Cloud security, at its core, is a simple problem.
It’s not about a specific vulnerability, misconfiguration, or identity issue. It’s not just about risks in Kubernetes or APIs. It’s about identifying the potential problems in your environment that could land you on the front page of the newspaper—and not in a good way.
I frame it in non-technical terms because that’s what security leaders care about. They want to understand their most critical risks and fix them as efficiently as possible, reducing exposure and saving valuable resources. They want to simplify the process—making it easier and more effective. That’s the real challenge of cloud security.
Simplifying cloud security
When we talk about simplifying cloud security, we can define it a number of ways. First, it means gaining full coverage of the risks in your environment without creating friction for you or your team. This means eliminating the need to ask engineers to install an agent, change a configuration, or perform other tasks to get the visibility you require. Simple also means receiving alerts that cover all types of risks—whether a vulnerability, misconfiguration, sensitive data issue, or identity risk.
But simplicity goes beyond coverage. It’s also about knowing which risks matter most. This means being able to analyze them across a variety of factors and within the full context of your cloud environment.
Security tools notoriously inundate teams with static alerts about a critical vulnerability here, a critical misconfiguration there. Often, these alerts don’t turn out to be critical, but they’re not false-positives either—they just lack important business context. For example, a “critical” vulnerability might affect an unexposed system or a cloud resource without access to sensitive data. Static analysis only considers the ease of picking the lock, not who can reach it or what’s behind it.
Combining several ‘best-of-breed’ solutions fails to address the core issue. If you use a tool for vulnerability management, one for posture management, and another for data discovery, prioritization becomes nearly impossible. Your team can choose to solve the top 10 vulnerabilities, data issues, or identity issues—but they can’t connect the dots. They won’t see how a vulnerability could amplify a data risk, or how multiple issues from different categories could create a dangerous attack path.
So, simplifying cloud security calls for not just gaining full coverage and detecting all risks, but analyzing them holistically and contextually. This philosophy led to our founding of Orca Security. Back then, the industry was fragmented, and no solution offered complete visibility. Fast-forward to today, cloud security is still hampered by technology that analyzes risks in silos and fails to fully contextualize their business impact.
This eventually led us to introduce Attack Path Analysis, a key feature of the Orca Cloud Security Platform. Orca’s Attack Path Analysis automatically surfaces dangerous risk combinations that could allow an attacker to compromise a high-value asset.
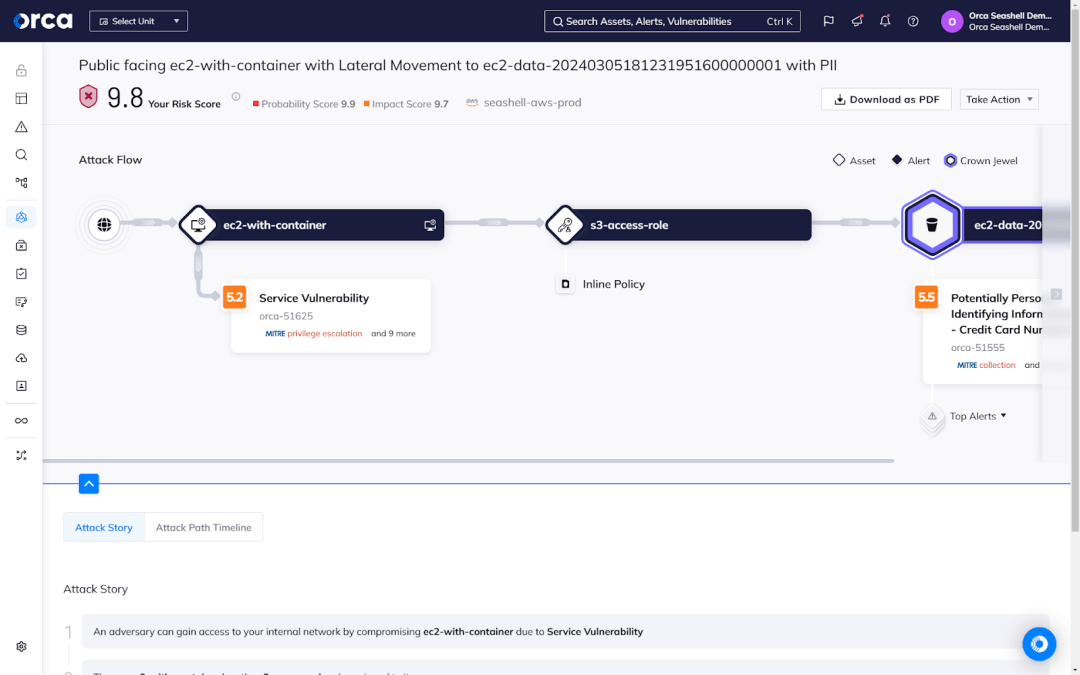
By consolidating different risk types into a single platform, we can identify the entire attack path, remediate a key risk, and break the kill chain. This approach dramatically simplifies the process of determining and prioritizing critical risks.
And it helps address the real business problem that keeps executives awake at night: identifying the risks could land you on the front page of the newspaper. Attack paths can do that. 99.9% of high-severity vulnerabilities, on the other hand, won’t—either because they’re not exposed or they don’t provide access to anything sensitive.
Providing the closest thing to self-driving cloud security
The future of cloud security is moving beyond raising alerts to actually preventing risk and streamlining remediation. With full visibility and effective risk prioritization, you establish the foundation to fortify your security in two important ways.
The first involves setting guardrails to prevent issues from resurfacing in production—because nobody wants to go through the endless cycle of detecting a risk, fixing it, only to see it resurface.
The second involves simplifying the remediation process in production. Even after prioritizing your most critical risks, your teams still have considerable work to do. The aim here is to reduce that workload so you can do more with fewer resources.
Some may point to auto-remediation and AI as solutions. To put these solutions in the proper perspective, I use the analogy of self-driving cars to cloud security. Today, self-driving cars may support fully autonomous driving in some areas, but for the most part they provide only assistance.
Cloud security works the same way. Auto-remediation serves certain use cases and does the work for us. But for most situations, it doesn’t serve as a viable solution. We still need to make decisions and work with engineering to build workflows that address issues. Most cases demand human intervention, which technology should simplify and make seamless.
Part of simplifying remediation calls for integrating cloud security technology with the right tools used by different teams. For engineering, this may mean ticketing systems such as Jira or ServiceNow. For a SOC team, it may point to a SIEM or SOAR solution. You need to establish shared communication channels and a common language for cloud security across all teams.
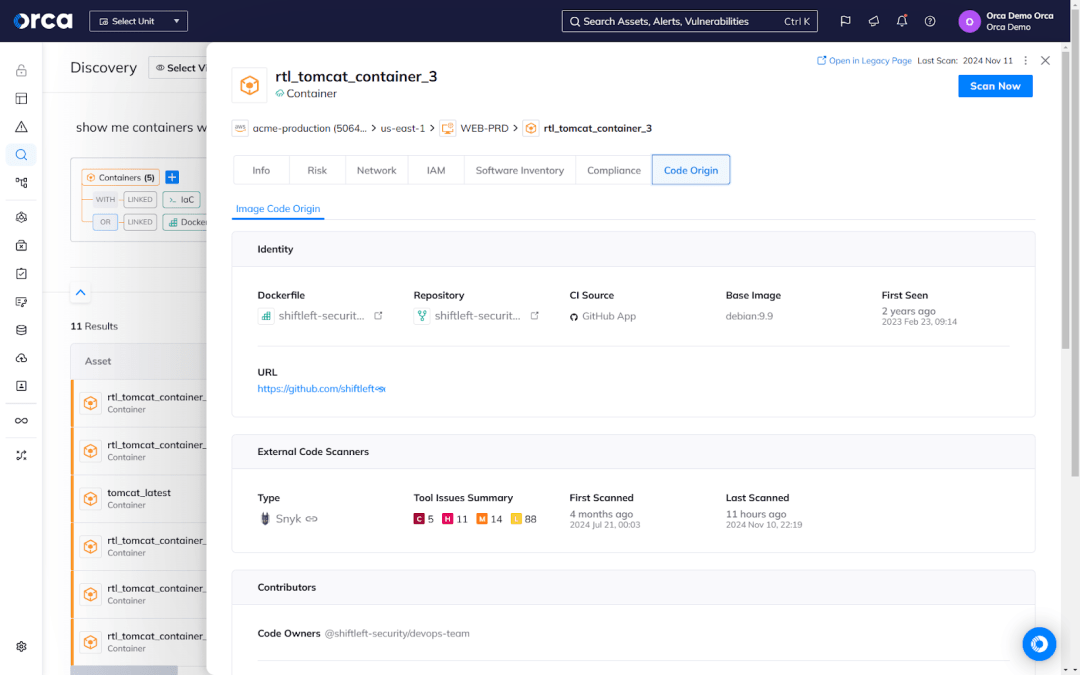
Another part of simplifying remediation is proper attribution. When security teams see an alert in production, they usually see a vulnerable, exploited, or misconfigured asset. And to resolve the issue, they need to track down the person responsible for it. In traditional environments, this was straightforward—there was a clear owner to patch the problem. But in modern development environments, the asset is usually the product of an Infrastructure-as-Code (IaC) artifact or the CI/CD pipeline. This means security teams must hunt down the person who wrote the problematic code.
I’ve seen security teams spend as much as 30% of their time tracking down code owners. That’s why we introduced the Cloud-to-Dev feature at Orca. It links the production issue directly to its code origin, making it easy for security teams to discover the issue at its source and communicate with developers in a way they understand.
This saves both teams significant time to focus on higher-value priorities. While it doesn’t fully automate the process—similar to how self-driving cars still run in the assistive phase—it significantly reduces the manual effort involved.
Solving the real business problem
At the end of the day, cloud security isn’t about a specific technology or product category—it’s about solving the real business problem of preventing a breach. And preventing a breach means eliminating all the friction of cloud security, while dramatically reducing the effort to detect and remediate your most critical and exploitable risks.
That’s the way we define our product at Orca. It frees us from the constraints of product acronyms so we can focus on what truly matters: helping you avoid what keeps you up at night.
Learn More
Interested in discovering the benefits of the Orca Cloud Security Platform? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can optimize your risk reduction ROI.






