API access from suspicious source IP was detected
Informational (4)
GDPR, HITRUST, NIST 800-53
About APIs
An application programming interface (API) is a standard interface that enables two or more computers or applications to communicate. APIs enable companies to share their internal data with trusted third parties or partners. The premise of an API is to mask how the system works internally. This simplifies the way other users or applications interact with a system and secures system internals.
APIs establish a contract that must be followed by all users. Contract violation results in denial of access. For example, an API contract identifies input parameters a client must provide for data retrieval and how the output is to be formatted.
APIs are a staple of cloud architectures. They enable applications to seamlessly communicate with other applications and cloud services; e.g., you can create an AWS Lambda function using the CreateFunction API.
Since APIs can often be publicly invoked, it’s important to track who is invoking them. An API call detected from a suspicious IP address should be rejected and an alert immediately raised. Most cloud platforms provide ways to do this; Azure has its Activity Log, AWS provides CloudTrail, while Google Cloud provides Cloud Audit Logs.
Cloud Risk Description
API access from suspicious source IP addresses is a serious concern. Suspicion can be aroused based on (among other things): location/country of origin, high volume of login attempts from a particular IP, or a high volume of error responses to requests from the same IP.
Suspicious access should be flagged and prevented going forward. If a cybercriminal manages to gain unauthorized API access, they can retrieve sensitive data and potentially cause downtime.
How Orca Can Help
With Orca’s cloud detection and response capabilities, organizations can detect, investigate, and respond to malicious activity. Orca alerts on possible malicious intent versus normal behavior, automatically prioritizing events that endanger the company’s most critical assets.
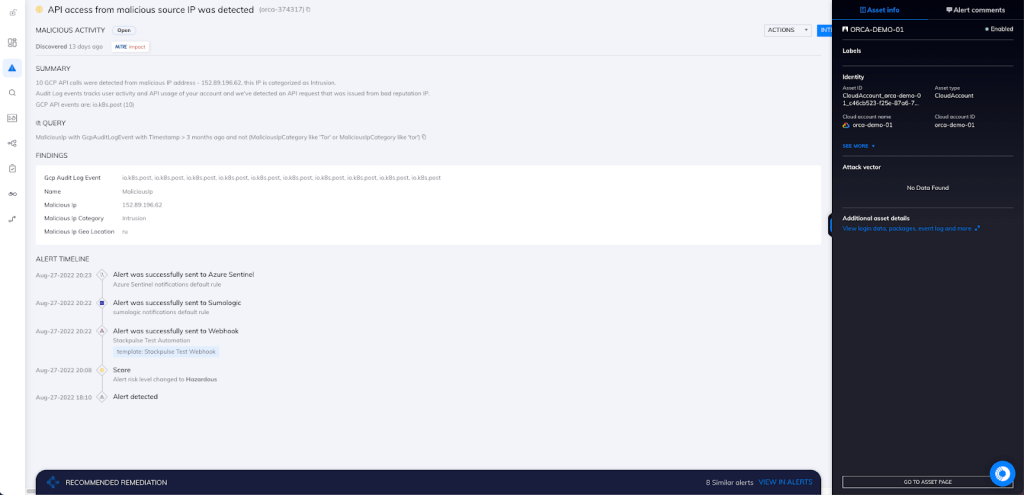
In this example, Orca has detected 12 GCP API calls from a malicious IP address, as seen in the screenshot above.
Recommended Mitigation Strategies
-
Set up a suspicious IP address throttling mechanism to protect against flooding and brute force attacks.
-
Use CAPTCHAs and firewalls to protect against bots. Sudden and exponential spikes in page views, bounce rates, and traffic from unknown countries/locations are a few indicators of bot/suspicious traffic.
-
Allow access from only whitelisted APIs when exposing internal APIs to partners.
-
Control access to data and services by assigning API/session tokens to trusted entities.
-
Identify and resolve vulnerabilities in your application, web servers, and any other components.
Useful Links
- How to Build an Effective API Security Strategy – Gartner (subscription required): https://www.gartner.com/en/documents/3834704
- What are APIs and how do they work? https://blogs.mulesoft.com/learn-apis/api-led-connectivity/what-are-apis-how-do-apis-work/
- OWASP API Security Project: https://owasp.org/www-project-api-security/
- 10 API Security Best Practices: https://nordicapis.com/10-api-security-best-practices/
- Suspicious API calls mostly used in malware: https://www.researchgate.net/figure/Suspicious-API-calls_fig2_333335327
- Top 10 API Security Risks: https://www.axway.com/en/products/api-management/manage-apis/top-10-security-risks
- Azure Activity log: https://docs.microsoft.com/en-us/azure/azure-monitor/essentials/activity-log
- AWS CloudTrail: https://aws.amazon.com/cloudtrail/
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
