We’re excited to announce that the Orca Cloud Security Platform now offers support for Harness, a popular AI-native software delivery platform. Through the integration, joint customers can embed Orca Security into the Harness CI pipeline, automatically scanning IaC templates and container images for security risks, and performing Software Composition Analysis (SCA). The scanning results are presented directly within Harness and non-compliant builds can be blocked automatically. Combining Harness’s industry-leading CI speed with the speed of the Orca CLI means builds are both fast and secure.
This integration shifts security left, allowing developers and DevOps teams to catch risks such as vulnerabilities, misconfigurations, exposed secrets, and overprivileged identities early on in the development process, before they reach production and are much more costly to fix. In this blog, we’ll provide more details on the integration, how to set it up, and how your organization can benefit.
What is Harness?
Harness is a popular AI-native software delivery platform that offers git-based repositories, hosted CI/CD pipelines, and many other devops-related tools. Harness provides one central platform for managing code, building apps, securing them, and deploying them.
What is Shift Left Security?
Continuous integration and continuous deployment (CI/CD) have become essential practices for delivering high-quality applications quickly and efficiently. However, as development cycles accelerate, security can often take a backseat, leaving organizations vulnerable to flaws being embedded in their apps.
Enter Shift left Security, a software development practice that integrates security measures early in the development process, rather than waiting to fix security issues when they have already entered production. The earlier risks are caught, the easier they are to fix. Also, security issues in production can have serious negative effects on a company’s image.
For this purpose, we introduced the Orca CLI, which enables DevOps teams to integrate Orca scanning into their CI/CD workflows, and mitigate any embedded flaws in the build (CI) step of their applications.
How Orca bolsters security checks in Harness
By embedding the Orca CLI in Harness, Orca automatically scans IaC templates, container images, and source code as part of the Harness CI process, checking for vulnerabilities, misconfigurations, and exposed secrets, and performing software composition analysis (SCA).
Orca scan results are shown directly in the Harness UI, embedding security into a streamlined development process that doesn’t require developers to switch to another platform.
Once the Orca CLI is embedded into Harness, the following key features will be available:
- Detailed IaC and container security scans– This integration allows security scans to be automatically triggered as part of the CI pipeline, requiring no manual intervention from developers or security teams. It also only requires a few commands in your build step. The results of these scans are then presented directly within the Harness interface, making it easy for teams to review and act on security findings without context switching or workflow disruption.
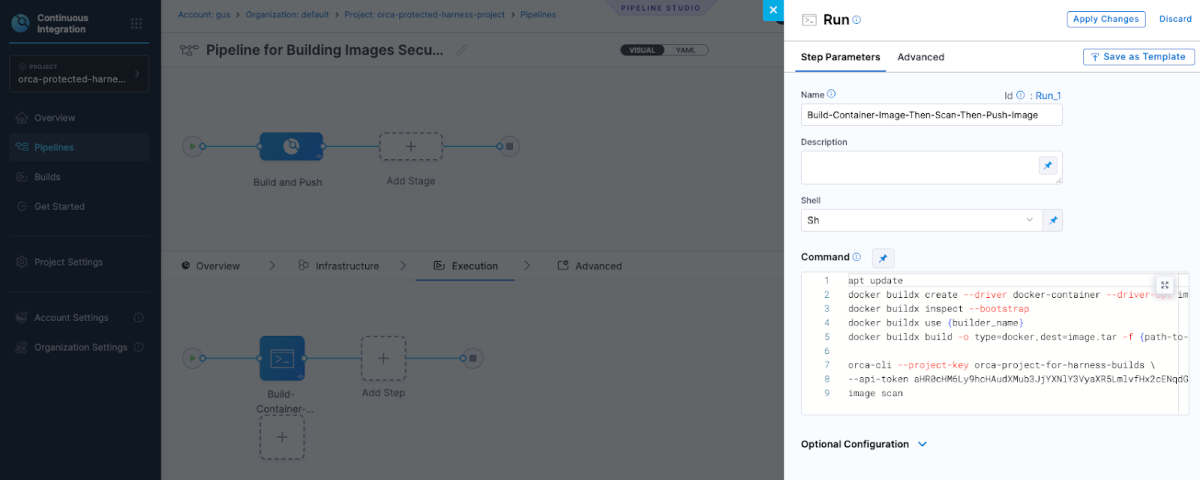
- Actionable risk insights and remediation guidance – Rather than simply identifying vulnerabilities, each identified issue is accompanied by detailed information about its severity, potential impact, and steps for remediation. This context-rich approach empowers developers to quickly understand and address security concerns, reducing the time and effort required to maintain a secure codebase.
- Customizable security policies – Recognizing that every organization has unique security requirements, teams can define their own security rules based on industry standards, regulatory requirements, or internal best practices. This flexibility ensures that the security scans align with the organization’s specific risk tolerance and compliance needs.
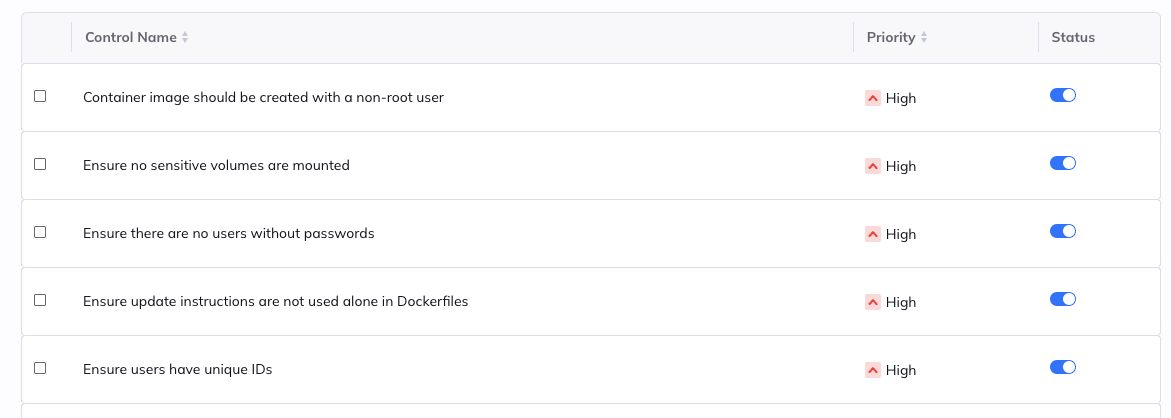
- Automated policy enforcement – To further streamline the security process, Orca Security’s solution enables automated policy enforcement within Harness pipelines. Based on predefined security thresholds, the system can automatically fail builds or trigger notifications when critical vulnerabilities are detected. This automation helps maintain a consistent security baseline across all applications and prevents insecure code from progressing through the pipeline.
How to integrate Orca and Harness
Orca and Harness can be integrated by following these simple steps:
- Create a Shift Left project in the Orca Platform.
- Attach the appropriate policies to this project (secret scanning policy, vulnerability policy, etc).
- Configure the policies (which controls to enforce and whether to block the build upon failure).
- Place the Orca CLI in Harness as a build step and configure it.
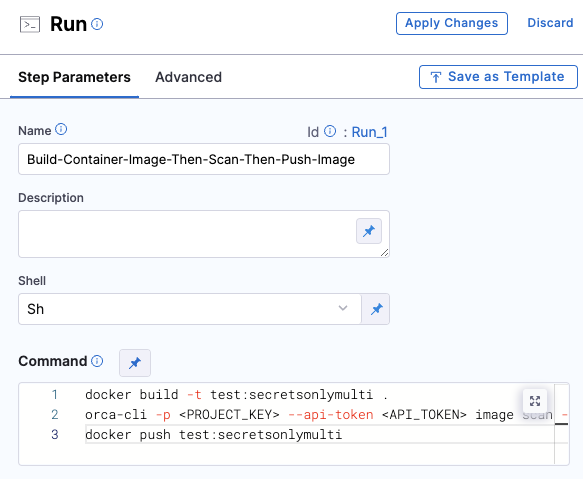
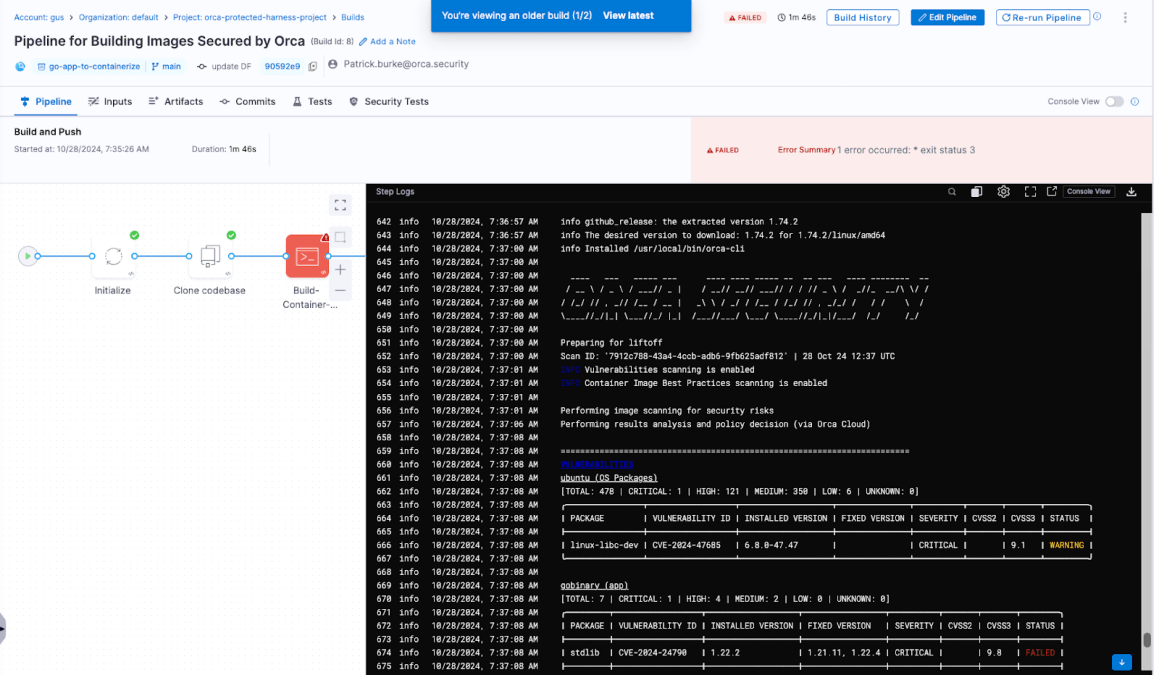
- Any security risks detected by Orca can now be remediated before deploying to production.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform and how it can be integrated with CI/CD pipelines such as Harness? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can identify, visualize, and prioritize risks in your cloud environment.







