Publicly disclosed computer vulnerabilities are compiled into a list called Common Vulnerabilities and Exposures (CVE). To understand the severity of those vulnerabilities they have a scoring system applied. The most commonly known of these systems would be Common Vulnerability Scoring System (CVSS) which is currently on version 4.
All scoring systems make trade offs and CVSS is no different. CVSS focuses on the vulnerability itself to determine its severity. It doesn’t take into account the likelihood of the vulnerability being exploited. This means that all similarly scored CVEs must be treated as equal regardless of the actual risk in the real world.
This blog provides further background on the EPSS system, and why, in addition to CVSS scores, we recommend that security teams also consider EPSS scores to get a better picture of the actual risk that a vulnerability creates.
Exploit Prediction Scoring System
The Exploit Prediction Scoring System (EPSS) is a scoring system which estimates the probability of a vulnerability being exploited. Like CVSS, this system is also managed by FIRST (Forum of Incident Response and Security Teams). This scoring system is complementary to other scoring systems, CVSS in particular.
EPSS is based on real life data of vulnerability exploitation attempts. Behind the scoring system is a machine learning model which integrates information from vulnerability databases, and real life exploitation attempts spotted in the wild.
EPSS continues to evolve; the framework was introduced at BlackHat 2019, and the latest update of the system was made in March 2023.
EPSS Scoring
The EPSS score is provided in a daily updated CSV format that can be downloaded from FIRST’s website. The CSV table contains 3 columns:
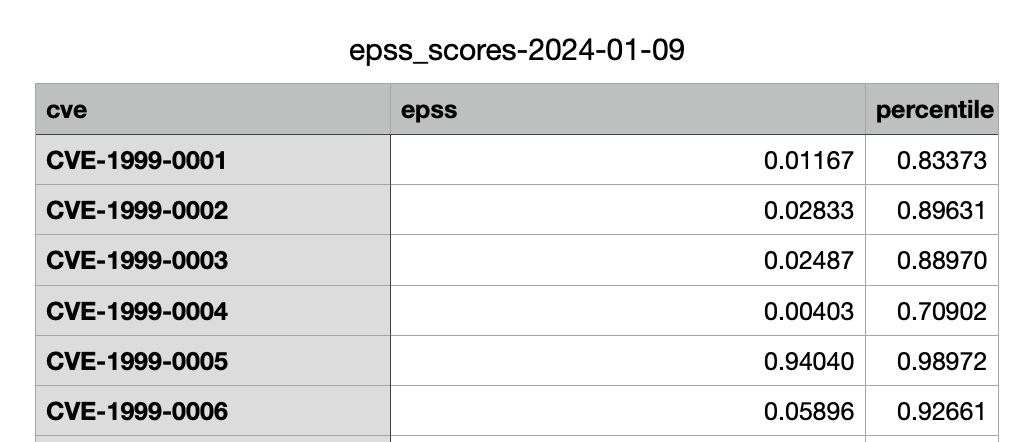
- CVE – The CVE reference as specified by MITRE’s CVE List
- EPSS – the EPSS score representing the probability of exploitation in the wild during the next 30 days in the range from 0 to 1
- For example, a CVE with EPSS of 0.96 has 96% chance to be exploited in the following 30 days.
- Percentile – Is a direct function of the EPSS score which positions that specific CVE in the percentile where the rest of the CVEs were scored lower by the system.
- For example, a CVE with percentile 98% means that 98% of the other CVEs have a lower EPSS score.
How Are the Scores Calculated?
Behind the scoring system lies a machine learning algorithm that is trained on a dataset of all the exploitations observed during the past day. Additional to that is a dataset of vulnerability details such as the vendor, age, MITRE CVE list, CVSS, Common Weakness Enumeration (CWE), and more. The model learns the connection between the vulnerabilities and the exploitation attempts observed, then generates a prediction based on these findings.
The exploitation data comes from a variety of sources such as honeypots, reports from companies, government organizations such as the Cybersecurity and Infrastructure Security Agency’s (CISA’s) Known Exploited Vulnerabilities (KEV) catalog, as well as real life data observed by the project’s data partners.
Why is This Important?
In our previous blog, we explained why CVSS alone is not enough for effective patch management. The EPSS project presented the following matrix which shows how resources could be wasted when remediating vulnerabilities based only on CVSS score. The below matrix makes the very reasonable assumption that organizations patch all vulnerabilities with a CVSS score of 7 (high) and above (critical).
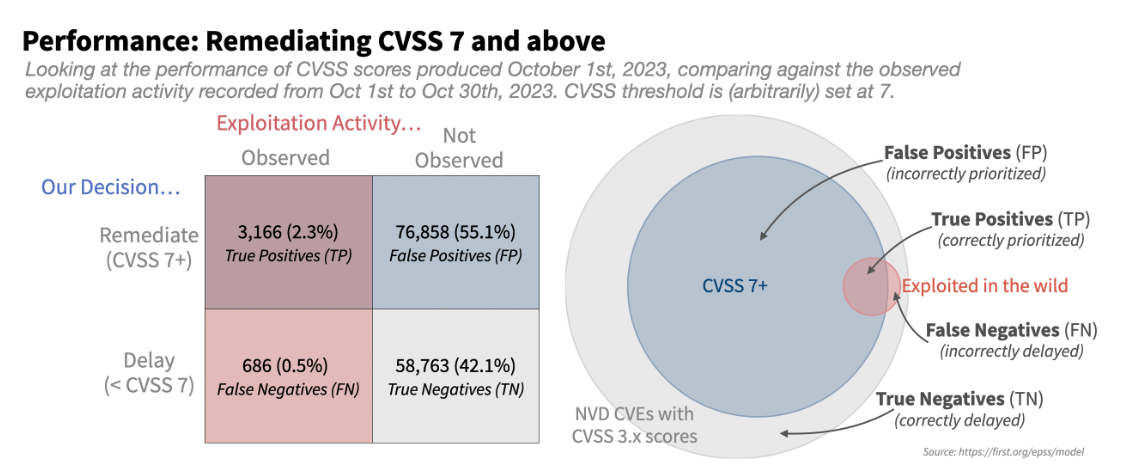
In the diagram we can see that only 2.3% of the CVEs scored at CVSS 7 or above were actually observed in an exploitation attempt (True Positives (TP)). The majority of cases would have been prioritized for remediation (CVSS > 7) but were not observed being exploited during the whole month being checked (False Positives (FP)).
This is a significant waste of resources for security and remediation teams!
How Would EPSS Have Helped?
Getting EPSS into the prioritization and patching, basing it on EPSS 10% and above, we’re getting a much more optimistic resource waste picture.
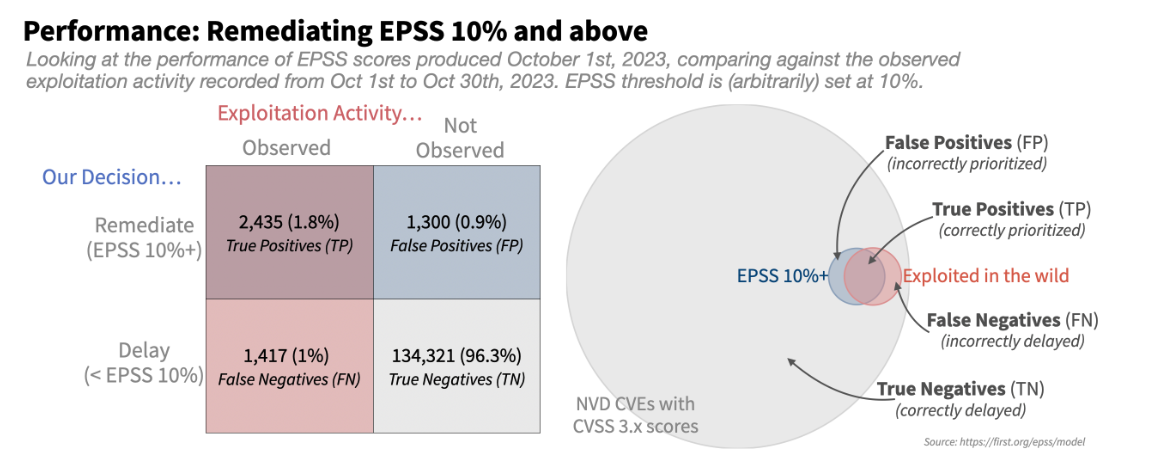
96% of the vulnerabilities, scored with EPSS score of less than 10%, were neither exploited or prioritized for remediation (True Negative (TN)). 1.8% were both exploited and prioritized for remediation (TP).
This is a significant decrease in the level of effort required from the security team in general, and a much more focused and efficient approach to vulnerability patch management. This allows the remediation teams to focus their efforts and resources on the most risky areas in their environment.
Generally speaking there is some correlation between EPSS and CVSS. EPSS provides a comparison of the scoring distribution comparing EPSS to CVSS on the same vulnerability.
From the following graph we see that most vulnerabilities receive a very low EPSS score. Some, mainly around the higher CVSS scores, are also getting a higher EPSS score:
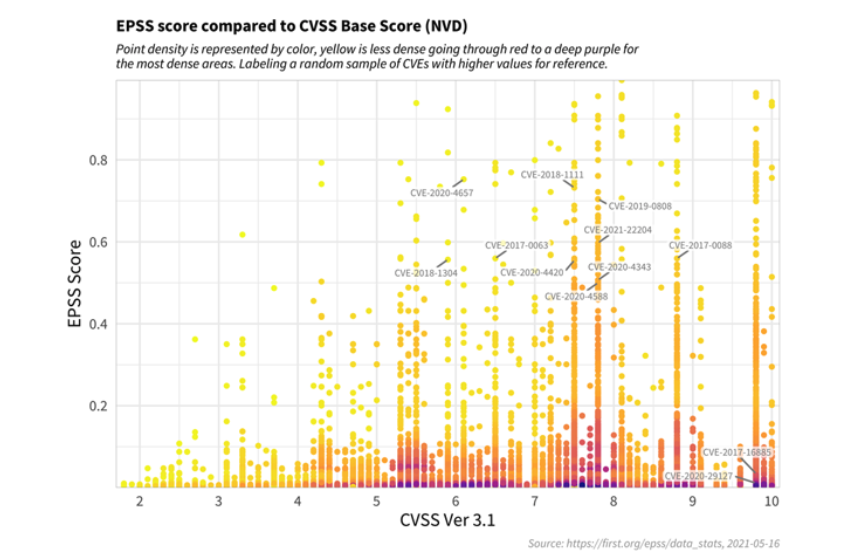
Another interesting finding from this graph is the high density of CVEs that are both scored with critical CVSS score, and scored 0 in EPSS. This means that even though these vulnerabilities are important and dangerous, the probability that they will affect the system is almost non-existent.
Let’s take 3 examples of vulnerabilities and how their EPSS score changes our patching approach..
- CVE-2021-44228 (Log4j)
- This has a critical score in CVSS (10), also has a high score in EPSS 0.974 (97.4%), as well as a large impact – the percentile 0.999 (99.9%). So far so good.
- CVE-2020-13956 (Apache)
- This has a much lower score in CVSS (5.3), but with its EPSS of 0.22 (22%) and the percentile at 0.96 (96%). So this middle CVSS score actually has over a 1 in 5 chance of being exploited across 96% of all impacted systems!
- CVE-2019-17531 (Multiple systems)
- Here’s the opposite example. This CVE has a critical CVSS score (9.8) but has an EPSS score of 0.008 (~0%) and a percentile of 0.8 (80%). So it’s got a practically 0% chance of being exploited. Should it be patched? Yes, but not with the same priority as the one above despite being a higher CVSS score.
Is EPSS Combined with CVSS Enough?
Even with all that information, EPSS plus CVSS is still not enough. There are still missing parts to the picture. While we get the information about which CVEs are more likely to be exploited in general, we need to find the systems that are more likely to be accessed and from there, be exploited.
We need to understand the possible impact of an exploitation on every machine, what the effect would be for the specific machine, and what the blast radius would be of a potential exploitation.
Factors such as the type of vulnerability and type of impacted asset become more relevant. To be truly effective, vulnerability management teams need to assess the exposure and attack paths to clearly prioritize patching order.
This level of deep context and attack path analysis is a key differentiator in the Orca Security platform. Orca uses EPSS:
I encourage you to learn more about how EPSS can complement your patching prioritization and I hope you’ll realize this is a great first step. If you really want to see an increased effectiveness of your teams with a significant decrease in wasted resources then please get in touch and a member of our pod will be happy to help.
Further EPSS Resources and the Orca Platform
A side note for data geeks like me… As data processors, EPSS provide a lot of interesting information about exploitations on their website. Everything from highest probability CVEs that were published in the past 30/90 days with the likelihood of exploit in the coming 30 days, through recent increases or decreases of exploitation in the wild, all the way to the correlation between the age of a vulnerability and its EPSS score.
Like FIRST, we are data obsessed at Orca Security and continually expand our Unified Data Model to enable advanced data analytics. This allows us to effectively prioritize threats so security teams can remediate strategically and focus their efforts on the risks that matter and avoid wasting time on those that don’t. If you’d like to learn more about how the Orca Platform can help improve your cloud security, schedule a demo with one of our experts and we’ll be glad to show you.





