Table of contents
- What is Shift Left Security?
- What is the software development lifecycle (SDLC)?
- Developing on-premise vs in the cloud
- Traditional security approaches and their limitations
- Benefits of Shift Left Security
- Implementing Shift Left Security
- Best practices for implementing Shift Left Security
- Tools and technologies for Shift Left Security
- Conclusion
- FAQs
Gartner forecasts cloud computing to become a business necessity by 2028, with the industry projected to exceed $1 trillion (USD) in global spending. Today, organizations increasingly depend on cloud-native development to consume and provide new solutions. As this trend continues, so will the need for enhanced approaches to application security (AppSec).
Traditional approaches involve security in the late stages of the software development lifecycle (SDLC), when addressing vulnerabilities, misconfigurations, and other issues are most time- and resource-intensive. This reactive approach not only increases costs, delays, and the potential for missing risks, it also creates tension between security, DevOps, and development teams.
Enter Shift Left Security, a revolutionary approach that infuses security into the earliest stages of the SDLC. Shift Left Security aims to minimize the time, cost, and effort needed to address security risks and prevent them from reaching production environments.
In this comprehensive guide, we dive deep into Shift Left Security, revealing what it entails, why it matters, how to implement it, and more.
What is Shift Left Security?
Shift Left Security refers to a branch of cloud security focused on software development. “Shift left” gets its name from the software development lifecycle (SDLC), a process that maps the activities needed to bring a new application to life. Development activities reside on the left hand side of the SDLC timeline, while security considerations and activities traditionally live on the right. “Shift left” refers to shifting security left in the SDLC, so it occurs during the initial phases of development rather than after it. With this approach, developers become responsible for promoting application security.
The Shift Left Security mindset emerged in recent years with the rise of DevOps and its focus on accelerating software delivery through automation. As release cycles accelerated, organizations discovered the need to integrate security with development. Inspired by manufacturing and lean principles, shift left incorporates security requirements, policies, and testing into every phase of the SDLC—from initial planning and design through coding, building, testing, and deployment.
So how does Shift Left Security work? It involves these practices:
- Defining security requirements upfront during planning.
- Using secure coding practices and static testing during development.
- Integrating automated security testing into CI/CD pipelines.
- Monitoring and responding to security events in production.
By embedding security in this way, Shift Left Security ensures that you can identify and resolve issues early before they get baked into releases. This improves your overall security posture in a consistent, scalable manner.
The shift left philosophy encourages shared responsibility between developers and security teams. Rather than operating in silos, they collaborate using common processes and tooling to build security into every phase.
What is the software development lifecycle (SDLC)?
The software development lifecycle (SDLC) refers to the different phases and activities of building software applications. The SDLC is an iterative process that guides projects from conception to delivery and maintenance. The SDLC consists of several key phases:
- Planning and requirements gathering: This initial phase defines the project’s goals, scope, and requirements based on business needs.
- Design: Architects and designers create the technical specifications, defining the application’s architecture, data models, interfaces, etc.
- Implementation: Developers write the actual code based on the requirements and design documents.
- Testing: QA teams test the application thoroughly, identifying and fixing any bugs or issues.
- Deployment: Once tested, the application is deployed or released into a production environment.
- Operations and maintenance: The final phase involves monitoring, maintenance, and ongoing support of the live application.
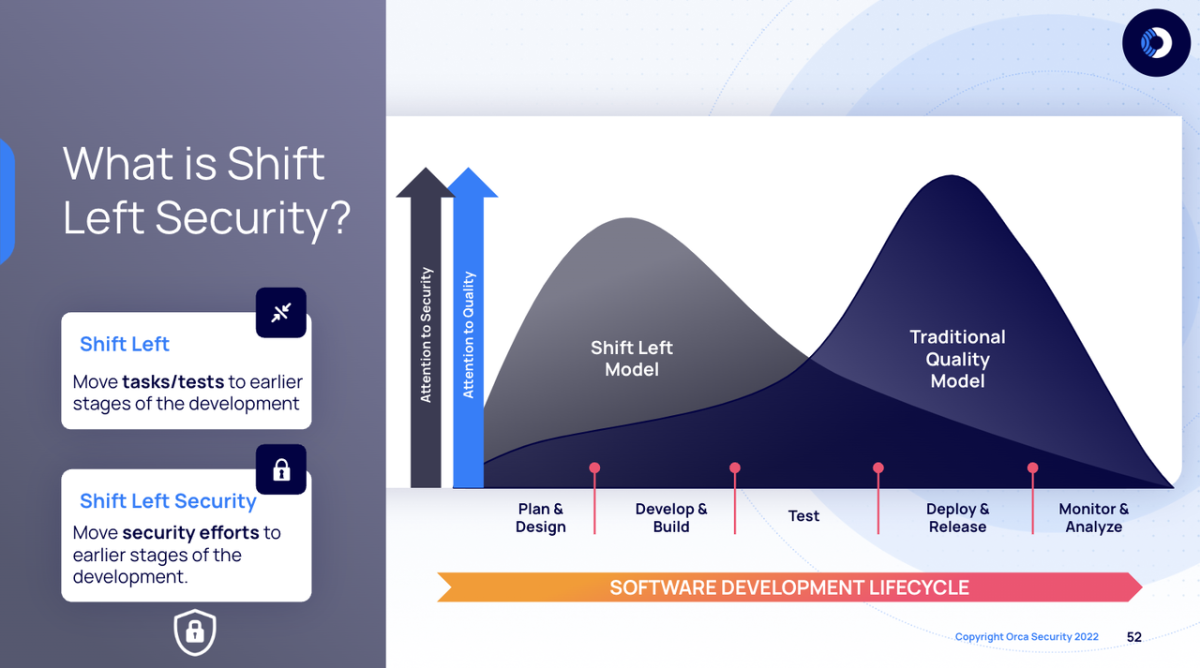
Traditional SDLC processes have evolved over time. Today, DevOps and DevSecOps have become an integral aspect of software development. Modern DevSecOps practices automate security scanning and testing within CI/CD pipelines. As developers commit code, security checks run automatically to flag vulnerabilities before they make it to production. Security tasks that once took days now take seconds with intelligent automation tools.
Shift Left Security is a core part of DevSecOps. As an example, Shift Left Security solutions enable security teams to set security policies for detecting unique risks during IaC, container image, and source code scanning. To illustrate, the Orca Cloud Security Platform offers more than 1,100 security controls for IaC scans, and allows security teams to quickly filter and apply controls by compliance framework, risk severity, and other qualifiers. Teams can also customize policies to automatically block risky builds, stop builds depending on risk severity, or allow builds to proceed while warning developers of detected risks.
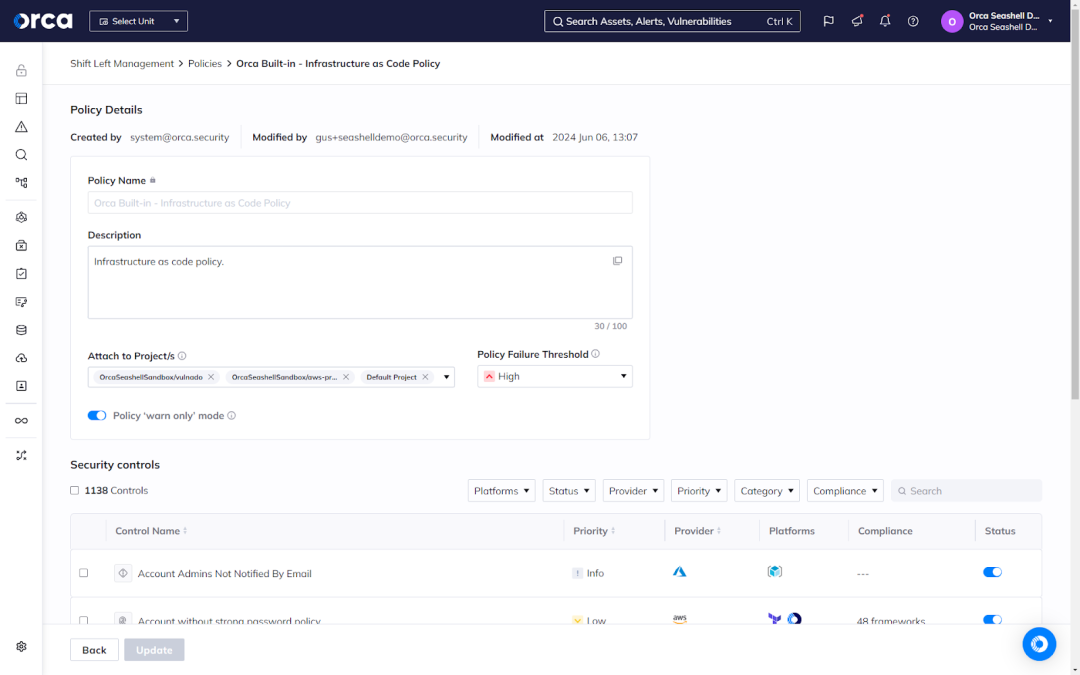
While shifting left does require upfront investment, the long-term payoffs are considerable and include increased efficiency, alignment and collaboration across teams, and more.
What is the CI/CD lifecycle?
DevOps practices aim to unify software development and operations teams. This collaborative approach automates the SDLC through Continuous Integration (CI) and Continuous Delivery/Deployment (CD).
The CI/CD lifecycle revolves around automating builds, tests, and releases. Developers integrate code frequently into a shared repository, automatically triggering builds and tests. Once validated, CD automates the release process—rapidly and safely deploying updates.
DevSecOps takes this further by integrating security practices and automation throughout the CI/CD lifecycle. This Shift Left approach helps catch issues earlier through continuous security testing and monitoring.
Developing on-premise vs in the cloud
What is cloud-native development?
Cloud-native application development refers to building and running applications using services and tools designed specifically for the cloud computing delivery model. Rather than hosting monolithic applications on single servers, cloud-native apps are decomposed into microservices that run in containers and are deployed across multiple cloud resources.
Containers, images, and IaC
Containers package applications with all their dependencies into lightweight, portable compute environments. Container images are read-only templates used to create containers. Infrastructure as Code (IaC) allows you to provision and manage cloud resources through machine-readable definition files rather than manual processes.
IaC templates define the desired state of your infrastructure—everything from virtual machines to networks to data storage. When combined with container images, IaC enables immutable infrastructure where images are deployed consistently across any environment.
Enabling rapid releases
The separation of application dependencies from the underlying infrastructure is a key cloud-native principle. Using containers and IaC, applications are no longer tightly coupled to specific servers. Images can be deployed rapidly across any conformant infrastructure defined by IaC.
This decoupling, combined with automated CI/CD pipelines, allows for far more frequent releases compared to traditional deployment processes. Infrastructure drift is minimized by spinning up identically configured resources from templates with each release.
On-premise vs cloud trade-offs
While cloud environments provide flexibility, scalability, and access to cutting-edge services, on-premise deployments may be preferable for strict data sovereignty requirements, low-latency needs, or managing legacy systems. Cloud costs can also become prohibitive at scale.
Many organizations leverage a hybrid approach—hosting sensitive workloads on-premise while taking advantage of the cloud’s benefits for certain use cases. Cloud-native principles like containers and IaC help facilitate consistency across hybrid environments.
Traditional security approaches and their limitations
In the traditional approach, security is often treated as a final box to check before shipping code. Security testing and vulnerability scans happen once applications are ready for deployment. This “bolt-on” security model presents major drawbacks.
This includes the cost and inefficiencies of finding and fixing vulnerabilities after development. Fixing issues in code after development causes delays, disruptions, and internal friction.
Additionally, traditional methods limit visibility into risks throughout the SDLC. Without integrating security practices from the start, vulnerabilities can easily sneak into production environments undetected.
This approach also creates friction between development and security teams. Developers want to rapidly ship new features, while security professionals apply the brakes to ensure nothing with potential risks goes out the door.
Older security models simply don’t mesh with modern DevOps practices and the fast pace of iterative development. With containers, IaC, and automated CI/CD pipelines, code gets deployed to production environments at lightning speed.
Trying to bolt security on at the end creates a major bottleneck and slows everything to a crawl. By then, it’s often too late—the vulnerabilities have already been deployed and exposed.
Benefits of Shift Left Security
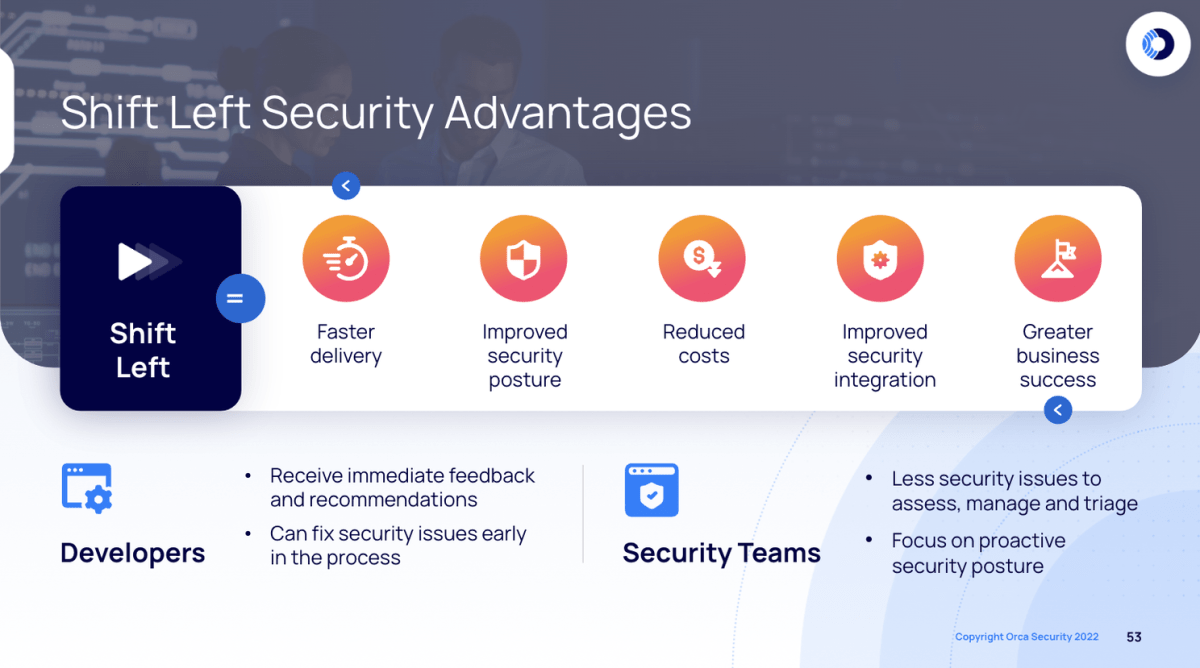
Boosted efficiency and cost savings
One of the biggest advantages of Shift Left Security? Improved efficiency and reduced costs. Traditional security practices leave vulnerabilities, misconfigurations, and other issues undetected until late stages. This leads to costly reworks and delays.
With Shift Left, security is integrated into every phase of the SDLC. Automated testing catches issues early when they’re easier (and cheaper) to fix. This streamlines processes and accelerates delivery timelines.
Hardened security posture
Identifying and addressing risks from the start enhances your overall security posture. Rather than scrambling to patch vulnerabilities post-deployment, security best practices occur during development and are integrated into your applications from the start.
Shift Left Security not only improves code security, it also ensures the proper configuration of source code management (SCM) platforms and their repositories. Traditionally, security teams lack visibility into, awareness of, and control over SCM solutions. This inevitably leads to misconfigurations and unmaintained repositories that can create security risks for applications in development.
Advanced and comprehensive Shift Left Security solutions include SCM Posture Management (SCM-PM) capabilities, which allows security teams to automatically identify and properly configure, control, and monitor SCM accounts and repositories. For example, the Orca Platform provides both code security and SCM-PM as part of its Shift Left Security, ensuring pre-production security at the SCM account, repository, and code levels.
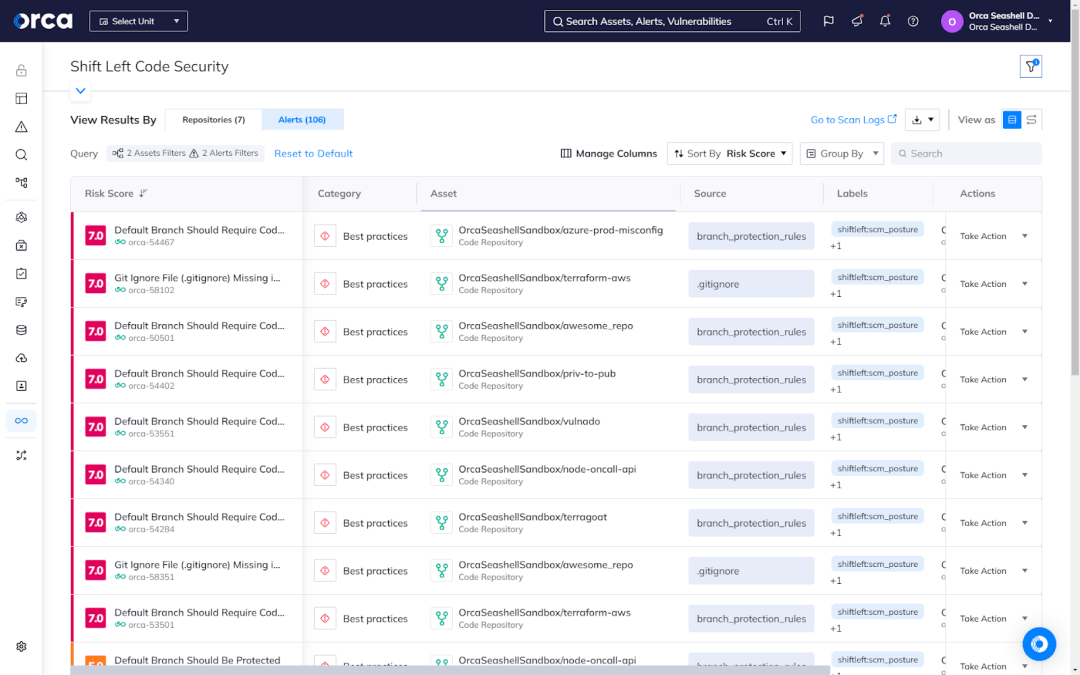
Continuously monitoring for threats throughout the lifecycle prevents oversights. Your applications aren’t just secure at launch—they stay secure with every update and release.
Bridging the DevOps-security gap
In traditional models, DevOps and security teams often experience friction due to conflicting priorities. Shift Left breaks down these silos.
Security is no longer an afterthought or roadblock. It’s a shared responsibility embedded into DevOps workflows. Enhanced transparency and collaboration reduce friction between teams. Everyone works together towards the same goal—delivering secure, high-quality software, fast.
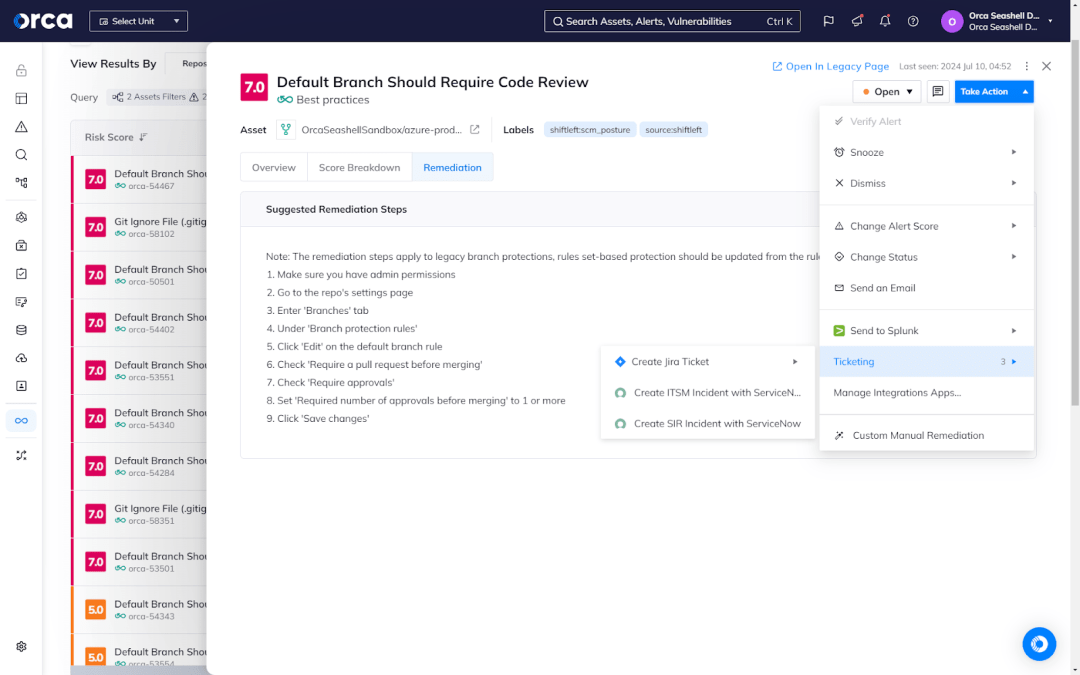
Shift Left Security solutions commonly provide features that promote the partnership between security and development teams. For example, the Orca Platform offers two-way integrations with Jira and ServiceNow to enhance collaboration. Security teams can create a ticket directly from an Orca Alert, assign it to the appropriate developer, and track its status—all without ever leaving the Orca Platform.
Meanwhile, developers never need to login to the Orca Platform to work on the issue, eliminating the need to learn another tool or deviate from an established workflow. Once they close the ticket, the Orca Platform automatically verifies the issue is resolved. In the event it still exists, Orca will reopen the ticket and alert the appropriate developer.
By integrating security from ideation to deployment, Shift Left represents a game-changing paradigm shift. It enables you to take advantage of accelerated delivery cycles, enhanced security, and improved cross-functional collaboration.
Implementing Shift Left Security
But how do you implement Shift Left Security? Where do you start? Focus on the following activities.
Integrate security into CI/CD pipelines
One key aspect is incorporating security scanning and testing directly into your CI/CD pipelines, including:
- Running static application security testing (SAST) to analyze code during build/commit stages.
- Performing dynamic application security testing (DAST) against deployed applications.
- Using interactive application security testing (IAST) to combine static and runtime analysis.
These automated security steps serve as a quality control for source code.
Make developers security-conscious
Shifting left also requires making developers more security-aware and responsible for secure coding practices. As an organization, provide developers with the following:
- Security training and certifications.
- Real-time feedback on coding mistakes and issues.
- Easy access to secure coding guidelines.
When developers own security, it naturally gets prioritized earlier in the SDLC.
Leverage automated security tools
Take advantage of DevSecOps tools that integrate security seamlessly into your existing workflows, including:
- Cloud-native application protection platforms (CNAPP).
- Code security tools like Software Composition Analysis (SCA), Secrets Detection, and IaC Security.
- Source Code Management Posture Management (SCM-PM) solutions.
The more you can automate security activities, the more frictionless shifting left becomes.
Implementing a comprehensive shift left strategy takes time, but pays major dividends. You catch issues earlier, release more securely, and better align security with development. It’s a modern, proactive approach to AppSec.
Best practices for implementing Shift Left Security
Use security champions
Identify security champions—developers passionate about secure coding practices who can evangelize Shift Left Security on their teams. Provide them with specialized training, then let them lead by example.
As the champions model best practices like writing secure code and fixing flaws in real-time, their peers will take notice. Developers tend to be more receptive to advice from those they consider a functional colleague.
Continuously improve
Shift Left Security isn’t a one-and-done effort—it requires continuous improvement. Regularly review your processes, tools, and training programs to identify areas for optimization.
For example, you may find certain security tools are a poor fit and need replacing. Or developers may need more training on secure coding practices.
Gather feedback from your developers and security teams. Use that input, along with metrics around flaw density, remediation time, etc., to fine-tune your program continually.
Embrace automation
Manual security activities are prone to human error and inconsistency. Wherever possible, automate security checks and workflows directly into your CI/CD pipelines and developer toolchains.
Automated SAST, DAST, and IAST tools can scan code commits, containers, and running applications for security flaws. Findings get reported back to developers in their familiar IDEs for rapid remediation. Security orchestration tools can automatically update policies, provision security controls, and more based on predefined rules.
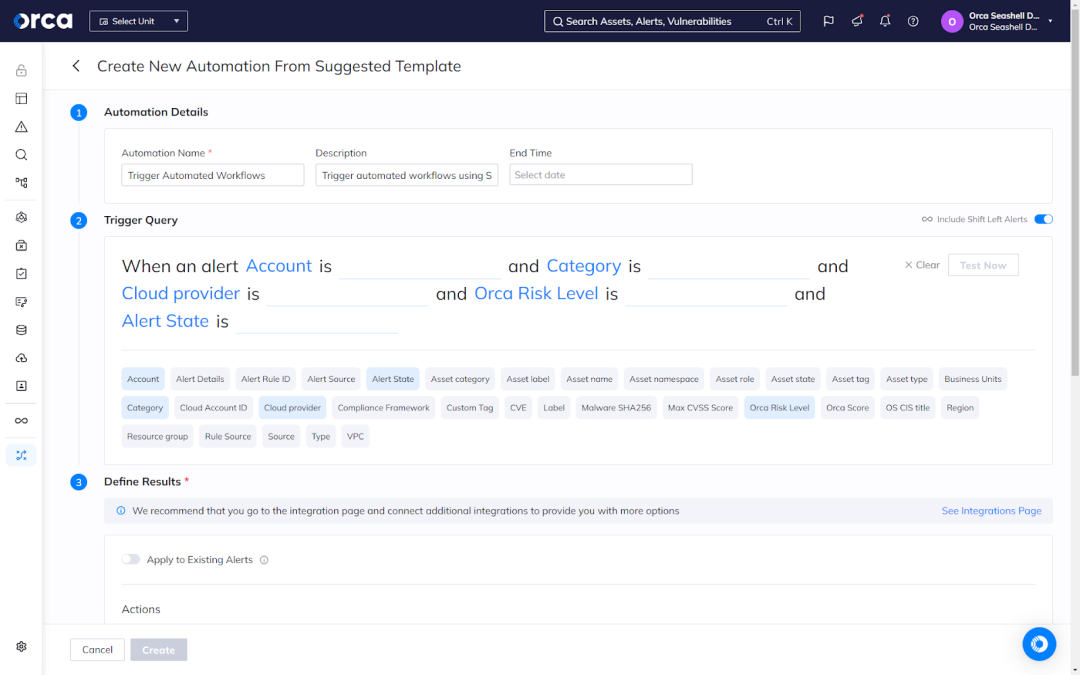
Additionally, some Shift Left Security solutions offer automated workflows to augment the time, skill, and capacity of your teams. For example, the Orca Platform offers the ability to create workflows that automatically generate tickets when detecting specific risks, send notifications, and complete other tasks. These automations work across Orca’s 50+ technical integrations, including those with popular SCM platforms like GitHub and GitLab, and CI/CD tools like CircleCI, Jenkins, GitHub Actions, Azure DevOps.
Tools and technologies for Shift Left Security
Adopting a Shift Left Security approach requires integrating security testing and automation throughout the software development lifecycle. Luckily, there are powerful tools and technologies available to make this process easier and more efficient.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) tools analyze source code to detect potential vulnerabilities before the application is even built or deployed. These tools dig deep into the codebase, scanning for insecure coding practices, hard-coded secrets, and other security flaws.
Using SAST early in the development cycle allows you to catch and remediate issues when it’s easiest and cheapest to fix them.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) takes things a step further by analyzing a running application from an attacker’s perspective. These tools simulate real-world attacks and malicious behavior to identify security issues that SAST may have missed or can’t detect, such as vulnerabilities at runtime.
Integrating DAST into your CI/CD pipeline lets you test each build in a safe, controlled environment before deploying to production.
Interactive Application Security Testing (IAST)
Interactive Application Security Testing (IAST) combines the strengths of SAST and DAST by instrumenting the application’s runtime environment. This allows it to monitor data flows, API calls, and all dependencies that applications use while also assessing external behavior.
IAST provides deep visibility into an application’s inner workings, helping to detect complex vulnerabilities that other testing methods might overlook.
Cloud-Native Application Protection Platforms
Cloud-Native Application Protection Platforms (CNAPPs) are a comprehensive cloud security solution that integrates the capabilities of several established technologies. This includes Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), Cloud Identity and Entitlement Management (CIEM), Vulnerability Management, API Security, and more.
Advanced CNAPPs offer Shift Left Security that includes both SCM-PM and code security capabilities, including SCA, Secrets Detection, and IaC Security.
About the Orca Cloud Security Platform
A true agentless-first CNAPP, the Orca Cloud Security Platform solves security risks and compliance issues across multi-cloud environments offered by AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
The Orca Platform natively integrates Shift Left Security, CSPM, CWPP, CIEM, DSPM, API Security, AI Security Posture Management (AI-SPM), Multi-Cloud Compliance, Vulnerability Management, and more. Leveraging its patented SideScanning™ technology, Orca offers complete coverage across your entire cloud estate and comprehensive risk detection.
Orca captures and integrates data insights into its Unified Data Model, which it uses to contextualize risks and uncover hidden, interrelated issues that present dangerous attack paths. As a result, Orca can effectively prioritize risks, reduce alert fatigue, and ensure your teams can focus on the most critical and important tasks.
To see how the Orca Platform can enhance your cloud security, schedule a demo with one of our experts. You can begin leveraging the Orca Platform as soon as you complete a quick onboarding session (~30 minutes).
Conclusion
The bottom line? Shifting security left delivers immense value by empowering developers to participate as security practitioners from the start of their workflows.This prevents vulnerabilities from reaching production environments when they become far more time- and resource-intensive to fix. Beyond bolstering your security posture, Shift Left Security also streamlines development, reduces friction between teams, and makes the most of your engineering resources.
You can start leveraging the benefits of Shift Left today. Leverage automated testing tools and platforms to catch bugs early. Foster collaboration between development and security teams. And embrace Shift Left as an ongoing journey, rather than a one-time event or fix.
FAQs
What’s the difference between Application Security and Shift Left Security?
Application Security (AppSec) refers to the collection of strategies, solutions, and practices designed to protect applications throughout their entire lifecycle. Shift Left Security refers to a set of technologies, strategies, and practices focused on preventing applications from introducing security risks into a live environment. Modern AppSec solutions and approaches include Shift Left Security while also providing security post-deployment.
Why should you shift security left?
There are several key benefits to adopting a shift-left approach:
- Improved efficiency: Finding and fixing vulnerabilities early prevents costly rework later on. This accelerates your delivery pipeline.
- Better security posture: Continuously validating security reduces the risk of vulnerabilities making it into production environments.
- Tighter collaboration: Developers and security teams work together from the start, fostering shared responsibility for application security.
What’s the difference between container images and IaC templates?
Container images package all application code, dependencies, and configurations into immutable artifacts that can be consistently deployed anywhere. Infrastructure as Code (IaC) templates define and provision all cloud resources needed to run applications—like virtual machines, networks, databases, etc. Together, container images and IaC code enable fully automated deployments across hybrid environments. This supports frequent, reliable releases while maintaining a consistent, secure application stack.
Table of contents
- What is Shift Left Security?
- What is the software development lifecycle (SDLC)?
- Developing on-premise vs in the cloud
- Traditional security approaches and their limitations
- Benefits of Shift Left Security
- Implementing Shift Left Security
- Best practices for implementing Shift Left Security
- Tools and technologies for Shift Left Security
- Conclusion
- FAQs




