Technology should automate our processes and elevate our people. Orca Security enables your team to operate at a higher level by reducing the threshold of cloud security expertise needed. Whether that is someone well-versed in security transferring their skills to the cloud, or someone delivering solutions who now needs to be more security-focused. We continue to lead in the development of AI features to democratize security, but in this blog I’d like to focus on a real world use case.
External Exposure
External exposure is more than just what resources are connected to the internet. External exposure refers to the vulnerabilities and risks that an organization faces from its external environment. In other words, the complex interconnections between components that could expose data or a service externally.
Mapping this out, even in a public cloud environment where it’s slightly easier, is no small task. It’s not only the network configuration that needs to be analyzed, including components such as Virtual Private Clouds (VPCs) and Security Groups. It’s also the Identity and Access Management (IAM) of users, groups, roles, and policies. It’s also the configuration of the assets themselves – are there passwords in the shell history or insecure ssh keys?
Each Cloud Service Provider (CSP) will be configured slightly differently and use different terminology for each area.
How can we elevate our teams to perform at a higher level?
Understanding External Exposure to Cloud Assets
Here’s our graph visualization of your cloud assets in our refreshed asset inventory page. Let’s take a look:

Yes this is pretty, but how does pretty help people?
This is about making everyone a competent security professional regardless of if they’re specialism is in Operations rather than Security. In the example above I can very easily see how I get from a public network to a virtual machine in Google Cloud Platform (GCP). Without any specific GCP knowledge I can understand the components that grant this asset network access and then what service accounts are associated with it.
Quickly Viewing Risk Score as Part of Exposure
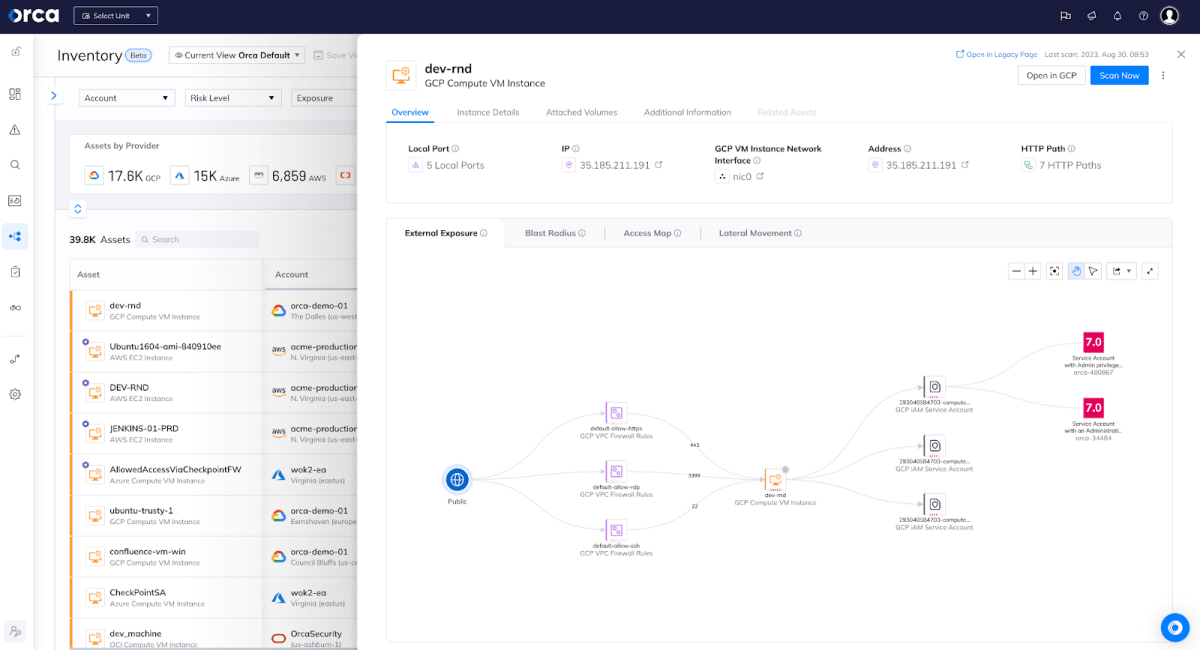
Now we have a very clear Orca Risk Score of 7.0 and, not to oversimplify, it’s red. The service account available to this asset has administrative privileges.
I didn’t need to know how to find and parse GCP VPC Firewall Rules (on the left of the diagram) or work out what service accounts were associated with a virtual machine in GCP or even what permissions they have. I have been able to clearly understand that these firewall rules are granting port access from the internet to an asset. I can see that the asset has permissions attached to it and those have alerts.
Cloud-Agnostic Security
This enables any technology professional to be able to understand the security risks cloud agnostically. This enables security professionals to operate confidently and competently in a public cloud environment.
We are really proud of all the features in our product that we roll out but it’s important to look at the overall picture – why does this help someone? How can we help people outside of security teams operate safely? This graph view truly democratizes security for the entire organization.
To see how Orca will elevate your people, why not get in touch for a personalized demo or view a demo on-demand.






