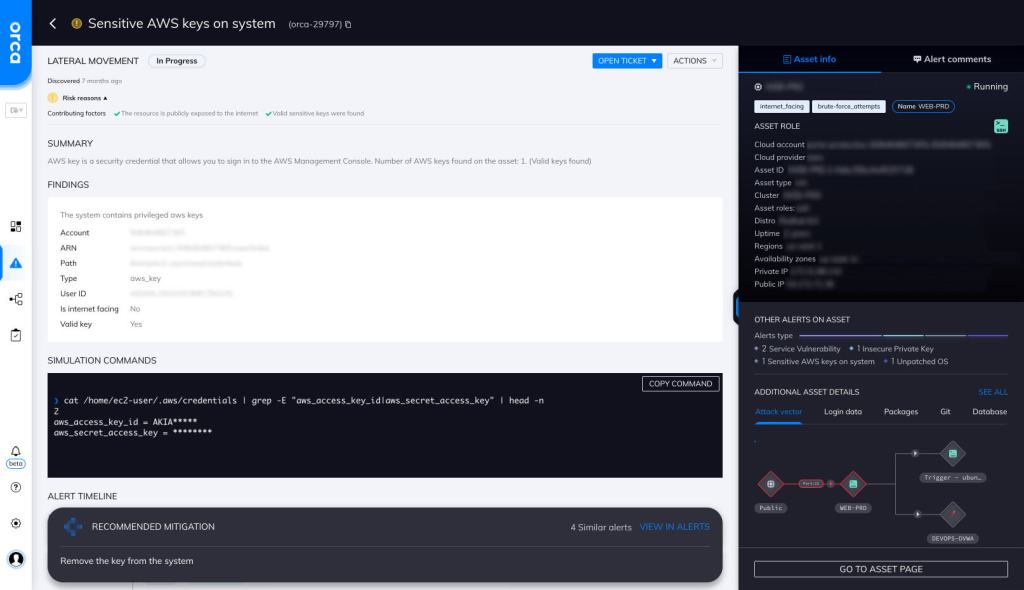
Sensitive AWS Keys on System
Hazardous (3)
- Orca Best Practices
About AWS Access Keys
AWS access keys are used to sign requests to the AWS API or CLI. An access key has two components: an access key ID and a secret access key. Both of these components are used during authentication.
To gain programmatic access to AWS, you must first authenticate using your access keys. Access keys can be created directly from the AWS IAM console.
AWS keys provide indefinite access unless they are manually revoked. However, for many use cases, you don’t need long-term access without an expiration date. This is why AWS recommends using temporary credentials (generated using the Security Token Service) instead of AWS keys. In addition to the access key ID and secret access key, temporary credentials also have a security token that specifies the expiration date of the credentials.
Think of AWS keys as literal keys to your system. Anyone with your key has access to all the resources that you do and can perform any operations that you are authorized to perform like launch EC2 instances, delete S3 objects, etc. This is why you must always store your keys in a safe location, and never share them with anyone, especially not external parties.
Cloud Risk Description
By default, sensitive AWS keys are stored on the file system. If these keys are obtained by a malicious actor, they can use them to access sensitive resources and perform unauthorized operations.
How Does Orca Help?
Orca checks for AWS keys in the default location where it is configured, which is ~/.aws/credentials.
Recommended Mitigation Strategies
-
Rotate access keys
Periodically rotate access keys.
-
Don’t embed access keys
Don’t embed access keys directly into code.
-
Remove access keys
Remove any unused or unnecessary access keys.
-
Use MFA
For the most security-critical operations, configure MFA.
-
Use temporary security credentials
Choose IAM roles with temporary security credentials instead of long-term access keys.
-
Use AWS Secret Manager
Use the AWS Secret Manager for safe storage and retrieval of sensitive information.
Useful Links
- Temporary security credentials: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp.html
- AWS access keys best practices: https://docs.aws.amazon.com/general/latest/gr/aws-access-keys-best-practices.html
- Managing access keys for IAM users: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html
- Create access key: https://aws.amazon.com/premiumsupport/knowledge-center/create-access-key/
- Rotating access keys: https://aws.amazon.com/blogs/security/how-to-rotate-access-keys-for-iam-users/
- AWS Secret Manager: https://docs.aws.amazon.com/secretsmanager/latest/userguide/intro.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
