The fast-moving evolution of cloud-native environments has increased the complexity of the security landscape, leaving security teams struggling to fix vulnerabilities and misconfigurations. The challenge, which is becoming more acute every day, is finding the right counterpart to handle the issue.
Resolving a cloud vulnerability in a traditional environment is fairly simple—someone patches the server and, if necessary, reboots it. The problem can be fixed where it lives.
But in today’s cloud-native environments, security teams must go to the source to fix the issue and then redeploy it, which is a painstaking quest requiring significant collaboration between security and development teams. When a security team identifies a risk, they must turn to the development team to find its source information—tracking down the original developer or team that created the artifact, as well as when it was scanned, when it was deployed and whether it was changed or modified since.
It’s an inefficient, time-consuming process that also leaves the organization exposed for an unnecessary length of time. For example, I once worked with a large organization that had found all their Log4J vulnerabilities within hours, but it still took three weeks to identify the correct individual to make the fixes—and this isn’t an extreme example.
The industry needs to rethink how it goes about this process, which right now is missing two important elements:
- The ability to share pertinent data across the organization, giving proper visibility into the cloud environment.
- A single person or team to facilitate the security/developer process, reducing the ping-pong effect between teams to more quickly and efficiently resolve cloud security/code origin issues.
Vulnerabilities multiply in the cloud
Taking advantage of the scale of the cloud requires tools that automate the provisioning of cloud infrastructure, using artifacts such as Dockerfiles to describe the desired state.
Infrastructure as Code (IaC) templates, for instance, allow DevSecOps practitioners and security teams to use a provider’s pre-configurations and images to build their own assets, in a similar way to how developers use external libraries and modules when coding.
It saves a lot of time and effort, but it can also lead to multiplying security issues such as misconfigurations. An unprotected bucket or misconfigured load balancer that was built using a misconfigured template is at risk of being exploited as an initial access point. Because IaC templates are used repeatedly, one small mistake can propagate hundreds of unsecured assets susceptible to a breach.
When you have a vulnerability or misconfiguration, patching a container or changing the configuration of live infrastructure doesn’t solve the issue because the container or infrastructure can be overwritten at any time, effectively reintroducing the security risk. IaC templates also can experience drift, which can lead to many different configurations.
So, teams have to fix the source of the issue—namely, the container image or IaC template where the risk originated—and then redeploy it. Someone has to be able to correlate the observed problem with the originating code and its owner. It makes remediation a lot more complicated and difficult than with traditional systems, which is why organizations need a new approach in the cloud era.
Shared information is key
Right now, security teams and developers don’t have visibility into each other’s side of the enterprise. This is the main issue. For example, a security practitioner can see an alert on a container but doesn’t know who caused it or which line of code is involved, nor do they know the reason for the issue or the problems it will cause. For that, security teams have to go to development teams, which then have to do some digging on their own. This process is recursive many times, when the team who is responsible for the service sometimes finds out that the issue lies in a subcomponent provided by another team.
At Orca, we have designed a better approach to securing cloud-native applications that alleviates these challenges. It begins with giving security teams a centralized view of cloud assets and risks with clear visibility into their code origins. Teams can see a full inventory of resources and risks originating from development, all prioritized by criticality and filterable using a variety of criteria. For example, users can easily filter results to not only see code repositories with deployed assets, but only assets exposed to the Internet or containing sensitive data. The result brings the connection between cloud and development into focus.
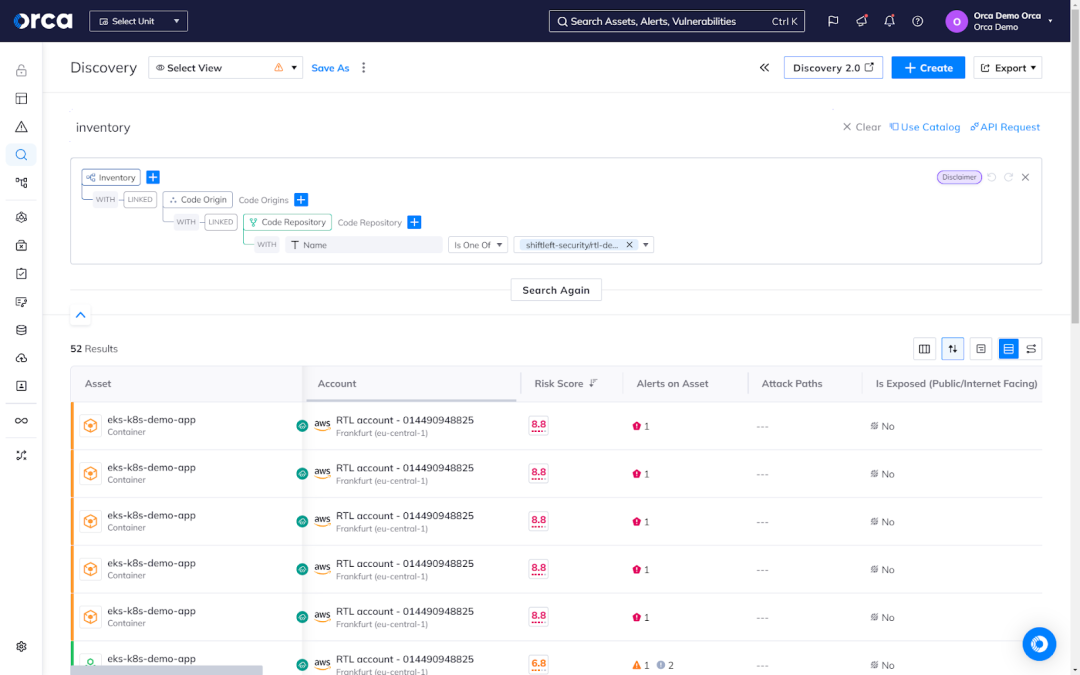
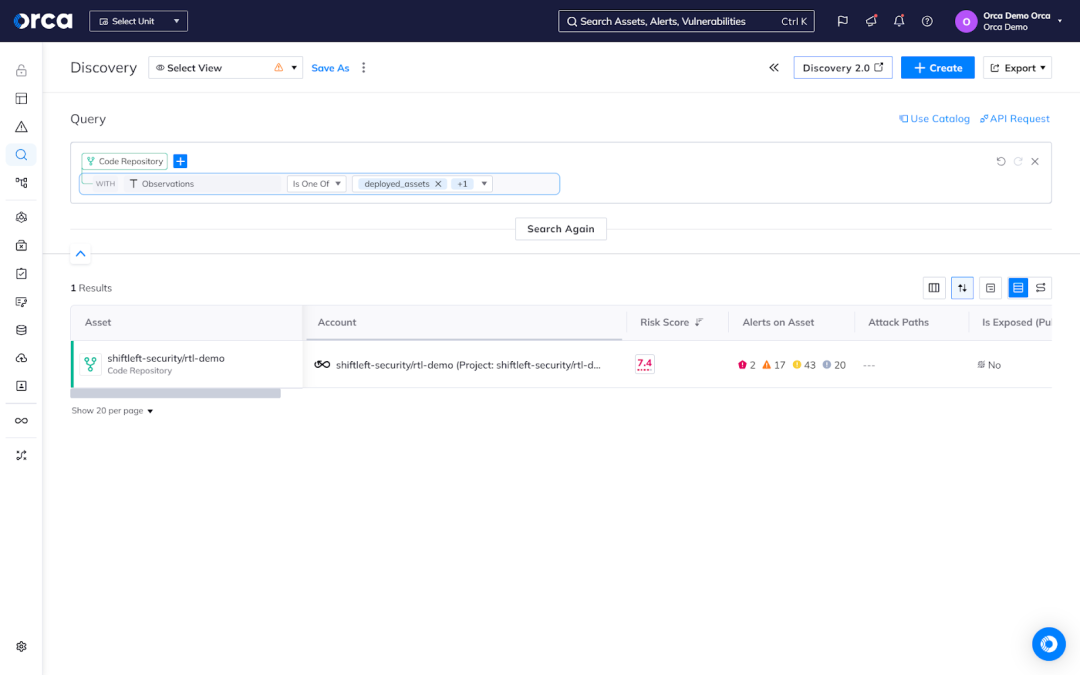
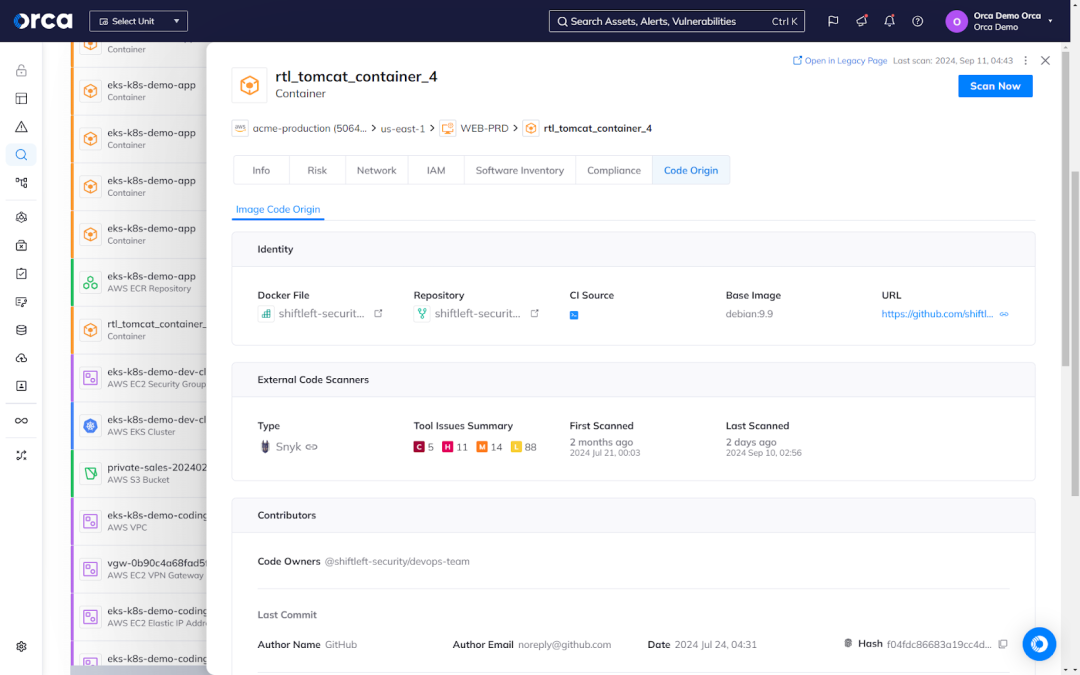
From this centralized view, security teams can quickly dive deeper for full contextual awareness. Clicking a container allows teams to view its origin Dockerfile, code repository, base image, code owners, and risk findings from external code scanners like Snyk. They can also see a prioritized list of risks associated with the asset, and dig deeper into a critical alert. From there, they can trace a vulnerability or misconfiguration back to its source—whether a container image or an IaC template.
This can greatly increase the Mean Time to Resolution (MTTR) by, for example, identifying the source code repository and the Dockerfiles responsible for the vulnerability, even down to the exact line of code that needs to be fixed, allowing the right developer to remediate it quickly.
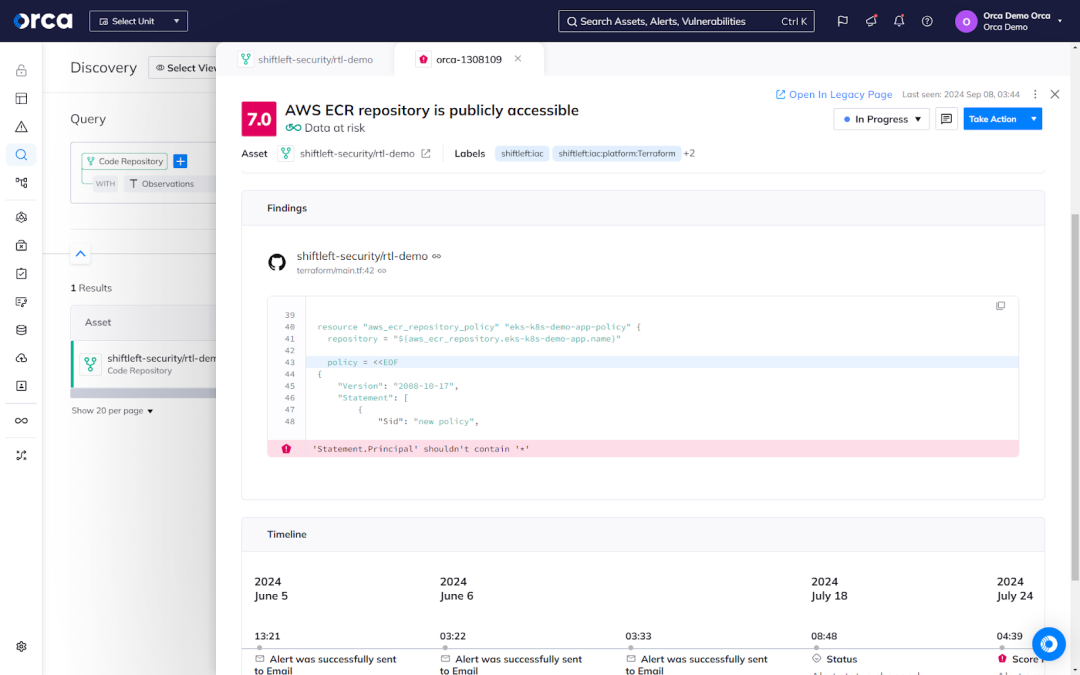
Orca also simplifies the remediation process itself. Orca’s two-way integrations with the ticketing systems Jira and ServiceNow enable security teams to create a ticket directly from an Orca alert and assign it to the appropriate developer. Developers receive the notification in the ticketing system and can resolve the issue using their preferred tools and workflows. Meanwhile, security teams can monitor the ticket’s status in the Orca Platform, which automatically verifies an issue is resolved each time developers close a ticket.
The result is quicker and more efficient remediation, avoiding the problems that exist in current methods, where security teams waste time tracking down the source, often across siloed systems.
With these capabilities, security issues that originated from a cloud-native artifact can be resolved in a matter of hours, as opposed to days or weeks. Needless to say, this can lead to a significant enhancement in cloud security posture.
A unified solution that connects security and development
The Orca Cloud Security Platform takes a holistic approach to managing cloud-native environments. A true CNAPP, the Orca Platform provides full visibility across the cloud estate and enables a whole lifecycle approach to application security.
The platform combines the functionality of multiple point solutions into a single solution for securing cloud-native applications. This includes Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), Cloud Infrastructure Entitlement Management (CIEM), Data Security Posture Management, API Security, Vulnerability Management, Shift Left Security, and more.
Orca’s Shift Left Security further enhances collaboration between security and development teams, ensuring both can work together to prevent risks from reaching production environments. For example, security teams can create, tailor, and enforce security policies that can block risky builds or warn developers of problematic pull requests. Available for source code vulnerabilities, secrets detection, IaC templates, container images, and source code management (SCM) platforms, these policies act as guardrails, enabling developers to address issues early in the software development lifecycle (SDLC) and maintain peak productivity.
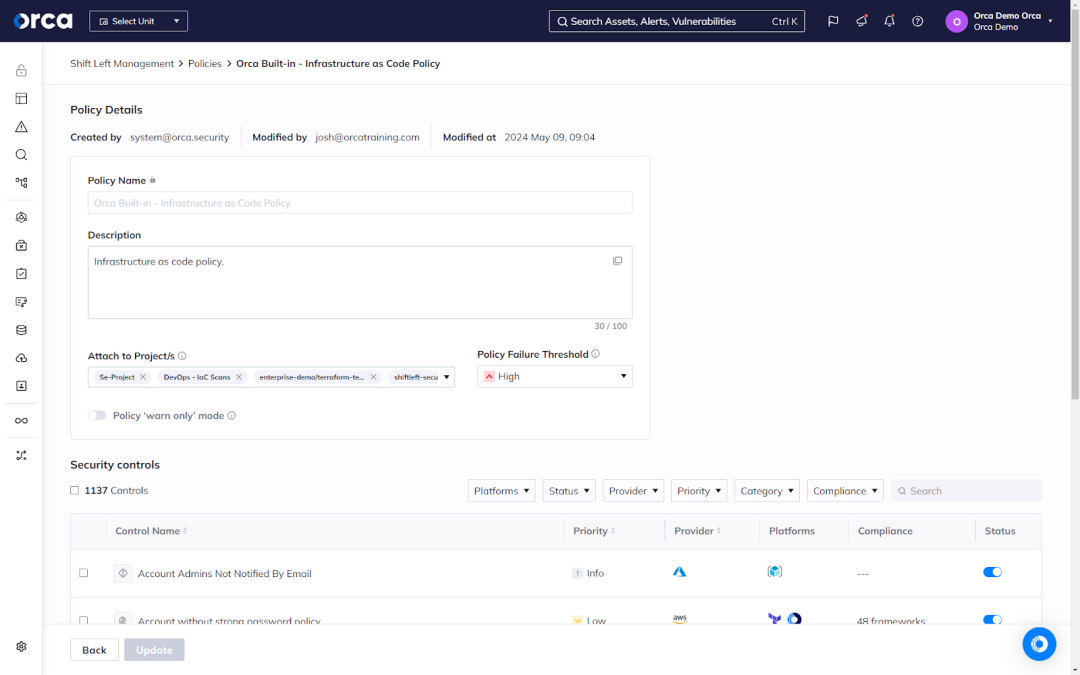
The Orca Platform helps both security teams and developers not just by benefiting security teams, but also providing major improvements for developers. It creates a new system where everyone benefits because it helps ensure secure operations while supporting faster application development.
About the Orca Platform
The Orca Cloud Security Platform identifies, prioritizes, and remediates security risks and compliance issues across the multi-cloud environments of AWS, Azure, Google Cloud, Kubernetes, Oracle Cloud, and Alibaba Cloud. A natively built CNAPP, Orca offers an agentless-first approach powered by its patented SideScanning™ Technology, which provides full coverage and comprehensive risk detection of your cloud estate.
In addition to offering an advanced Shift Left Security solution, the Orca Platform features powerful cloud-to-dev capabilities that trace runtime risks directly to their source.
Learn More
Interested in seeing Orca’s Cloud-to-Dev solution in action? Book a personalized 1:1 demo with one of our experts and we’ll show you how Orca can fortify your cloud security and improve cross-functional collaboration.