Agentless-First AWS Cloud Security Solutions
Get complete visibility and security for your entire AWS environment, including databases, storage buckets, workloads, applications, and more–integrated across the full stack and application lifecycle.
Orca is Deeply Integrated with AWS
Orca is an AWS Security Software partner that has achieved the AWS Security Competency and is AWS Service Ready for Amazon Linux 2. Orca is integrated with 100+ AWS services and products, including EC2, ECS, EKS, Fargate, Lambda, GuardDuty, CloudTrail, Bedrock, Security Lake, Security Hub, and more. Orca is available for purchase in the AWS Marketplace.
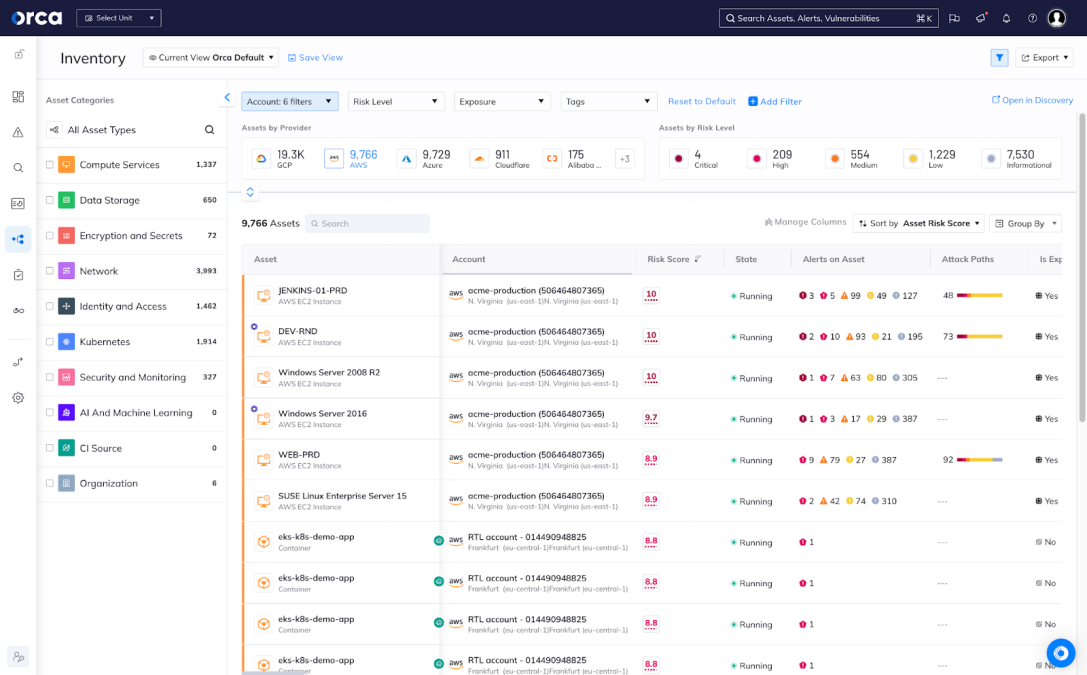
Detect critical risks across your AWS environment
Orca’s SideScanning™ technology reads your cloud configuration and workloads’ runtime block storage out-of-band to create a complete risk profile of your AWS cloud estate in minutes.
- Covers all your AWS workloads – VMs, containers, and serverless, including EC2, EKS, ECS, and Lambda instances
- Detects vulnerabilities, malware, misconfigurations, IAM risks, lateral movement risks, API risks, unsecured sensitive data, and much more
- By integrating with AWS services and delivering an agentless-first approach, Orca provides comprehensive security across your AWS environment quickly
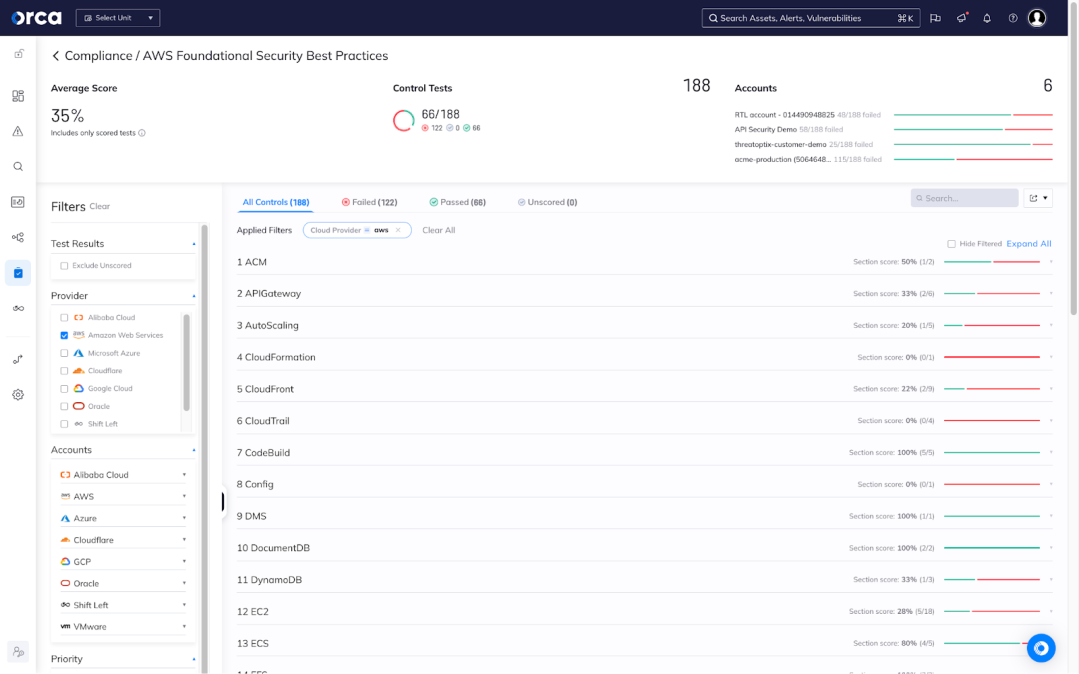
Simplify AWS compliance with a single platform
Achieve continuous compliance more easily than ever before with a single cloud security platform that covers 100% of your AWS environment, avoiding compliance gaps and failed audits:
- Meet over 100 compliance frameworks and key CIS benchmarks, including NIST 800-53, SOC 2, ISO 27001, AWS CIS, Docker CIS, Apache CIS, and Windows CIS, to name a few.
- Demonstrate your ability to meet key data privacy mandates in your AWS environment, including PCI-DSS, GDPR, HIPAA, and CCPA.
- Leverage Orca’s built-in compliance templates, or customize them to meet your specific needs.
Case Study
How BTG Expanded Globally with AWS and Orca Security
Discover how BTG, the largest investment bank in Latin America, successfully launched its first investment app for end customers with the help of AWS. Learn how Orca’s cloud security solutions and integration with Jira reduced BTG’s detection and response time by 30%, ensuring a secure, scalable, and fast deployment.
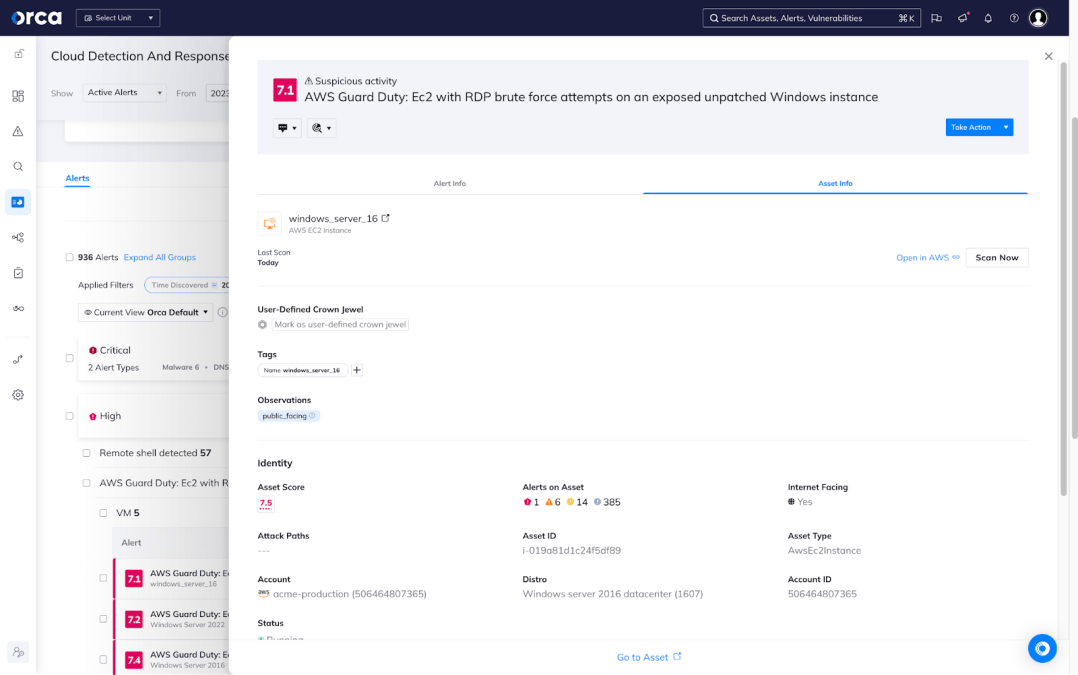
Supercharge your Amazon GuardDuty threat intel
Orca naturally digests Amazon GuardDuty alerts and adds contextual information to provide the basis for risk prioritization. Together, the platforms allow mutual customers to continuously monitor malicious activity and unauthorized behavior in your AWS accounts, workloads, and data, while relating such threats to the larger holistic story within your cloud estate.
- Better Visualization: See how this alert might play a role in a much larger attack path that could lead to the compromise of more sensitive data.
- More Context: Understand why an alert matters with a summary digest, along with recommended remediations.
- Accurate Classification: Group GuardDuty and other AWS alerts together based on compliance, severity, asset or risk type.
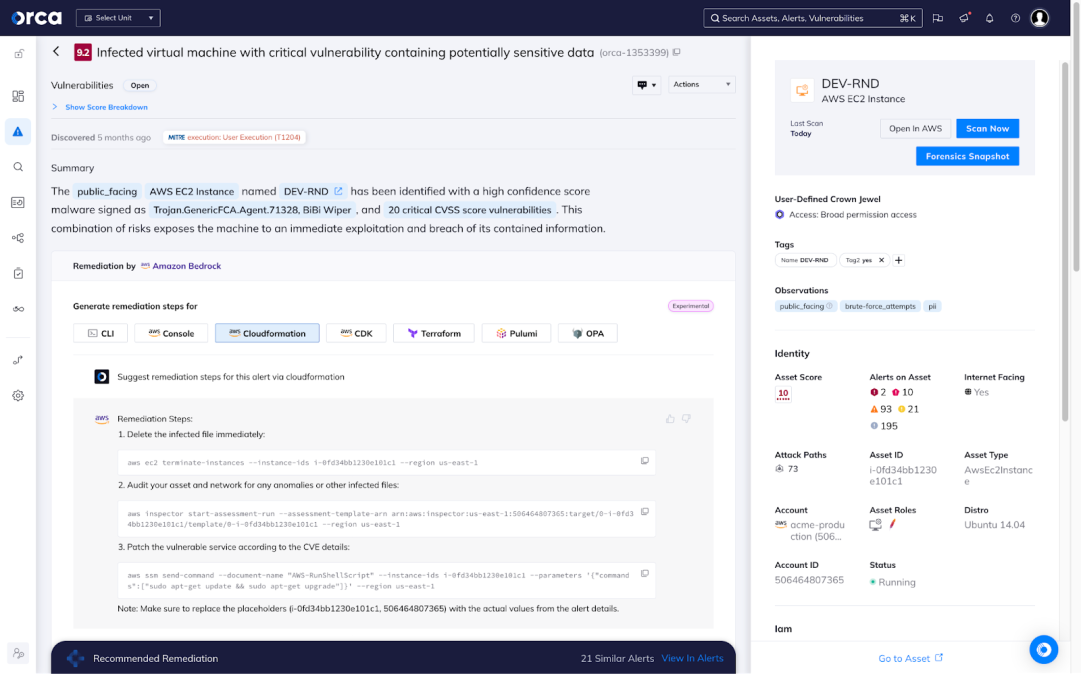
Accelerate remediation using AI-powered remediation with Amazon Bedrock
Instantly generate high-quality remediation instructions for each alert straight from the Orca Platform, enabling your team to address cloud vulnerabilities and risks 2-3 times faster. Data privacy is ensured by anonymizing requests and masking any sensitive data.
- Copy and paste remediation code into a command line interface or Infrastructure as Code (IaC) provisioning tools, or follow steps in the console.
- Leverage Amazon Bedrock as your AI engine to save teams’ time and effort.
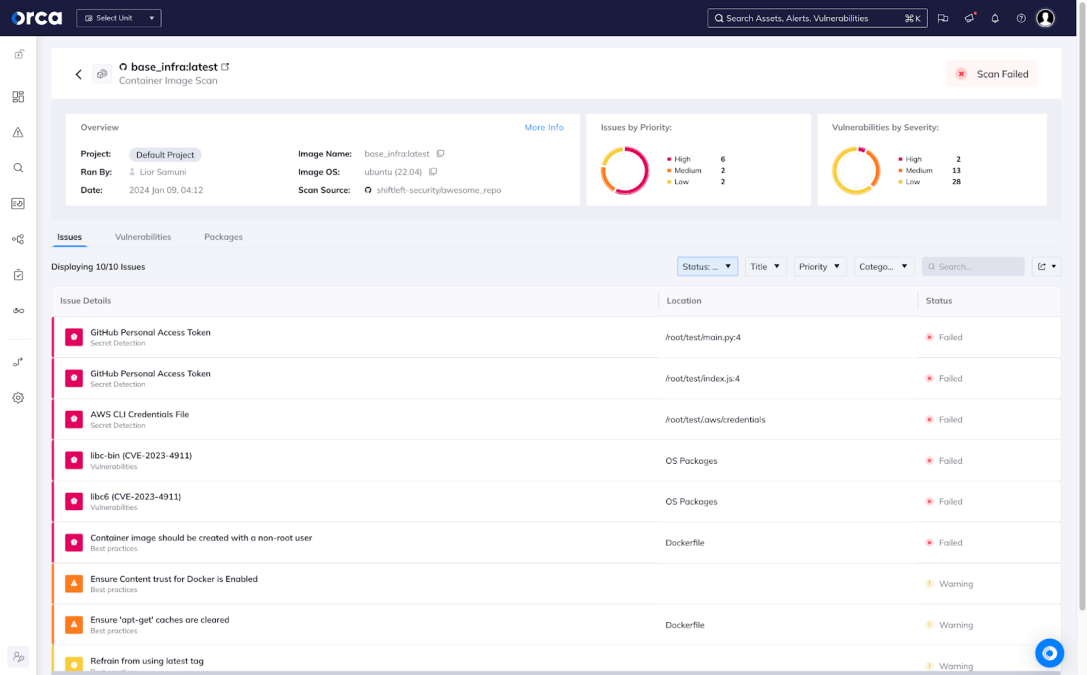
Integrate security into your CI/CD workflows
Orca integrates with all of the AWS services and tools you use to build and deploy your applications. This ensures that critical risks are identified before they reach production environments, ensuring security is implemented by design.
- Integrated with AWS tools: Orca integrates with Amazon CloudFormation, as well as third-party CI/CD tools, to automate IaC and container image scans as you build and deploy your applications.
- Support for IaC templates and container images: Orca supports AWS CloudFormation, as well as HashiCorp Terraform of Kubernetes yaml, as well as modern container image formats.
- Simplified policy management: Easily manage and customize over 1000+ policies, or leverage Orca’s pre-built best practices to improve code quality pre-deployment.
About Orca and AWS
Orca is an AWS Security ISV partner. Orca achieved AWS Security Competency and is AWS Service Ready for Amazon Linux 2. Orca is also a member of the exclusive AWS Co-sell program, ISV Accelerate, and is integrated with multiple AWS services and products, including EC2 Image Builder, Private Link, and more. Orca is available for purchase in the AWS Marketplace.