HTTP Protocol Stack Remote Code Execution Vulnerability (CVE-2022-21907)
When was CVE-2022-21907 identified?
On January 11, 2022, a security vulnerability was identified, and Microsoft assigned the CVE 2022-21907 with CVSS of 9.8.
Have there been any exploitations of this remote code execution vulnerability in the wild?
As of now (1/16/2022) Microsoft is not aware of exploitations for this CVE in the wild but urges clients to immediately apply the security patches they released in Microsoft’s January 2022 Patch Tuesday that addresses CVE-2022-21907.
What does it target?
The publicly disclosed vulnerability targets operating systems that are utilizing the HTTP Protocol Stack (http.sys) to process packets.
In Windows Server 2003 Microsoft introduced the http.sys driver, which launches the http stack application and listens for http and https requests.
HTTP.sys listens for HTTP requests from the network, passes the requests onto IIS for processing, and then returns processed responses to client browsers.
Among the services that use the http.sys driver you can find IIS and WINRM.
How could an attacker exploit this RCE vulnerability and which Microsoft operating systems are vulnerable?
In case the exploitation is successful, an unauthenticated attacker with network access to the target machine can achieve remote code execution on the target machine. The attack is performed by sending a specially crafted packet, without user interaction needed on the victim’s end.
According to Microsoft, the following operating systems are vulnerable:
- Windows Server 2022
- Windows Server 2019
- Windows 11
- Windows 10
For more information: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-21907
What actions should I take to protect my business from CVE-2022-21907?
- Apply Microsoft’s January 2022 Patch Tuesday that addresses CVE-2022-21907 as soon as possible, and prioritize internet-facing assets as they can be exploited by external unauthenticated threat actors.
- For Windows Server 2019 and Windows 10 version 1809 that are not vulnerable by default, delete the DWORD registry value “EnableTrailerSupport” if present under “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\HTTP\Parameters”.
- Implement Orca Security in your cloud environment to get full visibility and coverage in minutes.
Can Orca Security detect CVE-2022-21907?
Yes. By using Orca Security you have full visibility and coverage on your assets that show you if and where you are vulnerable, so you can take action to mitigate the risk, and apply ]security measures.
Orca Security detects CVE-2022-21907 and alerts on the vulnerable assets as shown below:
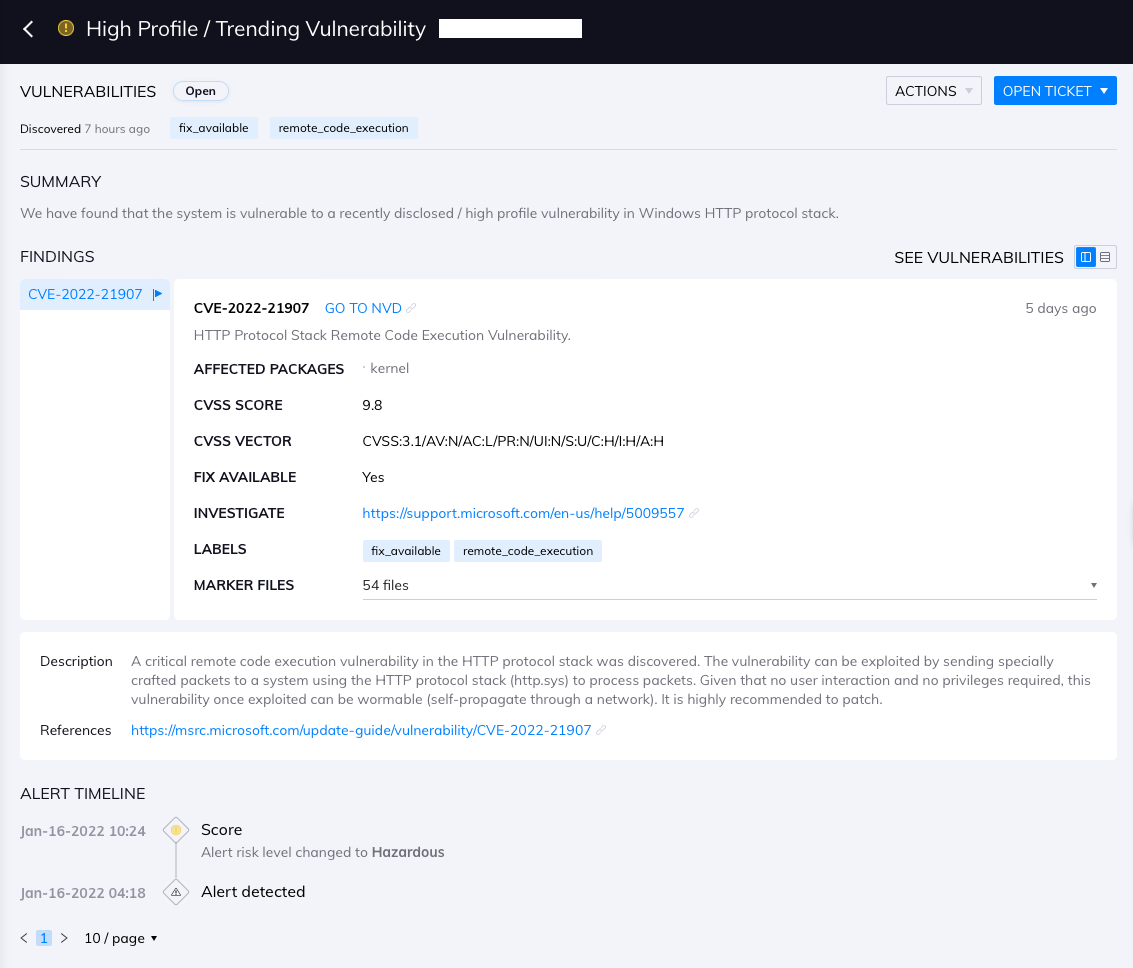
But I’m not an Orca Security customer yet. What should I do to identify this remote code execution vulnerability across my public cloud estate?
I invite you to experience our tech and talent first-hand with a no-obligation, free cloud risk assessment. You’ll get complete visibility into your public cloud, a detailed risk report (including CVE-2022-21907), an executive summary, and time with our cloud security experts.
Discover Your Cloud Vulnerabilities In Minutes
Scan your entire AWS, Azure, and Google Cloud environments for vulnerabilities with Orca Security’s free, no obligation risk assessment.







