Cloud storage buckets, such as Amazon S3 Buckets, Azure Blob storage and GCP storage buckets, are a popular storage solution for many organizations. In fact, we found that nearly all (99%) of Orca customers are using at least one type of storage bucket. Given the many advantages storage buckets offer, this is not surprising: these cloud repositories are highly scalable and cost-effective, and they simplify sharing for remote collaboration purposes.
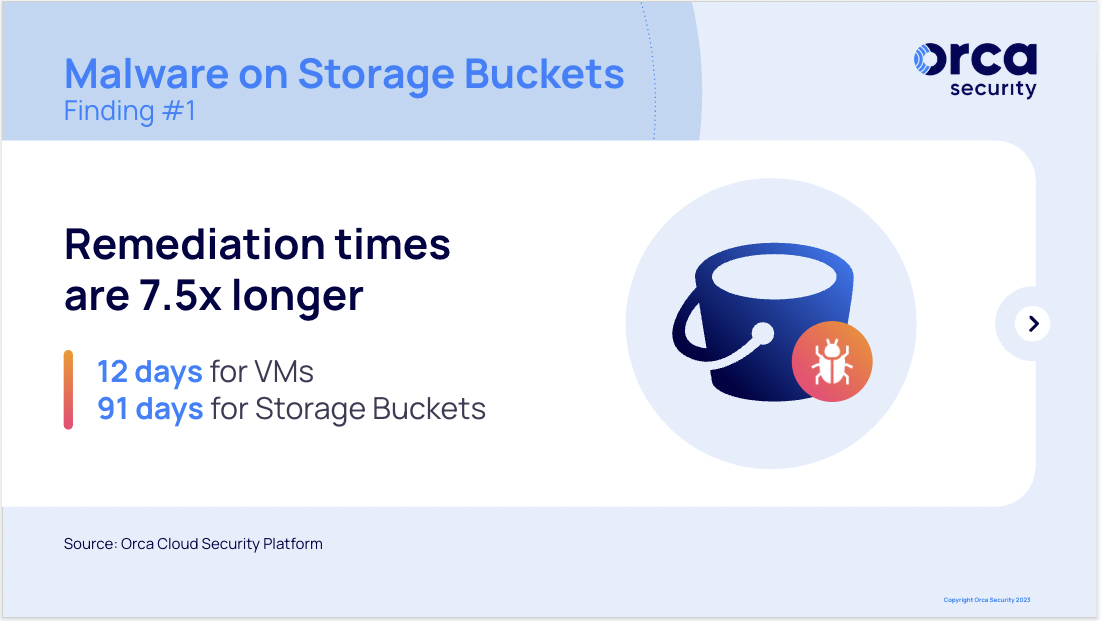
However, storage buckets are also susceptible to misconfigurations as well as malware and viruses introduced through infected files or phishing attacks. Whereas there is heightened awareness around storage bucket misconfigurations, the risk of malware in storage buckets is often underestimated. Analyzing data from our Orca platform, we found that on average it takes organizations 12 days to remediate malware on VMs, but 91 days to address malware in storage buckets, which is 7.5x longer.
Since storage buckets don’t have an OS, there seems to be a general perception that malware on buckets is not as dangerous as on other assets. This is surprising, especially given that cloud storage buckets often include ingested data from third-party providers and can contain sensitive data: we found that 21% of organizations have at least one bucket with Personally Identifiable Information (PII).

In this blog, we debunk the myth that malware on storage buckets is less dangerous than on other assets, and what needs to be done to protect against this risk.
Misconfiguration Risks on Storage Buckets
There have been several well-publicized instances where Amazon S3 Buckets and Azure Blob Storage containers have been accessed by bad actors, leading to data breaches. Most of these cases were the direct result of misconfigurations, even though the default setting on, for instance, S3 buckets blocks public access. However, the frequency of these incidents spurred AWS to introduce changes going into effect in April 2023 to tighten the S3 Bucket configuration settings, making it more difficult to accidentally create or configure a bucket with public access.
Malware Risk on Storage Buckets
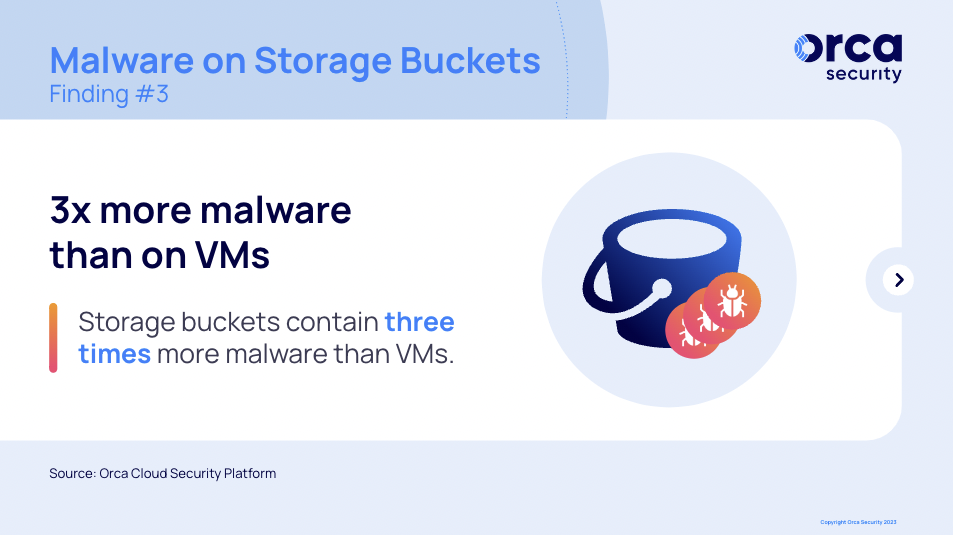
A far less publicized risk is the presence of viruses and malware on storage buckets. In our analysis of millions of workloads, we found that storage buckets contain 3x more malware than VMs, indicating that storage buckets are a popular target and that, as we have previously seen, teams are slower to remediate malware on storage buckets.
Even though malware cannot be executed on the bucket, it’s important to understand that the bucket is an instance type that usually serves a broad range of users and cloud resources. Because of this, malware in a storage bucket can have a far-reaching impact that in some cases can be even more severe than on other resource types.
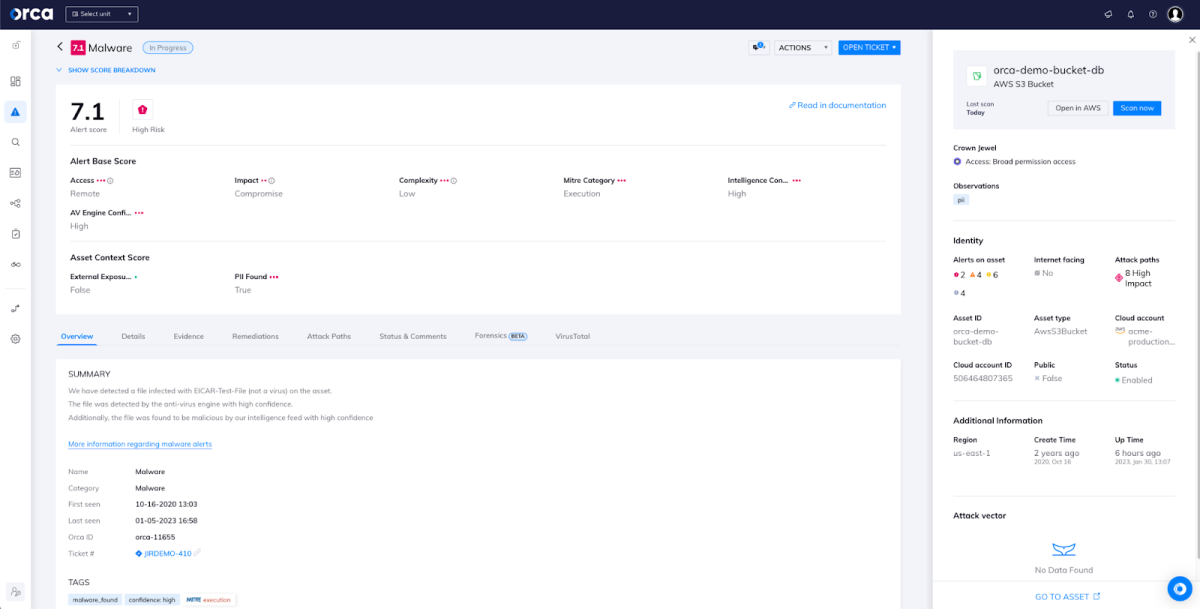
How Does Malware End Up in Buckets?
Malware can spread to storage buckets in a variety of ways. The most common way is an insecure configuration that allows websites and other resources to upload files to the bucket. Other ‘second hand’ malware infections include phishing attacks, unpatched software, and vulnerable applications. In addition, storage buckets can also be vulnerable to supply chain attacks, for instance if a third-party provider’s software has dependencies on libraries or packages that are infected with malware, and those dependencies are stored in a storage bucket, the malware may be introduced to the bucket when the dependencies are downloaded and installed.
Types of Malware on Storage Buckets
The types of malware on storage buckets, as detected by the Orca platform, are mostly trojans and scripts attempting to exploit a known CVE. A very small percentage are webshells.
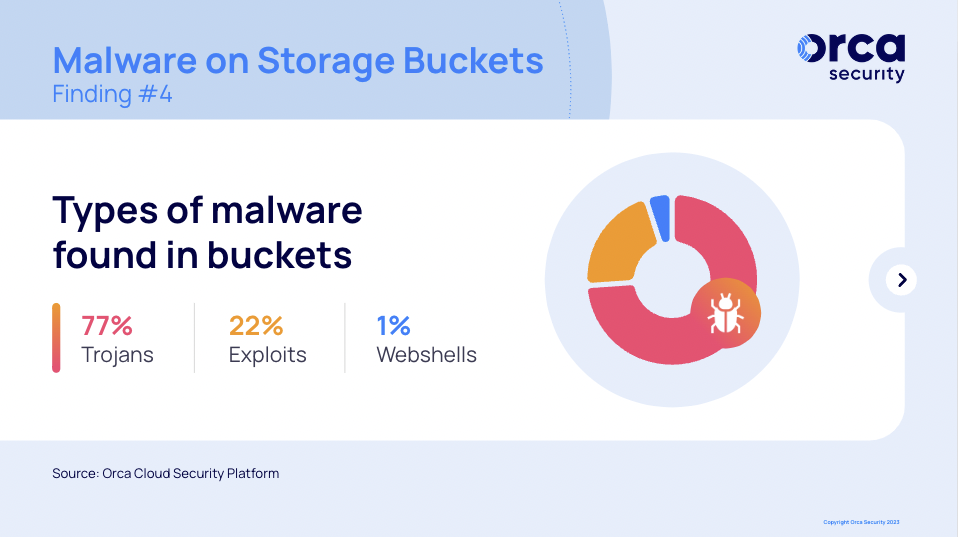
The distribution is as follows:
- Trojans (77%): Malware that’s designed to deceive users into thinking that it’s a legitimate software program or file, but carries out malicious activities once installed or executed, such as stealing data, taking control of the system, or downloading and installing other malware.
- Exploits (22%): A program designed to find and take advantage of a system vulnerability to gain unauthorized access, steal data, or carry out other malicious activities.
- Webshells (1%): Malicious software that allows an attacker to remotely access, execute commands, and perform various malicious activities on a web server.
Risks That Can Arise From Malware on Buckets
The risk of malware in a storage bucket is different from other cloud assets, mainly because a bucket cannot actually run files. But this does not mean that malware in storage buckets is not dangerous; the risk here is in the connections that the bucket has with other resources in the environment. Below we list the three main risks:
#1 Malware Persistence
The first risk is when a Compute resource, such as a VM, has permissions to fetch files from the storage bucket. With a relatively innocent script from the Compute side, it could fetch the malicious files, execute the malicious code or fetch parts of it, and disappear not long afterwards. This technique is an easy way to evade detection and maintain quiet persistence. Such malicious processes could be used to steal information, change configurations and more.
#2 Malware Propagation
Another risk is when a storage bucket is running a website. The Orca platform data shows that around 60% of the organizations that use storage buckets are running a website on it. Most of them (75%), are also serving external users. The presence of malware in such a bucket could expose the website users to the malware stored in the bucket, including internal and external users.

#3 Phishing Attacks
In a similar way, compromised websites on storage buckets can also be used in a spear phishing attempt to lure unsuspecting employees to download malware from what seems to be a safe source since it’s in the company’s cloud. By exploiting the integrity of the website on the storage bucket, an attacker could spread malware within the organization and perform other malicious activity.
How Can You Protect Against Malware on Storage Buckets?
The good news is that there are several actions organizations can take to minimize the occurrence and impact of malware on storage buckets:
- Limit permissions: Ensure that storage bucket permissions are configured to adhere to the least-privilege principle and that write access is limited only to trusted sources.
- Monitor activity: Implement logging and monitoring to detect suspicious behavior and events.
- Scan for malware and vulnerabilities: Deploy tools that detect malware and vulnerabilities. Make sure the tool you use not only finds known malware by using signatures, but also uses heuristic scanning to detect unknown malware and zero-day threats.
- Set security requirements for external providers: Only allow trusted third-party providers with a proven security track record and appropriate security certifications to access your buckets.
- Apply updates: Keep your software and dependencies up to date to reduce the risk of vulnerabilities being exploited.
- Prioritize remediation: If you cannot remediate all instances of malware on storage buckets, make sure you prioritize those buckets that contain sensitive information and/or are connected to the greatest number of instances, since a breach of these buckets could cause the greatest impact to the business.
How Can Orca Security Help?
Orca offers a cloud security platform that provides complete malware coverage of your cloud estate, including storage buckets, with zero performance impact. Orca takes snapshots from outside your running environment and scans cloud assets for malware using a variety of techniques. In addition to signature-based detection, Orca uses advanced heuristic methods such as file analysis, file emulation, and generic signature detection.
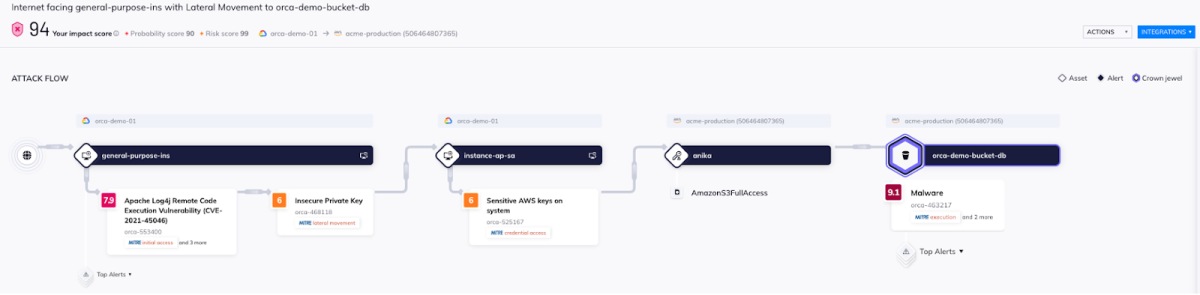
Orca shows all the attack paths leading to and from the storage bucket, and provides remediation steps for both the malware and the attack paths related to it, prioritizing risks that have the largest blast radius and potentially expose sensitive data.
Do You Have Malware in Your Storage Buckets?
Take Orca’s free risk assessment and find out. After a quick setup, Orca’s agentless Cloud Security Platform will scan your entire cloud environment, surfacing all critical risks, including any malware on cloud storage buckets. After the 30-day trial, we will also send you a detailed summary of all the cloud security risks we found.





