IAM Role with Administrative Privileges
Hazardous (3)
- Brazilian General Data Protection (LGPD) ,
- CCM-CSA ,
- CCPA ,
- cis_8 ,
- GDPR ,
- HITRUST ,
- ISO/IEC 27001 ,
- Mitre ATT&CK v12 ,
- New Zealand Information Security Manual ,
- NIST 800-171 ,
- NIST 800-53 ,
- UK Cyber Essentials
About IAM Roles
An IAM role in an AWS account is an identity with specific permissions that dictate what actions the identity can perform and which resources it can access. Unlike IAM users, IAM roles are not bound to a single person and can be assumed by anyone that is authorized to do so.
There are no long-term or indefinite security credentials associated with a role. Instead, short-term credentials are issued whenever a user assumes a role. Roles provide a great way to delegate access to users or applications that don’t usually need access to your resources. With that said, extra care should be taken to adhere to the Principle of Least Privilege (PoLP), ensuring that minimum access is given to the fewest number of people.
For example, let’s suppose your security team needs access to a testbed environment that’s normally only used by your developers. You can create a new IAM role in the testbed account and set its policy such that only your security team can assume it.
The permissions policy JSON defined for a role determines the actions and resources that the assuming user has access to. As a golden rule, never define an IAM role with full administrative privileges.
Cloud Risk Description
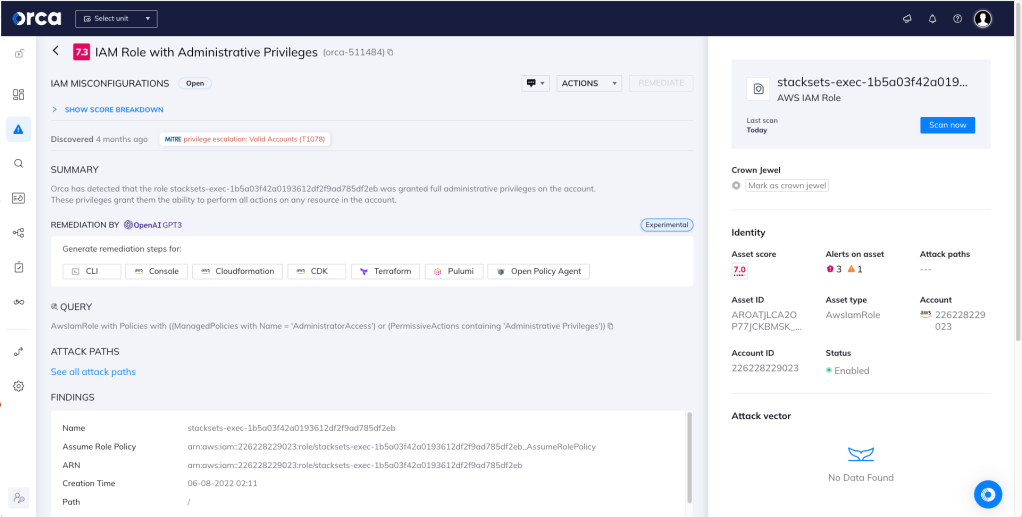
An IAM role was detected with full administrative privileges. Anyone who assumes the role will have the ability to perform any action on any resource in the account. This violates the PoLP and increases the risk of account takeover.
How Orca Can Help
Orca detects and prioritizes cloud identity and access management misconfigurations such as overly permissive identities. Continuous IAM monitoring across your cloud estate prevents malicious and accidental exposure. In this specific case, Orca helps by looking for “IAM Role with Administrative Privileges” and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Always adhere to the Principle of Least Privilege when writing policies for roles.
-
Audit for roles with administrative privileges and update their policies.
-
Use IAM Access Analyzer to validate all the policies that you create.
-
Use MFA to protect cross-account access.
-
Create a password policy for your AWS account that requires users to set strong passwords and change them periodically.
-
Remove any unnecessary or unused IAM roles from your AWS account.
Useful Links
- 2022 State of Public Cloud Security Report: https://orca.security/lp/2022-state-public-cloud-security-report/
- IAM JSON policy: https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies.html
- IAM roles glossary: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_terms-and-concepts.html
- Common scenarios for roles: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios.html
- Creating IAM roles: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create.html
- Best security practices in IAM: https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
