Lateral movement refers to the tactic used by threat actors to navigate horizontally or sideways across a network, typically after an initial breach, in order to gain access to different systems, servers, or endpoints within the network.
A major component of ransomware attacks (WannaCry, NotPetya), it has been featured in some big headline breaches such as Target’s (initial access via a supplier’s credentials then lateral movement to point-of-sale (POS) system) and the SolarWinds supply chain attack (a very sophisticated attack utilizing many advanced techniques).
Understanding the Complexities of Lateral Movement
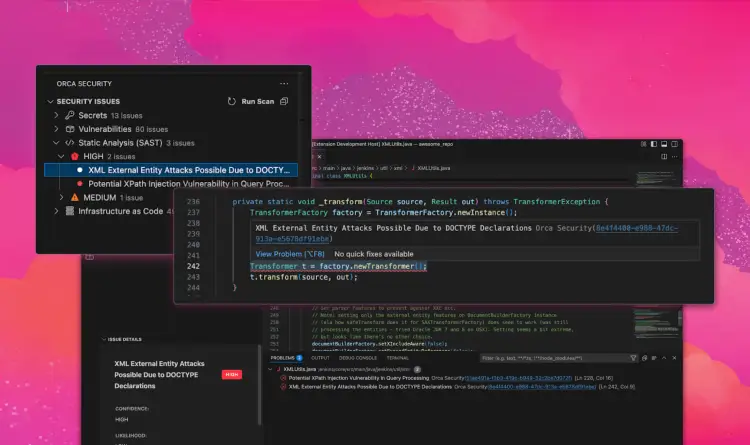
The specifics of this example aren’t important but Identity and Access Management (IAM) in cloud computing is notoriously difficult. It takes a lot of effort to get up to speed on what profiles could assume roles or what attached policies are. These vary with each cloud service provider (CSP) and cover a vast array of permissions.
With the screenshot above any technology professional should now be confident to understand the lateral movement available – without needing to know how to search for this themselves!
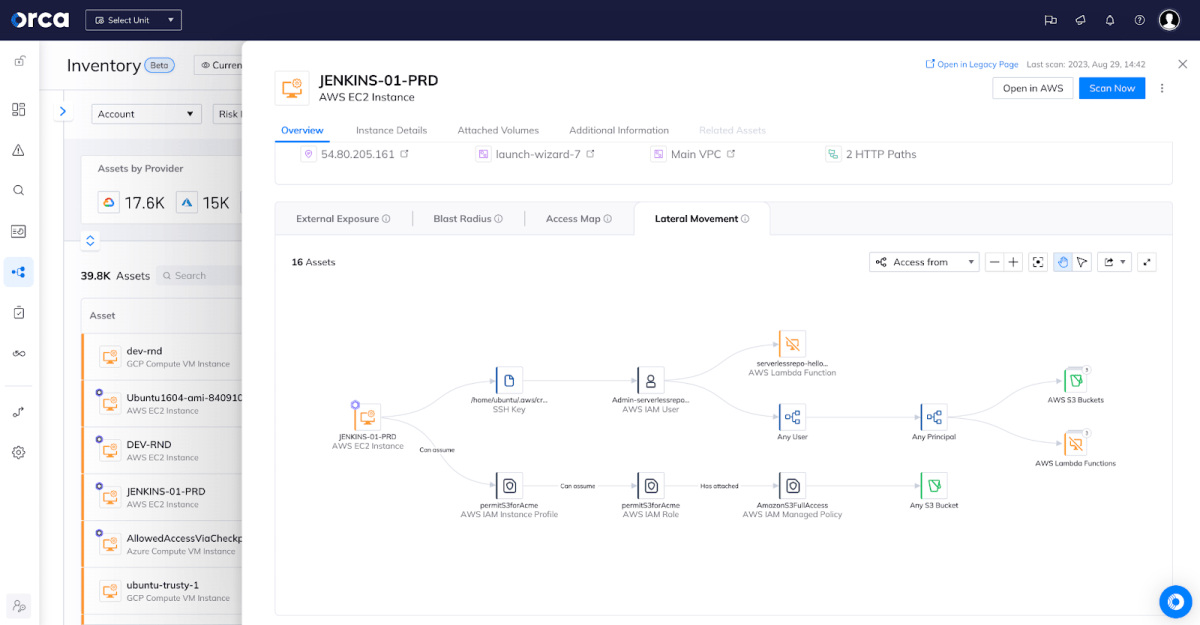
Using this graph view, we can easily identify that we have an asset on the left and then policies and permissions which lead to assets on the right.
We are visual creatures and this representation of complex underlying access patterns and dependencies which can then be explored to expose alerts and risks really can’t be underestimated.
As a CTO or CISO I can see that my security staff can act at a higher level because they don’t need extensive cloud provider training. My operations or DevOps teams can now understand how one misconfiguration can lead to larger consequences without being cloud security architects.
- People in any position can now understand how an asset is externally exposed, the blast radius, what users and groups can access, as well as the lateral movement possible. They can drill into misconfiguration and other alerts, from one seamless view. There is no need to be advanced experts in a particular cloud provider.
- Non-security people can now see how that external exposure is part of the bigger picture. They understand the context around the alerts without having to be deep security professionals.
In my example I picked on a virtual machine that was running but thanks to how Orca operates across cloud security domains this could just as easily have been a storage bucket, or AWS ElasticSearch instance, or even a managed database service. Here’s an example of one which perhaps better shows the interconnectedness of lateral movement. Remember, all of this has been discovered automatically without deploying software or having to manually assess configuration files. Orca has modeled our live estate:

Personally, as an ex-CTO, this makes me happy because it means my resources can now act at a higher level, helping with my resource constraints, and enables me to move fast to service the business needs.
As a security professional this makes me happy because now my operations teams are empowered to investigate and resolve issues.
Most importantly, as a human being, this makes me happy because regardless of your level in technology you can play an active role in securing cloud estates and that makes our people expand and grow.
Technology should elevate people and automate the processes.
To see how Orca will enable your people, why not get in touch for a personalized demo or watch an on-demand demo if you’re short on time.