Last week, Microsoft revealed that the Russia-based threat actor group known as Midnight Blizzard, Cozy Bear, and APT29 had compromised email communications at Microsoft, starting in November, 2023 and running through January 12th, 2024, when it was finally detected. Microsoft has since published a more detailed report on the approach that Midnight Blizzard took to gain initial access to the environment and then move laterally to the accounts and intel that they seem to have been interested in.
In this blog, we’ll explain how the Microsoft attack happened and what measures organizations can put in place to protect themselves against similar types of attacks.
Microsoft Midnight Blizzard attack explained
In their latest report, Microsoft identified two phases of the incident:
- Initial Access: Password Spray – The attackers used a short list of common passwords and tried them against a variety of accounts & systems. Midnight Blizzard targeted this approach to reduce the likelihood of discovery by targeting only a relatively small number of accounts, using fewer attempts, and using source IP address ranges associated with residential users to avoid detection based on the volume of login failures. This led to the compromise of a “legacy non-production test tenant account”.
- Propagation: Malicious OAuth Use – After gaining the initial foothold in the testing tenant, the attackers found an old testing OAuth application that had overly permissive permissions in the Microsoft environment. They used these permissions to create another OAuth application that eventually granted them the full_access_as_app role, exposing some mailboxes in the corporate Microsoft Exchange Online to the attackers.
These phases are worth paying attention to because, while Midnight Blizzard is typically known for sophisticated attacks and advanced techniques, they were able to use relatively common misconfigurations to achieve their desired results here. Rather than a sophisticated and advanced campaign, this breach is notable for the attacker’s persistence and patience in discovering and exploiting these issues.
The misconfigurations that enabled this breach are also notable for not just being common but for being problems that could affect on-prem resources, SaaS platforms such as Microsoft Exchange Online, as well as the sort of public cloud resources and workloads that the Orca Cloud Security Platform secures.
Fortifying your defenses against Midnight Blizzard and others
Across all platforms, organizations need to ensure that they’ve applied best practices everywhere – even a small lapse like Microsoft’s legacy account missing MFA, opens a door for a persistent threat. Below are four recommendations by which you can significantly reduce your attack surface:
#1. Ensure strong passwords are used everywhere
Research shows that the strongest passwords aren’t just long or composed of different upper case, lower case, numeric, and symbol characters; rather, they are unique – not used for accounts elsewhere with the same username/e-mail and not in the lists of the most common passwords used anywhere.
#2. Use multi-factor authentication (MFA) everywhere
Even exceptionally strong, unique passwords may fail in many ways – for example, if a user’s workstation gets infected with a key logger, even the strongest passwords are trivial for an attacker to collect. MFA creates additional protection for user authentication.
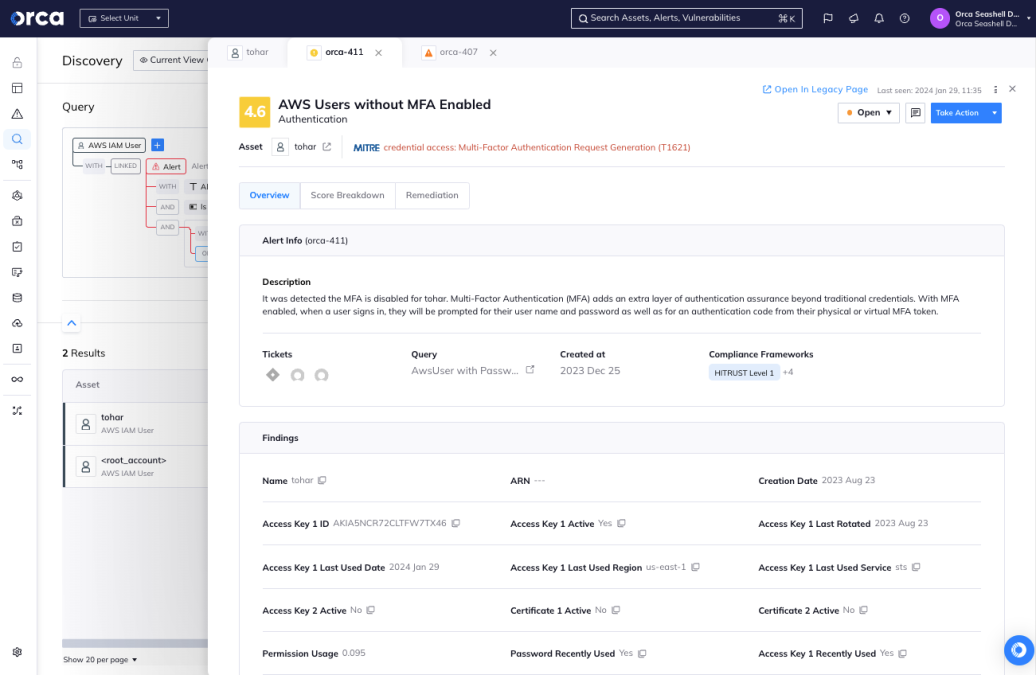
Orca warns when cloud users are configured without MFA enabled
#3. Monitor authentication failures for anomalous sources & patterns
Monitor authentication failures and, perhaps more importantly, successes for anomalous sources & patterns. Failed authentication indicates your controls are working but a successful, anomalous login may indicate your controls have failed.
#4. Monitor creation & configuration of OAuth applications
Block organization users from creating new OAuth app registrations – ensure that all OAuth app registrations are created by privileged users through an approved process – and regularly audit to check that apps, particularly those that are used in testing or that have been deprecated, don’t have unnecessary privileges.
How Orca Security Can Help
Security tooling can help to ensure that you are following the recommendations listed above and flag any instances where you are not. For resources in public cloud platforms, Orca Security alerts when it finds any unsafe resources.
For instance, Orca will notify security teams when it detects cloud users without MFA configured and local user accounts on virtual machines with password hashes that match known weak/leaked passwords, both factors that might be used in attacks against authentication. Additionally, Orca’s Cloud Detection & Response (CDR) can detect anomalous behavior that might indicate suspicious activity and data exfiltration, as well as finding malware and malicious tools used by attackers.
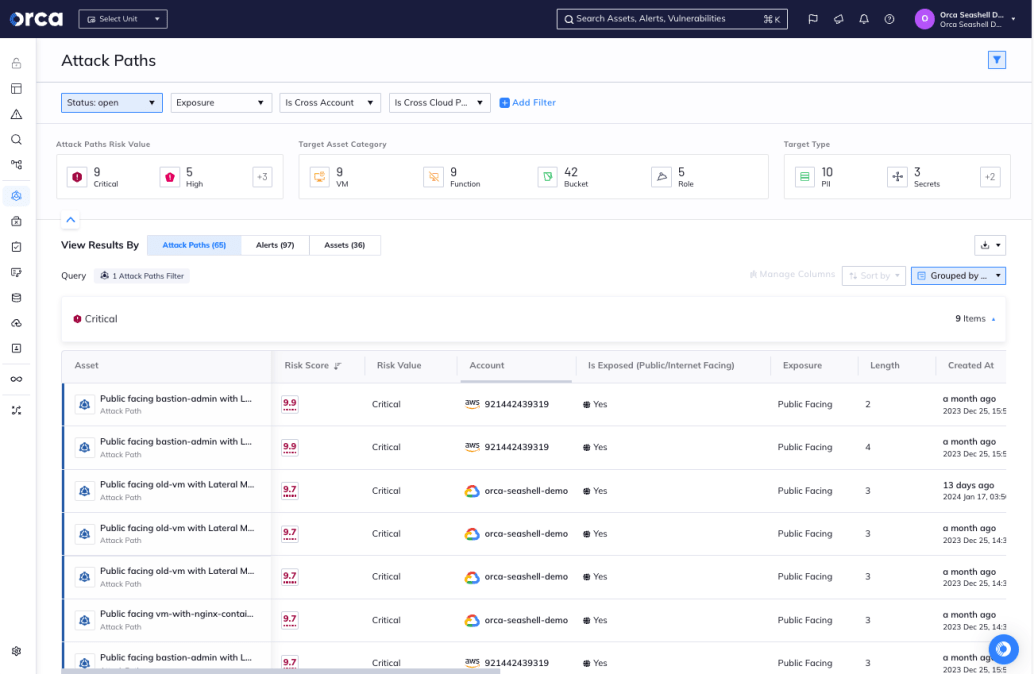
Orca finds all possible attack paths in your environment and scores them according to potential impact
Finally, by minimizing lateral movement risk in the environment and solving the misconfigurations and vulnerabilities that form dangerous attack paths to business critical assets, organizations can ensure that even if an attacker is successful in accessing the environment, the actual damage they can do will still be limited.