At Orca Security, we recognize two key paradigms that organizations are facing as they move to the cloud. First, the cloud is a tremendous part of every company’s business–enabling digital transformation, scale, and speed of delivery never before thought possible. With new cloud services, cloud native architectures, and modern DevOps workloads, organizations can achieve amazing things in the cloud.
However, the cloud brings with it notable security challenges and complexity. The sheer number of cloud services present a blind spot for security teams. And, if those cloud services are left misconfigured, they can expose sensitive data to adversaries. Next, ephemeral and dynamic architectures, such as the ones built on containers, Kubernetes, or serverless tech stacks, make it difficult for legacy, EDR-based solutions to be installed on them all–or, the findings lack the context into risks from all the other services that are connected to those workloads and applications. Finally, security teams know they need visibility and protection for running cloud environments and applications, but they also need visibility and control spanning the full application lifecycle to identify and prevent unwanted risks from making their way across the development pipeline.
At Orca Security, we’re on a mission to make it fast, easy, and cost effective for organizations to address the critical cloud security issues so they can operate in the cloud with confidence.
Securing the Cloud Starts with Foundational Cloud Security Controls
From the beginning, we have stayed true to the four principles that we believe an effective cloud security platform should be built on: 100% frictionless coverage of assets, comprehensive security incorporating all cloud risks, contextual intelligence to surface the most critical risks, and finally, consumable security to empower teams to take action and remediate issues.

This philosophy is important and drives how we build our product and deliver innovation to our customers. In order to secure cloud environments, practitioners need to solve foundational security controls first. This includes comprehensive visibility into the security posture of everything you have running in the cloud, spanning cloud services, workloads, data, identities and entitlements, APIs, and more, and handling the core tenets of cloud security: CSPM, CIEM, Vulnerability Management, Container Security, API Security, KSPM, and more. This will, by far, provide the best security ROI. Then, only once an organization can understand and prioritize their most mission critical workloads does an agent make sense for runtime protection and enforcement.
Why we chose not to build an agent
One may ask, Orca is the worlds’ most comprehensive cloud security platform that added so many innovations over the years–pioneering SideScanning, developing Attack Paths Analysis, integrating API Security into a Cloud Security Platform–why not ‘just’ build an agent and tick this box? Some vendors took this approach, and ‘just’ built an agent to tick the check box for runtime security. Unfortunately, the reality is that workload runtime security is a complex task that in order to succeed in, requires a substantial dedicated team focused on that specifically. This team would handle tasks such as protecting against the latest exploit or ransomware, with fast turnaround, or tasks such as making sure that it works on the greatest and latest application distributions. It is a company, not a team. No one wants to go through the agony of deploying an agent just to find out that it can be bypassed by changing one letter in the malware.
Agents coming from the on-premises world are definitely not the solution for the cloud
The next logical approach is to use an EDR agent. They have large teams building and maintaining security agents that provide runtime protection. Yet, few of our customers have tried leveraging EDR agents to handle cloud security. Endpoint Detection and Response encompasses a set of security controls for securing enterprise endpoints, such as on-premises servers, employee laptops, or mobile devices. EDR, which is enabled by installing an agent on these devices, ensures that security teams can ultimately stop or prevent specific user activity.
In the cloud, these solutions fail due to their high operational overhead for installation and operation, intensive CPU consumption, and poor support for dynamic and ephemeral cloud workloads. In fact, many cloud workload protection solutions are merely rebranded EDR solutions that lead to little value for security teams. We’ve seen customers complaining about excessive costs due to the overhead of running these tools–sometimes 10x of the tool cost itself–just to realize that they are tuned to protect against endpoint threats.
Enter ThreatOptix: Building a modern agent to secure cloud native workloads
TheatOptix, founded by former co-founders at EDR leader SentinelOne, is a workload protection company solely focused on modern applications. Their agent is optimized to address today’s ephemeral, dynamic architectures like containers and Kubernetes. For example, their agent ensures low CPU utilization and their R&D team is solely focused on innovation for runtime protection and enforcement of cloud native workloads. We’re proud to be partnering with a team solely focused on this problem, rather than attempting to start from scratch ourselves.
“At ThreatOptix, we have focused on cloud workload protection from inception. We ultimately believe the existing EDR solutions are ill-equipped to address the dynamic and ephemeral nature of modern cloud native applications that run on containers and Kuberentes. Partnering with Orca, the leader in agentless cloud security, will strengthen an already innovative solution to better address the use cases for deploying an agent for cloud workload protection.”
Udi Shamir, CEO and co-founder of ThreatOptix
Our Vision: An Integrated Experience, Not a Checkbox
In the cloud security marketplace, many companies have released a “platform”, but they have been lacking deep integrations, a focus on user experience, easy onboarding, and valuable ROI for their users. At Orca Security, we have a high bar for innovation and quality–which is why we’re leveraging our strategic partnership with ThreatOptix to build a great customer experience and quality product.
Upon the completion of an integration, Orca Platform customers will be able to immediately deploy and manage the ThreatOptix agent as well as configure policies from the Orca UI. All agent-based runtime telemetry will be fully available within the Orca Unified Data Model to ensure ease-of-use and operation. It will be sold as one SKU, supported by one team, and act as one product
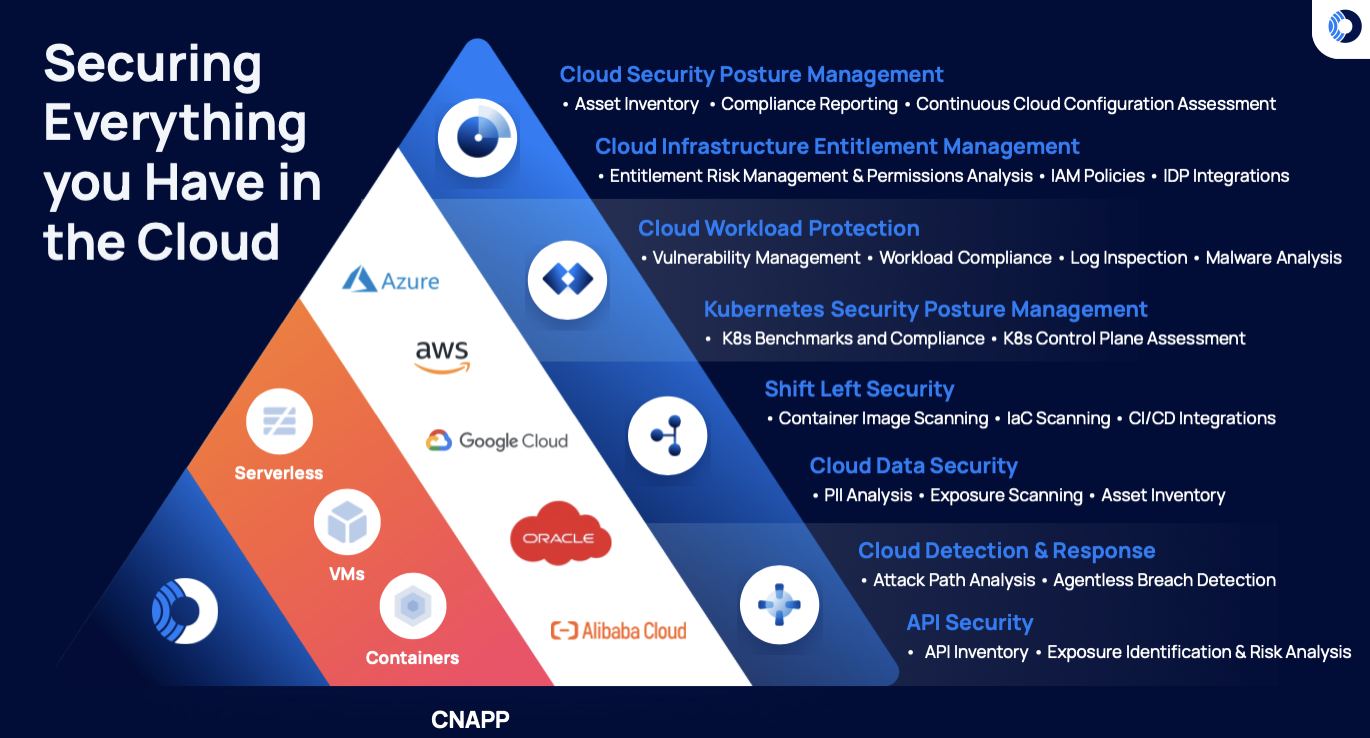
More importantly, the Orca Platform will support agent-based deployments for workloads across any environment that Orca secures today, including FedRAMP environments.
“Many partnerships in the cybersecurity ecosystem lack a deep integration strategy. This leads to duck-taped solutions that are inefficient and lack value for their users. We believe this strategic partnership and integration will be transformative for securing the cloud in a purpose-built way to deliver a seamless solution sold under a single SKU. Once integrated, Orca customers will have a seamless experience with the agent acting similar to a native Orca capability. The Platform will support all cloud environments secured by us today, including highly regulated environments like FedRAMP.”
Gil Geron, CPO and co-founder of Orca Security
Stay tuned for future platform announcements
As we look ahead, we believe the integration will be available in the second half of 2023. If you would like to learn more about the Orca Cloud Security Platform, I would invite you to watch our latest 10-minute demo or sign up for a free 30-day risk assessment.





