The development of cloud-native applications is fueling business innovation, but also expanding the attack surface. According to the Verizon Data Breach Investigations Report (DBIR), stolen credentials remain the leading cause of breaches in cloud environments, underscoring the growing risk tied to application-level identity and access controls.
This aligns with findings from the Orca 2025 State of Cloud Security Report, which reveal that 85% of organizations have plaintext secrets embedded in their source code repositories. These exposed credentials, tokens, and keys can be easily exploited by attackers to infiltrate cloud workloads, exfiltrate data, or escalate privileges.
When application secrets are mishandled, the risk extends far beyond the code repository. It opens pathways to compromise CI/CD pipelines, container registries, and production workloads, turning simple developer oversights into full-scale breaches.
Application Security (AppSec) addresses these challenges by embedding protection into every stage of the software development lifecycle (SDLC)—from secure coding and dependency management to testing, deployment, and runtime monitoring.
Application Security defined
Application security refers to the practices, technologies, and governance frameworks that protect applications from unauthorized access, misuse, alteration, or compromise. It spans every stage of the SDLC, embedding security into development rather than bolting it on after release.
Modern AppSec extends beyond traditional firewalls or web application protection. It integrates directly into CI/CD pipelines, automates testing, and continuously monitors applications in production. As cloud-native architectures multiply microservices and APIs, AppSec must evolve to protect code, dependencies, and data wherever they reside.
Why Application Security matters
Applications are now the front door to sensitive data and critical operations. A single vulnerability can trigger a breach with financial, operational, and reputational fallout.
In cloud and microservices environments, rapid deployments, open-source components, and third-party APIs create sprawling and dynamic attack surfaces. Key challenges include:
- Limited visibility: Teams often lack a complete inventory of apps, services, and APIs.
- Dependency risk: Open-source and third-party code introduce vulnerabilities.
- Architecture complexity: Serverless, containerized, and distributed systems complicate risk prioritization.
- Speed vs. control: Rapid DevOps cycles can outpace security oversight.
Embedding AppSec early—through “shift-left” testing, automated scanning, and continuous monitoring—helps ensure security keeps pace with innovation.
Key pillars of Application Security
Building an effective AppSec program requires a combination of governance, secure design, automated testing, and runtime protection.
Governance and SDLC integration
Define ownership, align AppSec with the SDLC, and establish clear policies for risk assessment, compliance, and remediation.
Secure coding and dependency management
Apply coding standards, input validation, and secure authentication practices.
Security testing, automation, and integration
Leverage security testing tools that automatically scan code for vulnerabilities, misconfigurations, and secrets. Ensure these tools include capabilities for static application security testing (SAST), software composition analysis (SCA), infrastructure-as-code (IaC) security, container image scanning, and Secrets Detection.
To catch risks early in development, integrate these security checks with integrated development environments (IDEs), source code managers (SCM), and CI/CD pipelines.
Also, enable and customize your security policies to ensure guardrails reflect the desired level of enforcement (block upon detection or only notify developers of risk).
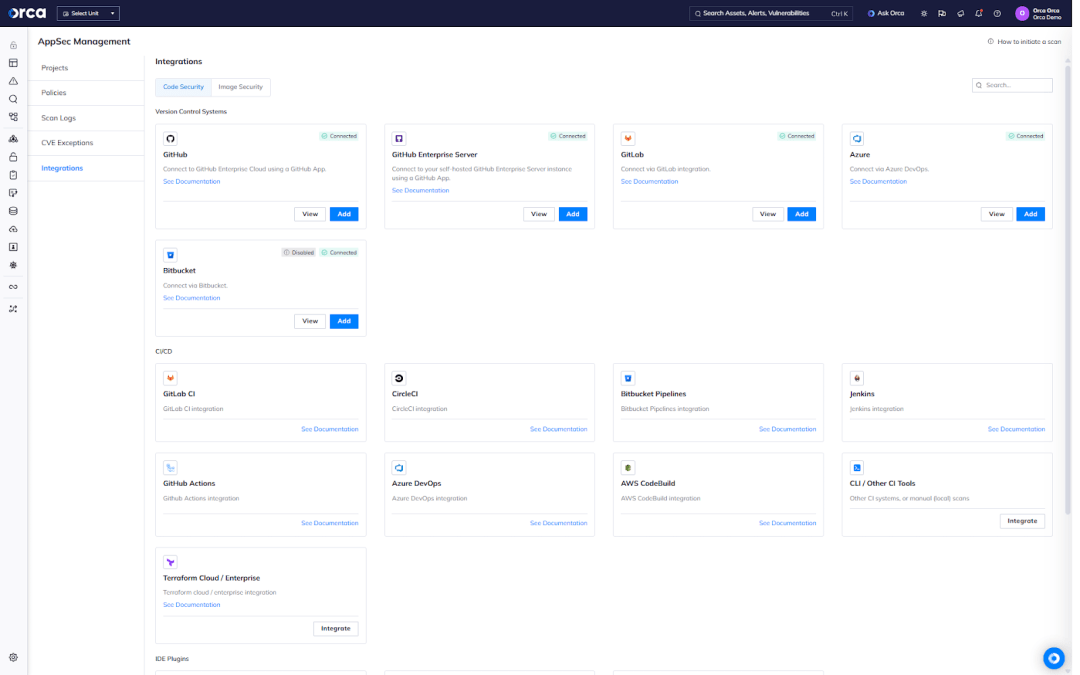
SCM Posture Management
SCM Posture Management (SCM-PM) goes beyond code security to detect risks in SCM tool configurations. This can detect risks such as a change in repository visibility from private to public, ensuring teams can leverage the native security features of SCMs according to best practices.
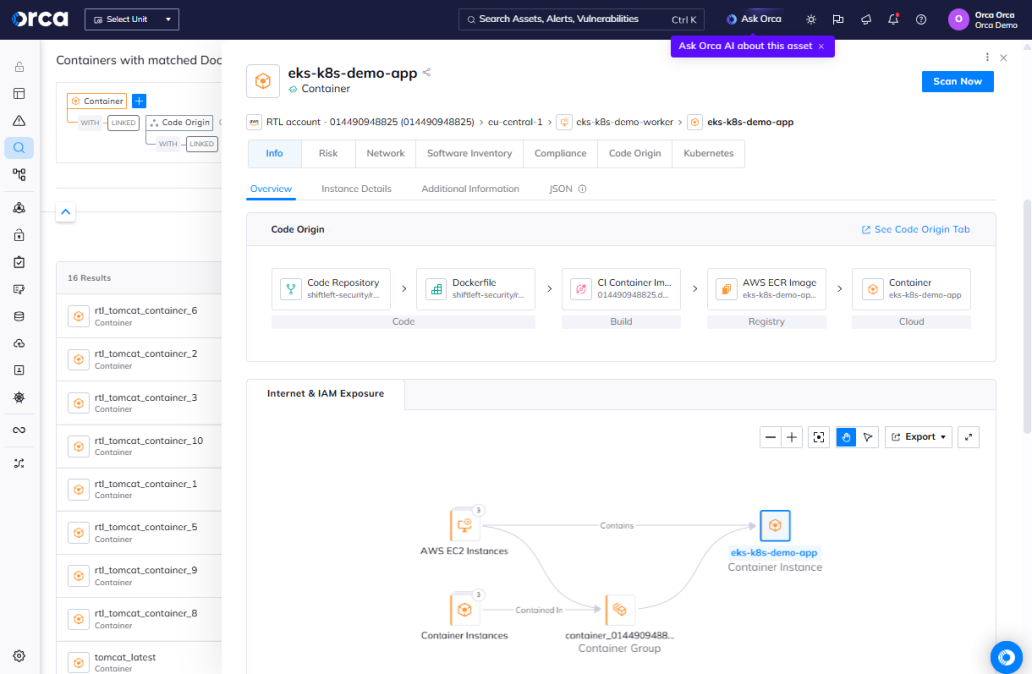
Cloud-to-Dev tracing and remediation
Use a Cloud-Native Application Protection Platform (CNAPP) to detect and prioritize runtime risks, and correlate them to their origins in the SDLC. Cloud-to-Dev tracing streamlines investigation and remediation, enabling security teams to quickly see the code owner and origin of a risk and fix issues at their source.
Continuous feedback and improvement
AppSec is iterative. Track metrics like time-to-remediate, critical findings, and coverage. Refine the program based on incident learnings.
Common risk vectors in Application Security
Applications face a wide range of threats, many captured in the OWASP Top 10 (2025). These include:
- Broken Access Control
- Security Misconfiguration
- Cryptographic Failures
- Injection
- Software Supply Chain Failures
- Vulnerability Management Failures
- Authentication Failures
- Logging and Monitoring Gaps
Understanding these patterns helps teams prioritize mitigations that reduce real-world risk.
Strengthening your Application Security
Improving AppSec maturity requires a structured, continuous approach:
Step 1: Discover and inventory assets
Identify all applications, APIs, and dependencies. Classify by sensitivity and exposure.
Step 2: Customize and enable security policies
Customize and enable your security policies across SAST, IaC Security, SCA, container image scanning, Secrets Detection, and SCM-PM. Set guardrails that align with your organizational goals for development.
Step 3: Embed controls and automate testing
Integrate security checks with IDEs, SCMs, and the CI/CD pipeline to create a seamless and secure experience for developers.
Step 4: Monitor and protect in runtime
Use Cloud-to-Dev capabilities to detect and prioritize cloud risks and remediate them at their source.
Step 5: Build governance and culture
Assign ownership, define remediation SLAs, and train developers and security teams to collaborate on shared goals.
How Orca Security helps
As applications shift to cloud-native environments, teams need security that extends from code to runtime without adding complexity. The Orca Cloud Security Platform delivers comprehensive Application Security capabilities to help you secure every stage of the development process.
With Orca, you can:
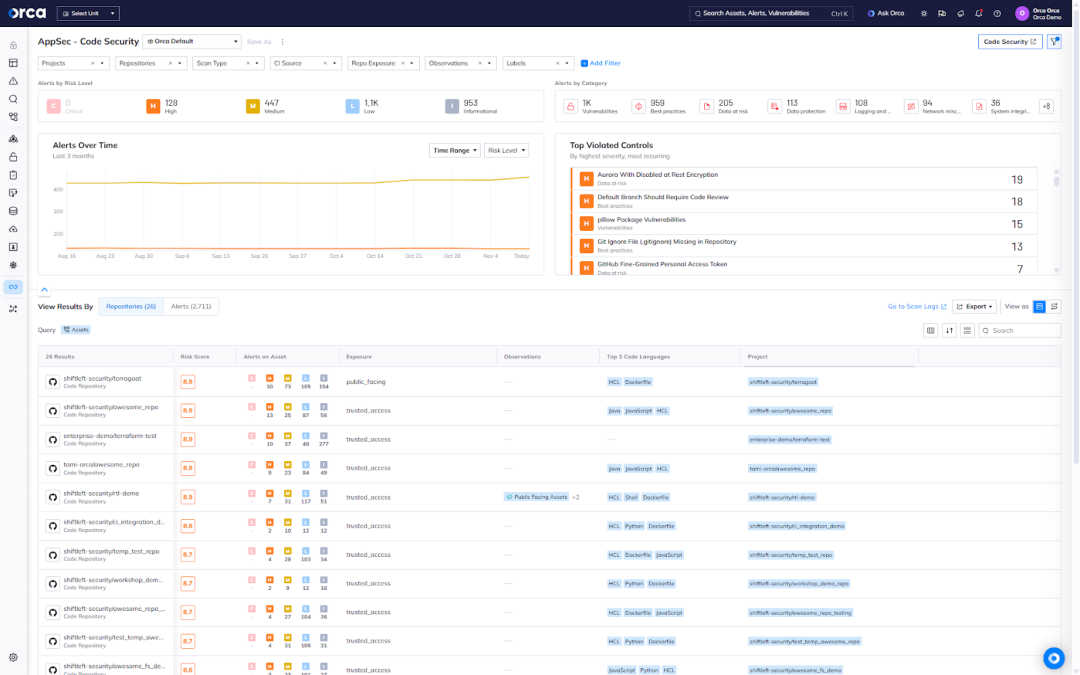
- Scan IDEs, repositories, and build pipelines to identify exposed secrets, vulnerabilities, and misconfigurations early in the SDLC.
- Implement customizable guardrail policies to catch risks before they can reach production.
- Correlate cloud risks with code issues to accelerate investigation and remediation and fix issues at their source.
- Integrate security checks with SCMs, IDEs, and CI/CD pipelines, making a seamless developer experience.
With Orca, teams can unify security from code to cloud, enabling them to reduce risk effectively and at scale.
Bringing it all together
Applications are the backbone of modern business, and protecting them is no longer optional. Effective application security is about building resilience into software from the start: embedding controls, automating testing, and aligning to frameworks like OWASP.
If your organization develops or relies on applications in the cloud, make application security a foundation, not an afterthought.
Ready to learn more?
To explore how Orca unifies Application and Cloud Security in one platform, schedule a personalized demo with our team today.






