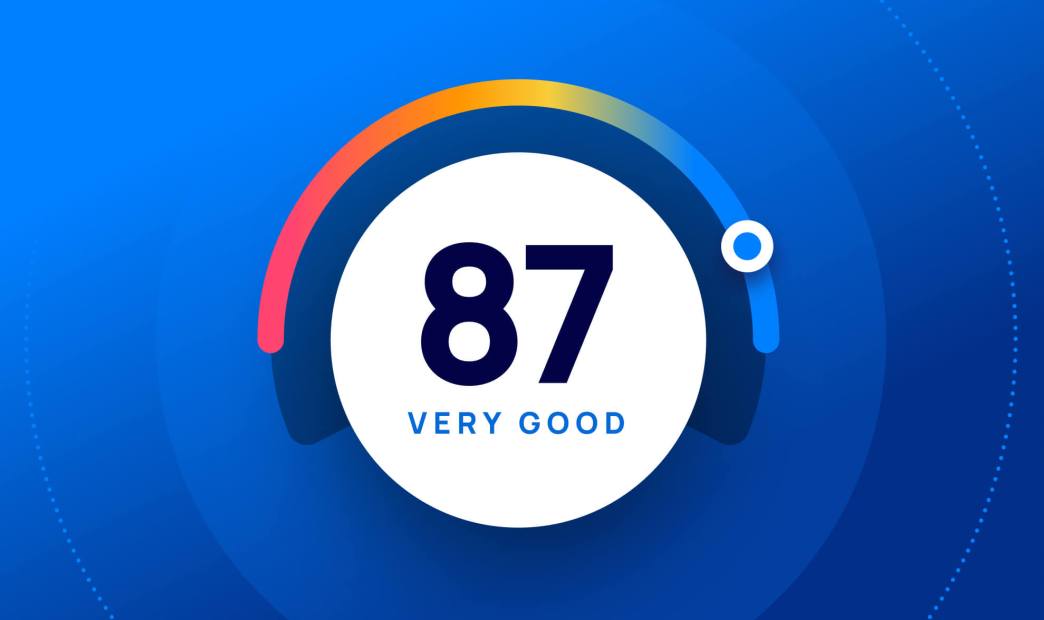
Most people think they’re an above average driver, but let’s be honest, that’s probably not true. Back in September, Tesla released its new Safety Score feature, “an assessment of your driving behavior based on five metrics called Safety Factors.” The idea is to get a data-driven, objective, and easy to understand assessment of your safety as a driver and the likelihood of getting into an accident.
Taking inspiration from Tesla, your cloud security posture can similarly be assessed by a set of data-driven, objective criteria. While this is no easy task, it is extremely valuable nonetheless. CISOs and senior management want to understand the organization’s security standing, its strengths, and more importantly, its weaknesses–that is, its risks.
Determining risk goes beyond pinpointing individual vulnerabilities or weak points. The value is more in a bird’s eye view—supported by objective data—that gives a broader “report card” of just how things are looking and where efforts should be directed first, in order to make the biggest security improvements.

As I said, that’s challenging. It’s difficult to convey the actual state of your security posture to management and directors of the board without getting into technical details. Furthermore, It is extremely hard to quantify if you have X vulnerabilities and Y compliance violations – is it good, bad, or just ugly?
In addition to helping customers identify and prioritize cloud risks, we at Orca are excited to offer a new way to understand and share your current cloud security status based on specific predefined parameters: the Orca Security Score.
The Orca Security Score enables you to:
- Objectively assess and monitor your cloud security posture
- Benchmark your cloud security performance against industry peers and across business units within the organization
- Measure your risk mitigation efforts
- Report security progress and results to senior management and Board of Directors more clearly and effectively
- Provide support for budget and staffing requests
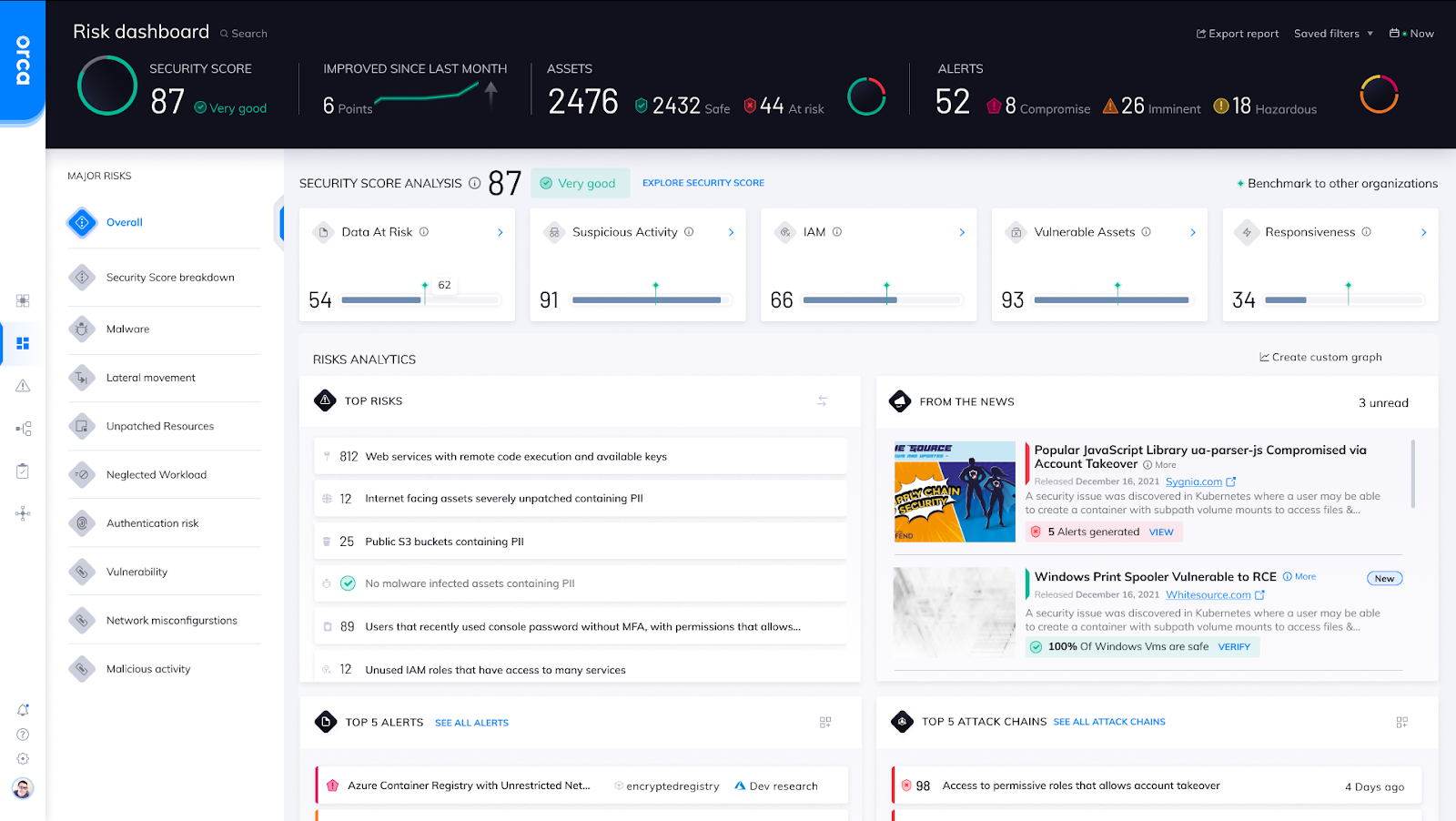
The Orca Risk Dashboard showing the Orca Security Score across 5 categories.
A Security Score With Actionable and Measurable Data
The Orca Security Score is found on Orca’s Risk Dashboard and is updated daily. The overall score is calculated based on performance in the following five categories:
- Suspicious Activity – Malicious or abnormal activity that may indicate a security breach, measured by the percentage of assets with malicious activity, malware, potentially unwanted applications, and suspicious activity in shell history.
- IAM – IAM misconfigurations or misplaced keys that can be used to gain deeper access to an organization’s high value assets. The lateral movement score is measured by percentages of inactive privileged identities, unused granted permissions, users without MFA, and assets with weak, leaked, or misplaced passwords and keys.
- Data at Risk – Misplaced sensitive data that is not properly protected or can be compromised, measured by percentages of internet facing assets with PII, assets with malware and PII, compute resources with broad access to buckets, and unencrypted buckets.
- Vulnerable Assets – Assets with critical weaknesses that can be exploited and lead to a possible breach, based on percentages of internet facing assets with critical vulnerabilities, unsupported compute, and neglected assets.
- Responsiveness – An organization’s ability to quickly identify, respond to, and resolve critical security issues. This score is measured by the average time to respond to alerts and percentage of unresolved important alerts, those labeled as “imminent compromise” and “compromised.”
A tab on the dashboard, Security Score breakdown, provides deeper analysis, with a drill down into each category. Note that each metric comes with recommendations for mitigation, making this data actionable and measurable.
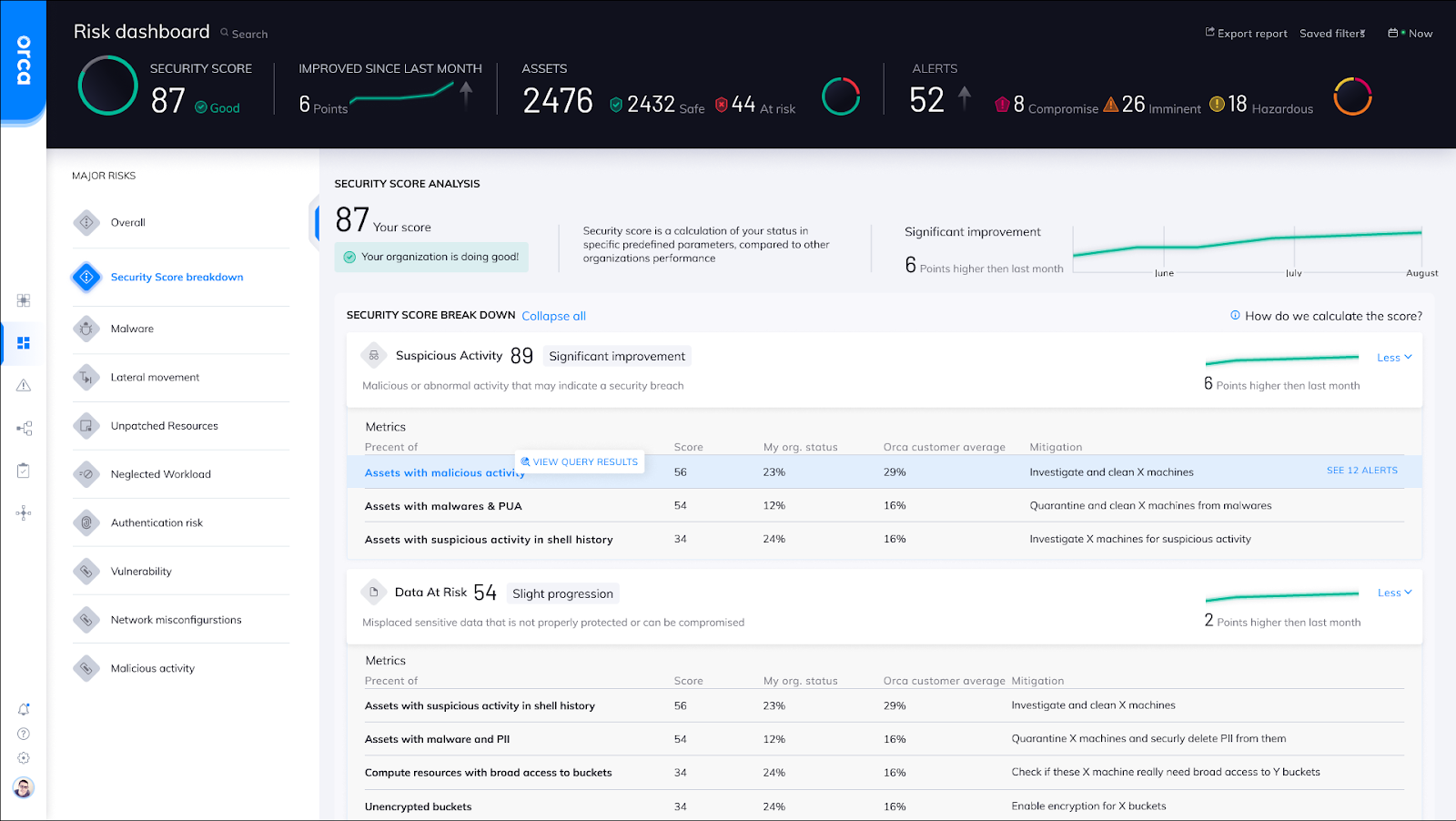
The Orca Risk Dashboard showing the Security Score breakdown.
Facilitating Communication Across The Organization
We believe that the Orca Security Score will help you report to higher management and board directors about security progress more clearly and effectively. Due to the fact that the scores are based on percentages and not raw numbers, you can more objectively make comparisons to other organizations and business units of different sizes.
In addition to reporting to senior management, the Orca Security Score can help with internal self-monitoring, as a way of measuring risk mitigation efforts, to know where to focus efforts, and track progress. It can be used to compare different business units and teams within a larger organization. It could potentially also play a role in measuring the security posture in company mergers and acquisitions, third-party risk management, and even cyber insurance underwriting.
How Good A Driver Are You?
Want to know your Orca Security Score? Orca provides a free, no obligation cloud risk assessment that, in addition to showing you where your most critical risks are, also reveals your Orca Security Score and how your cloud security posture compares to your peers.
You’ll also want to join our upcoming March 10 webinar, on Strengthen Your Cloud Security Posture: How to Evaluate Cloud Security Platforms, which will include a discussion and brief demo of the Orca Security Score.