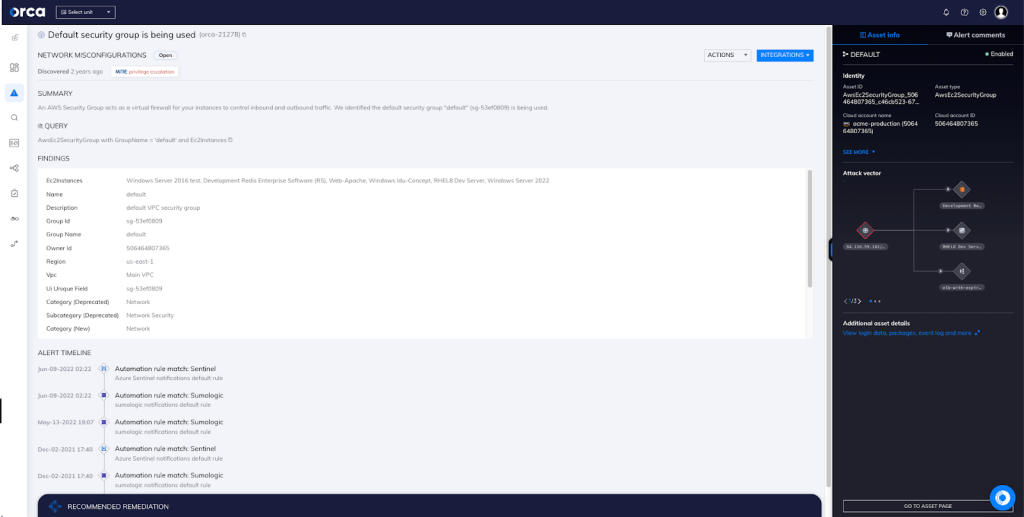
Default security group is being used
Informational (4)
Orca Best Practices
About AWS Security Groups
An AWS security group is a set of rules that define which traffic is allowed in and out of \cloud resource, such as EC2 instances. Inbound rules apply to incoming traffic, while outbound rules determine the flow of outgoing traffic.
Rules enable you to specify the following:
- Protocols – Which protocols (e.g., TCP/UDP/ICMP) are allowed?
- Port range – Which system ports should be open for traffic?
- IPs – Which source and destination IP addresses or IP group addresses are whitelisted?
You can create a security group using the AWS EC2 console. It’s recommended that instances having different roles belong to a purposeful, corresponding security group. For example, if one EC2 instance is running a webserver used by your clients and another runs an internal SQL database, each should have different inbound and outbound rules.
A security group can be applied to an instance upon its being launched. When launching an instance, you’re given the choice between a default security group or to choose from a custom group. When choosing the default security group, it has excessive privileges, including an outbound rule that allows all outbound traffic. You can alter the group as desired and have it apply to all new instances spawned without their own custom security group.
Cloud Risk Description
Applying the default security group to AWS EC2 instances could not only violate the principle of least privilege, it could put at serious risk for unauthorized outbound traffic. Disparate instances might have unique use cases; that is, one might be running an internal, security-critical application, another a customer-facing website. Again, it’s recommended that you configure customized security groups for EC2 instances having different roles.
If the default security group allows overly permissive access, and many instances are launched using it, this can significantly increase the chances of your organization getting breached.
How Orca Can Help
Orca offers extensive network misconfiguration detection across all of your cloud accounts. In this particular risk, as seen in the screenshot above, Orca identified the default security group being used, allowing overly permissive access and raising security risk levels.
Recommended Mitigation Strategies
-
Create unique, customized security groups for instances having different roles.
-
Audit for instances having default security groups and immediately change their security group.
-
Adhere to the principle of least privilege while creating rules for custom security groups.
-
To reduce your attack surface, ensure that your security groups don’t allow a large range of ports to be open.
-
Identify and delete any unused security groups.
-
Change the default security group to have non-permissive rules. This will ensure that even if an instance is mistakenly launched with the default security group, it doesn’t violate the principle of least privilege.
Useful Links
- Amazon EC2 security groups for Linux instances: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-security-groups.html
- Default and custom security groups: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/default-custom-security-groups.html
- Security group rules: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-rules.html
- Security group rules for different use cases: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-rules-reference.html
- Control traffic to resources using security groups: https://docs.aws.amazon.com/vpc/latest/userguide/VPC_SecurityGroups.html
- Create a security group: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/working-with-security-groups.html#creating-security-group
- Security group connection tracking: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-connection-tracking.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
