Last week we announced a couple of new Orca capabilities: Agentless Reachability Analysis and Dynamic Runtime Reachability Analysis. In this blog, we’ll dig more into the specifics of our patent-pending Agentless Reachability Analysis and how to use it in the Orca Platform. We’ll cover Dynamic Runtime Reachability Analysis in a separate blog.
In the last 25 years, we’ve seen disruption in three major areas of technology – IT infrastructure, building software, and securing organizations. While agile processes and cloud computing accelerated the builder’s speed to market, cybersecurity has been driving resilience through better detection and response at runtime, as well as preventative action across the entire application lifecycle.
The Challenge: Too many software dependency vulnerabilities to investigate and fix
While the use of open-source software has increased speed-to-market for innovation, it’s also made vulnerability management and patching more complex. The pre-production approach for security attempts to catch issues before they get shipped. However, code scanners end up generating an overwhelming number of vulnerability alerts for software packages and their dependencies.
To tackle the growing pile of remediation work, vulnerability management teams try to filter by what fixes are available and if there are active exploits happening. Even then, there are thousands of issues to address, and team members still have to test any fixes before deploying to make sure they don’t break any other parts of the app. This effort is also thwarted by the complexity of parent-child software packages where the parent may not have been updated to use a fixed dependency.
How can vulnerability management teams effectively prioritize what to patch, considering the trade-off between speed to market for new features and time sacrificed to test and deploy available security fixes?
The Solution: Know which vulnerable software packages are reachable by attackers in production
Orca’s newly released Agentless Reachability Analysis focuses on where application security and cloud-native security intersect in production. Vulnerability management teams get reachability evidence for container assets out-of-the-box, which drives patch prioritization based on whether an attacker could reach and execute a vulnerable software package – no agents or extra integrations required.
Other static reachability analysis tools require integrations with the CI/CD pipeline or CLI commands, and while some of these tools give you function-level visibility, the function required to exploit a vulnerability is rarely included in standard vulnerability databases.
With Orca’s patented SideScanning™ technology, we’re able to show you all of the installed packages running in your environment. Our Unified Data Model allows us to drill down to view which packages:
- Have a vulnerability, ranked by severity
- Have an exploit active in the wild
- Are potentially reachable by an attacker

The Cyentia Institute shared that teams only have the capacity to remediate 1 in 10 vulnerabilities in their environment in a given month, so it’s critical to direct everyone’s time effectively and efficiently. Our Agentless Reachability Analysis provides the immediate answer to which vulnerable packages to prioritize first—no agents to deploy and no extra integrations to set up outside the standard initial setup to implement the Orca Platform.
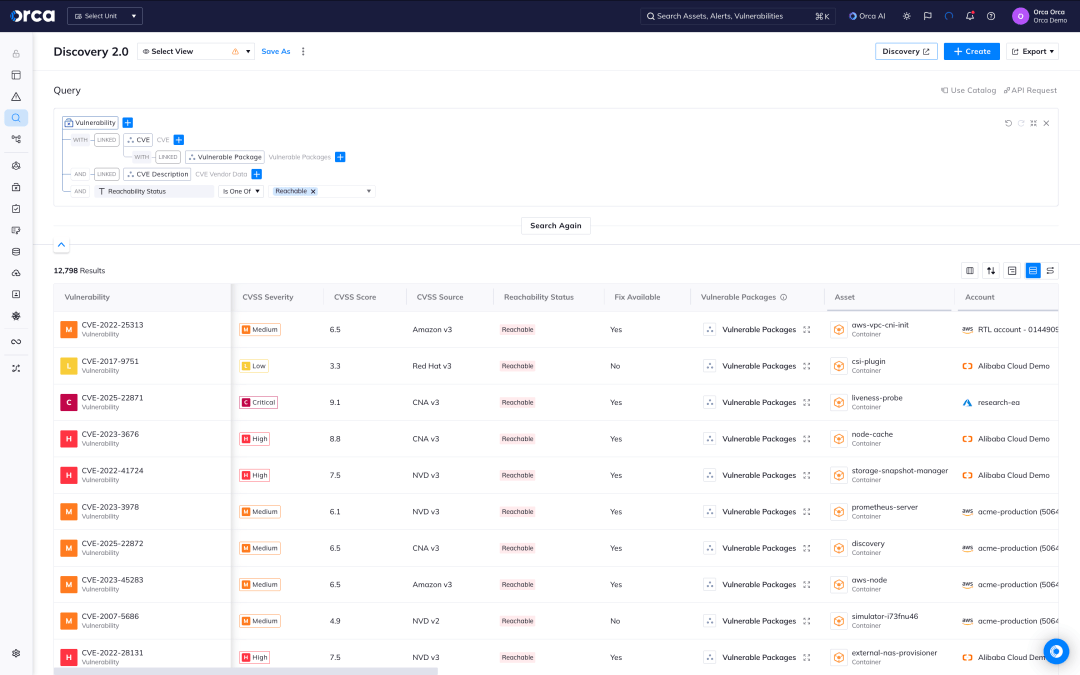
Additionally, to enhance code security and reduce their attack surface, teams may want to get a list of all installed packages that are not reachable, regardless if they are vulnerable, so that they can be removed.
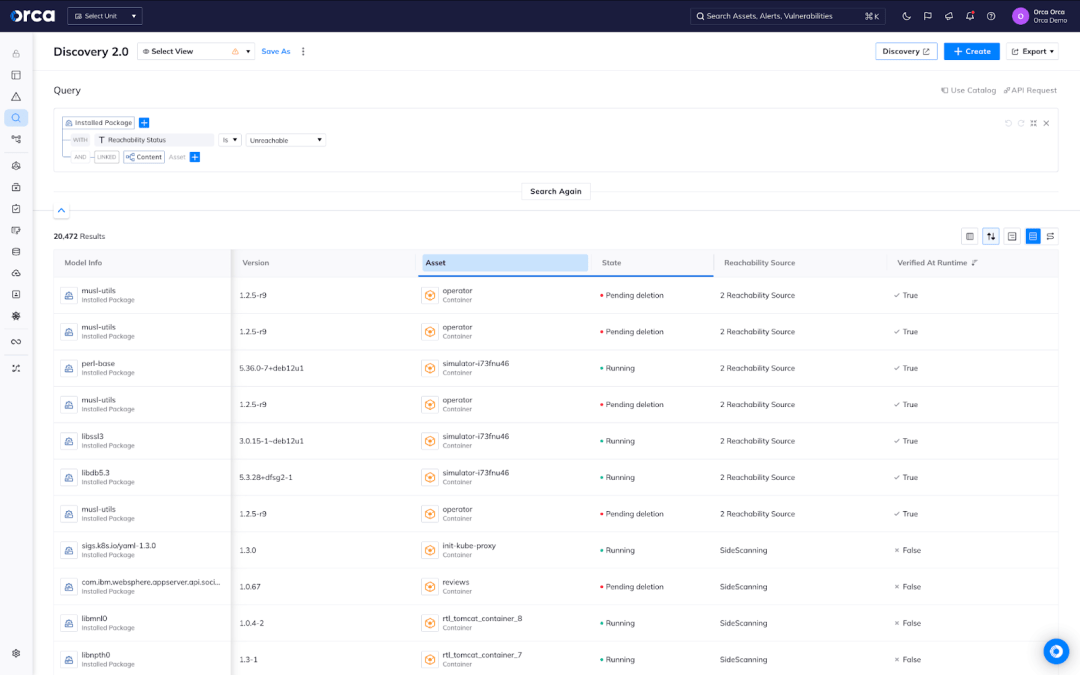
How Agentless Reachability Analysis Works
To get started with Orca, customers only need to follow a simple 3-step setup connecting with their cloud service provider. Within minutes, Orca’s patented SideScanning™ technology gathers information from the cloud control plane and takes snapshots of the data plane to enumerate containers, among other cloud assets. Orca delivers a complete inventory of your cloud estate in minutes with contextual information about misconfigurations, vulnerabilities, and other security risks and compliance gaps.
Orca has expanded upon this foundation to drive Agentless Reachability Analysis through patent-pending technology. The Orca Platform intelligently inspects container environments to understand application behavior and determine which components are actively used. By simulating runtime conditions and examining configurations, Orca identifies which resources are reachable or not reachable.
Command Your Cloud with Orca
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in seeing how the Orca Platform can help you command your cloud? Schedule a personalized 1:1 demo.





