Open-source software is used in the vast majority of today’s applications. Ready-made, reusable, and widely accessible, it gives developers a significant head start in bringing their projects to life. Despite its considerable advantages, open-source software presents significant security risks, which make Software Composition Analysis (SCA) an essential measure.
SCA detects open-source components, packages, libraries, and other dependencies in your codebase and analyzes for the presence of vulnerabilities, misconfigurations, and license requirements. When integrated into your CI/CD pipeline, SCA catches issues early in the software development lifecycle (SDLC), saving considerable time and expense, while preventing unnecessary exposures.
In this post, we detail what SCA is, why you need it, and how the Orca Cloud Security Platform delivers comprehensive SCA as part of its Shift Left Security.
What is SCA?
Software Composition Analysis (SCA) is a security discipline focused on analyzing software projects for open-source and third-party components. These components often contain security risks and come with licensing requirements, which SCA aims to detect so organizations can remediate. SCA is a necessary aspect of code security and a widely embraced practice in the software development lifecycle (SDLC), especially in the pre-deployment phase.
Why do you need SCA?
Open-source and third-party software components offer organizations a head start on their development projects. Rather than remaking software components from scratch, developers can reliably reuse components to accelerate their progress. Despite these benefits, software developed by third parties commonly contains security risks and licensing requirements. Both can expose organizations to significant consequences if they get incorporated into live applications. For example, organizations can experience critical security incidents, data breaches, and other adverse events, including those financial, operational, legal, regulatory, and reputational in nature.
SCA enables organizations to identify and understand the open-source and third-party components used in their software projects. This allows them to make an informed decision about what software they can reuse safely, securely, and appropriately. As a result, organizations can address risks before they make it into a live application, saving them considerable time, effort, and expense.
How Orca delivers SCA
As part of its Shift Left Security capabilities, Orca provides complete Software Composition Analysis, so that any vulnerabilities and risks in open-source software included in applications can be detected before applications are deployed into production.
Orca automatically scans container images, file systems, and Git repositories on every push or pull request for any open-source risks, and provides you with a full SBOM of your code repositories, including transitive dependencies.
Let’s dive into each of these features:
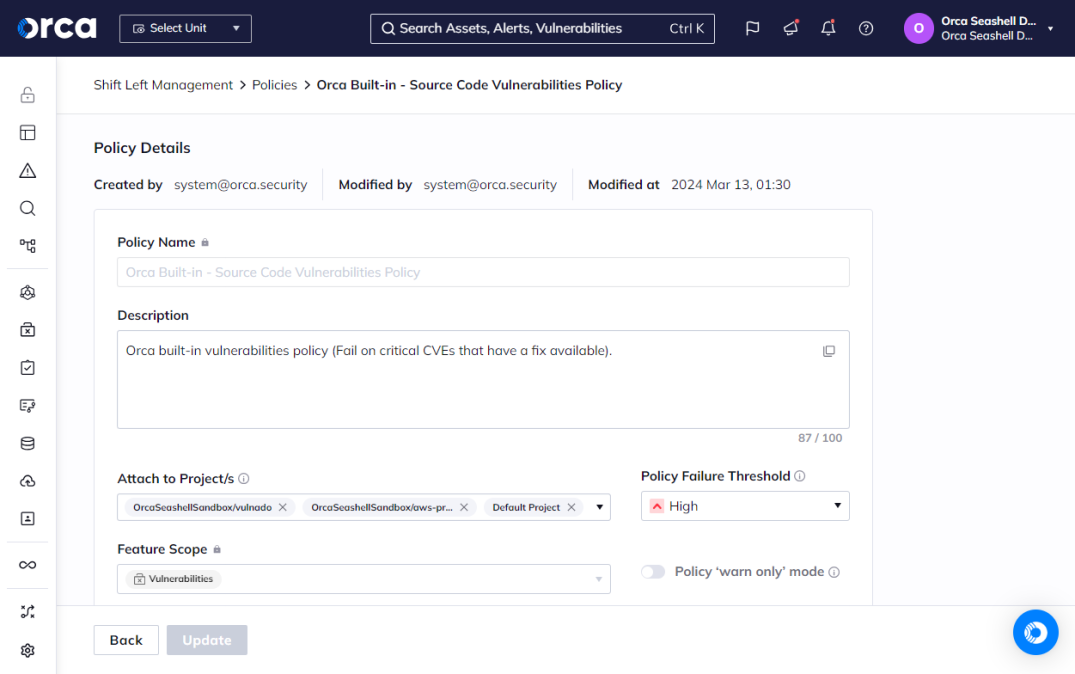
#1: Flexible policy creation
Orca allows security teams to easily define and manage policies for detecting and handling issues uncovered by SCA. This provides security teams maximum flexibility in tailoring SCA to address their unique security needs for open-source risks.
Via Orca’s intuitive dashboard, you can create and cater policies for source code, Infrastructure as Code (IaC), and container images, including defining the risk threshold for failing an SCA scan and the resulting enforcement action. Orca’s built-In policies allow you to block a build for failed scans or warn developers of policy violations while allowing them to proceed. This offers you full flexibility in setting guardrails that support your preferred balance of security and developer productivity.
You can apply policies to all repositories in your environment or assign them as appropriate. You can also ensure your policies apply automatically to any new repositories, ensuring ongoing and extended coverage.
#2: Comprehensive Software Composition Analysis
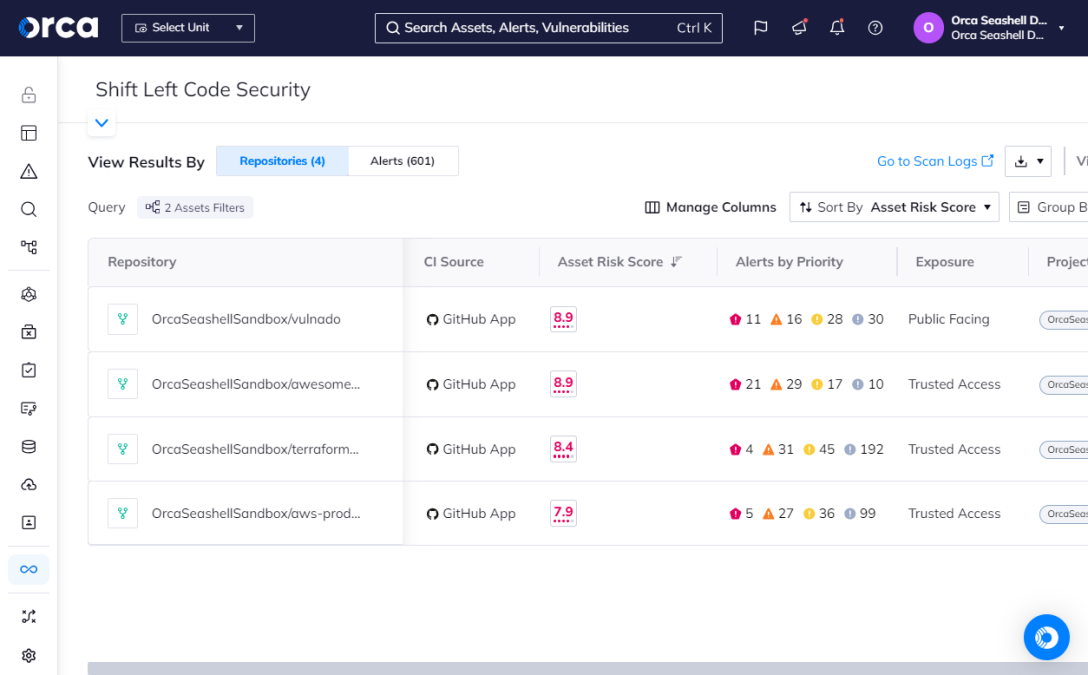
With Orca, security teams can leverage comprehensive SCA to detect open-source risks and effectively secure their codebase.
With your policies defined, you can integrate the Orca Platform with your code repositories to begin running SCA. Orca offers the GitHub App and GitLab App to easily integrate SCA into GitHub or GitLab repositories, respectively. Orca also offers the Orca CLI, a lightweight command-line interface, to integrate SCA into other repositories. Orca then enumerates all projects and integrates scanning.
Admins can easily onboard repositories individually or universally, and also easily discover and onboard new repositories with the separation of duties maintained.
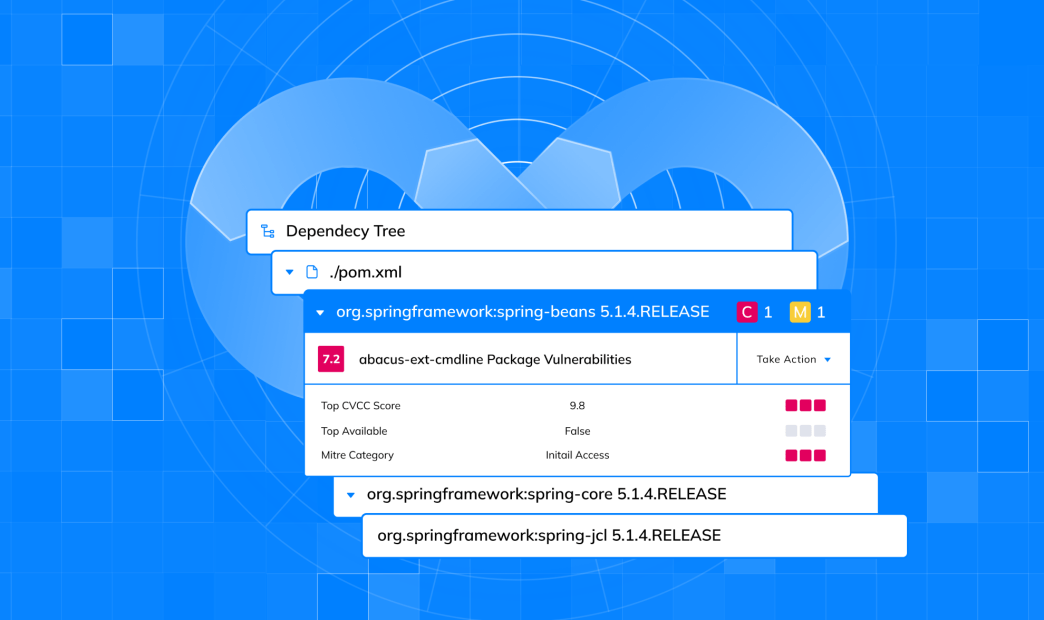
On every push or pull request, the Orca Platform scans your container images, filesystems, and Git repositories and detects vulnerable packages in Ruby, Python, PHP, Node.js, .NET, Java, and Golang.
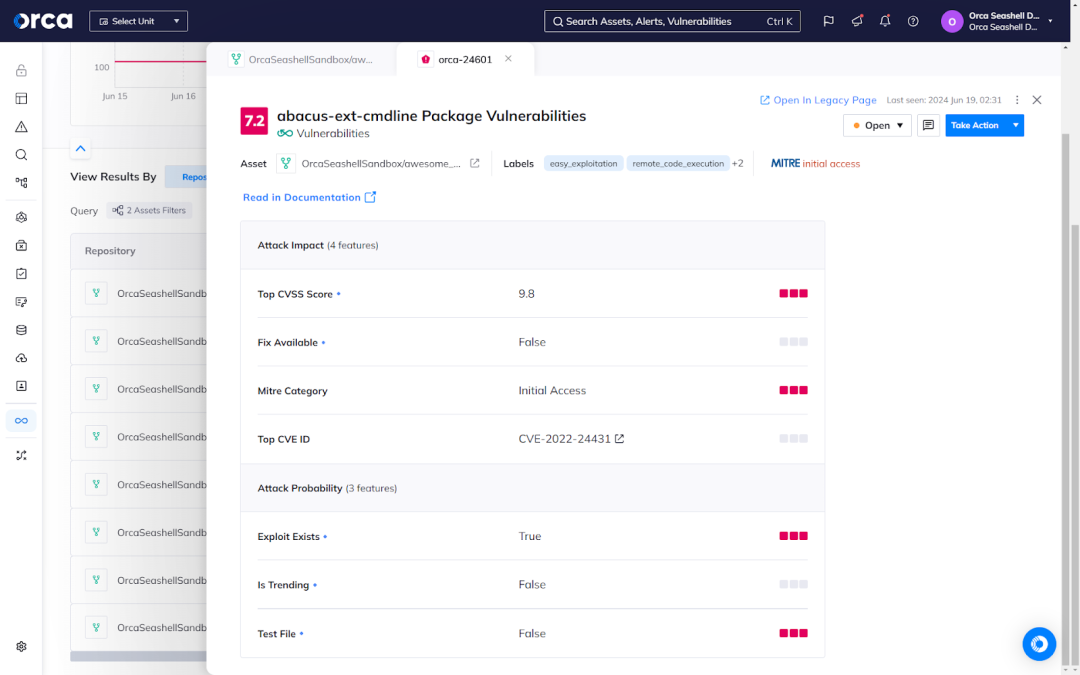
#3: Risk prioritization
Orca prioritizes risks uncovered by SCA to help your security and development teams enhance security and productivity. The Orca Platform combines its full coverage of your repositories with comprehensive risk detection, which catches misconfigurations, vulnerabilities, and more. This enables Orca to accurately assess and prioritize risks in the software development lifecycle (SDLC), and alert your team accordingly.
Orca dynamically scores risks based on a number of factors that contribute to the attack impact and probability. Depending on the risk, it may include the CVSS score, availability of a fix, presence of an exploit, external exposure, and more. As these factors continually change, Orca automatically updates the alert to reflect its current severity. This enables your teams to concentrate on the most important risks.
#4. Seamless integration and automations
Orca integrates SCA results into where your developers are working. Using Orca’s GitHub App, developers can see annotations directly inline for any pull request. This enables them to view and fix issues without deviating from their current workflows or tools.
For security teams, Orca offers a centralized log of all SCA scans, giving them full visibility across all repositories and pipelines as well as granular insight into detected issues. For example, security teams can quickly discover where and when vulnerable dependencies are introduced into source code. This enables them to ensure developers fix issues before deployment.
To accelerate and help automate critical tasks for your teams, Orca also offers two-way integrations with Jira and ServiceNow. This enables security teams to create, monitor, and verify tickets without leaving the Orca Platform, while giving developers the freedom to fix issues on-the-fly without deviating from their current workflows or tools. Orca’s integrations help reduce any potential friction between security, DevOps, and development teams.
Orca also offers the ability to automate ticketing management. Security teams can build automations that automatically open tickets based on defined criteria, and close tickets after issue resolution. When developers manually close a ticket, Orca automatically rescans the related asset to verify the fix and reopens the ticket in the event it remains unresolved.
Software Composition Analysis: An integral part of Shift Left Security
Open-source software is an invaluable resource when it comes to cloud development. Yet its universal accessibility and availability make it an attractive target for attackers.
That illustrates the importance of adopting Software Composition Analysis, and more broadly, Shift Left Security. SCA enables organizations to secure open-source components early in the SDLC, fixing misconfigurations and vulnerabilities at the easiest and least costly phase.
About the Orca Cloud Security Platform
The Orca Cloud Security Platform identifies, prioritizes, and remediates security risks and compliance issues across the cloud estates of AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. Orca offers an agentless-first approach that leverages its patented SideScanning™ technology to provide full coverage and comprehensive risk detection, identifying vulnerabilities, misconfigurations, malware, lateral movement, API risks, sensitive data risks, AI risks, overly permissive identities, and more. Unlike other solutions that loosely integrate multiple point solutions or require agents, Orca delivers comprehensive cloud security in a unified platform.
Learn more
If you want to learn more about Orca’s SCA or Shift Left Security capabilities, schedule a personalized 1:1 demo. We’ll show you how Orca helps organizations catch vulnerabilities and misconfigurations early in the SDLC and prevent them from reaching production.