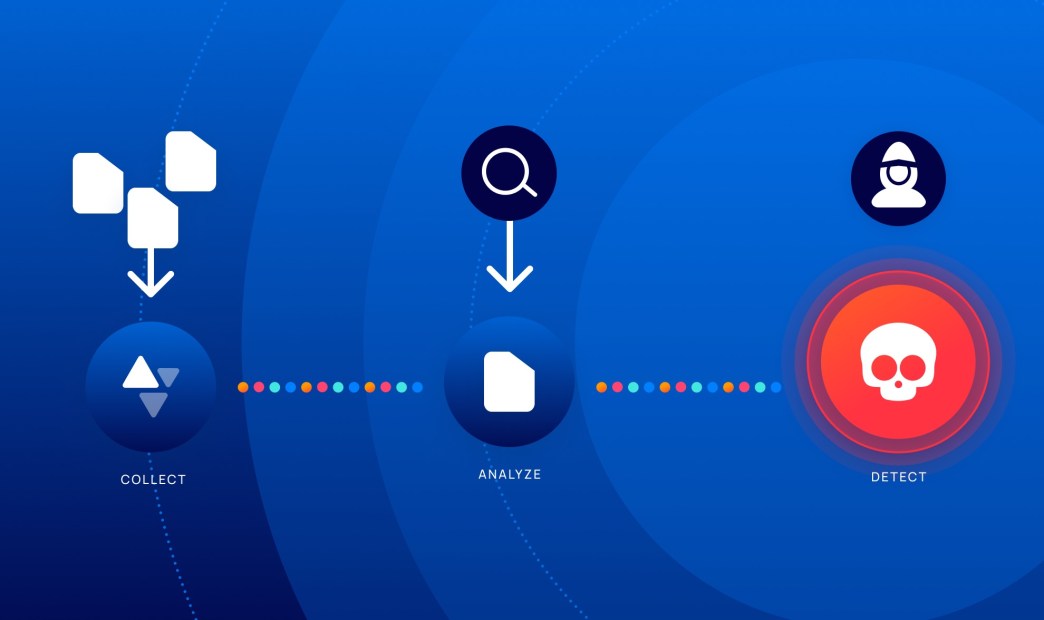
One of the offerings in the Orca Cloud Security Platform is Cloud Detection and Response (CDR), which allows organizations to detect active attacks in their cloud environments, quickly understand the context and potential severity, and respond as effectively as possible.
A new feature that we recently added to our CDR capabilities is the ability for organizations to create their own alerts on specific events and behaviors they want to track. By enabling organizations to create their own alerts in addition to the pre-existing alerts, security teams can tailor their cloud monitoring activities to a granular level and ensure that alerts are set to their individual requirements.
Orca’s Cloud Detection and Response Capabilities
Orca provides 24×7 monitoring of cloud provider logs, including AWS, Azure, and Google Cloud, as well as threat intelligence feeds to uncover malicious and suspicious activities, using anomaly detection enforced with AI. By consolidating this anomaly intelligence with security information collected from workloads, configurations and identities in a unified data model, Orca Security has insight into the full context of risks, enabling it to accurately understand which behaviors and events could potentially put the organization’s most critical assets at risk.
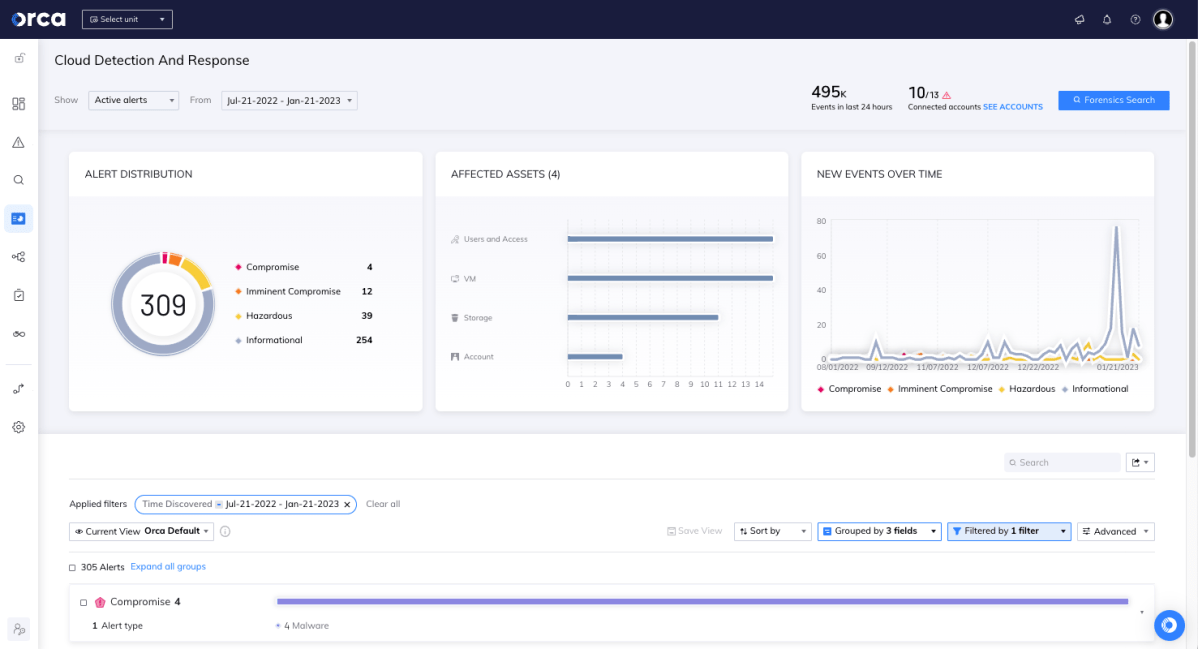
Detect, Investigate and Respond to Cloud Attacks
With Orca’s CDR capabilities, organizations can detect, investigate, and respond to cloud attacks in progress.
- Detect: Receive alerts when changes and anomalies occur that indicate possible malicious intent versus normal behavior, automatically prioritizing events that endanger the company’s most critical assets.
- Investigate: Research malicious activity to quickly gain insight into whether the events are malicious and if any of the organization’s critical assets are in danger.
- Respond: Intercept cloud attacks by leveraging remediation steps and automatically assigning issues using Orca’s 40+ third-party technical integrations (including SOAR, notifications, and ticketing systems).
Creating Custom CDR Alerts
Orca recently added the ability for organizations to create custom alerts on specific events and behaviors they want to track. For instance, security teams might want to be alerted when certain actions are taken on classified resources or assets, or when changes are made to specific permissions used within the organization.
To create a custom CDR alert, users can choose to build their own alert from scratch, or use one of the 1,800+ built-in templates and modify these to suit their needs.
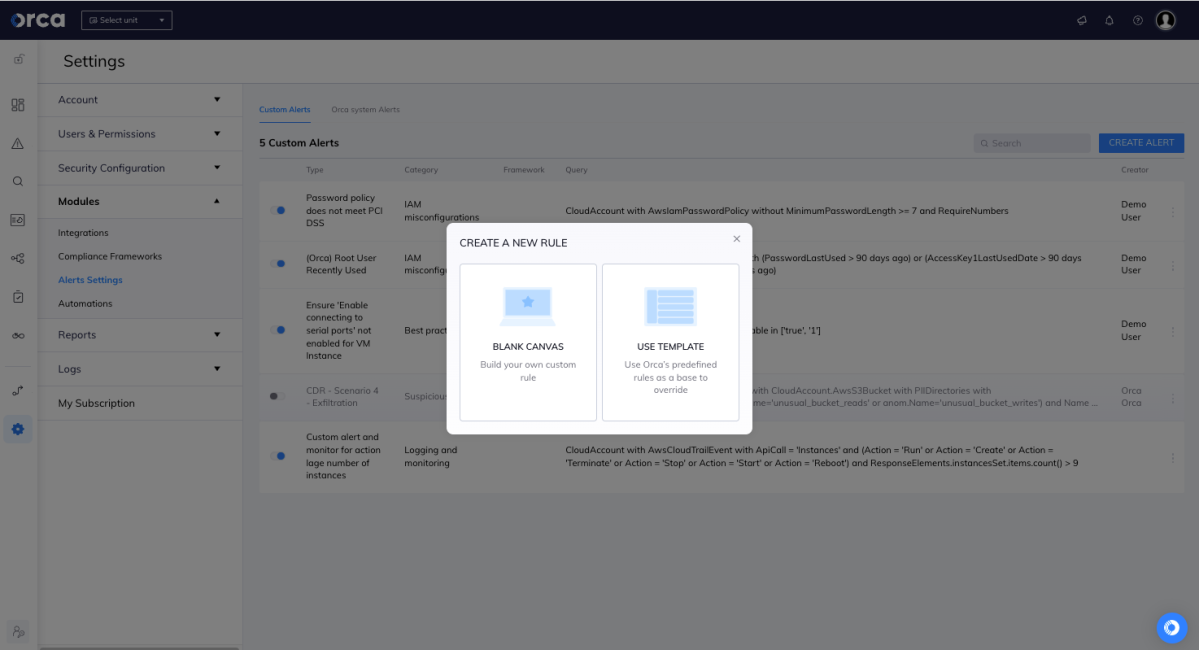
Orca’s intuitive query builder makes it easy to create and modify granular alert queries without requiring any developer experience. As users write a query, the query builder tests and validates rules and displays available attributes and commands to assist the user.
Using Orca’s Contextual Data for Risk Prioritization
Leveraging Orca’s unified, comprehensive cloud security platform that has visibility into every layer of your cloud estate, suspicious events and behaviors can be combined with relevant contextual data. For example, it is important to know whether the actions are being performed on an Internet-facing asset, whether the asset contains a vulnerability, if it opens up any lateral movement, and most importantly, whether it endangers the organization’s crown jewels.
By adding this contextual information, organizations can immediately assess the actual risk of the behaviors and events, avoiding false positives and ensuring malicious or dangerous actions are prioritized and addressed quickly.
Integrating Alerts Into Your Workflows
The Orca platform offers many integrations to allow organizations to incorporate and respond to cloud security alerts within their existing workflows. For instance, teams can configure alerts to automatically send notifications via email, PagerDuty, OpsGenie, or Slack, create tickets in Jira or ServiceNow, and much more. These integrations can help bridge the gap between security and DevOps/IT teams by automatically assigning alerts to the correct team members.
Examples of Custom CDR Alerts in Orca
Below we will discuss three examples of custom CDR alerts created in the Orca Cloud Security Platform for AWS, Azure and GCP.
AWS: Alert When an S3 Bucket with PII is Downloaded
In this example we created the following query to send out an alert when an S3 Bucket with PII is downloaded:
AwsS3Bucket with HasPii = true and CloudTrailEvents with EventName = "GetBucket"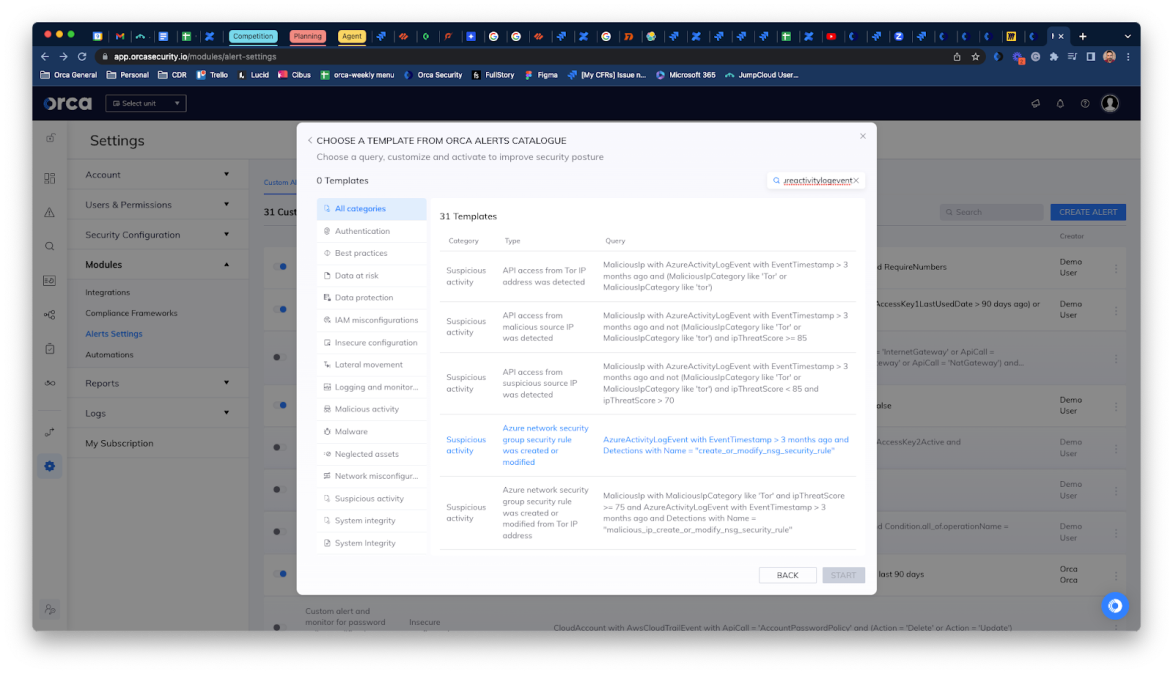
Azure: Alert When a Specific Network Security Group is Modified
To create this query we used the existing template ‘Azure network security group security rule was created or modified.’

The selected template included the following query:
AzureActivityLogEvent with EventTimestamp > 3 months ago and Detections with Name = “create_or_modified_nsg”Next, we updated the alert query so that it only alerts when a change is made to the resource group with the name “appX-prod”:
AzureActivityLogEvent with EventTimestamp > 3 months ago and Detections with Name = “create_or_modified_nsg” and ResourceGroupName = “appX-prod”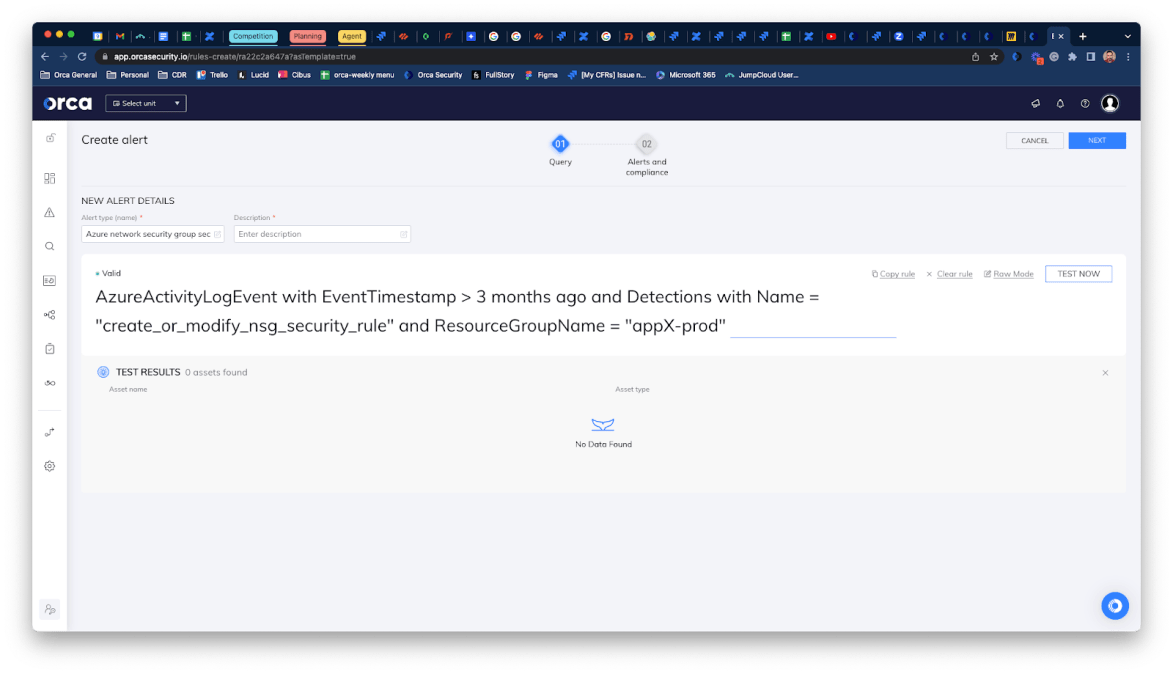
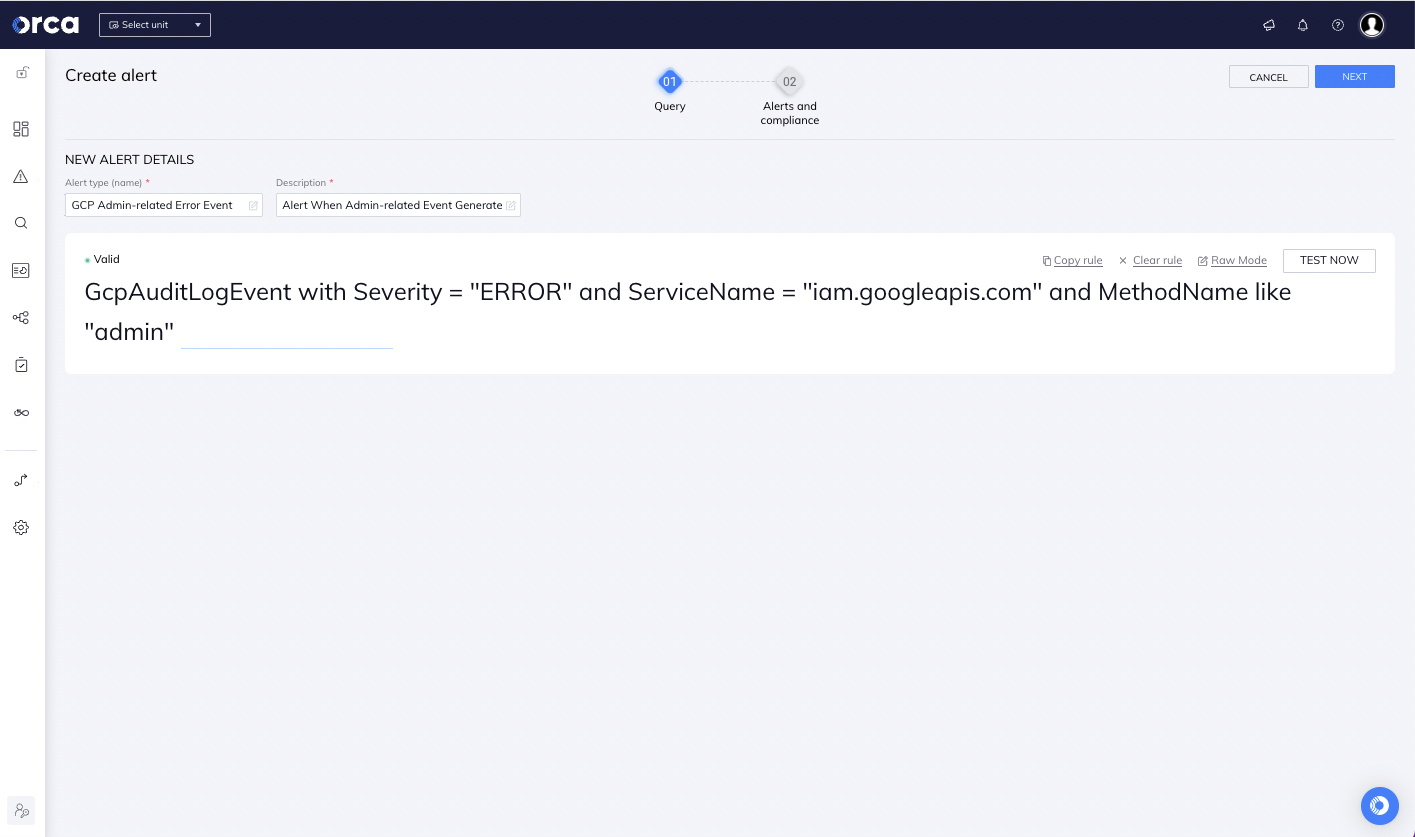
GCP: Alert When Admin-related Event Generates an Error
In this example, we created a query to send out an alert for all GCP IAM-related events (e.g., creating users or service accounts) with administrator permissions, that results in an error:
GcpAuditLogEvent with Severity = "ERROR" and ServiceName = "iam.googleapis.com" and MethodName like "admin"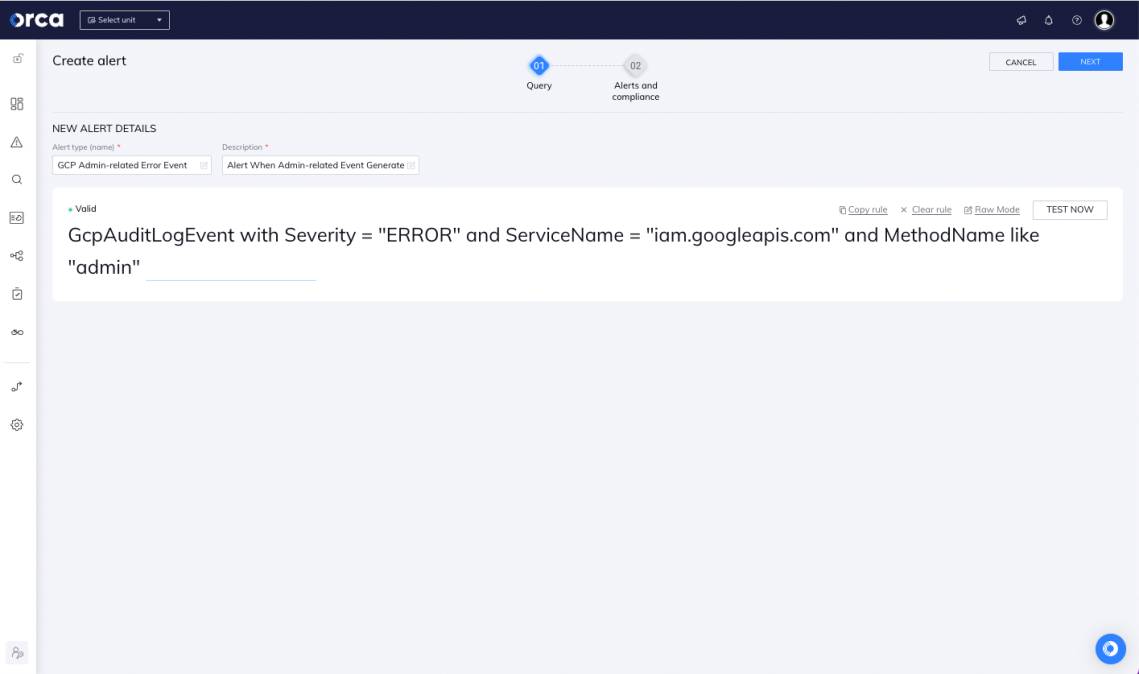
Learn more about CDR with Orca
As you can see from the examples above, it is easy to create granular CDR alerts in Orca, leveraging the rich data that Orca has gathered about your cloud workloads, configurations, and identities. Interested in trying it out for yourself? Watch a demo or take a free risk assessment. Since the Orca platform is agentless, you will be up and running with minimal effort.
About Orca Security
The Orca Cloud Security Platform identifies, prioritizes, and remediates risks and compliance issues across your cloud estate spanning AWS, Azure, Google Cloud, Alibaba Cloud, and Kubernetes. Leveraging its patented SideScanning technology, Orca offers comprehensive cloud security coverage detecting vulnerabilities, misconfigurations, lateral movement, API risks, sensitive data at risk, anomalous events and behaviors, and overly permissive identities. Instead of layering multiple siloed tools together or deploying cumbersome agents, Orca delivers complete cloud security in a single platform.