Serverless computing continues to gain popularity among organizations—and for good reason. By eliminating the responsibility of infrastructure management, the deployment method lets teams deploy and scale code without worrying about provisioning, patching, or maintaining servers. In fact, Forrester reports an increase in “serverless-first” strategies, as organizations look to simplify cloud-native development and operations.
But this simplicity doesn’t translate to security. The ephemeral nature of serverless functions makes it significantly harder to gain the visibility and control required for effective threat detection and response. This may help explain recent findings from the PwC 2025 Global Digital Trust Insights Report, in which CISOs reported cloud-related threats as their top cybersecurity concern and weakness.
To help teams close the security gap, Orca is pleased to introduce new runtime capabilities that extend to serverless applications. With this update, the Orca Sensor now covers serverless containers running on AWS Fargate—delivering real-time visibility, monitoring, and detection in environments notoriously difficult to secure.
What is serverless security?
Serverless computing eliminates the burden of managing cloud infrastructure, but it doesn’t remove the need to secure workloads and in many ways introduces new security challenges. Serverless functions are short-lived, stateless, and often event-triggered, making them difficult to secure using traditional runtime tools.
These characteristics can leave room for attackers to exploit vulnerabilities, inject malicious code, or trigger costly denial-of-wallet attacks. Organizations need serverless-specific runtime protections that can keep up with the pace and nature of these environments.
The Orca Cloud Security Platform integrates directly with AWS Lambda, Google Cloud Functions, and Azure Functions to protect serverless functions and identify, prioritize, and remediate their associated risks.
Leveraging our patented SideScanning™ technology, the Orca Platform scans and automatically inventories all serverless deployments across your entire cloud estate—with no impact on workloads. This scanning analyzes active functions, runtimes in use, networking configurations, and misconfigurations to prioritize serverless alerts that impact your security posture.
Orca detects a variety of serverless risks, some of which include:
- Environment variables exposing secrets
- Elevated permissions
- Vulnerabilities
- Unsupported runtimes
Why is Orca offering serverless runtime protection?
Orca is pleased to extend coverage of Orca Sensor to serverless environments, enabling organizations to effectively address:
- Increased adoption of serverless platforms like AWS Fargate.
- Limited visibility and detection in fast-moving, ephemeral environments.
- Protection gap left by current runtime tools, which only secure traditional container environments.
- Infrastructure limitations or deployment complexity that prevent runtime monitoring for serverless environments.
This release addresses these challenges directly, extending the advanced capabilities of Orca Sensor beyond Kubernetes clusters and virtual machines to serverless workloads.
What features are included with Orca’s serverless runtime protection?
The enhancement offers several important capabilities, including:
#1. Real-time detection of malicious activity
Challenge: Serverless functions don’t run continuously and are designed to terminate quickly after execution. This stateless behavior makes it difficult to monitor for threats using conventional tools. Threat actors can exploit this gap, injecting malicious inputs or executing unauthorized code in a brief window of time.
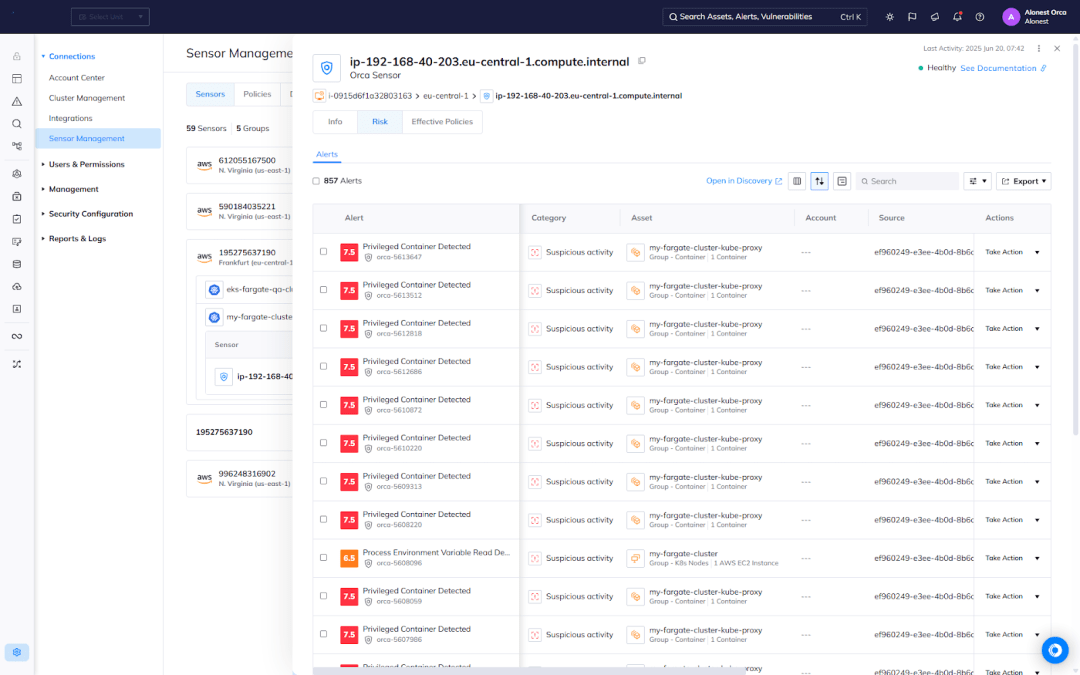
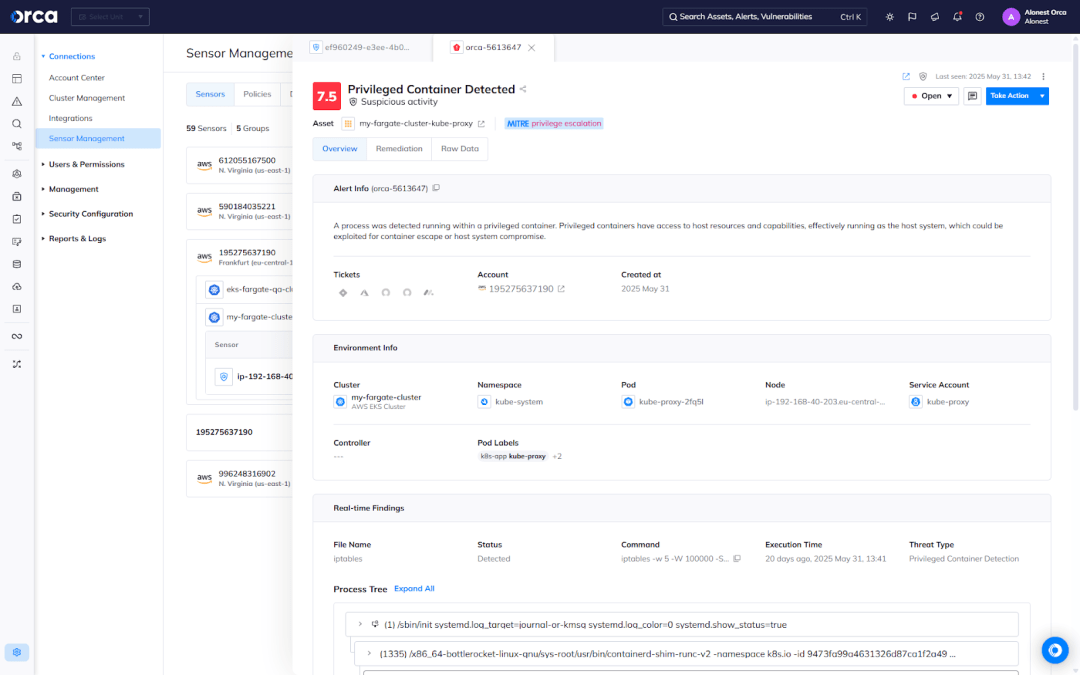
Solution: Orca Sensor enables continuous runtime monitoring, even in environments where functions may only run for seconds. It detects malicious activity such as privilege escalation, suspicious network activity, and execution anomalies—providing timely insights and automated alerts as soon as threats surface.
#2. Automated enforcement of runtime security policies
Challenge: Security teams are often overwhelmed. Research shows they can remediate just 1 in 10 vulnerabilities detected monthly. Meanwhile, vulnerability exploitation contributes to more than a third of data breaches, and many security teams lack the automation needed to respond at runtime.
Solution: Orca Sensor provides out-of-the-box runtime policies tailored for serverless use cases. Teams can enable policies as needed, triggering automatic detection and enforcement tailored to their unique circumstances.
#3. Container-level insights for investigation
Challenge: Investigating incidents in ephemeral workloads is notoriously difficult. Traditional forensics often requires node-level agents or privileged access—both impractical in serverless environments.
Solution: Orca Sensor integrates directly into existing AWS Fargate environments, requiring no architectural changes or privileged access. It captures logs, configurations, application data, and other runtime insights so security teams can get the context needed to understand root causes, scope incidents, and respond with precision.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of Orca Sensor and Orca Cloud Security Platform? Schedule a personalized 1:1 demo.






