Controller creating pods with privileged Docker
Informational (4)
Non-platform specific
EKS CIS, GDPR, GKE CIS, K8s CIS, NIST 800-53
About Controllers and Pod Security Policies
In a Kubernetes cluster, controllers are responsible for keeping the current state as close as possible to the desired state. The desired state is the original formation of the cluster defined via configuration files. For example, if an instance goes down, it’s the controller’s job to shift all the pods to another instance. Doing so will help maintain the desired state of the cluster.
Since a controller can create new pods in real-time based on multiple triggers, it’s important to have a cluster-level security policy in place. Kubernetes allows you to enforce such a policy via the PodSecurityPolicy objects.
A pod security policy defines the conditions required for a pod to run inside a cluster. Using PodSecurityPolicy attributes, an administrator can enforce certain security controls, such as which OS-level capabilities are allowed to a container, which kernel parameters can be configured at runtime and whether a container can run in privileged mode.
Cloud Risk Description
A PodSecurityPolicy object was detected with the privileged attribute set to true, allowing Kubernetes controllers to run containers in privileged mode. Privileged containers get root capabilities to all the devices on the host system. If a malicious actor gains access to the container, they can use it to compromise the system.
How Orca Helps
With support for CIS Kubernetes benchmarks, Orca will give you details of passed and failed control checks with extensive details around failed checks for the cloud infrastructure plane and Kubernetes Pods.
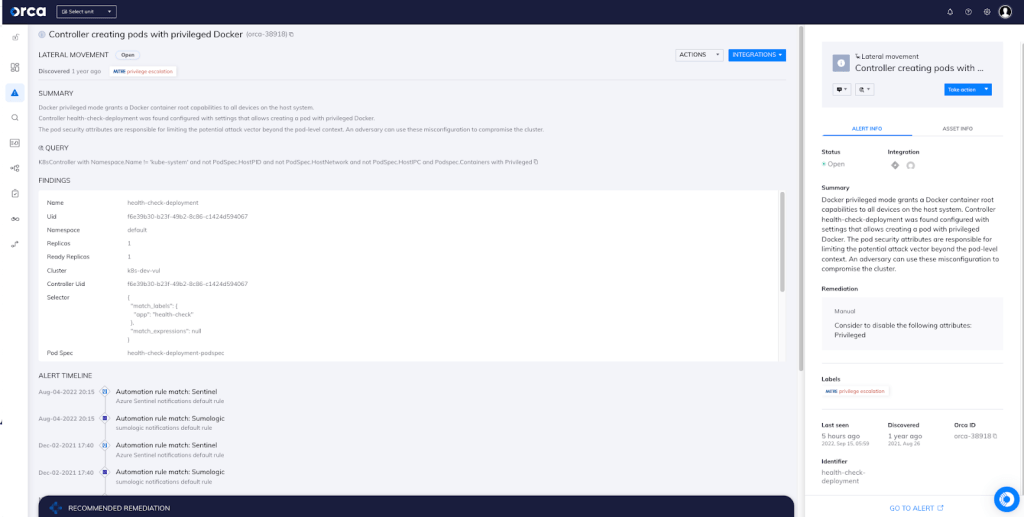
With Orca’s agentless design, you also gain two important advantages: complete 100% visibility of both the Kubernetes control plane nodes, the Pods, and the containers within them. Orca can even scan containers for vulnerabilities in pods that are either paused or stopped. In this specific case (as seen in the above screenshot), Orca has detected the PodSecurityPolicy object with unsafe privileges.
Recommended Mitigation Strategies
-
Disable the privileged attribute in the pod security policy.
-
Use encryption to secure Kubernetes secrets at rest and in transit.
-
Use a logging framework to monitor and analyze Kubernetes and OS logs.
-
Use RBAC authorization to limit access to the kube-apiserver.
-
Apply the principle of least privilege when creating a pod security policy.
Useful Links
- Kubernetes cluster architecture: https://kubernetes.io/docs/concepts/architecture/
- Pods: https://kubernetes.io/docs/concepts/workloads/pods/
- Configuring a security context for a pod: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/
- Pod security policies: https://kubernetes.io/docs/concepts/policy/pod-security-policy/
- Kubernetes and the desired state principle: https://yannalbou.medium.com/kubernetes-desired-state-4c5c4e873743
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
