Unused Credentials Found
Informational (4)
APRA, MAS, NIST 800-53 (Rev. 4), The Center for Internet Security AWS Foundations Benchmark
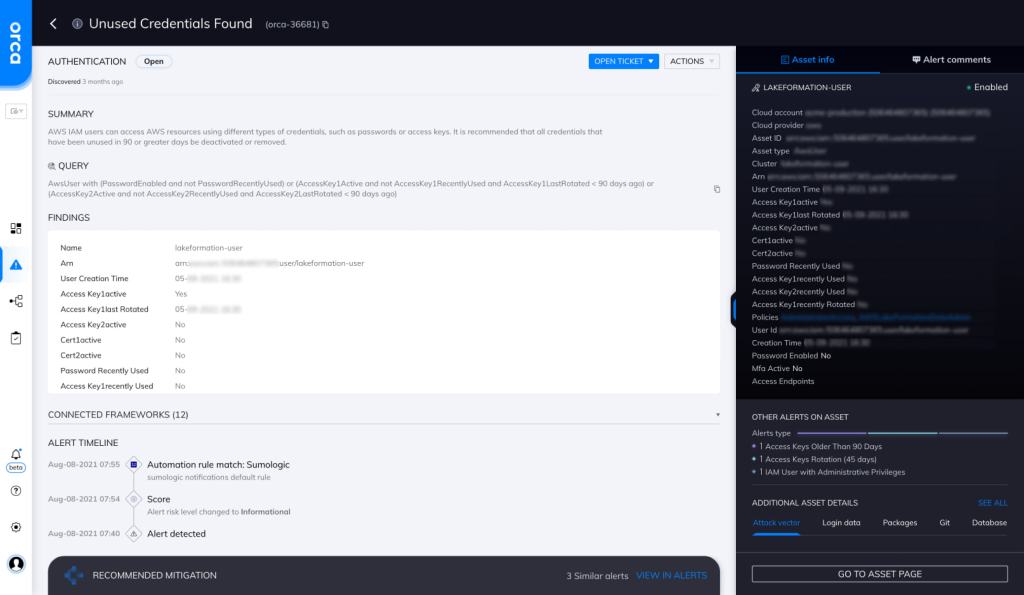
About Unused Credentials
Companies are implementing the zero-trust security model to secure distributed IT architectures. Zero trust assumes that no user or device (inside or outside the organization) is to be trusted. A primary tenet of zero trust is to revoke access privileges when they are no longer required.
“Unused” credentials can be defined as access keys and passwords that haven’t been used in a certain time period. The exact time period may differ based on company policy, but it shouldn’t be greater than 90 days.
Cloud Risk Description
Unused user passwords typically belong to people who are no longer employed by the organization or who no longer require access to a resource. Allowing these passwords to remain in effect enables users to illegitimately access company resources.
In addition to allowing unauthorized access, unused credentials are often at the heart of credential stuffing attacks. In such attacks, cybercriminals use leaked or stolen credentials of one website to log in to other websites. Since it’s common for people to use the same password or variations thereof for multiple accounts and websites, these attacks often succeed. If another company suffers a data breach and the stolen credentials include those of a former or current employee whose access hasn’t been properly deprovisioned, your system can be at risk of being compromised.
How Does Orca Help?
Orca employs multiple methods to identify poor password hygiene, including commonly used passwords, complex passwords that are reused across multiple applications and services, and highly secure passwords that have been leaked. Orca ensures password policy settings in your cloud meet industry guidelines around the use of MFA, minimum password length, use of special characters, password age, password reuse, and more.
Orca looks for unused credentials and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Use Temporary Credentials
Generate temporary credentials for users that require access for limited time periods. This is especially applicable when granting privileges to third parties such as contractors and partners.
-
Check for Unused Access
Set configuration rules that check for passwords and access keys that haven’t been used for a specified number of days. AWS, Google Cloud, and Azure have features to support this.
-
Quickly Act on Departing Employees
Formulate or refine your deprovisioning model to ensure that as soon as an employee leaves, all their accounts are deleted/deactivated, and privileges are revoked.
-
Use MFA
Wherever applicable, use multi-factor authentication (MFA). It adds an extra layer of security.
-
Enforce Strict Password Policies
Enforce a strict password policy. Encourage employees to set complicated passwords, which should not be reused for different accounts and should be changed periodically.
Useful Links
- AWS – Finding unused credentials: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_finding-unused.html
- Managing passwords for IAM users: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_passwords_admin-change-user.html
- AWS – Managing access keys: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html
- API security best practices: https://developers.google.com/maps/api-security-best-practices
- Security best practices in IAM: https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
- AWS – using temporary credentials: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_use-resources.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
