As cloud-native development accelerates, security teams are under increasing pressure to keep up. According to the Enterprise Strategy Group’s Modernizing Application Security to Scale for Cloud-Native Development report, security teams are most challenged by two key issues: prioritizing remediation and gaining visibility and control over development processes. This gap helps explain why both vulnerabilities and exploitation rates continue to rise, as highlighted in the 2025 State of Cloud Security Report.
The problem isn’t new, as cloud and application security have long operated in silos. Most security teams cannot see how issues in development impact production or what security measures were applied to cloud resources before deployment. This disconnect inhibits their ability to prioritize and remediate risks effectively and collaborate most productively across the pre- and post-deployment phases of the application pipeline.
Orca is addressing this challenge with powerful enhancements to its Cloud-to-Dev capabilities, delivering deep, end-to-end visibility from development to cloud. Security teams can now trace risks and vulnerabilities across the entire software lifecycle—from the Dockerfile definition, through the moment the container image is built and scanned in the CI pipeline, and all the way to running containers in production.
And we don’t stop there. Orca now also enhances the risk prioritization of code issues—such as IaC misconfigurations—by factoring in their actual cloud footprint. This allows teams to focus on the issues that pose the greatest real-world risk, not just theoretical ones.
By tying together development context with real-time cloud data, Orca empowers teams to prioritize and remediate risks based on actual exposure and impact.
What is Cloud-to-Dev?
Cloud-to-Dev is Orca’s approach to unifying security across development and cloud environments. It seamlessly traces production assets back to their originating code artifacts and owners, enabling fast and efficient investigation, reducing mean time to remediation (MTTR), and supporting a unified approach to cloud-native security.
Unlike other solutions that depend on manual tagging, custom scripts, or changes to developer workflows, Orca handles everything automatically. This ensures that Cloud-to-Dev delivers real, scalable value in production, not just scripted demos that don’t reflect real-world complexity.
The latest release further strengthens our Cloud-to-Dev capabilities, enhancing container security with extended visibility as well as improving AppSec risk prioritization with cloud contextual awareness.
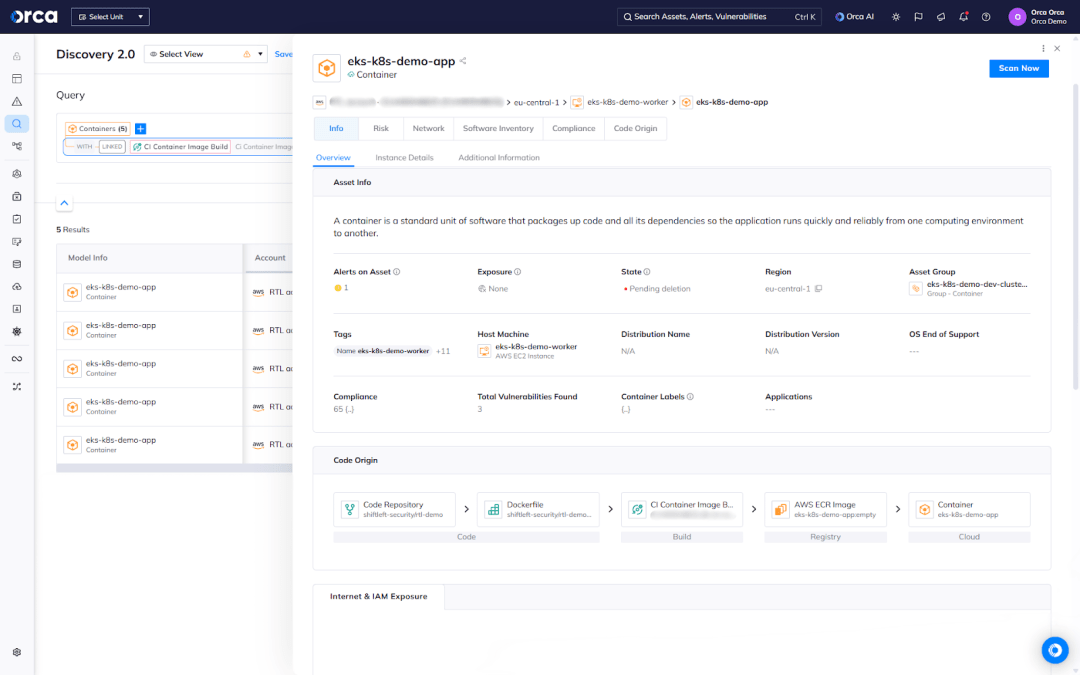
Connecting Containers to their CI Scans
Container environments face risks at every stage of the software supply chain, from insecure images to misconfigured deployments. Even a single exploitable vulnerability in a container image can jeopardize significant portions of your cloud infrastructure.
Security teams require clear visibility into whether running containers originated from images that were scanned, and whether these scans passed or failed. Without this visibility, accurately assessing exposure and quickly remediating risks becomes challenging.
Orca now makes this visibility seamless. With this new update, security teams can view whether a container was scanned in CI, its scan status (pass or fail), as well as any identified issues, directly from the container asset.
Additionally, users can access the scan log and review issues found in the CI scan, as well as view the CI build that produced the image and the platform that ran it. The enhancement gives security teams critical context and traceability, as well as the ability to investigate and fix issues at their source.
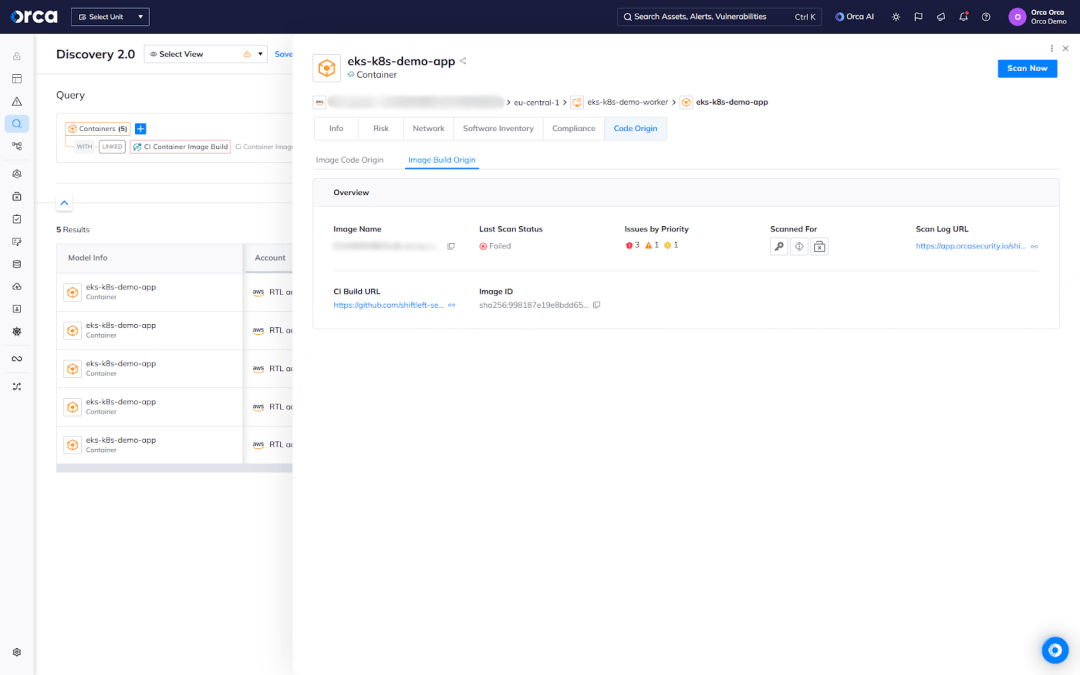
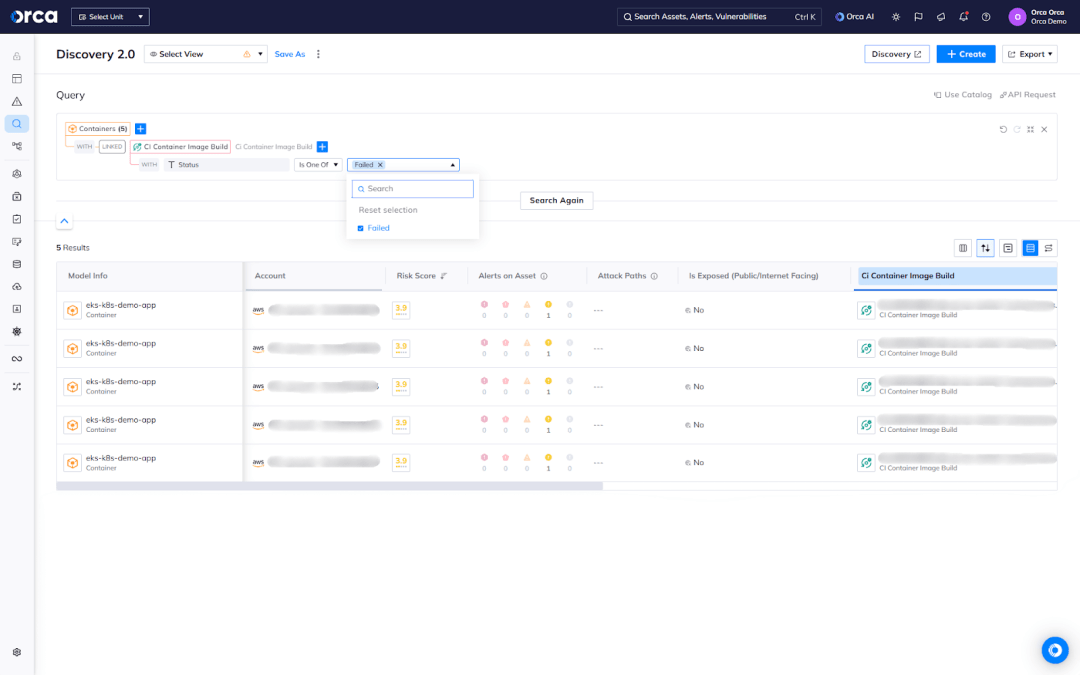
In addition to providing this correlation for each container and container image, Orca also enables teams to search, filter, group, and identify all running containers linked to unscanned images or images that failed CI scans. This makes it easy to spot coverage gaps instantly and speeds up investigation and remediation.
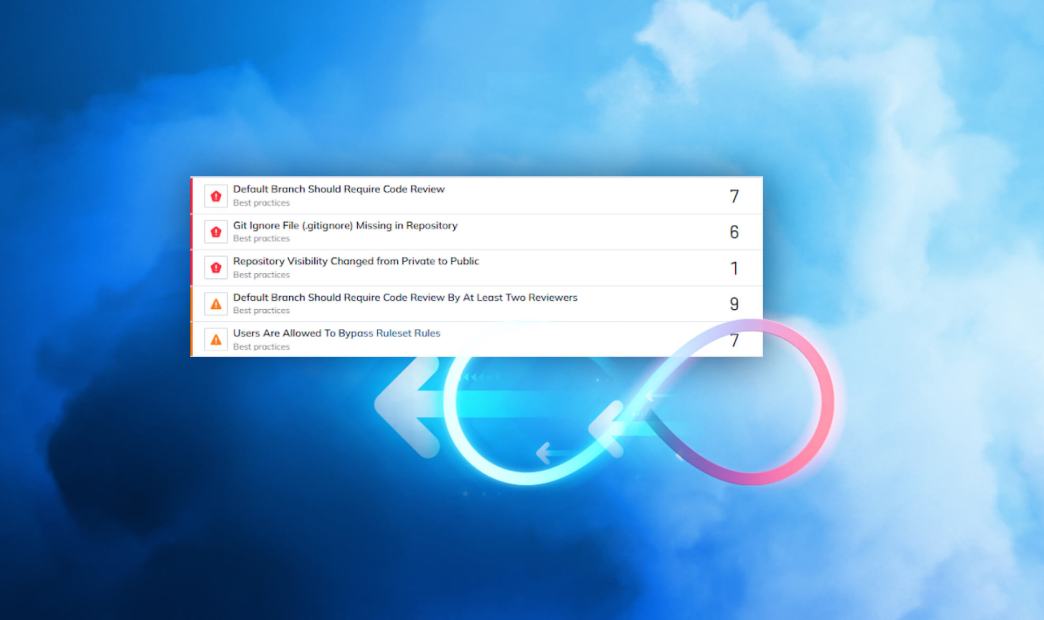
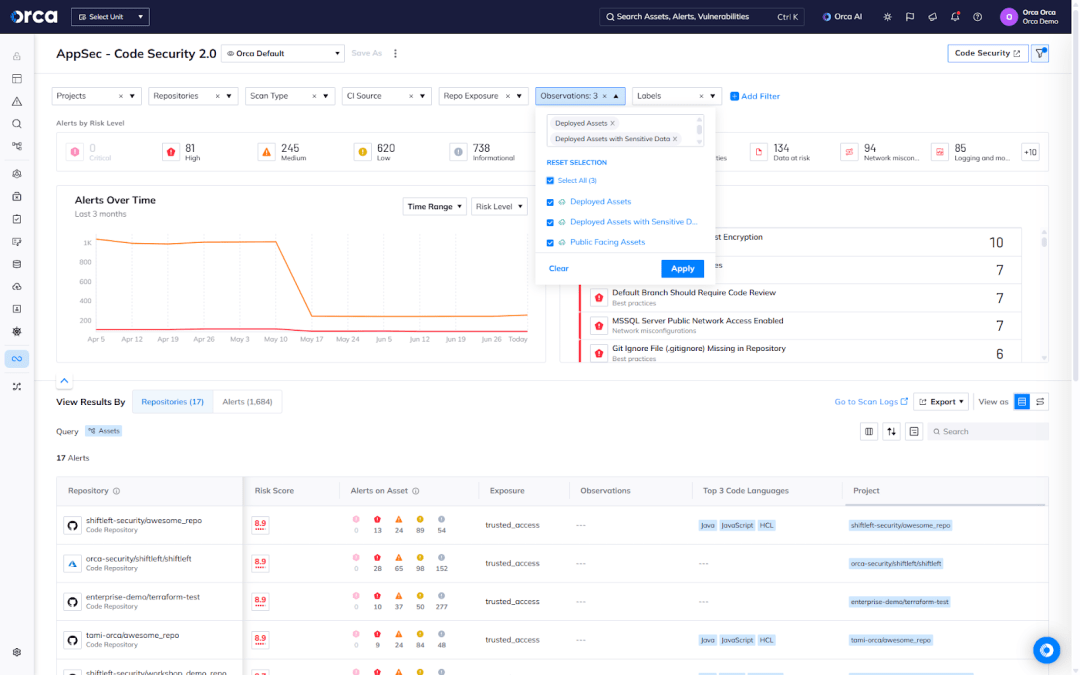
Prioritizing AppSec Alerts with Cloud Context
Security teams can’t fix everything. In fact, research from the Cyentia Institute shows that most teams can only remediate about 10% of the vulnerabilities they detect each month. This explains why risk prioritization is paramount.
Application Security tools often detect issues in isolation without understanding whether a misconfiguration or vulnerability actually impacts a production resource. As a result, teams may end up prioritizing a flaw in an undeployed IaC artifact over a similar issue propagating in runtime and directly linked to cloud infrastructure. While the former may deserve attention, the latter presents a more immediate risk to the business.
Orca’s Cloud-to-Dev capabilities now enable security teams to differentiate between the two by bringing production context to the dynamic risk scoring of AppSec alerts.
When Orca detects an IaC misconfiguration or vulnerability, it automatically checks whether the underlying artifact is linked to live infrastructure and uses rich cloud context to assess criticality. This includes factoring in asset exposure, the presence of sensitive data, exploitable vulnerabilities, and whether the asset is part of a critical attack path. By combining these insights, Orca ensures teams can accurately prioritize remediation efforts, reduce time to resolution, minimize alert fatigue, and avoid missing high-impact risks.
Beyond IaC issues, this capability also extends to SCM Posture Management (SCM-PM) alerts, enabling teams to address the misconfigurations in SCM accounts, or repositories linked to cloud resources.
Additionally, the feature also enables teams to immediately inventory all the code repositories linked to cloud assets, giving them contextual awareness that spans the entire application lifecycle.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Cloud Security Platform and its AppSec capabilities? Schedule a personalized 1:1 demo.