Table of contents
According to Gartner forecasts, the market for public cloud computing is expected to grow more than 22 percent in 2025, a trend driven by generative AI and application innovation. Already, cloud computing has become the backbone of many enterprises, providing them with unprecedented scalability, flexibility, and efficiency.
However, these benefits come with significant risk. Just consider these findings from Orca Security’s 2024 State of Cloud Security Report:
- 81% of organizations have public-facing neglected assets with open ports and known vulnerabilities.
- 61% of organizations have root users or account owners without Multi-Factor Authentication (MFA).
- 62% of organizations have severe vulnerabilities in code repositories.
To be clear, each of these scenarios can result in major consequences, such as system compromises, data breaches, and more. Together, they highlight the need for a robust Cloud Risk Management program, which can enable organizations to identify and remediate a myriad of cloud risks.
In this comprehensive guide, we explore Cloud Risk Management and what it means, why you need it, and how you can adopt it for optimal results in your organization.
What is Cloud Risk Management?
Cloud Risk Management refers to a set of strategies and practices designed to protect your cloud resources and data. It involves a comprehensive approach to identifying, assessing, remediating, and investigating risks in public cloud environments.
In simple terms, think of Cloud Risk Management as your organization’s shield against potential threats in the cloud computing landscape. By implementing robust measures, you can protect your organization’s reputation, bottom line, and operational continuity.
Cloud Risk Management involves these essential components:
- Continuous monitoring of cloud infrastructure.
- Continuous risk detection and prioritization.
- Risk remediation and mitigation.
- Incident response and investigation.
What’s the difference between Cloud and On-Prem Risk Management?
When it comes to managing risks, cloud and on-prem environments require vastly different approaches. Acknowledging their differences can help your organization better navigate the unique challenges of Cloud Risk Management.
On-Prem Risk Management
In a traditional on-premises environment, you own and control your infrastructure—from the physical servers to the software running on them. This autonomy comes with significant responsibilities, including:
- Physical security: Ensuring you secure and monitor your data center.
- Network security: Implementing firewalls and intrusion detection systems to prevent unwanted intrusions.
- Data backups and disaster recovery: Establishing regular backups and a comprehensive plan for recovering data in case something goes wrong.
- Software patching and updates: Adopting reliable systems and processes for patching software with the latest updates to protect against vulnerabilities.
While affording greater autonomy and control, On-Prem Risk Management requires you to bear the full burden of risk management.
Cloud Risk Management
Alternatively, when using one or more public cloud environments, you manage risk according to a shared responsibility model. Here, you own the responsibility to secure everything but the public cloud infrastructure, including data centers, networking, storage, servers, and virtualization.
While this shared responsibility model depends on the type of cloud service (see graphic below), you remain responsible for protecting your applications at a bare minimum, and oftentimes your databases and operating systems too.
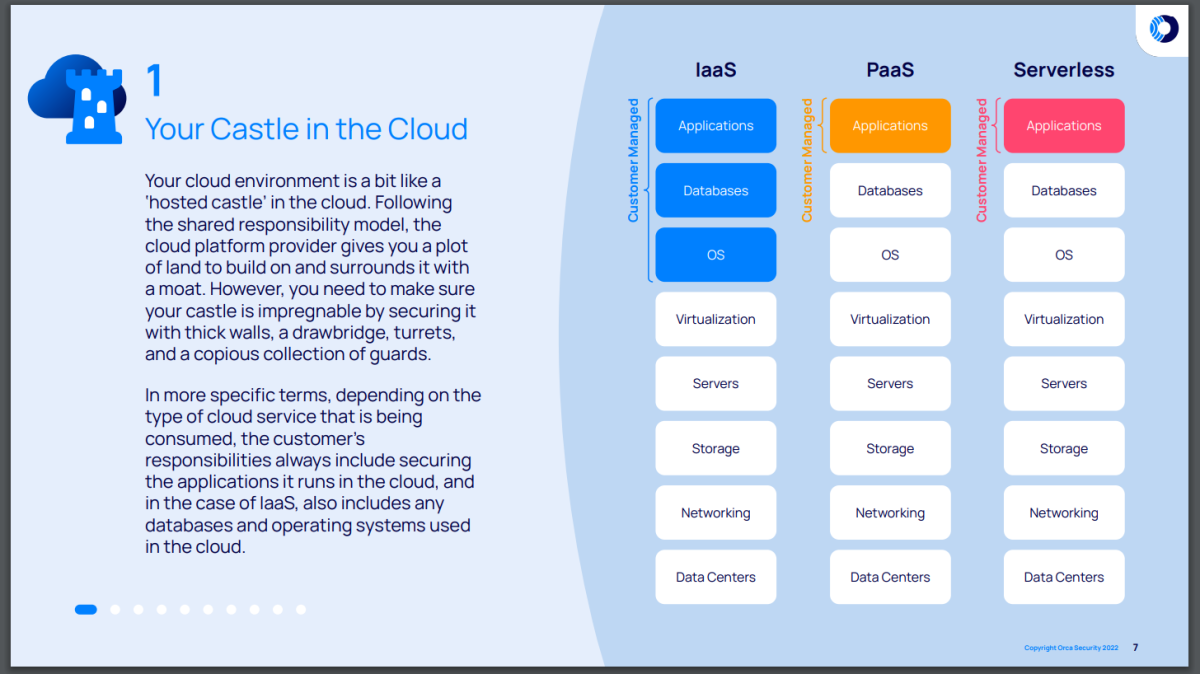
While this may sound less challenging than On-Prem Risk Management, several factors often make it more challenging, including:
- Lack of visibility: Cloud environments change rapidly, with new assets constantly spinning up and turning down. This makes it difficult to capture and maintain a full and accurate inventory of your cloud assets, which represents a basic need of risk management.
- Risk velocity: The dynamic nature of cloud environments often induce risk at a high velocity. The speed and ease with which developers can spin up new cloud assets leads to environments inundated with misconfigurations, vulnerabilities, and other risks. Meanwhile, security teams are vastly outnumbered by cloud development teams (in some cases by 100 to one), meaning there are far more creators of risk (developers) than those policing it (security practitioners).
Cloud Risk Management requires a different mindset and toolset. You need to focus on things like identity management, data encryption, and API security. In this new landscape, you must stay on top of cloud risks that are crucial for your organization’s security and success.
Why do you need Cloud Risk Management?
Why do you need Cloud Risk Management? Simply put, it’s your best defense against evolving cyber threats. It helps you maintain the security and privacy of your data and digital resources, ensures compliance with regulatory and industry requirements, and protects your business continuity and cloud innovation.
Effective Cloud Risk Management isn’t an event—it’s an ongoing process that evolves with your business and the dynamic threat landscape. By investing in this critical area, you can create the conditions for your organization to thrive in the cloud.
Here are the top three reasons why you need Cloud Risk Management:
1. Security
As investments in cloud computing continue to grow, so does the need for enhanced security. Look no further than the latest research reports from Verizon and IBM, which show a steep increase in the number and cost of data breaches, respectively. From vulnerabilities and misconfigurations, to malware and sensitive data exposure, organizations must contend with a variety of cloud risks that surface at any time.
That’s where Cloud Risk Management comes in. By implementing proactive practices, you can identify and remediate security risks before they lead to an incident or major compromise. In other words, it ensures that you can prevent the consequences that likely accompany an unattended risk.
2. Compliance
Regulations like PCI-DSS, ISO 27001, SOC 2, and others aren’t just mandatory for many organizations, they determine their survival. Compliance determines your authority to operate as a business, and managing risks happens to be a core requirement of all regulatory standards and industry benchmarks. Effective Cloud Risk Management ensures that you can meet regulatory standards and industry guidelines, such as data protection laws and industry-specific regulations. It also ensures you can avoid the financial, legal, regulatory, and reputational penalties that come with compliance violations, data breaches, or other severe security incidents.
3. Business continuity
Downtime is the enemy of productivity. Unforeseen incidents like cyberattacks, data breaches, or service interruptions can disrupt business operations and impact revenue streams. Cloud Risk Management plays a crucial role in maintaining business continuity by identifying and mitigating potential risks that could threaten the availability, confidentiality, and integrity of your cloud resources, data, and applications.
Common cloud security risks
As more organizations move to the cloud, they encounter various security risks that can threaten their data and operations. Here are some key concerns to keep in mind:
Lack of visibility
According to Orca’s 2024 Cloud Security Strategies Report, nearly half of executives believe that sharpening visibility into their cloud environments would provide the greatest boost to their cloud security posture. That’s not surprising—especially considering that visibility often eludes organizations without the right technology and processes in place. Unlike on-prem architectures, cloud environments constantly change, with new risks quickly surfacing around the clock. Because of the dynamic and interconnected nature of cloud resources, a lack of visibility prevents organizations from effectively securing their cloud environments.
Misconfigurations
Misconfigurations pose another significant risk. The complexity of cloud services can lead to accidental errors, such as leaving a database exposed or granting excessive permissions. Misconfigurations can create vulnerabilities that allow unauthorized access to sensitive data. Regularly reviewing and auditing cloud configurations is essential to identify and fix these issues before they can be exploited. Automated tools that scan for misconfigurations can help organizations stay on top of this.
Vulnerabilities
Cloud environments often rely on a mix of software components, including open-source libraries and custom code, which can harbor vulnerabilities. Attackers may exploit these weaknesses to gain unauthorized access or disrupt services. Keeping software updated with the latest security patches is crucial, and conducting regular vulnerability assessments can help identify and address potential weaknesses in your cloud infrastructure.
Unauthorized access
With the rise of remote work and decentralized access models, unauthorized access has become a growing concern. Ensuring that only authorized users can access cloud resources is vital to prevent data breaches. Implementing strong access controls, such as multi-factor authentication and role-based access, can significantly reduce this risk. Additionally, monitoring user activity within cloud environments can help detect suspicious behavior that may indicate a security breach.
Sensitive data exposure
Another major concern in cloud environments is the risk of sensitive data being compromised. Cloud services often store substantial quantities of sensitive data, including personal information and financial records. If not properly secured, this information could be exposed to unauthorized parties, resulting in data breaches and regulatory violations. One of the most effective ways to protect against the risk of sensitive data exposure is through encrypting sensitive data during transit and at rest. Organizations should also implement strong data access controls to ensure that sensitive information is only accessible by the right personnel.
Publicly exposed cloud resources
Finally, one of the most overlooked risks is publicly exposed cloud resources. It’s surprisingly common for databases, storage buckets, or even entire virtual machines to be inadvertently left open to the Internet. This oversight can create a significant vulnerability for attackers. Regular audits and monitoring can help identify and secure these risks before they are exploited.
How to manage cloud risks
Managing cloud risks is a crucial aspect of maintaining a secure and compliant cloud environment. Below are the key steps you need to take to effectively manage these cloud risks.
- Inventory assets: Start by creating a comprehensive inventory of all your cloud assets. This includes virtual machines, databases, storage buckets, and any other resources. Gaining a clear picture of your cloud estate—which assets are deployed in the cloud, how they are configured, and who has access to them—is essential for identifying potential vulnerabilities.
- Identify risks: Next, continuously monitor your cloud assets and detect any associated risks. This involves analyzing your cloud infrastructure and workloads for vulnerabilities, misconfigurations, sensitive data exposure, malware, and other risks.
- Prioritize risks: The 2024 State of Cloud Security Report illustrates the importance and need for risk prioritization. Risk prioritization involves dynamically assessing risks using a variety of criteria, such as their severity, exploitability, potential impact, sensitive data exposure, etc. This assessment determines each risk’s criticality, and assigns a rating to it that allows security teams to focus on the risks that pose the greatest danger to the business.
- Remediate risks: Once risks are detected and prioritized, security teams remediate them, starting with the most critical. This may involve a variety of actions depending on the type of risk, such as patching a vulnerability, revoking unnecessary permissions, or implementing other security measures.
Best practices for Cloud Risk Management
While Cloud Risk Management presents significant challenges, below are several best practices to optimize it for your organization.
Leverage a unified cloud security solution
Each of the steps explored in the previous section require a cloud security solution. Rather than rely on point solutions or poorly integrated platforms, opt for a comprehensive platform that gives you complete visibility into your entire cloud estate. This approach streamlines monitoring and response, making it easier to neutralize potential threats. Look for solutions that also provide comprehensive risk detection, effective risk prioritization, as well as key integrations that infuse security across your teams. By using a solution like the Orca Cloud Security Platform, organizations can gain a clear understanding of their cloud environments and quickly identify any risks or vulnerabilities that need to be addressed.
Customize your dashboards and views
Previously, we covered the importance of cloud visibility, which creates the conditions for you to secure your estate and resources. Customizing dashboards and views in your cloud security solution can help you improve and optimize your visibility. Most cloud security solutions offer this capability, while others also offer additional filters for sharpening visibility and increasing its relevance for a specific team or use case.
For example, the Orca Cloud Security Platform enables users to build custom dashboards for specific teams, users, or use cases. These dashboards are entirely flexible and customizable, so that your Security Operations Center (SOC) can surface the most important insights concerning malicious and anomalous activity, while your cloud security team can use a different dashboard to track hygiene risks, such as identity and access management (IAM) misconfigurations.
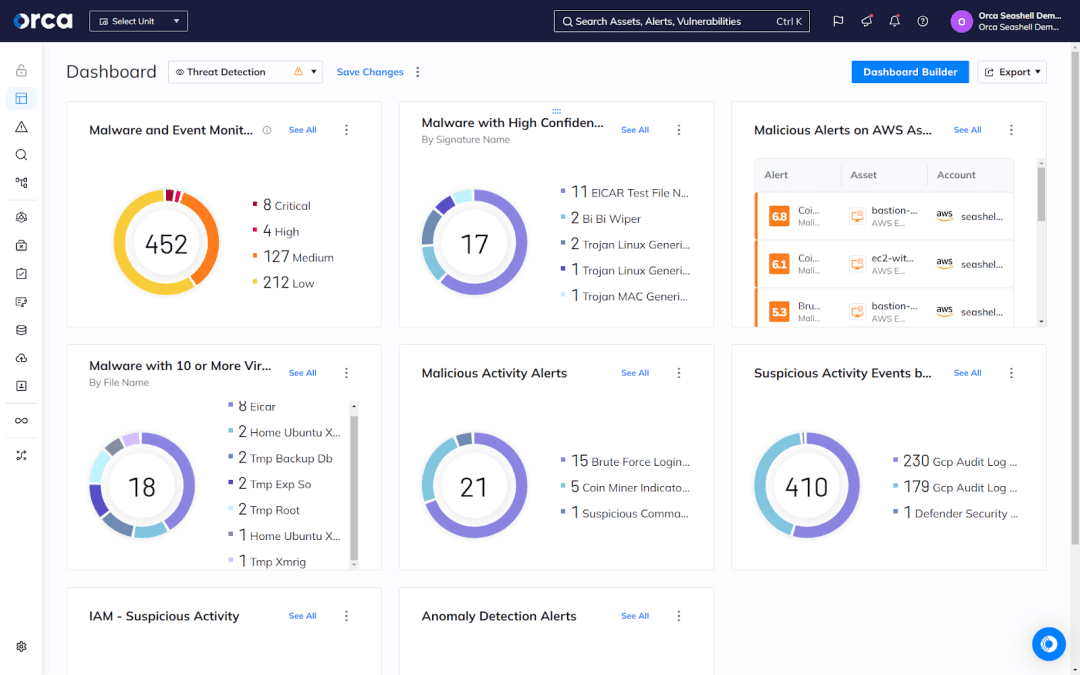
Additionally, the Orca Platform enables you to filter its scope by business unit, cloud environment, cloud account, and other criteria. This enables users to focus their work as needed.
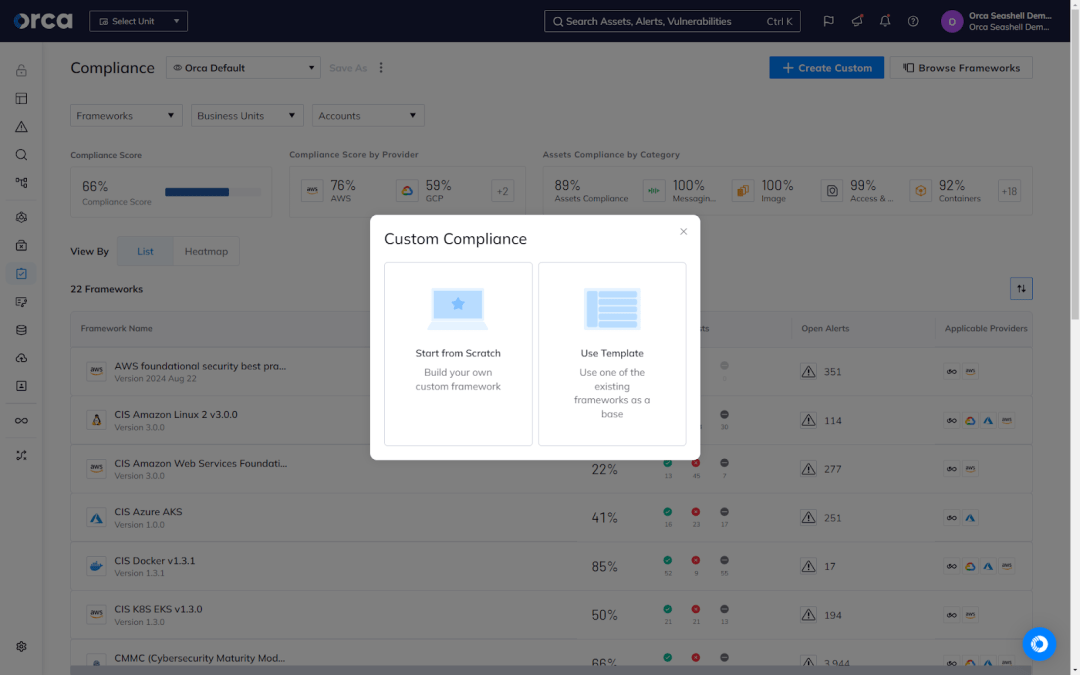
Set up your compliance frameworks
We covered the importance of compliance earlier. To help accelerate and facilitate it, many cloud security solutions provide built-in compliance capabilities. Advanced solutions offer off-the-shelf templates for major regulatory frameworks and industry standards. These enable you to automatically begin tracking and monitoring your compliance status against those benchmarks, saving you the time and effort of manually documenting framework controls, recording your compliance status against each, and reporting on them. To take advantage of this feature, these solutions require you to choose which compliance frameworks to track and continuously monitor against.
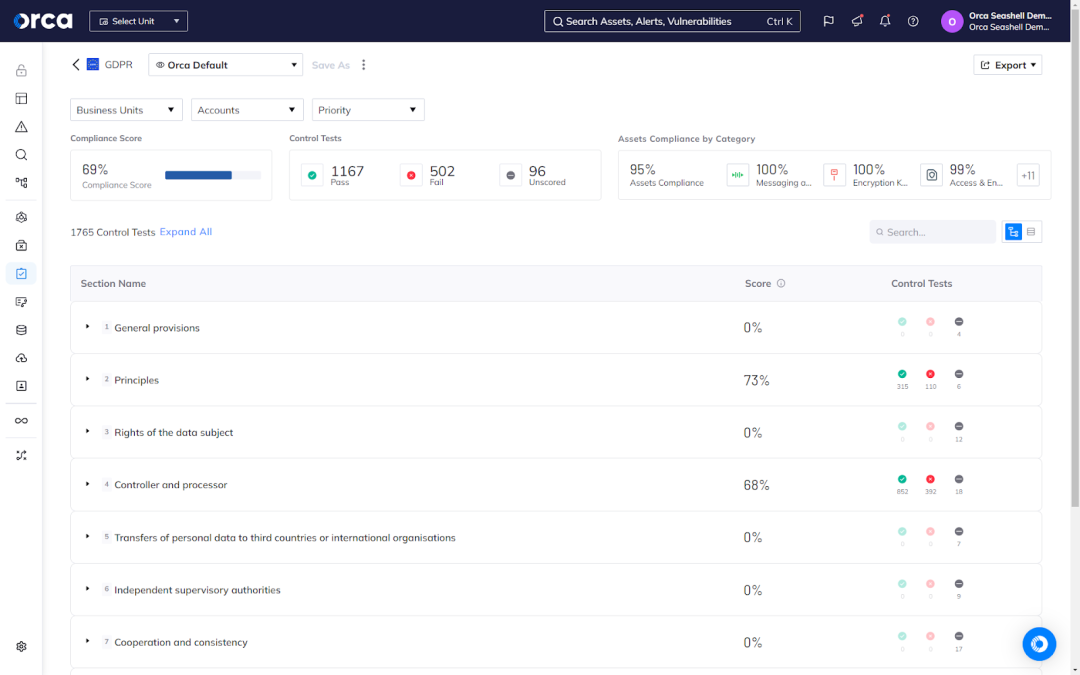
For example, the Orca Cloud Security Platform provides more than 160 out-of-the-box compliance frameworks, covering all major regulatory requirements and industry standards. By selecting one or more of these frameworks, Orca automatically maps your cloud assets and alerts to the relevant benchmarks and displays your current compliance status in real time.
Orca also makes auditing and reporting on compliance fast and easy. You can generate ad hoc reports on-demand in multiple formats, as well as schedule recurring reports to send to specific channels at predefined intervals. Orca also allows you to fully customize your compliance frameworks using any combination of the out-of-the-box templates, alerts from Orca’s Alert Library, or both.
Use automated features and workflows
Cloud security solutions automate a number of key tasks to keep your environments safe. Still, many offer the ability to program and leverage automated features to accelerate your team’s critical tasks. Regardless of the platform, best practice is to learn about all the automations your cloud security provider offers, do so from the initial phases of your partnership, and then set up and customize those features to leverage their benefits.
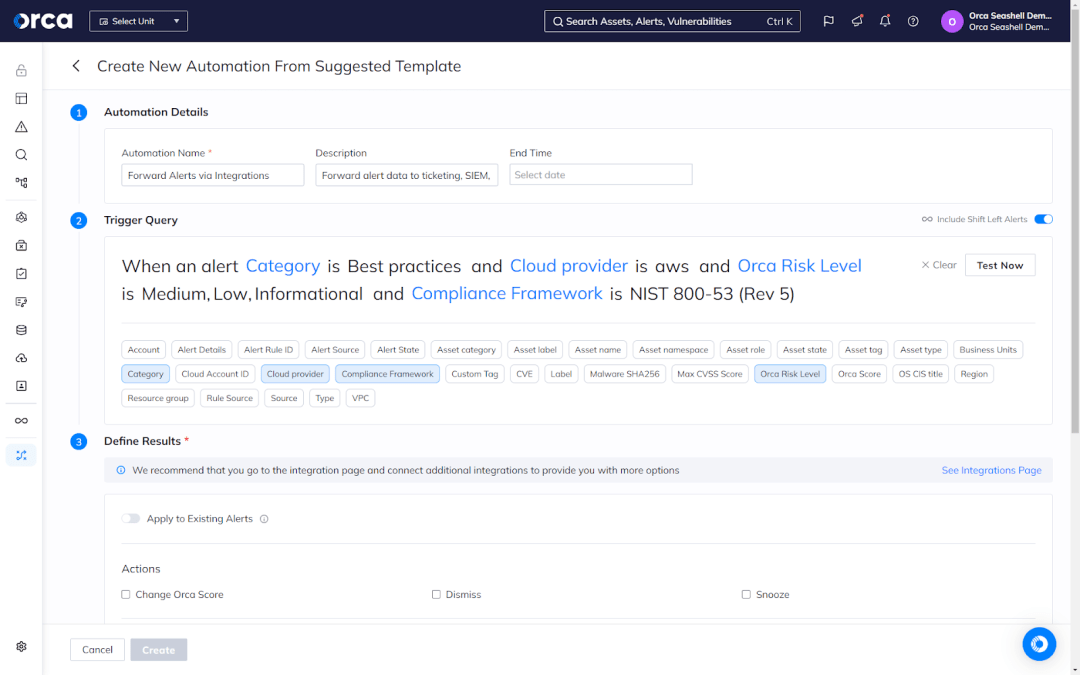
For example, the Orca Platform offers a number of features to automate critical tasks. This includes Auto-Remediation, which enables users to remediate a risk in one click. Orca also offers the ability to build Automations. In the Orca Platform, Automations are customizable workflows that perform actions based on predefined conditions that you set up.
You can, for example, build an Automation that automatically creates a ticket in Jira or ServiceNow for every risk detected that applies to the NIST 800-53 compliance framework. Meanwhile, the appropriate team and developer would see the ticket and could start resolving the issue, accelerating your Mean Time to Remediation (MTTR).
The future of Cloud Risk Management
The future of Cloud Risk Management continues to change with the emergence of innovative technologies. Integrated, AI-driven solutions are reimagining the possibilities of end-to-end risk management, enabling organizations to proactively identify and mitigate risks before attackers can exploit them.
As cloud environments become more complex, new security challenges arise. Organizations must remain vigilant about emerging threats and adapt their strategies, particularly concerning multi-cloud deployments, serverless computing, and edge computing. AI and machine learning technologies are crucial in this landscape, as they can analyze large datasets to detect patterns and anomalies more quickly and accurately than human analysts. This capability is essential for spotting sophisticated attacks and managing various cloud security risks.
About the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first Cloud-Native Application Protection Platform (CNAPP) that identifies, prioritizes, and remediates security risks and compliance issues across the multi-cloud environments of AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
The Orca Platform consolidates Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), Cloud Infrastructure Entitlement Management (CIEM), Vulnerability Management, API Security, and other solutions in a single platform. Leveraging a Unified Data Model, Orca contextualizes risks and recognizes when seemingly unrelated issues can create dangerous attack paths. This enables Orca to prioritize risks effectively, reduce alert fatigue, and ensure your teams can focus on the most critical and important tasks.
After a fast deployment that takes minutes, Orca provides deep and wide visibility into all cloud assets and helps organizations continually improve their cloud security posture.
Schedule a demo with one of our experts to see how the Orca Cloud Security Platform can boost your cloud security.
Conclusion
Cloud Risk Management is crucial for keeping your cloud environments and organizational data safe from potential threats. As technology continues to evolve, staying informed about emerging threats and adopting best practices is more important than ever.
Looking ahead, taking a proactive approach to risk management will be at the heart of your security strategy. By anticipating and tackling risks head-on, you can better protect your valuable cloud assets. Solutions like Orca Security can simplify your efforts and provide you with the insights you need to feel confident in your security stance.
FAQs
Why is Cloud Risk Management important?
Cloud Risk Management is crucial as organizations increasingly depend on cloud computing. Cloud Risk Management helps organizations reduce their attack surface, accelerate their Mean Time to Remediation (MTTR), protect their cloud data and assets, and help prevent costly security incidents.
What does Cloud Risk Management entail?
Cloud Risk Management involves identifying, assessing, and mitigating risks and compliance issues associated with cloud computing. This process requires cloud security technology and involves continuous monitoring, risk detection, risk prioritization, risk remediation, and compliance.
What is a cloud risk assessment?
A cloud risk assessment is a systematic process of evaluating potential risks in your cloud environment. It involves analyzing your cloud infrastructure, applications, and data to identify vulnerabilities and potential threats. This assessment helps prioritize risks and develop strategies to address them effectively.




