CVE-2021-4034 Update (07-01-22)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2021-4034 to its Known Exploited Vulnerabilities Catalog this past week, citing active exploitation.
This addition follows the original discovery of the Polkit vulnerability in January 2022. An out-of-bounds read and write vulnerability, “PwnKit” allows for local privilege escalation with administrative rights using its pkexec utility. When exploited, unprivileged users can execute commands as a root user. CVE-2021-4034 is categorized as high risk with a CVSS of 7.8.
For a full summary of this vulnerability and steps to remediate, read the original report below.
“PwnKit” allows privilege escalation in Linux
On January 25th, a new critical Linux local privilege escalation vulnerability was published and assigned CVE-2021-4034. This vulnerability was found on Polkit’s pkexec utility, which is a widely used package installed by default on almost all popular Linux distributions. CVE-2021-4034 allows every unprivileged user to become a root user in a few steps, which makes this vulnerability critical and highly exploitable. Its origin has been tracked to the initial commit of pkexec, more than 12 years ago, meaning that all Polkit versions since 2009 are affected.
What is Polkit’s pkexec utility?
Polkit (also known as PolicyKit), is developed and maintained by RedHat. Polkit allows creating and controlling centralized system access policy so that unprivileged processes can communicate with privileged processes in Unix-like systems. Pkexec is the execution utility of this package that allows an authorized user to execute a piece of code as another user. By default, if users are not specified, the executed code will run as root (super administrative user).
Linux PwnKit Vulnerability
The Polkit vulnerability, CVE-2021-4034, was published on January 25th by the Qualys research team and dubbed ‘PwnKit’. They found that if no arguments are passed to pkexec, a memory-out-of-bound situation is created, and the program is set to execute the environment variables. Hence, if a malicious user is creating a crafted environment variable, it can be executed as a root by this pkexec utility. A successful exploitation would grant unprivileged users root privileges on the affected machine. A number of publicly available exploits have already been published, which can easily be abused by a malicious actor.
Remediating PwnKit
All versions of Polkit since 2009 are vulnerable. As this package is installed by default with all popular Unix-like distributions, this affects most Linux and Unix-like machines. To remediate CVE-2021-4034, organizations must update the Polkit package by applying the patches that Polkit’s authors released on their GitLab page. RedHat and Ubuntu have also published remediation steps on their respective websites. However, before you can patch, you first need to find out which of your resources are running Polkit.
Detect PwnKit in your cloud in minutes
Orca Security’s agentless platform provides 100% visibility into your cloud assets on AWS, Azure, and Google Cloud and will generate an alert for each asset that is exposed to this vulnerability. In addition, Orca will prioritize detected vulnerabilities based on the possible business impact of a potential exploitation. This allows security teams to first focus on remediating the vulnerabilities that if exploited, would have the biggest adverse impact on the organization.
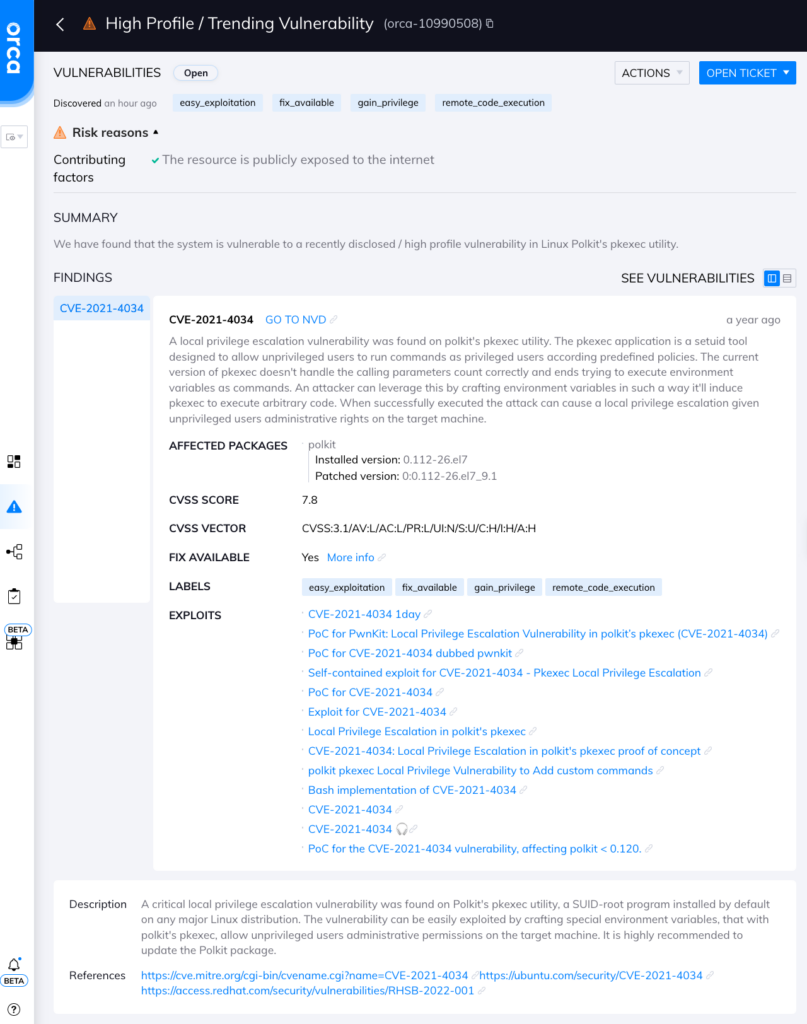
Orca Security’s alert for the PwnKit vulnerability
The Orca Security intuitive query engine also allows you to search for all cloud assets that are running Polkit, and automatically assign issues for remediation in ticketing systems such as Jira and ServiceNow. This provides security teams with a complete overview of all affected systems so they can effectively plan for their remediation.
Orca Security’s Free Cloud Risk Assessment: Identify Your Vulnerabilities
If you currently don’t have a cloud security solution that can provide 100% visibility into your cloud estate (note that agent-based cloud security solutions typically only cover 50% of cloud assets due to cumbersome and limited deployment), Orca Security is providing a free, no-obligation cloud risk assessment to help you detect all Pwnkit vulnerabilities in your AWS, Azure, and Google Cloud estates.
As part of the cloud risk assessment, Orca Security will provide your organization with a detailed risk report (including CVE-2021-4034), an executive summary, and time with our cloud security experts. Do you think you have already detected all your Pwnkit vulnerabilities? Why not get a second opinion?
Discover Your Cloud Vulnerabilities In Minutes
Scan your entire AWS, Azure, and Google Cloud environments for vulnerabilities with Orca Security’s free, no obligation risk assessment.