Table of contents
- What is agentless vs. agent-based security?
- What is agentless security?
- What is agent-based security?
- Advantages of agent-based security
- Disadvantages of agent-based security
- Advantages of agentless security
- Disadvantages of agentless security
- What are the key considerations of agentless vs. agent-based security?
- Recap: agentless vs. agent-based security
- Agentless-first security: Orca’s revolutionary approach to cloud-native protection
- Conclusion
- FAQs
According to some estimates, the global cloud security market value will reach approximately $156 billion (USD) by 2032, more than three times its value in 2024. As organizations ramp up investments in cloud security products, they inevitably encounter a common question in the market, “What’s better for my organization: agentless or agent-based security?”
The answer not only presents important implications, it can drastically impact security outcomes. And it highlights the importance of gaining a thorough understanding of the pros and cons of each technology.
In this in-depth guide, we examine agentless vs. agent-based security, what they entail, how they compare, and how to choose the best approach for your organization.
What is agentless vs. agent-based security?
The debate between agentless vs. agent-based security revolves around what provides more value, when, and to whom. Simply put, “agentless” refers to cloud security technology that monitors cloud resources via APIs and non-invasive methods. “Agent-based” points to technology that requires an application installed on a workload or device in order to monitor it. Both provide different advantages and disadvantages.
What is agentless security?
Agentless security is an approach to securing resources without deploying agents to each asset. Instead, agentless security solutions typically work by scanning and monitoring endpoints from the “outside” rather than running utilities directly on them. They can do this by examining information that’s available over the network, as well as parsing the configuration data that governs resources. In addition, some agentless solutions integrate with cloud providers’ APIs to obtain additional data about workloads without having to deploy agents directly alongside those workloads. These solutions read the runtime block storage of virtualized workloads out of band and cross-reference them with information pulled from those APIs.
What is agent-based security?
Agent-based security is the deployment of software agents on each endpoint that businesses need to monitor and secure. The software agents are responsible for collecting data from the endpoints. They may also be used to enforce security rules or take action on endpoints.
Advantages of agent-based security
An agent-based strategy has been the way businesses traditionally approached security. That’s because agent-based security offers the advantage of a simple, straightforward means of monitoring and controlling endpoints. Agents don’t require security monitoring platforms to create any special integrations with third-party services (like cloud providers’ APIs) to collect the data they need.
Here are the main advantages of agent-based security solutions:
- Real-time monitoring and in-depth scanning: Because agent-based solutions are installed on the workload, they can conduct real-time continuous scanning to detect threats and accelerate response. For example, agent-based security solutions can detect fileless execution in runtime environments. An attack technique, fileless execution happens when attackers execute malware directly from memory rather than a disk, making it much harder to detect even known variants of malicious code.
- Real-time incident response: Because agents reside within each workload they protect, they can provide real-time incident response to minimize the potential impact of a security incident in progress.
- Endpoint automation and control: Because they’re installed on the endpoint, agents can enforce defined security policies and perform key tasks without intervention, such as making configuration changes or applying patches.
Disadvantages of agent-based security
Despite the previous benefits, agent-based security solutions also come with limitations. These disadvantages include the following:
- Incomplete coverage and blindspots: Visibility is limited to the subset of assets that are known, accessible, and capable of hosting an agent. Agent-based solutions often result in blindspots, because agents can’t be installed on every asset due to time restrictions, understaffed teams, and the ephemeral nature of the cloud and cloud-native technologies, such as serverless workloads, that don’t support agents.
- Time-intensive: Deploying agents is a time-consuming process. Even if deployment is automated by software tools, engineers still have to configure the tools and monitor agent deployments to make sure they proceed as expected.
- Lack of universal support: Agents may not support all endpoint operating systems or configurations. This is especially challenging for businesses whose infrastructure includes resources like IoT devices in addition to standard servers and PCs.
- Resource overhead: Agents consume resources when they run. That means agent-based security can increase a business’s overall infrastructure spending. It may also deprive actual workloads of the resources they need to perform adequately, especially during periods of peak demand.
- Missed endpoints: You can’t deploy agents to endpoints that you don’t know about – and many businesses don’t know about all of their endpoints due to practices like shadow IT (meaning the creation of IT resources by employees who act without official approval). In
- Out-of-date agents: Agents need to be kept continuously up to date to handle the latest threats. But updating agents can take time, which means attackers may start actively exploiting a new vulnerability before agents are updated and IT teams are made aware of it.
- Friction with developers and DevOps: Agent-based security solutions require developers and DevOps teams to manually install agents for each workload. They also require developers to address issues outside of developer environments and when most time-consuming and disruptive to their daily workflows, as highlighted in the Gartner 2023 Market Guide for CNAPP. Both conflict with modern DevOps practices and create friction and tension between teams.
Advantages of agentless security
Agentless security offers several advantages from an administrative, performance, and coverage perspective. The benefits include:
- Fast and simple deployment: Because there are no agents to deploy, agentless security solutions can be up and running in minutes, rather than hours or days. In addition, engineers don’t have to worry about managing a complex deployment process.
- Complete coverage: By scanning all workloads from a central location—as opposed to attempting to deploy agents to each workload—agentless security platforms are better positioned to identify and secure all IT resources, even those that the central IT department doesn’t know about.
- Automatic scaling: Without the need to install an agent on each workload, agentless technology scales seamlessly and automatically to cover new cloud resources.
- No performance impact: Agentless security doesn’t increase the load placed on host infrastructure, so it doesn’t negatively affect workload performance or increase infrastructure costs.
- DevSecOps support: Agentless security supports the adoption of DevSecOps, or the process of infusing security across every stage of the SDLC. Gartner’s 2023 Market Guide for CNAPP highlights the importance of agentless technology in empowering developers to take ownership of security by making it more agile, convenient, and integrated with their existing tools and processes. Agentless security technology provides the speed, agility, and visibility needed for DevSecOps.
Disadvantages of agentless security
Like agent-based tools, agentless security solutions also come with several downsides. They include:
- Lack of real-time visibility: Agentless solutions provide visibility through snapshots of cloud environments. While providing organizations with near-real-time intelligence, it includes a slight delay and doesn’t occur in actual time. Agentless technology also doesn’t provide the depth of visibility into each workload that an agent-based solution does.
- Near-real-time incident response: Agentless security tools offer near-real-time incident response. They can’t offer it in actual time like agent-based tools because they aren’t installed on each workload. Agentless tools rely on snapshots of the environment, leading to a slight delay.
- Lack of endpoint automation or control: Because agentless security solutions aren’t installed on each workload, they lack the same level of endpoint automation or control of workloads covered by an agent-based solution.
What are the key considerations of agentless vs. agent-based security?
When evaluating whether to choose an agentless or agent-based security, keep in mind the following considerations:
- Speed and ease of deployment: Agentless security solutions can deploy within minutes and calls for simple configurations. Meanwhile, agent-based security deployments can take considerably longer, requiring security to work with DevOps to install an agent on each workload for monitoring as well as configure them to the environment. Agentless security tools enable you to limit your risk exposure and faster.
- Visibility: Agent-based security solutions can provide granular visibility. This visibility doesn’t extend beyond covered workloads, resulting in blindspots when considering the totality of a cloud environment. Agentless technology provides full coverage of the cloud estate, including existing workloads and any created in the future. While agentless security solutions offer granular visibility into each workload, they don’t provide the depth of insight of agent-based alternatives.
- Sensitivity of the workload: Agent-based security solutions can provide runtime visibility and protection, which can provide significant value for mission-critical applications that warrant enhanced security. Meanwhile, agentless security tools can provide robust workload security at scale and across an entire environment.
- Scalability: Agentless security tools offer a scalable solution that doesn’t require intervention to cover new workloads, which occurs automatically. Agent-based technology, on the other hand, requires the manual installation of any agent needing monitoring.
- Coverage: Connecting via APIs, agentless security tools can provide full coverage of a cloud environment, monitoring both the control and data planes. Agent-based security tools only cover the part of the data plane where agents are installed.
- Maintenance: Agentless security solutions don’t require maintenance, while agent-based security tools need regular updates to ensure up-to-date protection against the latest threats.
- Capacity: Capacity remains an important constraint for security teams. Many organizations lack the capacity to deal with runtime alerts, minimizing the primary value proposition of an agent-based security tool. We can see capacity constraints in today’s vulnerability management programs, where security teams fix roughly 10 percent of vulnerabilities detected each month. Numerous examples also exist, like the infamous Target breach of 2013. In this case, runtime tools generated multiple alerts of malware and lateral movement prior to the massive incident, yet security teams didn’t have the bandwidth to act on the intelligence.
- Performance impact: Agentless security solutions don’t increase the load placed on host infrastructure, so it doesn’t negatively affect workload performance. Meanwhile, agent-based security tools consume resources when they run, which may negatively impact performance based on demand.
- Return on investment: Agentless security solutions tend to generate a higher ROI than agent-based solutions. Agentless tools don’t increase infrastructure spending, eliminate the need for installing or maintaining agents, accelerate deployments, and increase developer and DevOps productivity.
Recap: agentless vs. agent-based security
To summarize, agent-based security works best for mission-critical workloads that demand runtime visibility and protection. Meanwhile, agentless security is ideal for coverage of cloud environments, where new workloads constantly spin up and turn down. Here, agentless security solutions can leverage cloud APIs to implement much of the functionality that has traditionally been provided by agents.
Both agentless and agent-based security tools provide advantages and disadvantages. When it comes to cloud-native computing, best practice is to harness both technologies in ways that maximize their benefits while minimizing their limitations. This approach calls for fully deploying an agentless security solution across your entire estate, ensuring complete coverage and comprehensive detection without any blindspots. It also necessitates using a lightweight agent-based security solution to cover a small number of critical assets, typically no more than 5%. Doing so ensures added protection for your most sensitive assets, while avoiding the diminishing returns that come with a large agent-based security deployment. Together, this combination of agentless and agent-based security results in the best and most sustainable security outcomes.
Agentless-first security: Orca’s revolutionary approach to cloud-native protection
In 2019, Orca was the first to market with its agentless cloud security solution, powered by our patented SideScanning™ Technology. SideScanning offers a true alternative to agent-based technology and continues to address every cloud security use case. By combining workload runtime data with metadata gathered from cloud service provider APIs, Orca is able to visualize your entire cloud estate to put risk and threats in the proper context for your unique environment.
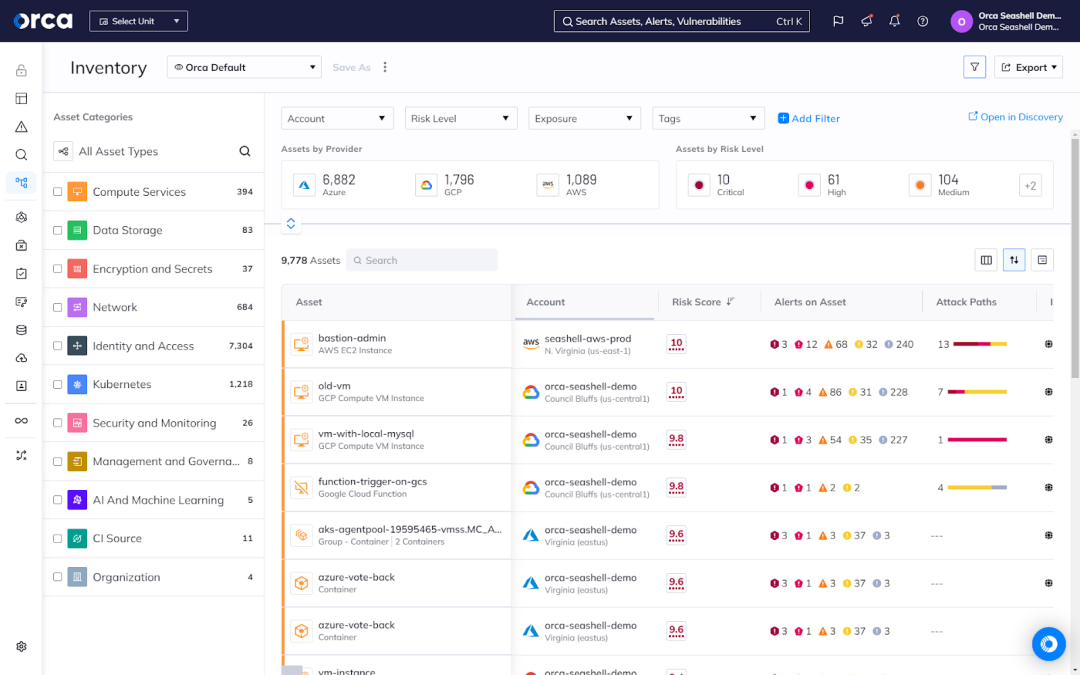
The Orca Platform provides the ability to detect every type of risk and the capability to analyze risk holistically in relation to your environment. This enables the Platform to effectively prioritize risks and surface hidden attack paths endangering high-value assets, enabling you to focus on the 1% of risks that matter most.
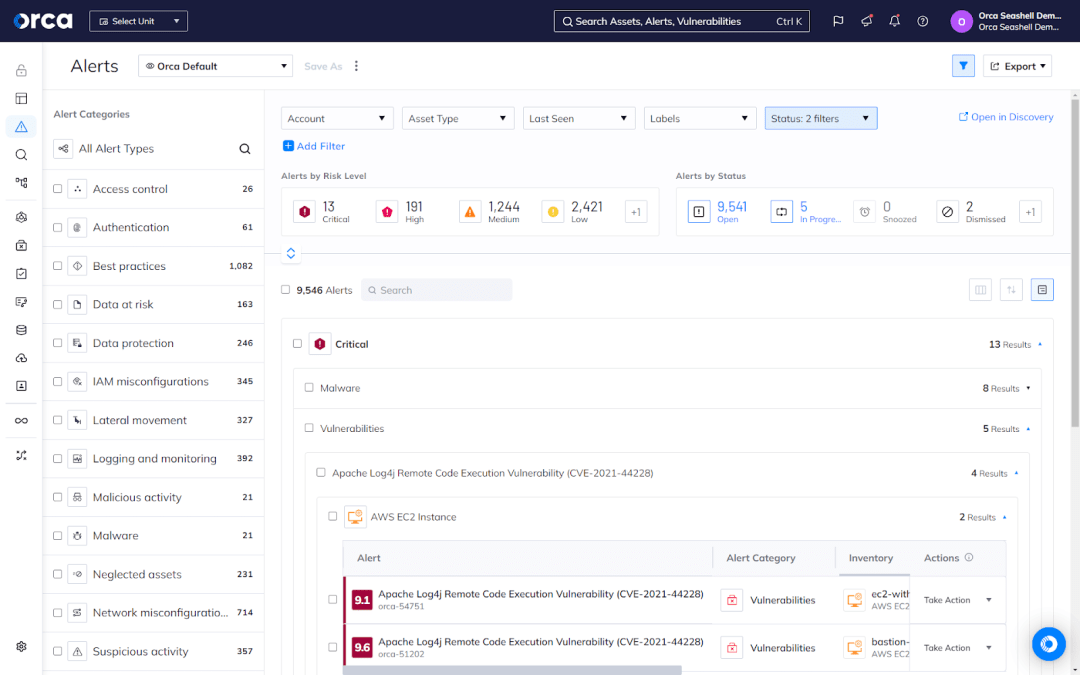
Orca’s agentless-first security approach doesn’t mean the complete absence of runtime protection. For example, some mission-critical systems may demand runtime visibility and protection. Agentless-first security supports runtime deployments for targeted, focused, and limited use cases. But beyond this, any runtime approach provides diminishing returns.
Agentless-first calls for leading with technology designed to deliver complete coverage, comprehensive detection, contextual awareness, and consumable insights across the cloud estate. More specifically, an agentless-first approach entails:
- Making sure you have full coverage of your environment out-of-the-box.
- Ensuring you can detect cloud security risk and evaluate it holistically, enabling you to understand the relationship between risks and resources, including any toxic combinations that endanger high-value assets.
- Prioritizing risks dynamically and continually based on multiple factors that account for their severity, exploitability, and context within your environment.
- Enabling fast, easy, and efficient remediation that fits your organization’s unique processes, including across functions.
- Supporting GRC teams in evaluating compliance for continuous authority to operate.
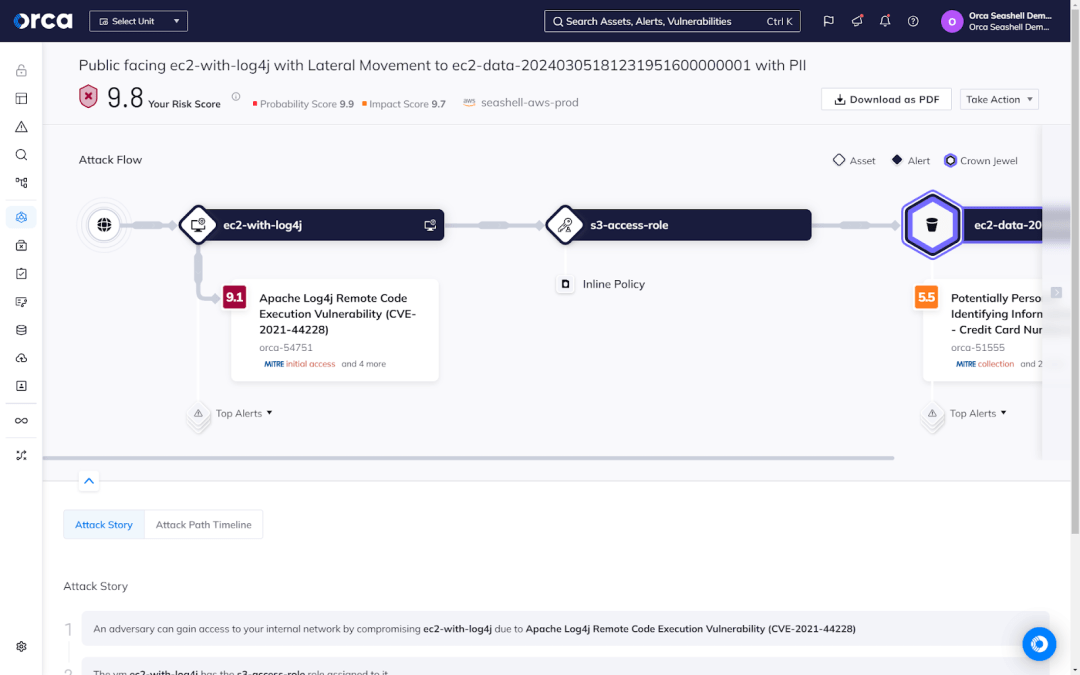
Orca’s agentless-first approach can make your cloud security practical, operational, sustainable, and effective. It goes far beyond building the foundation for a secure cloud while offering the springboard for approaching runtime protection more intentionally, strategically, and cost-effectively.
Here are just a few use cases where runtime solutions can offer value in Orca’s agentless-first security model:
- Areas where risk tolerance is low: Mission-critical and public-facing applications may warrant runtime protection.
- Regulatory and compliance cases that demand runtime protection: Some compliance requirements may mandate runtime visibility.
- Risky assets: Certain workloads stand a higher risk of compromise and necessitate real-time visibility, protection, and incident response.
Ready to see our agentless-first cloud security platform in action? Sign up for a personalized demo and discover how the Orca Cloud Security Platform can help you gain immediate coverage, comprehensive risk detection, and intelligent risk prioritization across your cloud estate.
Conclusion
As the need for cloud security solutions continues to grow, organizations encounter questions over agentless vs. agent-based security. Both forms of technology can provide value and impact security outcomes positively. Yet the opposite can also occur depending on implementation. Maximizing your security and ROI depends on knowing where and how to leverage each technology and intentionally committing to that strategy.
FAQs
What is agentless architecture?
Agentless architecture refers to the network design of cloud security technology. Agentless architectures provide visibility into and monitoring of cloud environments without the need to install agents. Agentless architectures primarily rely on API connections and other non-invasive methods. This design is best suited for cloud-native environments due to its flexibility, scalability, and ease of deployment.
What is agent vs. agentless monitoring?
Agent vs. agentless monitoring refers to two approaches to the monitoring of cloud environments or the resources contained in them. Agent-based monitoring covers individual workloads and occurs on the data plane, where an agent must be installed on the workload in order to monitor it. Agentless monitoring covers cloud infrastructure and all workloads in a cloud environment, covering both the data plane and cloud plane. Agent-based monitoring happens in real-time because it’s installed on each workload. Meanwhile, agentless occurs in near-real-time because it isn’t installed but connected via API. Additionally, though agentless technology covers multiple workloads, it does provide visibility into each workload, though not at the same level of granularity as an agent-based tool.
What is agentless scanning?
Agentless scanning refers to the use of agentless security technology to scan cloud environments for potential risks and compliance issues. Leveraging API connections, agentless scanning occurs at both the data plane and cloud plane of cloud environments, ensuring full coverage as opposed to agent-based scans, which cover each workload with an installed agent.
What is agent-based vulnerability scanning?
Agent-based vulnerability scanning refers to the use of agent-based security solutions to scan for vulnerabilities on covered endpoints or workloads. This process involves uncovering security weaknesses, assessing their criticality, and generating alerts for detected issues. In a cloud environment, agent-based vulnerability scanners lack awareness of the broader cloud environment and therefore can’t effectively determine criticality or prioritize alerts.
What is agentless vulnerability scanning?
Agentless vulnerability scanning refers to the use of agentless security solutions to scan for vulnerabilities in cloud environments. This process involves surfacing hidden risks, assessing their criticality using multiple factors, and prioritizing and generating alerts for detected issues.
What is an agent-based deployment?
An agent-based deployment refers to the process of installing, setting up, and configuring an agent-based security solution, often in a cloud environment. Agent-based deployments require an agent to be installed on each endpoint, or workload in a cloud context, that needs monitoring. This approach presents significant challenges in cloud environments, because workloads are ephemeral, dynamic, and highly distributed.
What is an agentless deployment?
An agentless deployment refers to the process of operationalizing and configuring an agentless security solution in a cloud environment. Agentless deployments don’t require the use of agents to provide continuous monitoring and protection. Because agentless security tools use an API connection, deployment can take minutes. The ease and sustainability of agentless deployments helps explain the popularity of its use in cloud-native environments.
What are agent-based vulnerability scanners?
Agent-based vulnerability scanners detect and analyze security weaknesses. While they provide in-depth scanning, they require an agent installed on each workload, need ongoing maintenance, and limit visibility to assets that are known, accessible, and capable of hosting an agent. Agent-based vulnerability scanners provide the most value for limited deployments covering high-value assets that warrant deep scanning.
What is agent-based cloud workload protection?
Agent-based cloud workload protection (CWP) provides continuous monitoring and protection of workloads in runtime. These solutions require the installation of an agent on each virtual machine or compute instance to function, leading to limitations in a cloud environment due to its ephemeral and dynamic nature. These solutions also call for ongoing maintenance, as agents must be updated to support different operating systems and versions.
Table of contents
- What is agentless vs. agent-based security?
- What is agentless security?
- What is agent-based security?
- Advantages of agent-based security
- Disadvantages of agent-based security
- Advantages of agentless security
- Disadvantages of agentless security
- What are the key considerations of agentless vs. agent-based security?
- Recap: agentless vs. agent-based security
- Agentless-first security: Orca’s revolutionary approach to cloud-native protection
- Conclusion
- FAQs






