According to the 2025 State of Cloud Security Report, 78% of organizations have at least one IAM role that has not been used in the last 90 days. These forgotten and neglected identities are increasingly common in cloud environments—and they’re exactly the kind of soft targets attackers look for.
Inactive identities offer a low-friction path for attackers to gain initial access, move laterally, escalate privileges, and carry out other malicious activities. For security teams, they represent a persistent and growing challenge: one that requires full visibility and scalable remediation.
To address this, Orca is introducing new enhancements designed to help organizations detect, prioritize, and remediate inactive identities—quickly, effectively, and at the scale of the cloud. The latest release further strengthens the Cloud Infrastructure Entitlement Management (CIEM) capabilities of the Orca Cloud Security Platform and helps teams reduce identity-related risk at scale.
What are inactive identities?
In cloud environments, an identity is generally considered inactive if it hasn’t been used for 90 days or more. These typically include:
- Users: Human identities with access credentials and permissions
- Groups: Collections of users with shared access privileges
- Roles/service accounts: Permissions that can be assumed by services, applications, or users
As environments evolve, these identities can accumulate—especially in large organizations with frequent changes in teams, roles, or services.
Why is Orca expanding its identity hygiene capabilities?
As cloud environments grow in size and complexity, so do identity risks. Inactive identities tend to accumulate over time—especially in large organizations with dynamic development teams, shifting priorities, and constant onboarding/offboarding. These dormant accounts create exploitable gaps that attackers are quick to target.
Most security teams lack the time and tooling to manually track down every inactive identity across their environment. Orca’s new enhancements are designed to close that gap, giving teams the visibility, context, and control they need to improve identity hygiene without additional overhead.
Key capabilities for Identity Hygiene
Orca provides several features for detecting, prioritizing, and remediating inactive identities, including:
#1. Centralized visibility across identity types
Security teams often lack a comprehensive view of their inactive identities, scattered across providers and identity types.
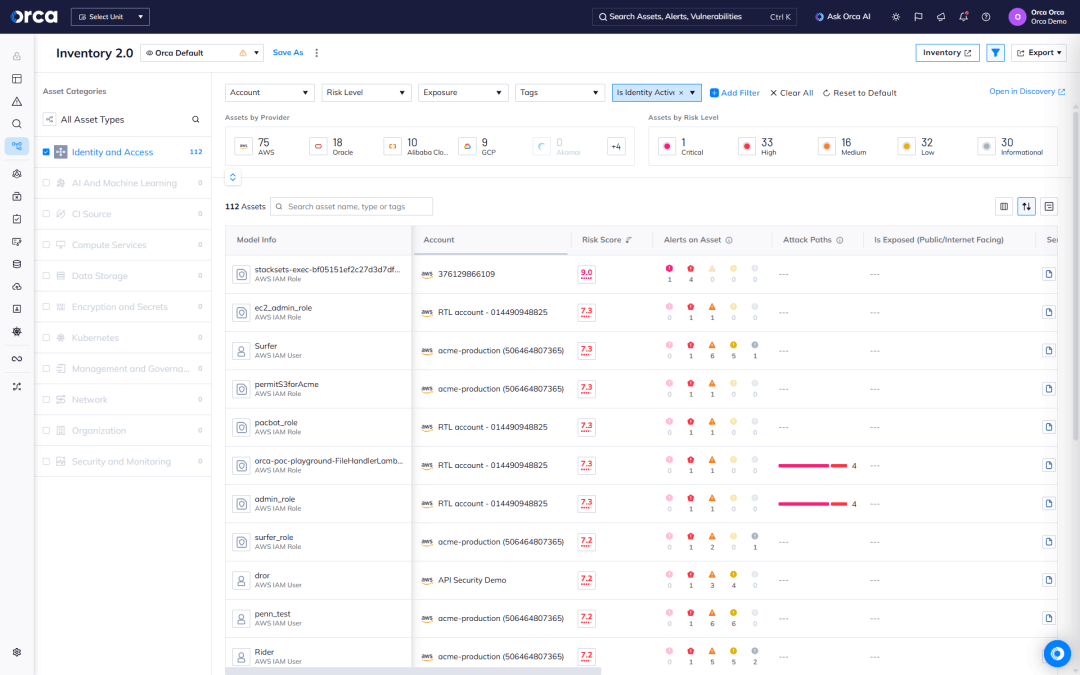
Orca now consolidates this visibility in one place. Teams can view all inactive identities across cloud accounts, filter by identity type (user, group, or role) or last active time, and sort by provider to better organize remediation efforts.
Within our Identity and Access dashboard, teams can also access a table view that displays inactive identities alongside their associated risks and attack paths, streamlining investigation and prioritization.
#2. Fast discovery with built-in and AI-powered queries
Finding inactive identities typically requires writing and executing complex queries across multiple cloud platforms. Orca removes that barrier by offering a set of built-in, pre-defined queries in the Orca Query Catalog—allowing teams to quickly answer common Identity Hygiene questions without extensive effort.
For even faster results, teams can also use Orca’s AI-Driven Search, which supports plain-language queries to locate inactive identities and related risks across their entire cloud estate.
#3. Prioritized and actionable identity alerts
Not all inactive identities pose the same level of risk—but many tools fail to distinguish between them, overwhelming teams with low-priority noise and leaving critical issues buried in the alert queue.
Orca dynamically detects and prioritizes risks across all inactive identity types. The platform analyzes each risk holistically in the context of your full cloud estate, accounting for factors such as attached permissions, resource access, and external exposure. This allows security teams to quickly identify which inactive users, groups, or roles pose the greatest threat and take action accordingly.
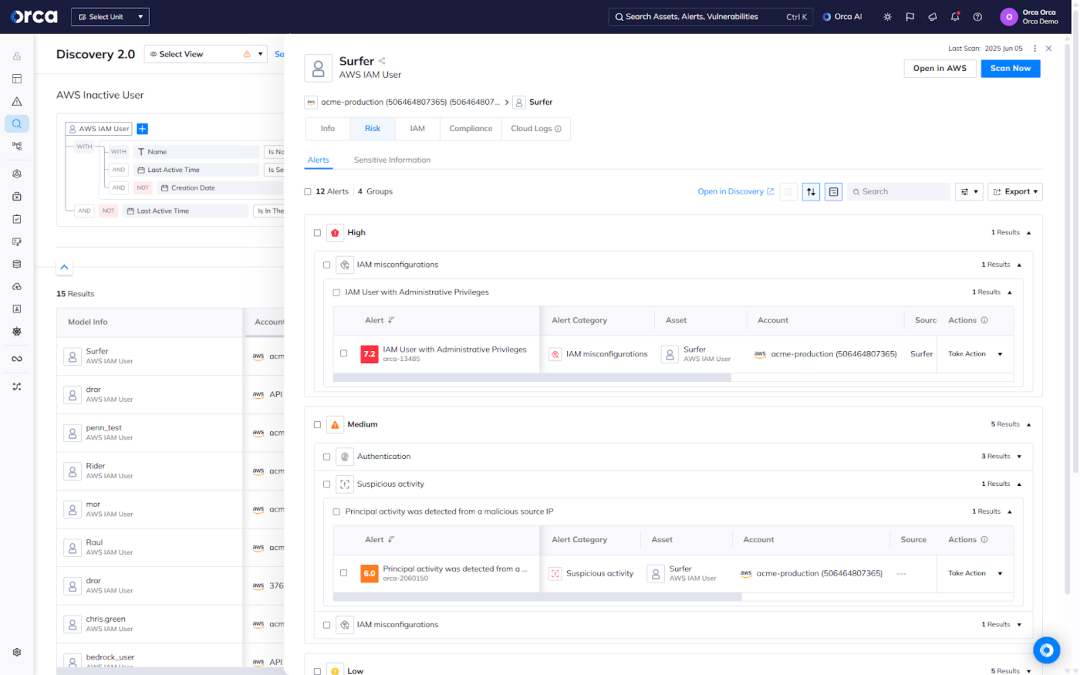
#4. Fast and easy remediation
Even after identifying high-risk inactive identities, remediation can be a slow, manual process, especially when teams rely on legacy tools or lack clear next steps. These delays give attackers more time to exploit gaps and increase the likelihood of an incident.
Orca accelerates response with multiple remediation options, including AI-Driven Remediation instructions and code as well as guidance developed by Orca experts. These options enable faster and more effective identity clean up—and help teams take immediate, informed action to reduce risk.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ Technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform, including its capabilities for identity hygiene? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can expedite and enhance your CIEM.






