Risk prioritization is a foundational requirement for effective cloud security. Security platforms typically generate many alerts. When you consider that security teams—often understaffed and overworked, and working under heavy pressure—are generally monitoring several tools simultaneously, that’s a lot to handle.
The Need for Strategic Remediation
The remedy, of course, is to remediate strategically and allow your cloud security platform to tell you:
- Which alerts are the most urgent and demand your immediate attention
- Which are of intermediate concern and should be dealt with as soon as you can but probably not critical for this exact moment
- Which alerts to be aware of but with remediation likely not as urgent
Orca Security recently rolled out a new alert scoring system, called the ‘Orca Risk Score,’ with the objective of providing customers a clear, easy-to-understand scoring system that aligns with industry standards and empowers customers to get a granular understanding of risk priority and tackle alerts strategically.
The Orca Risk Score ranges from 1-10 and includes one decimal to further fine-tune the priority of the alert. The score is determined by considering the full contextual picture of the risk and the surrounding cloud environment, giving you the information needed to understand the severity and urgency of each alert. Orca determines which risks are the most critical, so you don’t have to.
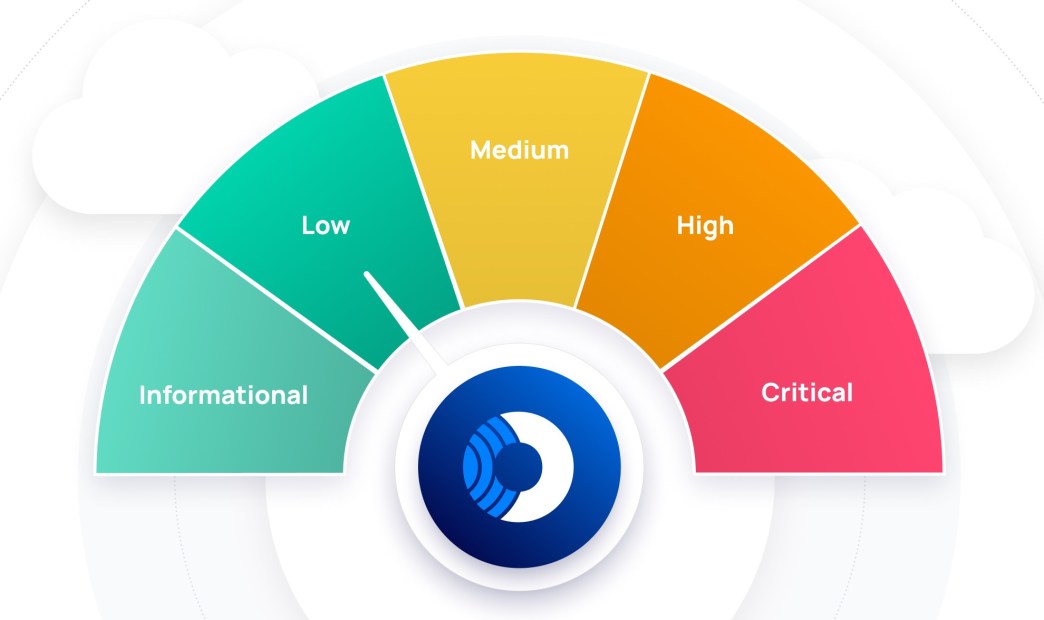
Orca Scoring Risk Levels
When viewing the Alerts page in the Orca Platform, the alerts are divided into the following risk levels:
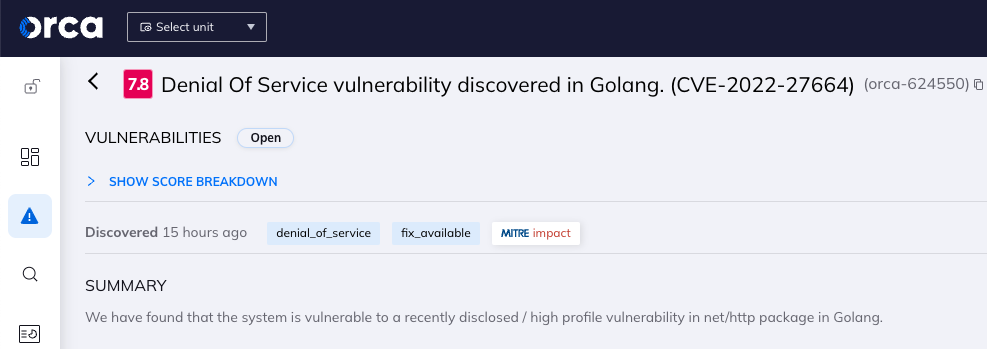
- Critical, (score 9.0 -10.0) – Alerts detected with a critical risk score have a high probability factor and/or the impact may be critical to the organization. Example: Malicious code was detected and malicious activity with a high confidence level was detected on the resource. (see example in the above screenshot).
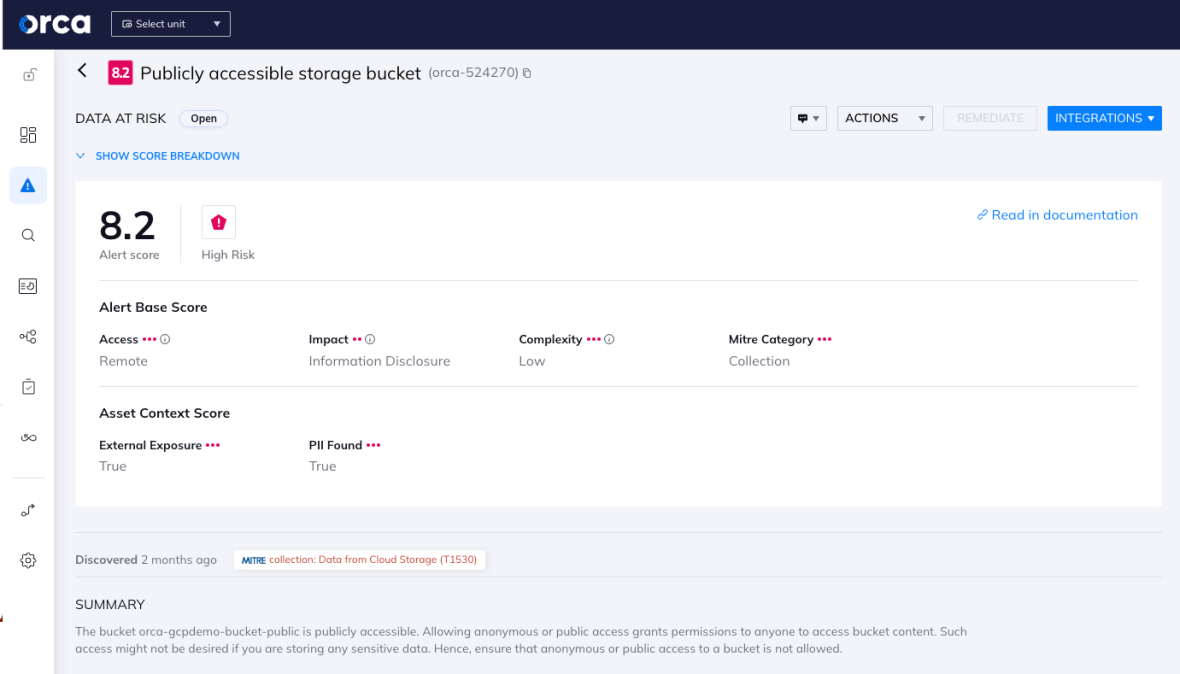
- High, (score 7.0 – 8.9) – Alerts detected with a high risk severity have a high/medium probability factor and/or the impact may be high to the organization. Example: Publicly accessible storage bucket that contains PII (see screenshot in the Scoring driven by risk and asset context section below).
- Medium, (score 5.0 – 6.9) – Alerts detected with a medium risk severity, have a medium probability factor and/or the impact may be medium to the organization. Examples: IAM role with administrative privileges, Azure guest user with a permissive role assignment, and Privileged group with unused service access.
- Low, (score 3.0 – 4.9) – Alerts detected with low-risk severity, have a low/medium probability factor and/or the impact may be low to the organization. Examples: EBS volume with no recent snapshots and Controller of pods with default service account.
- Informational, (score 1.0 – 2.9) – Alerts with no clear attack vector that pose minimal risk to the organization. Example: S3 bucket should use transfer acceleration.
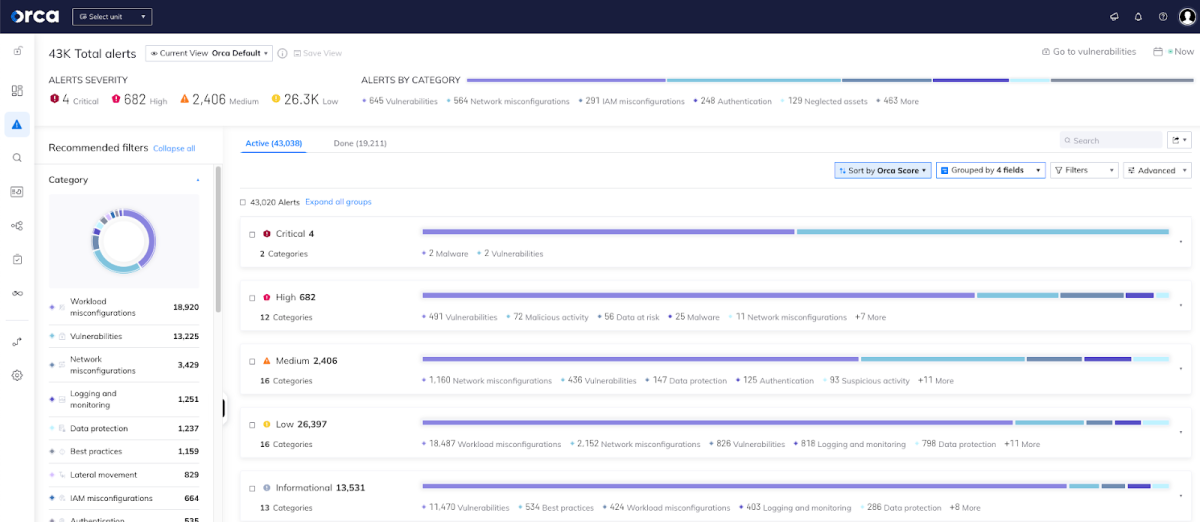
Orca divides and prioritizes alerts in 5 risk levels.
Alerts are grouped both by risk level (Critical, High, etc.) and by their numerical score. This allows for more granular risk prioritization, even within a particular risk level. For example, within the category of “High” alerts, you can see different scores. Or you may find several alerts about sensitive AWS keys being found on a virtual machine, but within those you’ll find some that are scored higher than others.
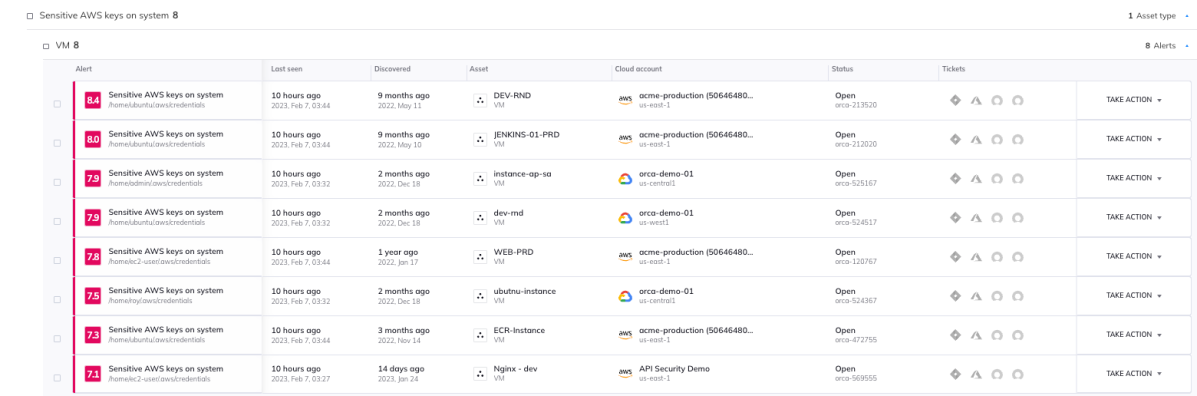
Different risk scores for alerts on sensitive AWS keys
Scoring Driven by Risk and Asset Context
The Orca Risk Score for each alert is determined by two subscores: an alert base score and an asset context score.
- The Alert Base Score is a standalone score that shows the alert’s risk and its potential impact. It consists of the following metrics:
- Access: The access needed in order to exploit or use the given risk.
- Impact: The potential impact that the given alert has the potential to have. For example, information disclosure or account takeover.
- Complexity: The complexity of exploiting the given vulnerability: low, medium, or high.
- MITRE Category: The category of the MITRE ATT&CK framework of attacker tactics and techniques the alert is most aligned with.
- The Asset Context Score gives us the asset’s background, and is based on the asset’s configuration. Meaning that if the asset’s configuration changes, so too can this score. Each asset consists of different unique parameters, based on its features. These include whether or not the asset is exposed to the internet, if it contains personal identifiable information (PII), whether it is currently running or paused, if there are additional detected vulnerabilities, and more.
Gain Insight into the Severity of Risks Found in Your Cloud Environment
Ready to try it out in your own cloud environment? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address cloud risks. Since the Orca Platform is agentless, you will be up and running with minimal effort.