Recently, the US National Security Agency (NSA) joined United Kingdom’s National Cyber Security Center (NCSC) in releasing an advisory detailing the recent TTPs (or tactics, techniques, and procedures) of the group known as APT29 (or, in other taxonomies of threat actors, Midnight Blizzard, the Dukes, and Cozy Bear). The threat actor is thought to be a part of the SVR (an element of the Russian intelligence services). The group has been active since at least 2008 and is associated with attacks against government ministries and agencies in Europe, the US, Central Asia, East Africa, and the Middle East.
Compromises at the US Democratic National Convention (DNC) during the 2016 election cycle and, more recently, against Microsoft are prominent incidents attributed to APT29. In the attack on Microsoft’s servers on January 12th, APT29 exfiltrated email-related data, and accessed Microsoft source code.
While we wouldn’t recommend basing protection and response strategies on the TTPs of a single actor without strong indications that your organization is being actively targeted, we do believe that looking at the activities of a group like APT29 can help us all develop strategies to collectively improve our defenses. In this blog, we’ll summarize the TTPs that NCSC identified and discuss how an organization’s ability to identify and remediate associated risks can be bolstered by the Orca Cloud Security Platform. Of particular note in NCSC’s advisory is the indication that APT29 is specifically targeting cloud services and deployments as part of their evolved strategy.
APT29 Tactics, Techniques, and Procedures
Over the years APT29 have evolved along with its victims, shifting from exploiting software vulnerabilities to using cloud services to their advantage and gaining foothold on the victim’s network.These are the current ‘signature’ TTPs of APT29:
- Access via service and dormant accounts: brute-forcing and password spraying service accounts to gain strong and privileged access to the network and dormant accounts that were overlooked by the security teams of the organization.
- Cloud-based token authentication: APT29 has been using access tokens to access victim’s accounts, without needing passwords. These tokens were likely leaked or stolen by the malicious actors.
- Enrolling new devices to the cloud: upon successfully bypassing authentication, APT29 were seen registering their own devices as a part of the victim’s cloud tenant and gaining access to the network.
- Residential proxies: another TTP associated with APT29 is the use of residential proxies, in an attempt to remain unseen on the internet. The malicious actors would use the residential proxies to make traffic appear to originate from IP addresses within the victim’s network, making it difficult to differentiate from legitimate traffic and making IP-based network defenses redundant.
Neglected cloud assets especially at risk
The first stage of APT29’s strategy focuses on what Orca refers to as ‘neglected assets’; that is, they focus on accounts and assets that are still active but aren’t well managed, if at all. Neglected assets can be a particularly thorny problem in the cloud as, particularly in larger organizations, they may be spread across hundreds of accounts in several different cloud providers.
Unfortunately, neglected assets, such as those with an unsupported operating system or no patching for 180 days, are pretty widespread and sometimes also easily accessible. Our 2024 State of Cloud Security Report found that 81% of organizations have public-facing neglected assets with open ports 80, 443, 8080, 22, 3389 or 5900, making them prime targets for attackers who routinely scan for open ports and known vulnerabilities.
This is a form of the Defender’s Paradox, often expressed as “defenders have to be right every time but attackers only have to be right once.” In other words, while an organization has to manage, maintain, and protect every identity and every asset, an attacker only needs to find a single one that’s been neglected to find a way into the organization. The use of leaked/stolen tokens is similar; for example, Cloudflare indicated that they thought the credentials used in a recent incident were no longer active.
The use of residential proxies negates much of the value of network protections based on deny lists of known bad IP addresses. This may complicate strategies for filtering network traffic to reduce risk.
Reducing emergent risk with Orca
It’s often said that Advanced Persistent Threats (APTs) such as APT29 are more persistent than advanced. The TTPs discussed above typically don’t require the resources of a nation-state actor but they do require persistence to be successful. APT29 might lead with these TTPs but we should expect them to be more widely utilized.
Across the board, Orca Security helps defenders by alerting to and helping teams find neglected assets,even if it’s a single unpatched workload or a single unused (but active) account within millions of assets, covering AWS, Azure, Google Cloud, Oracle Cloud, and Alibaba Cloud. This dramatically reduces the time it takes a security team to find these assets and provides a wealth of information about the asset that eases the job of determining whether it needs to be updated or decommissioned.
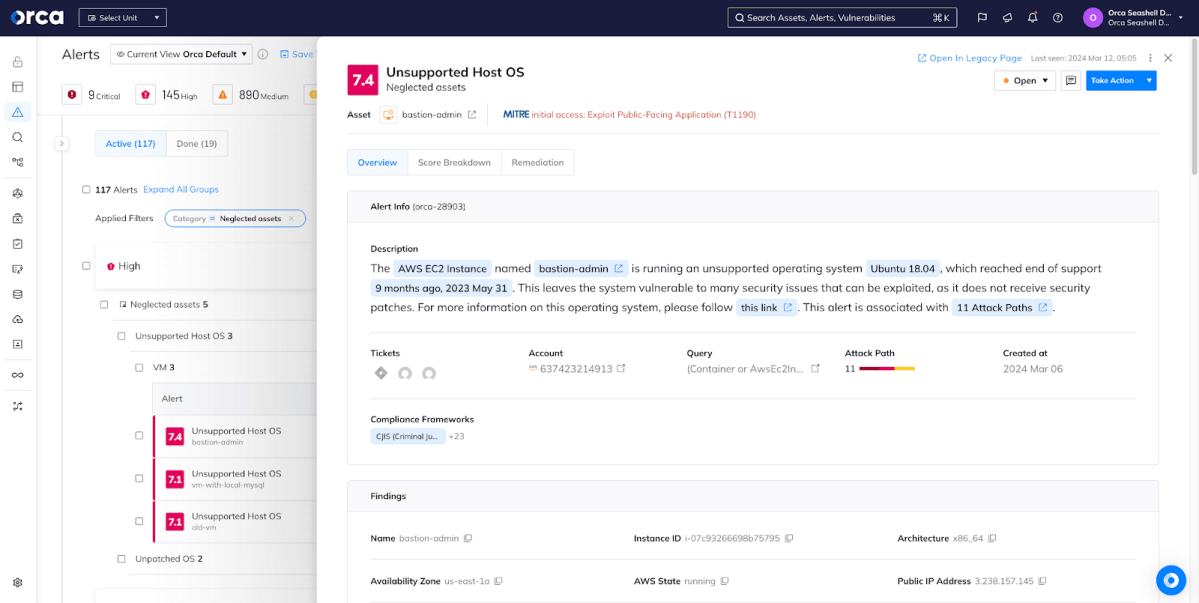
Orca automates detecting neglected assets in organizations’ cloud estate.
Detect and patch vulnerabilities, prioritizing exposed assets
Because Orca’s SideScanning technology provides complete coverage of virtual machines, containers, and other workloads in every cloud account being scanned, organizations can identify where exploitable vulnerabilities are present. Orca’s dynamic context takes this further, using a wide range of intelligence about each workload to score the relative risk, allowing analysts to identify which asset is riskiest based on clues such as whether it’s directly accessible from the outside world and if the workload has access to configurations, such as attached roles, that are exploitable for lateral movement.Address weak authentication and other access issues
Orca also identifies and alerts on the sorts of identity misconfigurations that APT29 is reported to use. Orca helps organizations identify accounts that are inactive, that do not enforce multi-factor authentication (MFA), and that have excessive and/or unused privileges.
Orca further identifies users in virtual machines where the account is using a password that is weak or that has been part of a previous breach – precisely the passwords that APT29 and other groups target in dictionary and password spray attacks. And Orca can help to detect and alert on the failed authentication attempts that are generated during such attacks. Orca can detect these risks and threats across accounts and Cloud Service Providers.
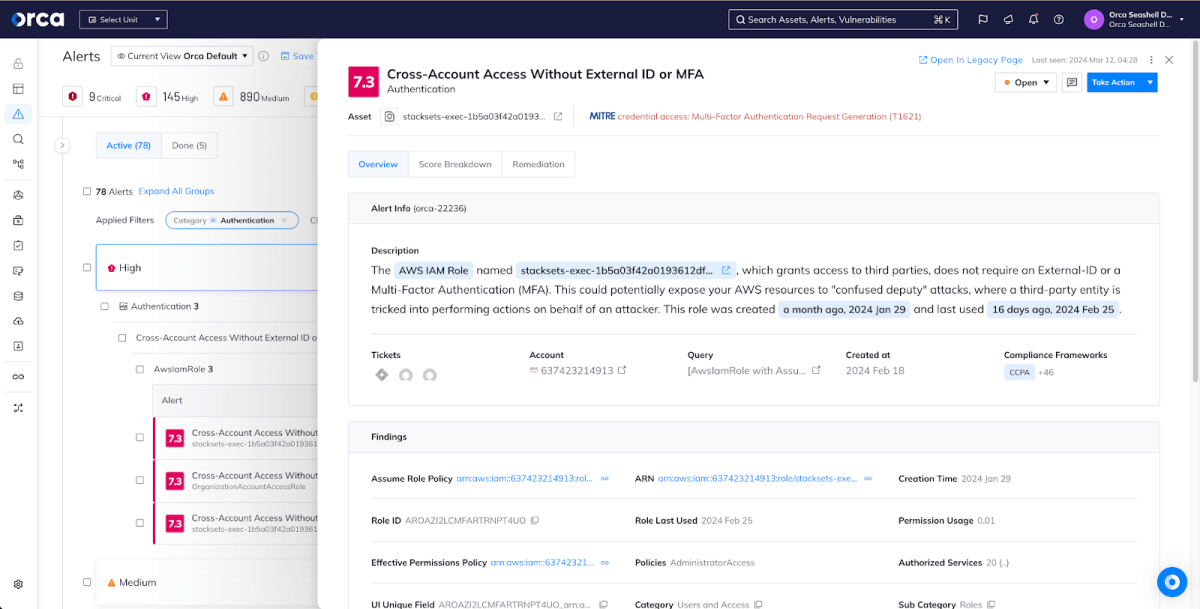
Identity risks are detected, contextualized, and alerted on by Orca Security
Detect exposed secrets in pre-deployment and production environments
Orca identifies hundreds of specific types of access tokens that may be used in, and to gain access to, cloud resources, as well as using advanced analysis to identify more generic, high entropy secrets. These secrets can be found both pre-deployment, where they can be more easily addressed, and in active deployments, where they might cause the most damage.
Swift cloud risk remediation
When Orca identifies risks, it helps security teams quickly remediate issues using automated, guided, and AI-powered remediation options. Using built-in GenAI, Orca allows teams to generate high-quality remediation instructions for each alert straight from the platform, enabling your team to address cloud vulnerabilities and risks 2-3 times faster. Automated rules can also be configured, which automatically fix issues as soon as they are detected, such as the absence of MFA on a user account.
Contextual insights from a unified platform
Orca brings all of this, and much more, together in a single data model, UI, and platform that enables security teams to efficiently consume all of the intelligence and to investigate risks and threats quickly. Schedule a personalized demo with one of our experts if you’d like to learn more about how Orca can help defend your cloud environments against threat actors such as APT29.







