SSH Authentication with Username and Password
Hazardous (3)
Non-platform specific
SOC 2
About SSH Authentication
Secure socket shell (SSH) is a protocol that allows users to log in to a remote computer. Its acronym also refers to tools and utilities that implement the protocol. A default SSH utility comes preinstalled on all Linux and Macintosh operating systems. An open source version (OpenSSH) is also built into Windows 10 and Windows 11, though it’s not enabled in default configurations.
SSH creates a secure, encrypted channel between a user’s machine and a remote server. The user must have an SSH client installed to initiate the connection. In turn, the remote server must be running an SSH daemon that’s always listening for new connections.
SSH enables engineers and network administrators to:
- Execute commands on a remote server
- Perform automated file transfers
- Apply software patches and updates
- Create automation scripts to securely access servers and perform required operations
Different ways exist to authenticate users (clients) during an SSH connection. The most common are passwords and public key authentication. In the latter method, a cryptographic public and private key pair is generated.
The private key is installed on the client machine, while the matching public key resides on the remote server. Messages encrypted with the client’s public key can only be decrypted with their private key, thereby making the connection secure.
In contrast, password-based authentication is not considered secure, because it only requires a username/password combination. Some cloud providers, such as AWS and Google Cloud Platform, disable such SSH authentication by default, though users can choose to enable it.
Cloud Risk Description
SSH configuration (/etc/ssh/sshd_config) on a server is set to allow username/password authentication. This is susceptible to brute force attacks and could result in compromise assets.
Moreover, people are naturally inclined to use personal information in their passwords, e.g., nicknames, names of their partners/children/pets, and birthdays. Much of this information can often be extracted via social engineering, making passwords even more susceptible to compromise.
How Can Orca Help?
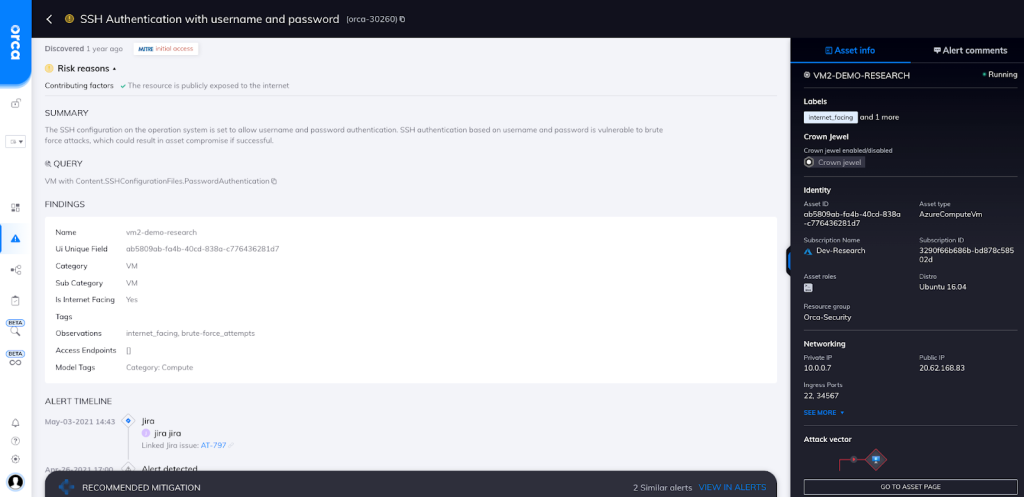
Orca detects, prioritizes, and continuously monitors for IAM risks and misconfigurations across your public cloud estate to meet stringent compliance mandates and improve your cloud security posture. As shown in the screenshot, Orca alerts you if you have an SSH server configuration that allows username/password authentication.
Recommended Mitigation Strategies
-
Ensure that SSH username/password authentication is disabled on all servers.
-
Use public-key SSH authentication on all servers.
-
Ensure that no SSH key pairs are shared between users.
-
Implement a key rotation policy.
-
Don’t hardcode SSH keys in your source code.
Useful Links
- How to disable ssh password login on Linux to increase security: https://www.cyberciti.biz/faq/how-to-disable-ssh-password-login-on-linux/
- SSH Essentials: Working with SSH Servers, Clients, and Keys: https://www.digitalocean.com/community/tutorials/ssh-essentials-working-with-ssh-servers-clients-and-keys
- Set up SSH public key authentication to connect to a remote system: https://kb.iu.edu/d/aews
- Automated SSH connections – Secure M2M connections: https://www.ssh.com/academy/ssh/automated
- sshd_config – How to configure the OpenSSH server: https://www.ssh.com/academy/ssh/sshd_config
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
