured rule can put you at risk of unauthorized access. Even though there are several best practices to follow, the most important one is to always apply the principle of least privilege.
Cloud Risk Description
According to the principle of least privilege, a security group should be configured to allow the bare minimum flow of incoming/outgoing traffic. If a security group allows unrestricted inbound traffic, then virtually anyone on the internet can access that instance. This is a serious violation of the principle of least privilege and puts your instance/network at serious risk of compromise.
How Can Orca Help?
Orca identifies, analyzes, and prioritizes network misconfigurations such as overly permissive network access controls. In this specific case, Orca helps by looking for “Security Group Allows Unrestricted Inbound Traffic” and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Audit for security groups that allow unrestricted inbound traffic and remove/modify the permissive rule(s) immediately.
-
While creating rules for custom security groups, adhere to the principle of least privilege.
-
As a rule of thumb, a security group shouldn’t allow a large range of ports to be open.
-
Identify and delete any unused security groups.
-
Create different security groups, with personalized rules, for instances that serve different purposes.
Useful Links
- AWS security groups: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-security-groups.html
- Default and custom security groups: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/default-custom-security-groups.html
- Security group rules: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-rules.html
- Security group rules for different use-cases: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-rules-reference.html
- Creating security groups: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/working-with-security-groups.html#creating-security-group
- Security group connection tracking: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-connection-tracking.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
